Citing a computer virus outbreak, a hospital system in the United Kingdom has canceled all planned operations and diverted major trauma cases to neighboring facilities. The incident came as U.K. leaders detailed a national cyber security strategy that promises billions in cybersecurity spending, new special police units to pursue organized online gangs, and the possibility of retaliation for major attacks.
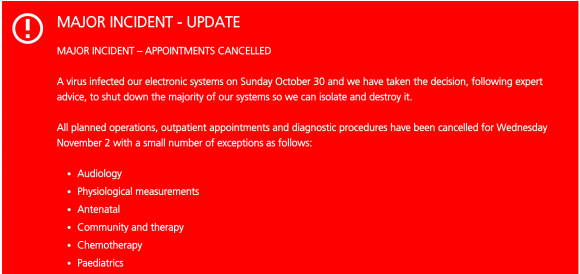
In a “major incident” alert posted to its Web site, the National Health Service’s Lincolnshire and Goole trust said it made the decision to cancel surgeries and divert trauma patients after a virus infected its electronic systems on Sunday, October 30.
“We have taken the decision, following expert advise, to shut down the majority of our systems so we can isolate and destroy it,” the NHS said, of the unspecified malware infection. “All planned operations, outpatient appointments and diagnostic procedures have been cancelled for Wednesday, Nov. 2 with a small number of exceptions.”
The advisory continued:
“Inpatients will continue to be cared for and discharged as soon as they are medically fit. Major trauma cases will continue to be diverted to neighboring hospitals as will high risk women in labour.”
Although the NHS didn’t say what kind of virus infected its systems, it is likely an infestation of ransomware — a malware scourge whose purveyors have taken to targeting hospitals and healthcare facilities.
Ransomware scours an infected computer for documents, audio files, pictures and other things likely to be of value to the system’s owner, and then encrypts that data with very powerful encryption software. Most ransomware variants also scour the local network for other systems or network shares to infect. Victims usually can only get their files back after paying a specified ransom demand using a virtual currency, such as Bitcoin.
Earlier this year, experts began noticing that cybercriminals were using ransomware to target hospitals — organizations that are heavily reliant on instant access to patient records. In March 2016, Henderson, Ky.-based Methodist Hospital shut down its computer systems after an infection from the Locky strain of ransomware. Just weeks before that attack, a California hospital that was similarly besieged with ransomware paid a $17,000 ransom to get its files back.
According to a recent report by Intel Security, the healthcare sector is experiencing over 20 data loss incidents per day related to ransomware attacks. The company said it identified almost $100,000 in payments from hospital ransomware victims to specific bitcoin accounts so far in 2016.
As dependent as healthcare systems are on computers and information technology, the notion that a computer virus could result in bodily injury or death is no longer the stuff of Hollywood movie scripts. Unfortunately, the healthcare industry is for the most part still catching up in its ability to anticipate, prevent and respond to these types of cyber attacks.
As macabre as it may sound, perhaps people dying because of poor cybersecurity is exactly what it will take for more organizations to dedicate the necessary resources toward adequately defending the systems upon which they so heavily rely.
In 2010, I was interviewed by Team Cyrmu‘s Steve Santorelli as part of their ongoing Who and Why Show. Santorelli gave me a few minutes to answer the question, “What keeps you up at night?” My answer was basically that I worry what will happen to the Internet as we know it when people start to die in a measurable way because of computer and Internet security vulnerabilities and attacks. Here’s the entire interview if anyone cares to have a listen.
The crippling of NHS’s systems came as U.K. Chancellor Philip Hammond unveiled a national cybersecurity strategy, warning that hostile “foreign actors” were developing techniques that threaten the country’s electrical grid and airports, among other critical infrastructure.
“If we want Britain to be the best place in the world to be a tech business then it is also crucial that Britain is a safe place to do the digital business,” Hammond said Tuesday as he described the National Cyber Security Strategy in London. “Trust in the internet and the infrastructure on which it relies is fundamental to our economic future.”
What can businesses do to lessen the chances of having their critical infrastructure crippled by malware like ransomware? The FBI has the following tips:
- Regularly back up data and verify the integrity of those backups. Backups are critical in ransomware incidents; if you are infected, backups may be the best way to recover your critical data.
