Far too many otherwise intelligent and talented software developers these days apparently think they can get away with writing, selling and supporting malicious software and then couching their commerce as a purely legitimate enterprise. Here’s the story of how I learned the real-life identity of Canadian man who’s laboring under that same illusion as proprietor of one of the most popular and affordable tools for hacking into someone else’s computer.
Earlier this week I heard from Daniel Gallagher, a security professional who occasionally enjoys analyzing new malicious software samples found in the wild. Gallagher said he and members of @malwrhunterteam and @MalwareTechBlog recently got into a Twitter fight with the author of Orcus RAT, a tool they say was explicitly designed to help users remotely compromise and control computers that don’t belong to them.
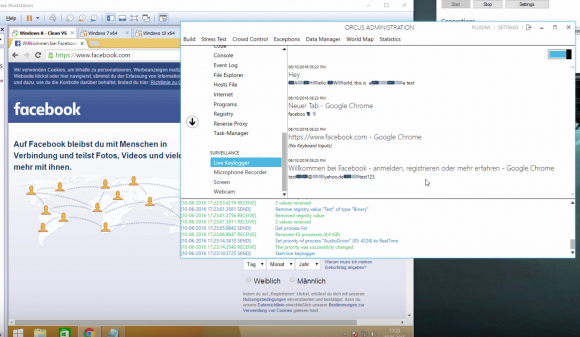
A still frame from a Youtube video demonstrating Orcus RAT’s keylogging ability to steal passwords from Facebook and other sites.
The author of Orcus — a person going by the nickname “Ciriis Mcgraw” a.k.a. “Armada” on Twitter and other social networks — claimed that his RAT was in fact a benign “remote administration tool” designed for use by network administrators and not a “remote access Trojan” as critics charged. Gallagher and others took issue with that claim, pointing out that they were increasingly encountering computers that had been infected with Orcus unbeknownst to the legitimate owners of those machines.
The malware researchers noted another reason that Mcgraw couldn’t so easily distance himself from how his clients used the software: He and his team are providing ongoing technical support and help to customers who have purchased Orcus and are having trouble figuring out how to infect new machines or hide their activities online.
What’s more, the range of features and plugins supported by Armada, they argued, go well beyond what a system administrator would look for in a legitimate remote administration client like Teamviewer, including the ability to launch a keylogger that records the victim’s every computer keystroke, as well as a feature that lets the user peek through a victim’s Web cam and disable the light on the camera that alerts users when the camera is switched on.
A new feature of Orcus announced July 7 lets users configure the RAT so that it evades digital forensics tools used by malware researchers, including an anti-debugger and an option that prevents the RAT from running inside of a virtual machine.
Other plugins offered directly from Orcus’s tech support page (PDF) and authored by the RAT’s support team include a “survey bot” designed to “make all of your clients do surveys for cash;” a “USB/.zip/.doc spreader,” intended to help users “spread a file of your choice to all clients via USB/.zip/.doc macros;” a “Virustotal.com checker” made to “check a file of your choice to see if it had been scanned on VirusTotal;” and an “Adsense Injector,” which will “hijack ads on pages and replace them with your Adsense ads and disable adblocker on Chrome.”
WHO IS ARMADA?
Gallagher said he was so struck by the guy’s “smugness” and sheer chutzpah that he decided to look closer at any clues that Ciriis Mcgraw might have left behind as to his real-world identity and location. Sure enough, he found that Ciriis Mcgraw also has a Youtube account under the same name, and that a video Mcgraw posted in July 2013 pointed to a 33-year-old security guard from Toronto, Canada.
