A massive and sustained Internet attack that has caused outages and network congestion today for a large number of Web sites was launched with the help of hacked “Internet of Things” (IoT) devices, such as CCTV video cameras and digital video recorders, new data suggests.
Earlier today cyber criminals began training their attack cannons on Dyn, an Internet infrastructure company that provides critical technology services to some of the Internet’s top destinations. The attack began creating problems for Internet users reaching an array of sites, including Twitter, Amazon, Tumblr, Reddit, Spotify and Netflix.
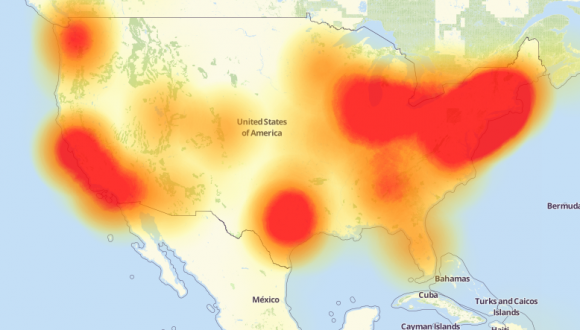
A depiction of the outages caused by today’s attacks on Dyn, an Internet infrastructure company. Source: Downdetector.com.
At first, it was unclear who or what was behind the attack on Dyn. But over the past few hours, at least one computer security firm has come out saying the attack involved Mirai, the same malware strain that was used in the record 620 Gpbs attack on my site last month. At the end September 2016, the hacker responsible for creating the Mirai malware released the source code for it, effectively letting anyone build their own attack army using Mirai.
Mirai scours the Web for IoT devices protected by little more than factory-default usernames and passwords, and then enlists the devices in attacks that hurl junk traffic at an online target until it can no longer accommodate legitimate visitors or users.
According to researchers at security firm Flashpoint, today’s attack was launched at least in part by a Mirai-based botnet. Allison Nixon, director of research at Flashpoint, said the botnet used in today’s ongoing attack is built on the backs of hacked IoT devices — mainly compromised digital video recorders (DVRs) and IP cameras made by a Chinese hi-tech company called XiongMai Technologies. The components that XiongMai makes are sold downstream to vendors who then use it in their own products.
“It’s remarkable that virtually an entire company’s product line has just been turned into a botnet that is now attacking the United States,” Nixon said, noting that Flashpoint hasn’t ruled out the possibility of multiple botnets being involved in the attack on Dyn.
“At least one Mirai [control server] issued an attack command to hit Dyn,” Nixon said. “Some people are theorizing that there were multiple botnets involved here. What we can say is that we’ve seen a Mirai botnet participating in the attack.”
As I noted earlier this month in Europe to Push New Security Rules Amid IoT Mess, many of these products from XiongMai and other makers of inexpensive, mass-produced IoT devices are essentially unfixable, and will remain a danger to others unless and until they are completely unplugged from the Internet.
That’s because while many of these devices allow users to change the default usernames and passwords on a Web-based administration panel that ships with the products, those machines can still be reached via more obscure, less user-friendly communications services called “Telnet” and “SSH.”
Telnet and SSH are command-line, text-based interfaces that are typically accessed via a command prompt (e.g., in Microsoft Windows, a user could click Start, and in the search box type “cmd.exe” to launch a command prompt, and then type “telnet” to reach a username and password prompt at the target host).
“The issue with these particular devices is that a user cannot feasibly change this password,” Flashpoint’s Zach Wikholm told KrebsOnSecurity. “The password is hardcoded into the firmware, and the tools necessary to disable it are not present. Even worse, the web interface is not aware that these credentials even exist.”
Flashpoint’s researchers said they scanned the Internet on Oct. 6 for systems that showed signs of running the vulnerable hardware, and found more than 515,000 of them were vulnerable to the flaws they discovered.
“I truly think this IoT infrastructure is very dangerous on the whole and does deserve attention from anyone who can take action,” Flashpoint’s Nixon said.
It’s unclear what it will take to get a handle on the security problems introduced by millions of insecure IoT devices that are ripe for being abused in these sorts of assaults.