- Secure your backups. Ensure backups are not connected to the computers and networks they are backing up. Examples might include securing backups in the cloud or physically storing them offline. It should be noted, some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real-time, also known as persistent synchronization.
- Scrutinize links contained in e-mails and do not open attachments included in unsolicited e-mails.
- Only download software – especially free software – from sites you know and trust. When possible, verify the integrity of the software through a digital signature prior to execution.
- Ensure application patches for the operating system, software, and firmware are up to date, including Adobe Flash, Java, Web browsers, etc.
- Ensure anti-virus and anti-malware solutions are set to automatically update and regular scans are conducted.
- Disable macro scripts from files transmitted via e-mail. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full Office Suite applications.
- Implement software restrictions or other controls to prevent the execution of programs in common ransomware locations, such as temporary folders supporting popular Internet browsers, or compression/decompression programs, including those located in the AppData/LocalAppData folder.
Additional considerations for businesses include the following:
- Focus on awareness and training. Because end users are often targeted, employees should be made aware of the threat of ransomware, how it is delivered, and trained on information security principles and techniques.
- Patch all endpoint device operating systems, software, and firmware as vulnerabilities are discovered. This precaution can be made easier through a centralized patch management system.
- Manage the use of privileged accounts by implementing the principle of least privilege. No users should be assigned administrative access unless absolutely needed. Those with a need for administrator accounts should only use them when necessary; they should operate with standard user accounts at all other times.
- Configure access controls with least privilege in mind. If a user only needs to read specific files, he or she should not have write access to those files, directories, or shares.
- Use virtualized environments to execute operating system environments or specific programs.
- Categorize data based on organizational value, and implement physical/logical separation of networks and data for different organizational units. For example, sensitive research or business data should not reside on the same server and/or network segment as an organization’s e-mail environment.
- Require user interaction for end user applications communicating with Web sites uncategorized by the network proxy or firewall. Examples include requiring users to type in information or enter a password when the system communicates with an uncategorized Web site.
- Implement application whitelisting. Only allow systems to execute programs known and permitted by security policy.
Further reading: SC Magazine UK’s take on the attack.




First thought was a crypto of some variety. They’re probably debating paying it or not right now. Software restriction policies and end user training help prevent this kind of junk but may not entirely eliminate it.
They would not pay the ransom, this is a hospital, they have redundancies for these types of catastrophic events. With remote desktop backup, network drives etc., they should have something to fall back on. If not, they should take a look at IT administrators to see why this was not planned for.
I work in a hospital, and I don’t know if I agree with you, depending on the circumstance.
If it’s affected a significant chunk of workstations as well as the servers, restoration from backup is going to take a while. Hospital IT staff is notoriously understaffed (and not frequently staffed with the top 10% of IT people in terms of skill) and fixing that mess could take weeks or even months the way they usually implement things.
This means absolutely unacceptable financial losses, not to mention the impact to patients. Hospitals often pay these ransoms because they simply can’t afford the downtime to restore from backup (and don’t get me started on the fractured nature of how we store data in the medical community; there’s dozens of interacting 3rd party systems that store their data all over the place; some we can work around, others break everything if they bite the dust).
“If not, they should take a look at IT administrators to see why this was not planned for.”
Money, the answer is almost always money. The problem is that no one cares about backups. They are underfunded and neglected. However, everyone cares about restores. Unfortunately, because no one gave a damn about the backups, there is nothing to restore. It usually takes an incident like ransomware actually hitting a business before they come to this realization and fund backups. Though, even that fails over time. A business will setup a great backup system, and then move on with business. Eventually, someone starts to ask why we’re spending several hundred dollars a year in replacing tapes or if we really need to replace that failing backup server. Or, the data on the network expands to the point that the backups are taking too long; but, increasing backup capacity is expensive and maybe we don’t need to backup some stuff. In 5 years time, the backups have once again decayed to the point that they aren’t worth much; but, no one cares about backups.
And don’t get me started on the people who store business critical data only on their laptop/workstation. These people should be waterboarded.
IT Administrators ? They dont do the planning, they are part of operations and maintenance and some times deployment. Policies and plans like these come from very top managers, dierctors, CIOs level top. I lot of hospitals might not have a budget, or staff to plan for such scenarios.