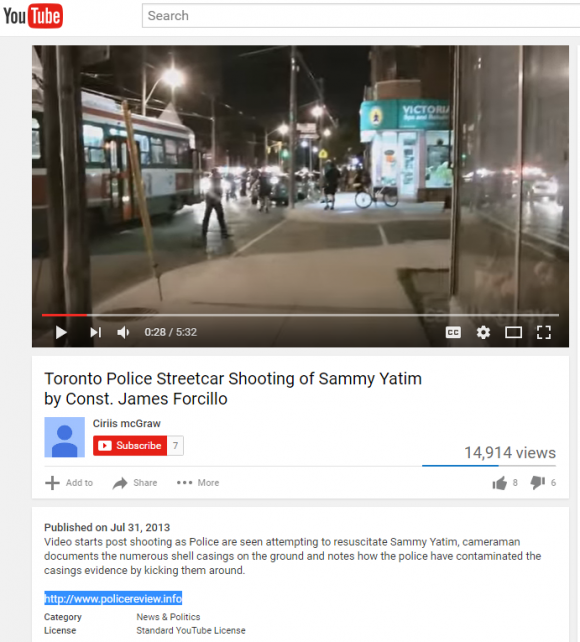 Gallagher noticed that the video — a bystander recording on the scene of a police shooting of a Toronto man — included a link to the domain policereview[dot]info. A search of the registration records attached to that Web site name show that the domain was registered to a John Revesz in Toronto and to the email address john.revesz@gmail.com.
Gallagher noticed that the video — a bystander recording on the scene of a police shooting of a Toronto man — included a link to the domain policereview[dot]info. A search of the registration records attached to that Web site name show that the domain was registered to a John Revesz in Toronto and to the email address john.revesz@gmail.com.
A reverse WHOIS lookup ordered from Domaintools.com shows the same john.revesz@gmail.com address was used to register at least 20 other domains, including “thereveszfamily.com,” “johnrevesz.com, revesztechnologies[dot]com,” and — perhaps most tellingly — “lordarmada.info“.
Johnrevesz[dot]com is no longer online, but this cached copy of the site from the indispensable archive.org includes his personal résumé, which states that John Revesz is a network security administrator whose most recent job in that capacity was as an IT systems administrator for TD Bank. Revesz’s LinkedIn profile indicates that for the past year at least he has served as a security guard for GardaWorld International Protective Services, a private security firm based in Montreal.
Revesz’s CV also says he’s the owner of the aforementioned Revesz Technologies, but it’s unclear whether that business actually exists; the company’s Web site currently redirects visitors to a series of sites promoting spammy and scammy surveys, come-ons and giveaways.
IT’S IN THE EULA, STUPID!
Contacted by KrebsOnSecurity, Revesz seemed surprised that I’d connected the dots, but beyond that did not try to disavow ownership of the Orcus RAT.
“Profit was never the intentional goal, however with the years of professional IT networking experience I have myself, knew that proper correct development and structure to the environment is no free venture either,” Revesz wrote in reply to questions about his software. “Utilizing my 15+ years of IT experience I have helped manage Orcus through its development.”
Revesz continued:
“As for your legalities question. Orcus Remote Administrator in no ways violates Canadian laws for software development or sale. We neither endorse, allow or authorize any form of misuse of our software. Our EULA [end user license agreement] and TOS [terms of service] is very clear in this matter. Further we openly and candidly work with those prudent to malware removal to remove Orcus from unwanted use, and lock out offending users which may misuse our software, just as any other company would.”
Revesz said none of the aforementioned plugins were supported by Orcus, and were all developed by third-party developers, and that “Orcus will never allow implementation of such features, and or plugins would be outright blocked on our part.”
In an apparent contradiction to that claim, plugins that allow Orcus users to disable the Webcam light on a computer running the software and one that enables the RAT to be used as a “stresser” to knock sites and individuals users offline are available directly from Orcus Technologies’ Github page.
Revesz’s also offers a service to help people cover their tracks online. Using his alter ego “Armada” on the hacker forum Hackforums[dot]net, Revesz also sells a “bulletproof dynamic DNS service” that promises not to keep records of customer activity.
Dynamic DNS services allow users to have Web sites hosted on servers that frequently change their Internet addresses. This type of service is useful for people who want to host a Web site on a home-based Internet address that may change from time to time, because dynamic DNS services can be used to easily map the domain name to the user’s new Internet address whenever it happens to change.
Unfortunately, these dynamic DNS providers are extremely popular in the attacker community, because they allow bad guys to keep their malware and scam sites up even when researchers manage to track the attacking IP address and convince the ISP responsible for that address to disconnect the malefactor. In such cases, dynamic DNS allows the owner of the attacking domain to simply re-route the attack site to another Internet address that he controls.
Free dynamic DNS providers tend to report or block suspicious or outright malicious activity on their networks, and may well share evidence about the activity with law enforcement investigators. In contrast, Armada’s dynamic DNS service is managed solely by him, and he promises in his ad on Hackforums that the service — to which he sells subscriptions of various tiers for between $30-$150 per year — will not log customer usage or report anything to law enforcement.