As I noted in The Democratization of Censorship, to address the threat from the mass-proliferation of hardware devices such as Internet routers, DVRs and IP cameras that ship with default-insecure settings, we probably need an industry security association, with published standards that all members adhere to and are audited against periodically.
The wholesalers and retailers of these devices might then be encouraged to shift their focus toward buying and promoting connected devices which have this industry security association seal of approval. Consumers also would need to be educated to look for that seal of approval. Something like Underwriters Laboratories (UL), but for the Internet, perhaps.
Until then, these insecure IoT devices are going to stick around like a bad rash — unless and until there is a major, global effort to recall and remove vulnerable systems from the Internet. In my humble opinion, this global cleanup effort should be funded mainly by the companies that are dumping these cheap, poorly-secured hardware devices onto the market in an apparent bid to own the market. Well, they should be made to own the cleanup efforts as well.
Devices infected with Mirai are instructed to scour the Internet for IoT devices protected by more than 60 default usernames and passwords. The entire list of those passwords — and my best approximation of which firms are responsible for producing those hardware devices — can be found at my story, Who Makes the IoT Things Under Attack.
Update 10:30 a.m., Oct. 22: Corrected attribution on outage graphic.




I have a ChannelMaster DVR. Not sure if it XiongMai-based. Contacting the company tomorrow. What tools can I use to know if I am a node in a DDOS attack?
Even more fundamentally, how does Mirai get through my firewall?
Not a networking expert like most here.
The first four places I would check is the website for Channelmaster, the paperwork that came with the device, whatever might be said within the setting for it as far as firmware, and then whatever might come up within a google search.
I think the starting point is to look at your router itself, and see if the DVR has used UPNP (universal plug and play) to drill a hole in the firewall (i.e see if any ports are being forwarded to your DVR.
you say regarding dvrs, you need to secure your router. most people that have physical dvrs in their home rent them from a cablevision or fios or other provider and don’t control the device. it’s a black box to us, on the providers network, not behind your personal firewall and we have no control over it.
These are not the DVR’s in question. We are not talking about machines for recording Game of Thrones (although they could probably be use for that) that come from cable tv providers.
We are talking about DVR’s that are part of security camera setups. The Machines that these cameras are connected to for monitoring and recording whatever the security cameras see.
These are two very different things. “DVR” means Digital Video Recorder. This is a generic term.
I don’t think you will get an answer.
If not, the right tool is a hammer.
That’s what Crooked Hillary used on her cellphones
How about checking your 23 ports on your device[s]?
If you look at your device logs, if possible, look for large numbers of icmp packets being sent to the same destination
The real culprit behind all of this is UPnP. Your dvr/camera isn’t connected to the internet, your router is. And,as pointed out in one of these articles, ease of use concerns have overriden practical configurations for a while now. If you want to make sure your router doesn’t open up a hole without your knowledge, go kill UPnP on it.
Anyone here already heard of maidsafe.net: https://hacked.com/decentralized-internet-solution-outages ?
It has great potential, I think.
They are still in development and the proof of the pudding is in the eating.
But maybe some people here can help them in achieving their goals.
For DHCP, DNS, and a couple of other services, the client server model could be adjusted so that clients need to use public key cryptography with client keys. Manufacturers could produce keys for themselves, sign intermediate keys for products lines and models, and then include either a per device or per build key which clients would use to get prioritized access to APIs. Services under load could choose to drop unsigned requests, and would generally provide responses to such requests with a higher latency (lower priority). Providers would also maintain a blacklist of abused certificates.
Yes, this makes each request more expensive, but part of the reason that these attacks work is that the client request is much cheaper than the server response. By altering that equation, adding some tracking, and enabling discrimination, the equation can be changed.
Microsoft could issue certificates such that perhaps 1000 users share a certificate. When an OS update is delivered, Microsoft could replace the certificates. If a Microsoft certificate is rejected, it wouldn’t doom all users, just some fraction, and they could contact support for help.
The same would apply to any other vendor.
Certificates should be time limited.
Between the expiry on certificates and the ability certificates or intermediaries, manufacturers would be forced to support devices with at least basic periodic updates. And they couldn’t advertise a device as lasting forever unless they committed to actually supporting it.