You would be surprised, how often such common things are missing due to lack of will to pay for them from the management 🙂
This comment reeks of someone who’s never worked a day in an enterprise IT environment.
The most important thing on the list in my opinion” Regularly back up data and verify the integrity of those backups. Backups are critical in ransomware incidents; if you are infected, backups may be the best way to recover your critical data”
Backup is important, for all the reasons that it’s always been. Ransomware is just a new form of the same threat, inadvertent loss or destruction of important data, but the old saw, “An ounce of prevention is worth a pound of cure…” was never more appropriate than in the case of ransomware. It is so easy for an attack like this to succeed, given that the attack vector virtually always includes a user whose PC is already inside most traditional defenses. More effective defenses are in order here. Application whitelisting is the best, though other approaches are showing promise.
If said backup system was connected at the time of infection, and it was of some variant a cryptowall piece of malware, then that malware can or may traverse the network share and start encrypting the backup as well thus your backup is ruined, so youll have to resort to off site backups. That may be nice, but you will have to re-enter all charts and data dating back to when the last offsite was done. That is of course you do keep paper backups.
It’s really worrying! Thanks for this interesting article.
To the list of FBI tips the possibility of local data encryption can be added. We’ve developed a physical device, SMiD Cloud, that performs automatic full data encryption before uploading data to the cloud, thus providing hospitals, lawyers, and other businesses with sensible data with a cheap and powerful way to secure their data.
Don’t hesitate to contact us for further discussion.
Encrypting data sent to the cloud doesn’t help a bit when the data is already encrypted by malware. You can do better than that.
Maybe their encrypting for compliance with security policies given the sensitive nature of their data?
Sure, but what about if the data hasn’t been infected??
Your service would do little to prevent data loss. While it is true the files are encrypted on your servers, you still have to decrypt them for the user. Since the virus runs in the user context it too will see the unencrypted files. The only added security you are really offering is if the mapping to the files isn’t a standard windows file share. That would likely prevent the current ransomware products from finding the shared files. Anything saved locally, however, would still be lost.
By way of clarification…. Most of the ransomware that I have come across infects only the machine that opened the infected email / website. The ransomware then leverages the infected machine to encrypt local and shared files that it has access to. The servers providing the shared files are not actually infected. The article implies that the infection is spread to the machines hosting the shares, but I don’t believe that is the case (even though the effects are certainly spread to those hosting machines). Some may think this is not an important distinction, unless of course, it is your job to find and stop the malware from encrypting your shares.
It depends on how sophisticated the malware is in scanning your local machine and network – but from everything I’ve read, the list in the article is correct. You have to assume the worst scenario in planning anyway.
How do you get an avatar for your postings?
Gravitar(dot)com is the easiest place to register your avatar.
You can almost eliminate the issue of RansomWare via emailed attachments containing scripts in or outside Zip files too by changing the Windows default file associations for (.js, .jse, .wsf, .wsf & .hta) to open Notepad vs. launching the scripts that would infect the machines. This will render whatever the user opens harmless.
This does not work in Windows 10 Home, Anniversary Edition, except for .js
Wouldn’t it be easier if the server would rename the file extensions to something like blabla.ext.txt?
Office macros are one of the biggest risks.
Disabling hospitals with ransomware reminds us that the moral depravity of criminal pathology has no bounds.
When people start dying on account of malware, as Mr. Krebs has warned us a long time ago, perhaps computer security will begin to receive the priority it deserves.
“When people start dying on account of malware, as Mr. Krebs has warned us a long time ago, perhaps computer security will begin to receive the priority it deserves.”
That’s a highly optimistic assessment. I suspect we’ll swing from underprioritizing computer security to wildly overprioritizing it: Everything from overwrought demands that systems be re-engineered *NOW*, throwing boatloads of money at the issue (which will be scooped up by scam artists posing as security professionals) to a worst case of crippling/shutting down internet communications.
I suggest you listen to the interview, which makes your point exactly: That the problem with waiting until people start dying because of poor cybersecurity is that we will swing so far in the other direction that getting online will be about as free and fun as getting on an airplane these days.
