Identity thieves stole tax and salary data from payroll giant ADP by registering accounts in the names of employees at more than a dozen customer firms, KrebsOnSecurity has learned. ADP says the incidents occurred because the victim companies all mistakenly published sensitive ADP account information online that made those firms easy targets for tax fraudsters.
 Patterson, N.J.-based ADP provides payroll, tax and benefits administration for more than 640,000 companies. Last week, U.S. Bancorp (U.S. Bank) — the nation’s fifth-largest commercial bank — warned some of its employees that their W-2 data had been stolen thanks to a weakness in ADP’s customer portal.
Patterson, N.J.-based ADP provides payroll, tax and benefits administration for more than 640,000 companies. Last week, U.S. Bancorp (U.S. Bank) — the nation’s fifth-largest commercial bank — warned some of its employees that their W-2 data had been stolen thanks to a weakness in ADP’s customer portal.
ID thieves are interested in W-2 data because it contains much of the information needed to fraudulently request a large tax refund from the U.S. Internal Revenue Service (IRS) in someone else’s name. A reader who works at U.S. Bank shared a letter received from Jennie Carlson, the financial institution’s executive vice president of human resources.
“Since April 19, 2016, we have been actively investigating a security incident with our W-2 provider, ADP,” Carlson wrote. “During the course of that investigation we have learned that an external W-2 portal, maintained by ADP, may have been utilized by unauthorized individuals to access your W-2, which they may have used to file a fraudulent income tax return under your name.”
The letter continued:
“The incident originated because ADP offered an external online portal that has been exploited. For individuals who had never used the external portal, a registration had never been established. Criminals were able to take advantage of that situation to use confidential personal information from other sources to establish a registration in your name at ADP. Once the fraudulent registration was established, they were able to view or download your W-2.”
U.S. Bank spokesman Dana Ripley said the letter was sent to a “small population” of the bank’s more than 64,000 employees. Asked to comment on the letter from U.S. Bank, ADP confirmed that the fraud visited upon U.S. Bank also hit “a very small subset” of the ADP’s total customers this year.
ADP emphasized that the fraudsters needed to have the victim’s personal data — including name, date of birth and Social Security number — to successfully create an account in someone’s name. ADP also stressed that this personal data did not come from its systems, and that thieves appeared to already possess that data when they created the unauthorized accounts at ADP’s portal.
ADP Chief Security Officer Roland Cloutier said customers can choose to create an account at the ADP portal for each employee, or they can defer that process to a later date (but employers do have to chose one or the other, Cloutier said).
According to ADP, new users need to be in possession of two other things (in addition to the victim’s personal data) at a minimum in order to create an account: A custom, company-specific link provided by ADP, and a static code assigned to the customer by ADP.
The problem, Cloutier said, seems to stem from ADP customers that both deferred that signup process for some or all of their employees and at the same time inadvertently published online the link and the company code. As a result, for users who never registered, criminals were able to register as them with fairly basic personal info, and access W-2 data on those individuals.
U.S. Bank’s Ripley acknowledged that the bank published the link and company code to an employee resource online, but said the institution never considered that the data itself was privileged.
“We viewed the code as an identification code, not as an authentication code, and we posted it to a Web site for the convenience of our employees so they could access their W-2 information,” Ripley said. “We have discontinued that practice.”
In the meantime, ADP says it has developed systems to monitor the Web for any other customers that may inadvertently publish their signup link and code.
“We’ve now aggressively put in some security intelligence by trying to look for that code and turn off self-service registration access if we find that code” published online, Cloutier said.
ANALYSIS
ADP’s portal, like so many other authentication systems, relies entirely on static data that is available on just about every American for less than $4 in the cybercrime underground (SSN/DOB, address, etc). It’s true that companies should know better than to publish such a crucial link online along with the company’s ADP code, but then again these are pretty weak authenticators.