This model also covers the case where certificates are stolen: the original devices have to update to get replacement certificates from the vendor, and the thieves have to work to steal another certificate. If a vendor’s certificates are stolen too many times, then service providers could stop accepting them.
If we compare the Internet to a highway system, these certificates would be the equivalent of licensing drivers and vehicles to use roads. Private roads / servers could choose not to require licenses / certificates, but they could change their rules if they need to. And with roads and driver’s licenses, the issuers can choose to revoke or suspend a license, or to stop renewing it. Also, for places with reciprocal licensing agreements, they can choose to stop recognizing another entity’s licenses if there are too many problems.
Privacy would be managed by issuers not generally issuing individual licenses to individual devices, but instead issuing them to groups – and since there’s a cost to issue a certificate, vendors would try to issue as few certificates as possible. But penalties exist for not replacing certificates fast enough: customers could sue or switch vendors. And penalties would exist for issuing 1:1 certificates in that customers would complain about loss of privacy and switch vendors.
This would make DoSing them EASIER – since verifying the client certificate is quite an expensive procedure, all you’d have to do is hurl lots of phony requests with random (but semantically valid) data at them.
There have been some experiments with client-side proof-of-work (one related and common example would be CloudFlare’s captchas when a site is under attack or the client looks suspicious), but not a lot really helps once the attack is big enough to saturate your pipes.
Kill upnp, job done
Nope.
Only if that’s the only device in your LAN.
Ever heard of an infected PC?
Kill UPNP on the router (if you can).
On the device… well, another story.
As the article mentioned, the end user can change the web interface password but ssh and telnet passwords are hard coded into firmware.
The latter are not reachable in most home networks because most are NAT’d and require port forwarding be established for these services.
So it would seem to me that if an end user changes their web based password on the device in question and if they do not establish port forwarding to the telnet or ssh port on the device, then the device should be secured from this type of attack.
Hi Brian,
for me the whole story sound very whitehatish
First the attacks against your site. Attacking the no1 security journalist who will report every detail about the attack and who is even capable of handling the attacks?
Then the release of the source to reveal vulnerabilties so that every hacker will start using it as long it’s not fixed.
It has fix that! written all over it. Too bad it didn’t happen fast enough
Sounds like you don’t have a clue what a white hat is. It’s certainly not someone who launches massive DDoS attacks.
My fault. By definition (Wikipedia) that would be a “grey hat”.
I just don’t see a reason why someone would ddos your site and then release the source (for free) any other than that.
Anyway thanks for the reply.
They release it for free to obscure themselves and watch the world burn. If everyone in a crowd has the Anonymous/Vendetta mask on, who is the one you were looking for?
I agree the author chose to release it to be able to hide. if only you are using it then it’s only a matter of time before they can tie you to it.
Why worry about the source code? There is only one vulnerability to a weapon that is believed to be invulnerable and all powerful…..over confidence.
Brian Krebs is going to make sure the world knows what this is. This is a good thing. Although his ability to ‘handle’ these attacks are only as strong as Google wants to make him.
This is quite simply part of what can be perceived as a cyber virtual version of a ‘cold war’. This whole thing really is more about politics than technology. It is more about international relations than bit coins. The problem here is that in order for this to work, huge numbers of users (potentially all over the world) get used. The end user wether they know it or not, gets used (played) in an attack against who ever or what ever is targeted.
example:
it does not matter what side of the political spectrum YOU personally fall on. This weapon could be used to take down any political party or opponent, Any reporter not saying what the attacker wants them to say, or even any company not doing the bidding of the attacker. The attacker could be a political leader or a rogue nut job.
The funny part is that while all this is happening, YOUR so called security cameras could easily be helping to facilitate more ammunition. And you never know it. But ya know, who’s to say that all those IP addressable light bulbs could not be conscripted into the battle at some point? lol…..All while your sitting down at the dining room table having a quiet evening meal.
The problem today is the industry sells cheap powerful often unpolished (Linux) devices to old cripple women trying to drive a Ferrari.
They give it a buzzword, named IoT.
And everybody bites.
Smart…..
How about we stop making things in china!
Let’s call it price/quality.