Maybe then my wife will spend time with me instead of her social media “friends”
This is when transparency works both ways. Transparency into actual causes of technology problems will help us learn how to be more transparent in preventing them. Also, many hacktivists still are focused on transparency (political hacks, dating sites, big companies)…as many regulators are now too(data collection and FTC)…and hopefully more consumers as well. consumer awareness is what drives change.
Another problem with people dying over this will be the resulting lawsuits. Can you just imagine how much patients dying because of a computer virus will cost in legal fees and settlements? Of course, nothing will sting a business and make them act responsibly more than hitting them hard in the pocketbook, but that won’t bring the dead back.
I agree with the first part of your statement.
The second part depends on if companies(a hospital is a business) are willing to spend the money on security even if it means losing some money IMHO. As we know, some businesses actually calculate weather it might be cheaper to let people die & pay lawsuits than to take preventive measures.
The article states “Secure your backups. Ensure backups are not connected to the computers and networks they are backing up”
I use a combination of Aegis Apricorn encrypted hard drives for archive purposes off of Synology NAS drives on my LAN network
I am fully prepared for any ransonware attack
Don’t bet on those drives protecting you. Most NAS systems mount using SMB and show up as another driver letter. Most ransomware will happily encrypt those too. and it looks like the encrypted drive does the same once unlocked. Oopsie… they’re toast too.
Older ransomware wouldn’t touch ftp servers, so they were safe for backup. Not sure if that is true any longer.
No you aren’t.
Modern ransomware will look for all attached storage, network drives, and even other things to encrypt.
Backups that are in tiers, and offsite, help with this. So you can go back a week to restore things etc.
That’s the whole idea behind offloading the backups ( which are encrypted in the first place ) to a Aegis Apricorn encrypted hard drives which are not connected to any any computer permanently . This is done for long term archiving. All other files all backed up to a cloud server in France and or New Zealand, daily sometimes weekly.
That’s great until you realize that your offsite backups will now take days or weeks to get back on your servers! Even with backups – recovery can be a long and expensive process.
Brian,
Is there another DDOS that just started? Down dector shows heavy outages and lynda.com is down.
http://downdetector.com/status/level3/map/
I can’t find official news confirmation yet.
I was also wondering that. I couldn’t get to this site about an hour ago.
In the previous attacks on hospitals I don’t remember then cancelling any appointments or operations. Is this the first time a cyberattack has taken down a major piece of infrastructure like this?
Uninformed people showing up the ER to just be turned away could be in serious danger.
We did a massive amount of IR for hospitals / med centers in March-May this year. Most were hit by SamSam/Samas and in more than a few cases, surgeries had to be rescheduled, operations delayed, and general operations came to a halt.
I don’t know how to say this without sounding like a vendor, but the best way to prevent ransomware is to leverage AI and predict its variants before there are any patient zero victims such that you can block it pre-execution and not have to rely on delayed signatures or behavior/heuristic based detection. It’s 2016… predictive AI is everywhere. It’s time to leverage it and get back to our mission as organizations; especially hospitals.
Antimalware AI is a cool thing, but I think its primary market space is well-secured companies that still need more cutting-edge security.
Hospitals are… Not well-secured. They have horrible security practices at every level, are terribly unprepared for major network failures, happily compromise even nominal security if anyone above a lowest-level supervisor insists, and are probably more vulnerable to social engineering attacks than anyone else anywhere.
The main reason that they’ve been left alone so far is that hackers generally avoid targeting them, because doing so paints a huge target on your back and makes you a pariah in all but the most sociopathic blackhat groups. However, now that “harmless” (if you pay) ransomware is out there, they’re not the happy DMZ they used to be and are now just another target.
We can see from observed evidence how well that’s working out for them.
An addition also, apparently a UK gambling site is under DDOS attack is well:
http://www.theregister.co.uk/2016/11/02/william_hill_ddos/?mt=1478102841882
I don’t know the grand scope of things beyond the Level3 map.
With the NHS issue they should be keeping separate networks, one for the data and critical and patient booking systems with NO access from outside, except through a secure gateway used only for updates and another network that does have external access.
Also, perhaps changing the extensions of office documents to beat the ransomware (if it was ransomware). It may or may not work, might cause issues for the users when selecting files but if it works it should help. If ransomware is looking for partitcular files using their extension then this should work, at least until they add a workround.