According to writeups by Kaspersky Lab and Heimdal Security, Revesz’s dynamic DNS service has been seen used in connection with malicious botnet activity by another RAT known as Adwind. Indeed, Revesz’s service appears to involve the domain “nullroute[dot]pw”, which is one of 21 domains registered to a “Ciriis Mcgraw,” (as well as orcus[dot]pw and orcusrat[dot]pw).
I asked Gallagher (the researcher who originally tipped me off about Revesz’s activities) whether he was persuaded at all by Revesz’s arguments that Orcus was just a tool and that Revesz wasn’t responsible for how it was used.
Gallagher said he and his malware researcher friends had private conversations with Revesz in which he seemed to acknowledge that some aspects of the RAT went too far, and promised to release software updates to remove certain objectionable functionalities. But Gallagher said those promises felt more like the actions of someone trying to cover himself.
“I constantly try to question my assumptions and make sure I’m playing devil’s advocate and not jumping the gun,” Gallagher said. “But I think he’s well aware that what he’s doing is hurting people, it’s just now he knows he’s under the microscope and trying to do and say enough to cover himself if it ever comes down to him being questioned by law enforcement.”





That was a great piece of investigation…gum shoe tracking blended with high tech malware analysis…Mickey Spillane would be proud!!
One of the write-ups states “We have become aware of unusual malware that was found in some banks in Singapore. This malware has many names – it is known as Adwind RAT” and “Most of them rely on free Dynamic DNS providers and are not real domain registrations.”
My gut tells me that a review of personal bank accounts may be one of the next steps the authorities take…
Love your work Krebs.
Mr Revesz , please go directly to jail, don’t pass go and don’t pickup any commission from your commercial keylogger.
Maybe now your secret is out, some Canadian who enjoyed having your software on their computer will try and seek you out, or thank you for being such as great developer. 🙂
Contacts from my time in the CF have decidedly contacted me in relation to this article, seems Brian has sparked more interest than he might have intended. Something Brian did not note in the article is I am also former military. To which an interest in my product has been expressed. Thanks Brian.
I have to admit that reports about card breaches in Fast Food chains or posts about Flash updates aren’t my cup of tea, but this, this was an awesome read. Great work!
On their site and in multiple posts it says OrcusTechnologies is a registered business in Canada, but there Canadian Companies House shows no Ltd companies registered in that name. Is there any other kind of way to register a business in Canada or am I right in my assumption that they didn’t actually register it as that’d require putting their real info on the internet?
MalwareTech, I believe that companies in Canada can be registered at Federal or at Province level (happy to be corrected if that’s not a fair representation of the situation). The OT website states that it is registered in Ontario, Canada. The Ontario registry charges 8 bucks per search, which I certainly don’t feel like paying to satisfy my curiosity!
http://www.ic.gc.ca/eic/site/cd-dgc.nsf/eng/cs01134.html#Ontario
Correct. A company can be registered at the province or federal level. Multiple legal forms exist: Partnership, corporation, limited partnership, sole proprietorship.
In case of sole proprietorship, the business could be a registered number on which the owner assigns any company name. He would use this number for legal and taxing purposes, but use his fake name for its publicity.
That doesn’t make it illegal.
And there you have it.
Its public information to begin with.
Not to answer the question; however, I ran across an unrelated website similarly claiming to be a registered entity, of a US state. Upon a brief question to the state registration office, I got a reply that a fraudulant filing complaint may be filed. I filed the complaint.
To anwer the question, it may be posed directly to Government of Canada (GC):
http://www.ic.gc.ca/eic/site/icgc.nsf/eng/h_07026.html#from=Corporations
If someone asks the question, I’d be curious what the answer is.
I searched the site for filing a complaint of fraudulent filing, and found none.
Can it be confirmed that John Revesz was really working for TD Bank?
I agree. I would like to see this being confirmed. Any TD Bank people here?
Irrelevant at this point in time.
Looks like a RAT, sounds like a RAT, smells like a RAT – yup – its a RAT!!!
Nice one Brian! And major H/Ts to Daniel Gallagher, @malwrhunterteam, and @MalwareTechBlog.
Serves as a timely reminder of how immature our legal/criminal/LE systems are relative to the technology criminals are exploiting.