How many Linux developers are there in the West?
How expensive are they?
Simple answer.
There are almost no Linux developers in the West because our educational system failed.
Linux and FOSS in general sucks, right?
We missed the boat and are being left with W10 as disaster….
Nu 1, what Linux developer have to do with it? Not a thing, w10? Same, it’s all based on something else. Machine language. Just as English, is a derived language, and Spanish, and even Chinese are all derived languages. The problem is someone uses language to hide something, like your lightbulb spying on what you do, and reporting not to the power company, but to your neighbor. Now imagine, the same chips are in pacemakers, cars and semi automious vehicles. Overload the network. Will the vote counting machine report your vote? Will your pacemaker work? Will your car make the high speed turn to your driveway? Or will your lightbulb turn on?
I thought: “Kill upnp, job done” was enough?
So, it has nothing to do with Linux?
Damn….
I run Linux on a 8-bit AVR.
Ok.., it’s a little slow but it felt secure.
Thanks for destroying my day.
Want to stop making things in China? Then make them in the USA. How to do that? The secret is in knowing why they’re made in China in the 1st place. People think it’s ‘cuz the Chinese work for peanuts. That doesn’t hurt, but that ain’t the reason. The reason is the USA’s egregious corporate income taxes at near-40%. Trump wants to lower them to 15%, which will help, but the real solution is the Fair Tax, that totally repeals absolutely all the US income taxes of the backs of everybody – personal income tax, corporate income tax, payroll tax, gift tax, self employment tax, capital gains tax, estate tax – all forms of income tax. It replaces them with a consumption tax and a “prebate” that pays to each legal resident the amount of money they need to pay the consumption tax on all purchases up to the poverty level for their living situation. If they are a family of 4 and the poverty level for a family of 4 is $24K, then they get enough each month, in advance, to pay for the tax on 24,000/12 = $2,000 of spending each month. So, the poor pay $0 tax, and the rich, such as Trump who is speculated to not have paid any income tax for 18 years due to a huge loss in 1995, would have paid $30,000,000 on the purchase of a new $100,000,000 Boeing 757 that he so conspicuously flies around in.
So, you want to build all that stuff in the USA? Get the US income tax off the backs of the US people, and we will be the newest, bestest manufacturing tax haven on the planet, where people can build things and hot have the government tromping thru the door to steal 40% of your profits, or 15% of your profits, or anything. That’s how to quit making crap in China.
How many US manufacturers actually pay income ? Not many from what I have seen, the USA gives companies that export from the US fantastic tax breaks. It is government policy and it has been that way just about forever.
So these devices listening on telnet and ssh all need to be accessible through NAT on the user’s firewall, right? First question is, is that early necessary? Second, it seems like ISP’s may be able to block this access themselves, perhaps with an advisory to the customer, and without affecting other services? If flashpoint can see easily scan for affected devices, why don’t they share this information with providers?
Understandably, guilty routers and firewalls may be available by default, but surely DVR’s, printers, etc… Why are they reachable on 21 and 22 from the world?!
To answer part of my own question, it seems upnp might be part of the problem. Still, potentially there might be a role for service providers to okay in assisting? I imagine new legislation that allows notice to be served to an ISP, who would then take action to reduce the threat from a particular customer.
The key here is something called “universal plug and play” or UPNP for short. This allows devices to reconfigure the router to add a port forward so that the device in question is visible to the entire internet.
What happens if you turn that off? Depends on the device I guess – there will probably be some loss in functionality. The industry worked hard to make things easy to use and configure and never considered the possibility that brain-dead devices might be added to the network.
ISPs could change the settings to disable UPNP. And they would probably field a lot of phone calls.
On our own FIOS router, I note that there are port forwards to the FIOS TV boxes (which we no longer have). The router does not allow me to delete these forwards, which I find to be interesting. But the forwards themselves lead nowhere (nothing is at the IP addresses in question in our house), but if you had Verizon FIOS TV boxes, it is likely that your DVR would be accessible to the internet as a whole. Since we no longer have those boxes, I can’t probe them to see what kind of security they might have.
would be better to have upnp disabled by default. people that know what it is could enable it if they need it.