Cloutier said ADP does offer an additional layer of authentication — a personal identification code (PIC) — basically another static code that can be assigned to each employee. He added that ADP is trialing a service that will ask anyone requesting a new account to successfully answer a series of questions based on information that only the real account holder is supposed to know.
Cloutier declined to say who was providing the verification service, but these so-called knowledge-based authentication (KBA) or “out-of-wallet” questions generally focus on things such as previous address, loan amounts and dates and can be successfully enumerated with random guessing. In many cases, the answers can be found by consulting free online services, such as Zillow and Facebook.
The IRS found this out the hard way, and over the past year has removed two separate authentication systems that placed too much reliance on KBA and static data to authenticate taxpayers. In May 2015, the IRS took down its “Get Transcript” service after tax refund fraudsters began using it to pull W-2 data on more than 724,000 taxpayers. In those cases, the fraudsters also already had the victim’s SSN, DoB and other personal data. In March 2016, the IRS suspended its “Get IP PIN” feature for the same reason.
But somehow, KBA questions are an innovation that’s worth looking forward to at ADP.
“The IRS didn’t have a PIC code or client code,” Cloutier said when I brought up the IRS’s experience. “They didn’t have as many levels and individual authentication components that we provide our clients.”
Cloutier’s words recalled to mind a scene from the movie Office Space, in which Jennifer Aniston’s character is upbraided by her manager for wearing too few “pieces of flair” on her ‘Chotchkie’s’ uniform. His comment also made me think about one of the best scenes from the cult hit “This is Spinal Tap,” in which the character Nigel Tufnel shows off how all the knobs on his amplifier go to “level 11,” while other amps only go to the more boring and standard level 10.
It’s truly a measure of the challenges ahead in improving online authentication that so many organizations are still looking backwards to obsolete and insecure approaches. ADP’s logo includes the clever slogan, “A more human resource.” It’s hard to think of a more apt mission statement for the company. After all, it’s high time we started moving away from asking people to robotically regurgitate the same static identifiers over and over, and shift to a more human approach that focuses on dynamic elements for authentication. But alas, that’s fodder for a future post.
Update 1:59 p.m. ET: Clarified Spinal Tap reference.
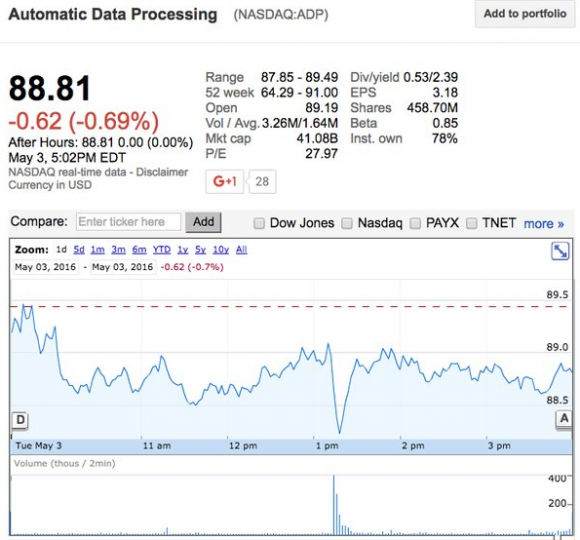
Update, 10:07 p.m. ET: It looks like ADP’s stock took a pretty big hit immediately after this story ran today.
The stock later rebounded:




Thank you for sharing this story, Brian.
Someone hacked my credit card info and stole money out of my account. ADP DID NOT REPLACE MY MONEY YET PLEASE DON’T TRUST THEM WITH YOUR MONEY
What? ADP isn’t a bank. Do you mean ALINE card funds? Because that’s handled by MB Financial Bank, N.A., a third party. ADP doesn’t have any of your money.
Trust seems to be a lesser issue for you than basic knowledge and financial awareness. I’d work on that first.
Alicia Romero…ADP is a payroll company, not a bank. They would not replace funds hacked, that would be from your bank o employer.