Any company or oganisation should do the same – find all your mission-critical systems, services and applications, effectively turn them into virtual appliances with no Internet connectivity under any circumstances. Whitelist the internal servers and other devices that feed and use these virtual appliances and deny connectivity from everything else. Remove/disable all applications, services and ports you do not need, and you have a fighting chance.
Patches and updates can be done on a quarterly cycle, or similar slow-time schedule.
The next step is to seriously consider some kind of VDI-like service for all your end user computing devices.
I have actually worked with the NHS in creating a piece of software that they later hosted. I can tell you that the NHS infrastructure is really quite secure and well managed, albeit I’m talking about the central NHS and not the local health trust. Indeed, all “cloud” software is actually hosted inside the NHS on a kind of really big Intranet, with no outside access.
Likely this attack has not affected the NHS at all, and instead has affected local computers at the health trust only.
Unfortunately, as helpful as any of the tips may be, they are only as effective as each organization’s willingness to adhere. In my opinion, the important question is, “Why is healthcare being targeted?”
As Mylan and other drug pricing stories have developed over the last couple years, it’s becoming more and more obvious that the demand of healthcare products and services is quite inelastic (everybody likes to live, right?). And companies in the industry know it.
The incentive to take any measure is going to be small until healthcare loses the ability to easily pass costs onto the consumer.
If the food I put on the table came from ransom payments, I’d probably focus on the easy targets too.
This problem is not helped by archive programs that want you to run backups regularly, but which go looking for the backup drive that they expect to be there.
Funny, all of it concerns some form of software or actions by users yet none address the actions by users being human and fallible, i.e., what kind of training to help users understand the very techniques used to get them to do something – think Manipulation Professionals and how they use influence principles such as, “reciprocity, liking, social proof (a big one), scarcity, authority (remember the IRS scam), and consistency” that tend to turn human actions into automatic responses, etc.
How we treat people, how we influence them and are influenced by them and other human conditions that would create an obligation of consistency toward security and IT safety?
We keep on assuming that the very software we depend on is the very software that is most vulnerable to nefarious predatory actions.
Two additional recommendations.
1) Network firewalls MUST have policies that allow “only that which is required” both inbound AND outbound.
2) Partition your networks into security zones and place those zones into as many DMZ’s as possible.
A more interesting question to be asked is why many of these systems even need to be hooked into the internet. Years ago, they weren’t. And while there may be compelling reasons for SOME of them to be connected, it would seem that many would be infinitely more secure — and immune to cyberattack — if they weren’t.
Do you remember reading about Stuxnet?
First: not being connected to the Internet didn’t protect Natanz from Stuxnet. The software happily traversed the airgap between the Internet and Natanz’s network. Iirc, it did this by infecting USB devices.
There are a number of reasons for devices to have Internet access. From a security perspective, perhaps the most important reason is that anyone who thinks that an airgap will protect them from attack is delusional. It’s better to start with the assumption that you are reachable and plan defenses from there instead of sticking your head in the sand.
Second, updates exist for hardware (drivers), operating systems, and software. Getting software updates and deploying them is harder and more expensive without network access.
Third, most applications are only valuable because they collect information, process it, and return information. Often not all information is collected in-house, and typically the people who need the results aren’t in house either.
Consider a hospital. It’s primary task is care for a human patient. The patient visits a doctor who runs some tests, collects some data and refers the patient to the hospital.
How should the doctor’s valuable patient history be made available to the doctors at the hospital?
1. We could give the patient the original records to give to the hospital. – This is clearly a horrible idea. What if the patient loses them, or gets into an accident, or the place where they store them suffers a disaster of its own?
2. We could send the data via the postal service, as printed pages. – That’s a lot of pages, it’s expensive, and then somehow the information needs to be extracted for easier analysis. Scanning and OCR are typical techniques. Neither is 100% without error, there’s typically data loss and data degradation. Not to mention the risk of the mail being lost, misdirected, or destroyed, and the requirement to get confirmation of receipt.
Are you familiar with RFCs 1149 and 2549? Because solutions like 1 and 2 should sound a little like the scenarios addressed by them.