The problem with this approach, is that UPnP was designed with people who aren’t tech savvy in mind. The kind of people where even going into their router and enabling UPnP would prove problematic. I think baking security standards into our internet connected devices would probably be a better idea, at least from a business perspective.
After reading the mass media claiming that New World Hackers is formed by Chinese and Russian hackers, we have put together a list of facts
http://www.spoofit.org/new-world-hackers-and-blazingfast/
Those in the community that can help in the research please reach out.
What’s really interesting is the idea of, at some point, having to use a defensive hack to take down these susceptible devices. Sending out a code that essentially “bricks” all these IoT devices if they’re being used to target something a little more dangerous than Reddit or Twitter.
@signaldistress
Bricking a half a million devices would be a very dubious thing to do. In this instance the “infection” is in RAM so it would probably be best to craft something that reboots the device with the problem disabled.
However, this is unlikely to be easy, you’d probably end up having to flash the device remotely. A complex and dangerous task at best; quite likely to lead to the bricking you mentioned.
Maybe it would be enough for a “Grey-hat” to infect lots of them and just turn them all off at some appropriately disruptive time. ( hopefully: “busybox poweroff -n -f” )
Repeat as necessary.
These are security cameras, right ? Turning them off is part of the joke. Along with their recorders.
The culprits for these attacks are IoT and Firewalls with default settings, known unpatched security problems, and devices that use a listing server such as IP cameras. These have a way to punch through your basic firewalls to allow you to view them on the internet. That same server can be used to cough up your IP camera access/info, then the camera can be used externally to attack others.
There are a lot of bots posted with full code atm, all of them have different approaches and script kiddie like adults using them.
I’m glad we didn’t see the Russians were behind it on Krebs here. I’m so tired of hearing that unsupported crazy MSM garbage.
An update to Mirai to brick an IoT device until power cycled would motivate owners to change the password or get a firmware update. Also, I read that 80% of the bots were DVRs – as these devices are usually owned by the cable/satellite company getting a fix out should be routine for them.
Go back and look at Krebs Oct 3 column.
Brian – Regarding your UL comment, I’m surprised you’re unaware of the work Mudge and his wife are doing around creating essentially a Cyber UL called the Cyber Independent Testing Lab.
http://cyber-itl.org/
I strongly suggest looking into their work, they’re off to a great start (in my opinion) and this is long overdue.
I’m well aware of it, thanks, and even followed their presentation this year at Defcon on the subject
https://www.youtube.com/watch?v=HVjgKP2KIYI
My comment about the need for a UL goes beyond this effort, however, which currently seemed more aimed at software than hardware. What we need is something quite a bit broader and more urgent.
Understood and agreed. It’s apparent the companies pumping these insecure products out won’t make any moves in the right direction unless it effects their bottom line.
The Zatkos seem to be trying to empower the consumer with information to make more educated buying decisions, which may or may not incentivize manufacturers to change their behavior.
It’s of my opinion we need some significant legislation to push manufacturers in the right direction, but it will take someone much smarter than I to sketch out what that would look like.
Brian is spot on. The Federal Gov sometimes protects you from things you don’t want to happen, ex. buying a lamp that burns your house down. To prevent that there are Nationally Recognized Testing Laboratories (NRTLs), of which UL is one. US law enforces that lamps sold must pass the UL electrical safety tests, sparing millions of people from electrical fires in their home. It would make sense for the IEEE to develop the standard. Maybe some kind of auto traffic throttling if anomalous traffic patterns were detected, the algorithm would have to be very good though.
Access to internet is now as vital as running water and protecting that access is going to fall on government, commercial industry has no motivation. But undoubtedly this protection will equate to less privacy.
UL is already working on this. They do work with IoT and also have specific focus on medical devices and SCADA standards.
How does one targeted by DDOS ever defend? Why do these attacks ever end? It would seem that they would continue until the botnet controller decides to stop. I suppose that the defense would be different for a site like Krebs compared to a network like DYN. Comments?
Hangzhou Xiongmai Technology has acknowledged responsibility, says it initiated a first fix in September 2015 and wants customers to update their firmware.
http://www.computerworld.com/article/3134097/security/chinese-firm-admits-its-hacked-products-were-behind-fridays-ddos-attack.html
But who are its customers? What brands of security cameras, sold in the US, use this chip set, and for how long have they done so?