Brian, I navigated here from LinkedIn… in the process I had to sign in to linkedIn from a different computer and LinkedIn sent me a code to use via sms on my iphone. I am sick of standard questions – “mom’s maiden name”, “name of your dog” or your “first grade teacher”. This was good back in 2005 but now… much of our information is in the public domain or residing on the black market. In my opinion, banks and other financial institutions are a decade behind on security – paralyzed to move and innovate for a variety of reasons (some customer driven). Then on top of it all… we have security professionals from financial institutions that are arrogant and think that their systems can’t be exploited and throw the vendors under the bus – the Wendy’s case and the lawsuit is a prime example. This is not rocket science and token technology is NOT a new… it comes down to laziness and the inability to innovate and grow with the technological environment in reference to Financial Institutions and Government Agencies. I am a US Bank customer, my company uses ADP, my information was in OPM, and I love Wendy’s hamburgers. So, yes, I care about this and I am a stake holder. These companies/financial institutions need to stop pointing fingers and making excuses and get with the program.
Good piece.
Thank you ADP for adding more “flair” and forgodsakes don’t go enabling dual factor authentication for account holder logins.
That would require way too much time and effort.
We prefer to spend that time on the phone with IRS fraud investigators.
or just abolish the IRS…
I’d like to remind everyone that when this happened, the company at risk posted CONFIDENTIAL Registration information on a public website. Would you post your bank account login information on your blog? Same Idea.
on the office space flair reference 😀
Also the PIC code … its all about how they distribute it and allow retrieval of it. I mean the IRS had an IP PIN in addition to KBA and SSN auth, and that didn’t matter in the end.
Let me blunt. This is inexcusable on the part of ADP. The methodology used to exploit their system has been known about for years. Years! This wasn’t a sophisticated hack. This was a rudimentary attack that should have never happened.
Another one bites the dust, but at the cost of personal data not having the value it deserves. Lets hope your illumination of KBA (Knowledge Based Authentication) exploitation by Darknet OSINT tactics takes hold.
Most importantly in this story you need to get your spinal tap reference accurately. The 11 scene is with Nigel Tufnel a band member showing off his guitars and amps. The amps as you say go to 11 which is one louder than 10 of course trumping the obviously wrong theory that an amp which only goes to 10 could be just as loud!
Later interviews with Nigel Tufnel indicate the band is working on amplifiers which “go to infinity” – you can keep turning the knob round and round and it never stops.
Haha right you are, Matthew. I’ll fix that, thanks.
Good jab, Brian, to ADP for the “human approach”. This industry wide problem gets so frustrating sometimes, that it seems only draconian methods will ever get them to wake up. Of course that is not an option in a Democratic Republic. The frustration drives on! Long live incompetence in free society! /sarc :p
Why not? They’ve already taken draconian methods to get rid of that inconvenient (to police) 4th amendment… It’s a done deal… what free society? Oh, you were being sarcastic. Never mind.
Thanks for another interesting post, Brian. As a an avid reader who has no technical background in security, I look forward to the alluded to future post on dynamic elements for authentication.
Get ready! The IRS is adding “Get Transcript- online” this month. We will have to see how much has changed in their security.
I appreciated the Spinal Tap Reference!
We are a small law Firm in Southern Ca and we too have fallen to ADP’s weak security and inability to take responsibility for their shortcomings. Someone logged into their portal as our administrator. This hacker setup bogus direct deposit accounts for a number of our users, if our Finance director would not have seen these bogus accounts we would of lost over half of our payroll to these criminals. ADP refuses to share the logs showing the IP address linked to this attack and said the changes were made from our organization. We have checked our network and did a forensic examination of our Finance directors computer, the attack did not come from our network and we are 100% sure. We have made multiple requests for their log information and the last response indicated the logs were property of ADP.
I guess the good news is that ADP has competitors. Ceridian comes to mind, but there are others.
For a minute there I thought you were going to say “Green Shade”. Not!