Further: the physical document / device approach doesn’t prevent attacks (see Anthrax mail attacks), attacks against OCR software (either attacking the OCR software, or getting the OCR software to generate something that would break the next component in the chain).
3. You could replace the postal service with a fax machine based system. This potentially gives you delivery notifications, and reduces the risk of files being lost / destroyed before arriving at the destination. It doesn’t protect against data degradation or attacks on the OCR pipeline.
4. You again consider the RFCs … perhaps it’s best to send actual data instead of printouts of data. You could use the carriers described in the RFCs, but at this point, your system is no longer any more disconnected than Natanz. From a security perspective, you should switch to assuming attackers CAN send data in, and start worrying about what happens when it arrives.
5. OK, so Internet access. How about a firewall?
First, as noted earlier, once you have Internet access, you probably want to be able to update all of your software and devices in order to receive security updates.
Second, hospitals also need to be able to consult with other doctors and send results back to referring physicians.
At this point, you now have roughly equivalent large packets of data being sent and received to and from a large range of arbitrary and seemingly random remote endpoints.
What rules could you write to make your firewall remotely useful? It’ll quickly devolve into Swiss cheese.
There are some things you can try, such as requiring all data be processed by a bulletin board system instead of using email. If people have to create accounts before using the system, and accounts can be audited, and records are tied to user pairs, perhaps you can require doctors to essentially handshake out of band their identifiers. The bulletin board can at least try to scan and audit all data, and pairing accounts might make it harder for a random attacker to send data to an interesting user.
But, if the system is too cumbersome, people will switch to systems equivalent to the aforementioned RFCs.
This doesn’t even begin to address social engineering or Spear phishing.
Obviously there is a need to move from prevent to detect. Ransomcare is our detection solution. Yes we are new and small, but having worked with Ransomware for a few years we believe that we have what the market needs. Up and running in an hour. Low cost and giving an alarm instantly in case of a breakout. This system detects where other fail to protect.
Check http://www.bullwall.com
The very first question has to be: Why are these critical systems even on an exploitable path from the public Internet? Isolate and segregate. Put your email systems and other public-facing systems on an isolated sub-net. Control your environment.
I have to ask: “what if anything was that hospital running for malware protection on the computers that typically receive emailed invoices?” As of last week, I have seen a (Monday – Friday) flood of fake invoices, proposals and airline e-tickets all containing ransomware inside zipfiles (via .wsf exploits), or Office documents (via macros). I am guessing that somebody in the billing department probably opened one on an unprotected PC.
I wonder if it was an economic decision to not have a serious anti-malware product installed, or if somebody disabled what was installed, or they simply forgot to renew their per-seat subscription? Surely, the cleanup or ransom will exceed the cost of a multi-seat business license for a major security program.
Many times those attachments come in as 0 day viruses, and aren’t picked up by Symantec, etc yet. So even if they were running AV it may not have helped them.
FUD
designed to drive us even further into the arms of those who play both ends of the game for fun and profit. In a nutshell, the “hacker” who for whatever reason wants to be tool of the oligarchs, “hacks” and we FUD in response, and allow ever more intrusive erosions of our autonomy and liberty, our equality and fraternity… To the betterment of those who are playing both sides against the middle, we the sheeple. So it just happens that this OS, and that bit of kit, and that app, can keep us just ahead of the game (but still has the secret backdoors for security we all need for our protection from ourselves)
Look at where the money goes, the ransomware happens on both sides of the dilemma… it’s just that the game is massively asymmetric in it’s profit disbursal…
The only way out is completely hack proof networks and devices. And that can be done. Quantum crypto and entanglement teleportation of information is now doable and reasonable…
The price is eternal vigilance of all the players. Not the citizens…
Good luck with that – has it ever occurred to you that the only crime that can be committed in todays universal surveillance state is state sanctioned?
I wonder how this kind of thing is going to change the IT culture in hospitals?
At least in the US, the culture has been really averse to the the risks of changing things. IE6 (cursed be its name) was really hard to get rid of in hospitals, because IT people could get sacked for doing an upgrade, but not for leaving vulnerable software in place.