We need to find that out.
I work at UL and we do have a Cyber Security program. It seems to be geared at this point towards Health Care Equipment and Industrial Control Equipment but I would assume that Consumer Devices is on it’s way. Better minds then mine would know.
http://www.ul.com/newsroom/pressreleases/ul-launches-cybersecurity-assurance-program/
Ok – here’s what I did keep my Night Owl AHD7 security camera DVR from being a bot
Useless for using internet to see my cameras but I could care less – I rarely leave my home/lab – http://www.ajawamnet.com
It does still allow me to log in on the local network with a browser and see the cameras/admin the box
First, set up your router to not do silly – no remote, shut off all port forwarding, etc… and def the satan of uPNP (see http://console-cowboys.blogspot.com/2013/01/swann-song-dvr-insecurity.html ). Set all the router stuff to a 0 address and disable
Note Console cowdude was able to get U-Boot to give him a login, I think (since his article was from 2013) they shut that off. I’ll let you know…
But I was able to set up the DVR to hose it’s ability to connect to the mothership. Just go into the network config of your DVR, use a static IP and settings, disable DHCP, and set the gateway and DNS last octet to 0.
Example – 192.168.1.0
I consoled into mine using a RS-232 level shifter. Before I did this you could see (both on the console and wireshark that it was phoning home and all happy with being able to connect to the internet:
Here’s a link to a pic of my levelshifter connections:
http://www.ajawamnet.com/stoopiddvr.jpg
Before I set the Gateway and DNS to null:
UIIPC]F:calback, L:608, UI msg main:1000, sub:62
[APP]: End process message(MainType:1000, SubType:62, MsgSize:0, Sequence:21)
[GUI]: Received message(MainType:1000, SubType:62, MsgSize:8, Sequence:21)
Calling IOTC_Device_Login() ret = 0, UID[BGT8FTFD7C2GUJW4111A]
P2PTunnelServer_Start Success, I can connected by Internet.
Call P2PTunnelServer_GetSessionInfo ret[0]
set HDDled group: 10 bit: 3
set Record Group: 12 bit: 1
set PlayBack group: 12 bit: 0
set NetWorkBit group: 12 bit: 4
change_file end is /dev/ttyAMA2
Open /dev/ttyAMA2 success!!
Set termios done!
Set termios done!
With a “real DNS and Gateway set up in the DVR’s network settings, my Wireshark Port mirror showed all kindsa stuff going to about 5 different routable IP addresses (prob in CN somewhere…)
After I set it to null for gateway and DNS and I verified this with Wireshark running on a port mirrored switch (look up port mirroring the Netgear Prosafes can do this):
No Internet, error[-41]!! Reconnect after 15sec…
Calling IOTC_Device_Login() ret = -41, UID[BGT8FTFD7C2GUJW4111A]
No Internet, error[-41]!! Reconnect after 15sec…
Calling IOTC_Device_Login() ret = -41, UID[BGT8FTFD7C2GUJW4111A]
No Internet, error[-41]!! Reconnect after 15sec…
Calling IOTC_Device_Login() ret = -41, UID[BGT8FTFD7C2GUJW4111A]
No Internet, error[-41]!! Reconnect after 15sec…
[COMM][TcpConnect] line[701] getaddrinfo error host.nightowldvr04.com, 80: Name or service not known
[NET][TutkPushRegServ] line[6950] tutk pushreg fialed
[COMM][TcpConnect] line[701] getaddrinfo error host.nightowldvr04.com, 80: Name or service not known
[NET][TutkPushRegServ] line[6950] tutk pushreg fialed
[COMM][TcpConnect] line[701] getaddrinfo error host.nightowldvr04.com, 80: Name or service not known
[NET][TutkPushRegServ] line[6950] tutk pushreg fialed
[NET][AlarmTUTKPushThread] line[7466] tutk reg faile !