Did you check your Finance Director’s emails? Likely they were victim to a phishing attack and provided the credentials the hackers used…that could be why ADP is saying the login was legitimate.
Breaches are supposed to be reported to Attorney General of your state. In your case, your payroll system data, located at ADP, was breached, and ADP refuses to cooperate with your investigation, so you do not yet know which of your employees PII data was compromised. The AG should be told # of employees at potential risk, and $ total of a normal payroll run, to show level of seriousness. Have you in fact made such a report to CA AG?
You probably ought to send copy, of the report to CA AG also to your local police dept; FBI; and Secret Service. They can then decide if they want to get involved in tracking down the perpetrator. Ask the law enforcement authorities if they will issue the subpoena for ADP logs, or if you should do that.
The IRS also needs to be told that your employee records may have been breached, at ADP. You do not yet know which employees, thanks to ADP non-cooperation. Are you familiar with IRS form 14039?
Your employees should be informed. You should consult with your firm’s legal advisor on the phraseology to be used, to avoid libeling or slandering ADP, and what kind of credit monitoring aid should be granted to your employees. If ADP does not respond well, is this something which can be paid for through your firm’s insurance?
Ever think that maybe your computer or that of your CFO was compromised via some type of malware. Thus getting all your key strokes and they can effectively run your computer at night and change account numbers. Of course it would say it’s coming from your company because they could have made the changes from your computer. I suggest engaging law enforcement and getting a better IT department, because they need your companies admin information to make changes.
This is pretty disappointing (albeit not remotely surprising).
Companies should just give a corporate email address for each employee. Passwords should be generated by employees resetting their account passwords (which should involve sending an email to the corporate email address with a token).
Static pre-minted tokens are a horrible idea.
And any “Knowledge Data” is essentially a pre-minted token.
Unfortunately, the entire cloud-based “API ecosystem” is built upon this very idea as the foundation of access control to data-spigot service APIs to sensitive/confidential/regulated data (e.g. PCI data).
Almost all API onboarding consists of “Here’s your API key (aka user ID) and your API secret (aka password)”.
Regarding the removal of the code as per the quote below, is it not still available via the way back machine?
“We viewed the code as an identification code, not as an authentication code, and we posted it to a Web site for the convenience of our employees so they could access their W-2 information,” Ripley said. “We have discontinued that practice.”
They mean that they won’t post such a thing in the future.
ADP indicated that they would invalidate codes they detect being publicly available:
«“We’ve now aggressively put in some security intelligence by trying to look for that code and turn off self-service registration access if we find that code” published online,»
Thanks Brian, we can always count on you! Unfortunately, security appears to be something that is only thought about with an event such as this one. I dream of the day when someone takes security advise and moves towards remediation for more than a week!
I fear that once this is out of the news, everyone will go back to their same ol same ol.
Trenches are getting tougher, fighters getting fewer.
Some years ago my employer selected ADP+SAP as a Payroll solution, without going through the usual ‘Due Diligence’ process (which I was then in charge of).
When live, we discovered that more than one person could logon to the same Employee account simultaneously : a colleague & I tested it together.
When we reported it (along with 20+ other ‘bugs’), the Payroll Manager rejected the complaint(s) as ‘irrelevant’.
usa dollar is worth nothing, soon it will be dead,usa dollar will be worthless,and next will be pound. i know for fact, i hope criminals who got alot usa dollars will buy something else with them like bitcoins or gold couse usa dollar is just paper.now days
I wondered when that was going to happen, and get noticed. A similar jab was a movie in the late 80’/ early 90’s, about capturing the odd pennies off a payroll, and retiring to Brazil.
Nothing about this in the papers, but, should this be broadcast to all payroll departments, to verify the data from ADP. Check and see, if there are additional add one that are not yours.
About ADP competitors, they are only as safe as the lowest common denominator. They are not in-house. You as the employer, create a more secure environment, by doing the payrolls in house. You can insure that employee, is working for you. You hire it out, you cannot control the quality. Remember, you are cutting costs. You are cutting your security.