@zcobb
Krebs, you should probably update your post to reflect the reality that he worked at TD almost 10 years ago? Your post seems to suggest he is currently employed at TD as a security engineer. This puts TD in the headlines in a bad way. From his CV, and from his LinkedIn this is not true. He also was not a security engineer there. He was a windows administrator / server admin. He seems to have been self employed since 2007. Whatever activity he’s involved in is likely very far removed from his work at TD Bank. So to be fair to TD….
Also, coincidentally there’s a DDoS muscle crew that goes by the name “Armada Collective”…..might be worth snooping around that.
John, the article doesn’t say he works at TD Bank, it says the last time he had a job where he worked as a system administrator — according to him — was when he was working at TD Bank. It doesn’t suggest he still works there. Read carefully.
Another slice of superb sleuthing. Great work, Brian!
For more details, readers should also check out the Softpedia article on Orcus, which started that Twitter feud: http://news.softpedia.com/news/meet-orcus-latest-addition-to-the-rat-market-506006.shtml
Let’s not forget that the justification for disabling the camera light was for users who may have sensitivity to LED lightning.
https://twitter.com/Ciriis/status/750712172641005568
“…sensitivity to LED lightning.”
Seriously? Is that a thing?
I’m always glad when an article like this from Krebs shows up in my email – he’s truly a master at this kind of work, and is what drew me here in the first place.
I think the reason that otherwise intelligent and talented software developers do stuff like this is that they suck at evaluating risk verses reward. All they see is the reward.
Could I be tempted? Of course, but the reward would have to be greater than many many years of professional employment. I doubt his reward is that high.
Nice work from the malwrhunterteam, and a great presentation of the story as always! When do we get another book?
very interesting stuff…thanks for the great investigative work as usual, i’m sure there are plenty of moonlighting individuals currently employed at banks and other companies, and it is material to the story to show the career evolution of this person. I can understand why TD would be sensitive to being mentioned (as safe branding is a priority for banks). It’s only through media like this blog that the many actual financial fraud risks can be made known to the public…otherwise they would branded away as insignificant and alarmist.
Some additional connection data based on whois phone data
https://i.imgur.com/X22BA2D.png
Man is that person ever going to get annoyed with calls.
That is no longer my #
Of course. When you make your living off of other people’s misery, you have to be light on your feet.
But, we all rely on others’ misery (so to speak). There is always someone poorer from whom our lifestyle takes resource and leaves impoverished. “‘Twas Ever Thus.” It appears that the question was resolved a couple hundred years ago to center around “private property,” which landholders lord over the less fortunate. Just because there are many more landholders now doesn’t change the basic physics of finite natural resources and poverty. I think these folks understand the Internet as a new resource to exploit. There are those who do it without consequence (our government) and those who get in trouble for it. Is it like poaching on your neighbor’s land?
Actually, we all rely on others’ cooperation, to make life better. If we all work together, we can make remarkable progress as a civilization. Otherwise, we’re all just running around individually, “trying to spear a squirrel,” as one commentator puts it.
But cooperation relies on trust, and that is why I have no sympathy for someone who enables criminals to commit identity theft and other headaches for innocent people.
Yes, it is a crime to poach on your neighbor’s land, for good reason. The Web being new territory does not excuse invasion of privacy and other crimes. Common decency is never out of fashion.
“‘Twas Ever Thus.” I hope I never become quite that cynical. It must be miserable.
Funny how the article down plays my correspondence with said malwarehunter team and have revised the software explicitly towards their concerns.
Orcus was designed for legal use, we will continue development towards ensuring no enduring abuse of the software exists. Its not an easy task at times due to the software having been cracked. However we are confident with given time this will be resolved.
You were extremely smug and arrogant towards everyone and coincidentally decided to reach out to “rectify the problem” only once researchers followed you on your personal twitter account to show they’d found your real identity.
You don’t get your own article on KrebsOnSecurity by being a thoughtful and law abiding citizen, you get it by being a total jackass, which you were.
Nice words. But I wonder how much more spam and ransomware has polluted the Web, thanks to your “legitimate business operations.”
By the looks of the evidence, your company name should really be “Botnets R Us.”
Morality and topic aside, Armada has shown us the proper way to respond to an article written about you when you don’t want to enter into a (Cici’s-article-style) losing debate in the comments section.