Calling IOTC_Device_Login() ret = -41, UID[BGT8FTFD7C2GUJW4111A]
No Internet, error[-41]!! Reconnect after 15sec…
Calling IOTC_Device_Login() ret = -41, UID[BGT8FTFD7C2GUJW4111A]
No Internet, error[-41]!! Reconnect after 15sec…
Calling IOTC_Device_Login() ret = -41, UID[BGT8FTFD7C2GUJW4111A]
No Internet, error[-41]!! Reconnect after 15sec…
Calling IOTC_Device_Login() ret = -41, UID[BGT8FTFD7C2GUJW4111A]
No Internet, error[-41]!! Reconnect after 15sec…
[COMM][TcpConnect] line[701] getaddrinfo error host.nightowldvr04.com, 80: Name or service not known
[NET][TutkPushRegServ] line[6950] tutk pushreg fialed
[COMM][TcpConnect] line[701] getaddrinfo error host.nightowldvr04.com, 80: Name or service not known
[NET][TutkPushRegServ] line[6950] tutk pushreg fialed
[COMM][TcpConnect] line[701] getaddrinfo error host.nightowldvr04.com, 80: Name or service not known
[NET][TutkPushRegServ] line[6950] tutk pushreg fialed
[NET][AlarmTUTKPushThread] line[7466] tutk reg faile !
Calling IOTC_Device_Login() ret = -41, UID[BGT8FTFD7C2GUJW4111A]
No Internet, error[-41]!! Reconnect after 15sec…
Love the misspellings for their console output – “Fialed” (I should talk – I suck at typing, I’m a bass player)
As I mentioned – a 5 hour run with a port mirrored Wireshark session shows no connection to the web. It be all confoosed with null for a gateway and DNS…
BTW – if anyone wants to see the full logs pre and post null settings email me. My email is on my link to my webpage They’re quite interesting….
As i mentioned before, they should not be using Linus for this stuff. Yea, they’ll patch their busybot firmware, but really… there’s no need to run a GP Os on this kinda stuff.
http://www.ajawamnet.com
Any advice on how I can fin a DVR that doesn’t have components from XiongMai in it?
thanks
What really ticks me off is that I have warned people of this while doing Qualifications (audit on steroids). Many companies lack the administrative personnel to make the proper IT calls on removal of this crap. Mind you even if they do remove it, what are the viable alternatives that are cost effective and easily integrated?
It’s always easy to say something sucks, not as easy to find a solution to the problem. There is also the factor of investing in right people to monitor, secure and maintain the network. Which I have to say, is difficult to do when there is such a fatty layer of figureheads in IT director positions.
One last thing. While doing a qualification of a WAN I sent I sent an envelope with tests for routers and switches, a camera, and a pen to fill out results to a branch in Beijing. (We do this to ensure the testers cannot claim they could not find one and therefore not complete a test) The envelope was stopped by customs in China. It was stripped and our personnel were asked why they could not use a pen made in China and why they could not use a camera made in China. So this blind trust we have in China is not reciprocated. How many times do we have to get burned before we smarten up?
If the mafia had a internet security company they would launch attacks until everyone subscribed. And occasionally after that to keep everyone in line. Just sayin’
Not an expert
For another point of view, why not take a look at http://truthnetmedia.com/malicious-hacking-caused-internet-outage-affected-various-u-s-european-cities-source-attack-yet-determined/
On the bright side, many of those consumer grade IoT devices use low quality components and they will gradually disappear from the Internet as they fail. It will take several years, and in the meantime countries should establish customs screening to keep vulnerable IoT devices out of their domestic markets.
Interesting that none of this seems to be impacting Apple’s IoT products (HomeKit). Apparently the “walled garden” is a safe place to be these days.
Idealistic proposals and fantasy won’t work. Only one approach will. Any hacker with Bot Net experience could build a Bot that logs in to any unsecured devices and changes the settings/password to secure that ip. It would be a Bot Net attack in reverse. That is the only way to quickly attack and solve the problem. It may brick some devices but the alternative is nationally suicidal. Is anyone here qualified to do it?
If the IoT devices can be identified and hacked to serve the DDos purposes, why couldn’t a similar system exist that identified and either inoculated or simply shut down the same devices?
very interesting, billLee, it does exist, check out http://www.cybersecuritysalary.org/