The problem in a lot of healthcare places is that the doctors are in charge. They generally don’t care about the complexities of other professions besides their own. If there’s a delay fetching a record, the doc complains and the IT head scapegoats somebody.
And, let’s not talk about Internet of Things vulnerabilities, OK? Devices like IV infusion pumps, X-ray machine controllers, pill-dispensers, etc, all are Things on the Internet. So are the printers and fax machines on the units. Let’s not talk about them; too frightening.
not sure i like that my test results can be accessed on a computer where email or lunch browsing occurs. i can see networking the xrays and mris etc to doctors and surgeon vis a having to sneakernet films but outside of billing most computers involved in the care process should be segregated. unless in the OR someone is googling, “how to treat septic bowel”
To be fair, this IS the Grimsby Hospital, that when first opened had a striped carpet in the main area that causes people to faint as walking over it. The joke is if you get run over in the car park, get them to take you to the city 40 miles away to get looked at.
(though I find it odd that last time I was there, they were still using a PICK system on some old IBM mini (or maybe a VAX)). I guess they upgraded to Windows for Workgroups last year.
Sure the FBI tells most about the issues, but remember this is an organization that is in the UK. The first thing they are going to do after all this is call their local police and it will get elevated from there.
I think there is a non profit organization in the UK that have quite a few solutions against ransomware. IF it is ransomware, lets hope the key is available and they can move onward.
Sorry, but hospitals need to be off-limits.
I don’t care if we have to treat every incident like this to be attempted murder multiple counts (how about one for every patient in the hospital).
If other nation states are tied to it, either by actively participating or simply shielding their citizens from extradition then view it the same we would them trying to murder our civilians.
Respond aggressively, even with military options in that case. Make the price so steep for either an individual or another nation that they’d never even think about doing it.
Aha! Finally some group decided that that fun was illegal. Hooray. Now,go find the bugger. Legally convict, and ” hang the pirate out to dry”. Show everyone, and make a big deal out of it. And again and again. Show that there are real world consequences to the bad guys. Right now, it’s a slap on the wrist, stay off the computer for a while, go to work for someone breaking into systems. Actually a reward, and on
I would say that variant attack, is over, holloween, next to look toward all systems, would be vets day in America. So that means a different style of attack parameter, like changing lures to attract?
2 things. Disallow end users saving files locally. NAS units with snapshots only accessible by the local o/s. problem solved.
The irony , just soon after the government makes a budget for cyberwarfare this happens. It looks like a false flag to justify the funding for cyberwarfare, on the cost of human life… disgusting . Theresa May is worse than David Cameron.
Health systems have challenges that most other enterprises do not. They have a large number of staff who are not employees (e.g., contract nurses, medical students, attending physicians, etc., etc.). The usual job sanctions don’t apply.
The clinicians have hundreds of hours of mandatory clinical training. Cyber training is very difficult to fit into the schedule.
Clinicians often have to get lab results, discharge summaries, etc., etc., etc. from other clinicians or clinical entities in the form of PDFs. A big hospital may get hundreds per day. They will click if the results appear to relate to one of their patients. They have to know what the lab tests showed. System integration is still really broken. So the advice about not clicking on pdfs is nice but usually ignored.
Everyone gets that.
But at what point does security start trumping convenience?
If we can’t bring ourselves to do that with human lives hanging in the balance (quite literally it seems) then when the heck is it going to get done?
Nobody is saying that the issue of user negligence can be erased completely or even if so it’ll be done overnight.
But anyone making excuses and not pushing users to be held to a higher standard needs to be held accountable at some point, whether it is the C-suite exec who fosters an atmosphere where information assurance isn’t deemed vital or the end user who just willfully ignores everything you arm them with.
That is where it starts to come around.
It is daunting and it’ll take a while to make the slightest progress but you do it anyways because it’s what we need to do.
http://www.theinquirer.net/inquirer/news/2472495/nhs-trusts-are-still-using-unsupported-windows-xp-pcs
Still using XP at that hospital I wonder?
Sure, the hospitals are forced to use the operating systems loaded by the medical device vendors. Some devices use NT, some use XP, some post manuals on the internet with the hard coded default passwords. Life in health IT is “entertaining”.
See, for example, this: http://www.medpagetoday.com/practicemanagement/informationtechnology/56566