Same movie as the one Brian cites earlier, Office Space. That and Idiocracy (both written and directed by Mike Judge) are becoming truly prophetic.
So now we know the stock market reads Krebs too.
Go Krebs!
I am betting there is a savvy trader constructing options contracts on breach announcements.
Not one mention in support of out-of-band authentication?
I am disappointed.
I’ll bet that a Microsoft update would have fixed all this.
Did I just read this correctly? Geez, the government does it that way so it must be secure. Oops, the government got hacked. But we have so many authentication options (easy and weak, or difficult and hard), so isn’t that better? Or is it ‘no one ever got fired for buying IBM’?
Time to turn that brain back on, warm it up, and see if it just might be able to produce a better answer. If not, perhaps another line of work is worth considering. Walmart greeter perhaps?
I received an email from an individual claiming to be an HR recruiter a couple of weeks ago. The individual said he had a job in my professional field and in my local region (he acquired my resume info from LinkedIn or Indeed). The individual’s email domain matched the website that he provided a link to. Doing a little quick search led me to believe that he is a scammer who has contacted others with the goal of getting a hold of victim’s social security number and date of birth.
More than likely this scammer has been collecting SSNs so he could file false return to steal refunds.
I did further research and found that the scammer has created more than twenty fake staffing companies with all the information on the web sites being identical but for the HR directors’ names.
As a warning to others I created a blogger web site with all the information I gathered. It seems the scammer likes using one particular hosting company in Brea California that has let him continue to operate even though I warned them. I think the hosting company likes getting money from criminals.
You can see the list here:
http://fakestaffing.blogspot.com/
nice work!
REPOST: somehow got eaten and never showed up.
What’s with the “Log in with your ADA.org user ID and password”? A manual of updated billing codes is considered confidential rather than public information? Whose privacy or security is harmed if which-code-means-what-procedure becomes more broadly known than just ADA members?
Something like this recently happened to a friend. What I don’t understand, and granted I’m unfamiliar, but how does actually fraudulently getting a tax refund work? Or maybe I’d like more details of the mechanics of the actual fraud in the first place.
I mean, if it’s a rapid refund place, shouldn’t they be checking more than one form of ID, including a photo ID? Or mail a check to the address on the W2? And if it’s normal turbotax electronic filing, again, shouldn’t they send the check to the address on the W2? It seems like it should(?) be incredibly hard to impersonate someone to the point where you actually get money back. And what if they file and owe money? Joke’s on them!
When the IRS receives an Income Tax return, it does not know if it is really from you the tax payer, or from a fraudster. It uses the info on the return as if it is 100% accurate, and if a refund is due, then they pay the refund to whoever filed the return.
Later, your friend files his return & IRS discovers that one of the returns must have been fraudulent. There are over a million new victims of this every year.
Maybe you should point to the people who created the portals most people think its the underground who look like these Executives in their very owen Department .
When Spinal Tap was first released, some folks thought it was a real documentary that was awful…obviously, not the case. Since ‘real’ security is not being deployed, maybe it’s time to start forcing these companies out of business (3 strikes rule?), since they want to do ‘bidness’, but don’t care to0 much about the important stuff like securing our PII data. We also need to license any company or individual mining, collecting, selling and / or distributing PII data. Just my .02.
That is a lie that it was from unregistered ADP accounts. I know employees that have accounts set up and were still compromised and had taxes filed in their names. Let’s worry about where people are going to go to the bathroom instead of stopping these databreaches.
I like the Canada Revenue Agency approach to online access. The first part of the process relies on KBA, including information from past tax returns. But that only gets you half way there. Then they mail you a token to the home address they have on file (and which you can’t override during sign-up). You have to enter that code to complete the registration. During the process, they email you about what’s going on.
Slow to sign up initially, but hard for scammers to subvert.
Interesting post ! I was fascinated by the details – Does anyone know if I could possibly get a fillable a form version to fill out ?