I fail to see the debate.
Concerns were brought to our attention about our products functionality and we are working to address said concerns.
The fact the Author started out with a very obvious bias regarding all of this and despite the “investigative work” taken. They still got a lot of the supposed “facts” wrong.
If your going to post such personal information about someone, at least get it right. Looks very unprofessional otherwise.
For reference my initial comment was written when the only response from Armada on this post was the phone number comment above. My original point was that responding obliquely, in brief, and with a bit of humor is the best option, rather than engaging the readership in a debate by directly opposing/commenting on the article or replies. The back and forth since has undermined that point.
Wondering if he’s “armada.collective@gmail.com” sending out those ransom emails with the same bit coin wallets
Can’t say I know anything about that one, sorry.
Ya, it should be public service messaged to everyone “Don’t behave like the president or congress or corporations or advertisers or the media.”
Does it make sense to contact TD (Toronto Dominion Bank) and inquire how easily a former employee could plant backdoors?
I don’t see what point that would serve? I worked there nearly a decade ago, as a contractor, my access to any such devices is long gone, and even if I somehow to miraculously remember any passwords, they are surely changed by now. Further lets not forget the DMZ that exists. even if malware were to somehow get installed on the internal infrastructure, it has no way of reaching out.
Networking people. Basic networking…..
And here we see exactly why he’s no longer employed as a sys/net admin.
Brian sure is good at ruffling feathers. I counted at least 6 poorly reasoned damage control posts on here, although fair play, this chap is at least willing to use his own name, and his spelling and grammar don’t suck, so that’s a big step forwards from most of Brian’s prey.
Would be quite interested to hear an actual lawyer’s perspective on liabilities given the when-discovered response to misuse is shared with major corporate entities, though. I assume he’s actually bulletproof, unlike the Canadian-owned and thus court orderable DNS service.
With your understanding of basic networking, you do realize that a DMZ is a part of the network where devices are allowed external access, but have heavy restrictions on accessing the internal network? A DMZ has nothing to do with blocking outbound traffic from your malware on the internal network…
But you already know that, right? Of course you do. Since you wrote a very nice article on how to spread malware, with details on bypassing AV and getting traffic to leave the network.
One of my favorite quotes from you in that tutorial:
“we want to market this gibberish to the “Soccer Mom” class of users. We are talking the parents who are either too busy or simply dont know any better than to check the stuff on their computer.”
If anyone want’s to take up a collection, I will be happy guide him from the tyranny of evil and deliver him upon the path to the lord.
j/k I don’t play that for geeks.
We’ve used a keylogger during investigations on multiple occasions.
Great read, thank you for sharing this Brian!
Might as well condemn every offensive hacking tool author. How much harm does metasploit do to the world? I don’t see the difference imo? Because it had a keylogger? really? …
This is the world we made, now we have to lie in it. How can anyone be surprised this guy does not feel like he is doing anything wrong. There should also be laws against most of what so called white hats think they are entitled to do. Hypocrites pointing fingers at others when imo most people in the compute industry, let alone the “security” industry, are also criminals and frauds harming the world.
But wait, Metasploit is intended for legal pen testing ONLY, AM I RIGHT?
I suppose its the companies fault when a malicious user gets their hands on the software and abuses it to breach a services security. But Orcus, hell no its the devils child.
Double standards all up in this place, seriously, I am glad someone can see some reasonable logic through all of this.
are you using diff accounts or names to post things in ur support ?
No in the support system I am registered as System Administrator
We have a support team which also answers trouble tickets.
Hi John Revesz nice to see you also have multiple personalities disorder. #damagecontrol #rekt
How ironic is it that the man who sells tools to cover your tracks did not cover his tracks?
Never really tried to cover my tracks or hide my identity, I just never publicized it either. The Author apparently felt the need to do so.
To that note, I should also caution the author of my legal rights in both my country and theirs regarding Libel.
Enjoy your sleep tonight.
P.S. Statements of fact are not libelous.
I will sleep on this one and get back to you.
Ah yes, the inevitable libel threat. The last vestige of those who feel certain facts are inconveniently brought to light. I’m sorry if the facts in this story are inconvenient, but that’s hardly grounds for libel. But far be it from me to discourage you from trying to sue me though. Discovery would be quite interesting, I’m sure.
Also, you never really tried to hide your identity? Is that why you told your customers on Hackforums that “Ciriis McGraw” was your “legal name?”
No threat, I just caution you on what your posting, proper journalists would have been much more cautious about posting of personal information, to which you seem to disregard.
My identity was never a secret as noted numerous times, I simply dont go toting around introducing myself as John online.
I never told Hack Forums or my customers I was Ciriis Mc Graw, it is but one of many alt nicks I have used online and in games over the years. Nothing more.
None the less, a pretty good write up Brian. In another light we could have worked well together. I used to hunt malware and viral stuff back in my time as IT myself.
BTW. You need to fix the way your wordpress references itself.
If you try to load say this url but without the / at the end your site references the following:
http://krebsonsecurity.com%2Ckrebsonsecurity.com/2016/07/canadian-man-is-author-of-popular-orcus-rat/
Which naturally is broken. Check Settings in wordpress admin for correction.
Hey armada – this article has been forwarded to the RCMP. Maybe their investigators would like to poke around a bit.
Have fun.
I would like to see which section of the criminal charter Id be charged under. My lawyers can’t find any?
All cybercrime are under rotchilds string guidance nothing happens if they dont allow. All the stolen money goes back to them wich they borrow to people with intrest. Then they let steal again from people then again its circle. Fraud also gelping rotchilds to make laws more tight end game is everybody chipped
Goverment secret agents give ideas to organize crime syndicates how to make money. Everytime goverment do so if they want to make new laws or rules. After the criminal syndicates are used then they will be trhowed in to jail in reality those criminals will become …..
Crimnals being told that their back is protected but its lia after
@May, I gotta admit, I have no clue what you are on about.
he means you lawyers are lying to you just to get every last buck out of you till you can’t pay them
PS – big fan of orcus and its sophistication
I again circle back to my Canadian charter and criminal code of conduct. Whete I have violated no law.
Your argument is irrelivant…
@ Armada: Maybe, so far–if Canada is indeed the new Russia–but karma will catch up with you, eventually, one way or another.
And be careful where you go for your holidays, eh? You just might have an unscheduled detour, with an extended stopover.
Id rather choose to face any such implications as you so imply head on.
Again softwares legal. Canada is not the new Russia, our government see no need to by tyrannical in controlling its populous from creation and innovation.
I suppose that is why we lead the way in medical research huh?
Again arguments are irrelivant, I violate no Canadian law in my product. American law does not apply to me, and frankly I see absolutely zero draw to even step foot on American soil. Ya’ll got your own issues going on down there I want no part of.
Thanks for the warning though, I will be sure to make the right turn at Albuquerque .
You really are not as bright as you think you are.
You may have broken many Canadian laws and if any of your users were from the United States, or if your software was used on Americans, you could be extradited there to face charges should they want to go that route. Canada and America routinely hand criminals over to one another.
Run while you can.
I would suggest reviewing the Canadian Criminal Code Part I Section 21 to start with. Here are a few excerpts:
Parties to offence
21 (1) Every one is a party to an offence who
(a) actually commits it;
(b) does or omits to do anything for the purpose of aiding any person to commit it; or
(c) abets any person in committing it.
Person counselling offence
22 (2) Every one who counsels another person to be a party to an offence is a party to every offence that the other commits in consequence of the counselling that the person who counselled knew or ought to have known was likely to be committed in consequence of the counselling.
Also, since you are so adamant in stating that you run a legitimate business, this might interest you:
Other offences — organizations
22.2 In respect of an offence that requires the prosecution to prove fault — other than negligence — an organization is a party to the offence if, with the intent at least in part to benefit the organization, one of its senior officers
(a) acting within the scope of their authority, is a party to the offence;
(b) having the mental state required to be a party to the offence and acting within the scope of their authority, directs the work of other representatives of the organization so that they do the act or make the omission specified in the offence; or
(c) knowing that a representative of the organization is or is about to be a party to the offence, does not take all reasonable measures to stop them from being a party to the offence.
For some clear evidence of counseling others:
https://pastebin.com/8jhAsQ2S
https://pastebin.com/EfhyyCxh
From there, I would suggest next reviewing Part VI Section 184 (Interception of Communications)
That is just scratching the surface though…
Awesome investigation Brian, i like how this guy is in Damage Control on your own comment section. Keep taking down these bastards.