In what’s being billed as an unprecedented global law enforcement response to cybercrime, federal investigators in the United States, United Kingdom and Europe today say they’ve dismantled a sprawling cybercrime machine known as “Avalanche” — a distributed, cloud-hosting network that for the past seven years has been rented out to fraudsters for use in launching countless malware and phishing attacks.
According to Europol, the action was the result of a four-year joint investigation between Europol, Eurojust the FBI and authorities in the U.K. and Germany that culminated on Nov. 30, 2016 with the arrest of five individuals, the seizure of 39 Web servers, and the sidelining of more than 830,000 web domains used in the scheme.
Built as a criminal cloud-hosting environment that was rented out to scammers, spammers other ne’er-do-wells, Avalanche has been a major source of cybercrime for years. In 2009, when investigators say the fraud network first opened for business, Avalanche was responsible for funneling roughly two-thirds of all phishing attacks aimed at stealing usernames and passwords for bank and e-commerce sites. By 2011, Avalanche was being heavily used by crooks to deploy banking Trojans.
The U.K.’s National Crime Agency (NCA), says the more recent Avalanche fraud network comprised up to 600 servers worldwide and was used to host as many as 800,000 web domains at a time.
“Cyber criminals rented the servers and through them launched and managed digital fraud campaigns, sending emails in bulk to infect computers with malware, ransomware and other malicious software that would steal users’ bank details and other personal data,” the NCA said in a statement released today on the takedown. The criminals used the stolen information for fraud or extortion. At its peak 17 different types of malware were hosted by the network, including major strains with names such as goznym, urlzone, pandabanker and loosemailsniffer.At least 500,000 computers around the world were infected and controlled by the Avalanche system on any given day.”
The Avalanche network was especially resilient because it relied on a hosting method known as fast-flux, a kind of round-robin technique that lets botnets hide phishing and malware delivery sites behind an ever-changing network of compromised systems acting as proxies.
“The complex setup of the Avalanche network was popular amongst cybercriminals, because of the double fast flux technique offering enhanced resilience to takedowns and law enforcement action,” Europol said in its statement.
It’s worth noting here that Avalanche has for many years been heavily favored by crime gangs to deploy Zeus and SpyEye malware variants involved in cleaning out bank accounts for a large number of small to mid-sized businesses. These attacks relied heavily on so-called “money mules,” people willingly or unwittingly recruited into helping fraudsters launder stolen funds.
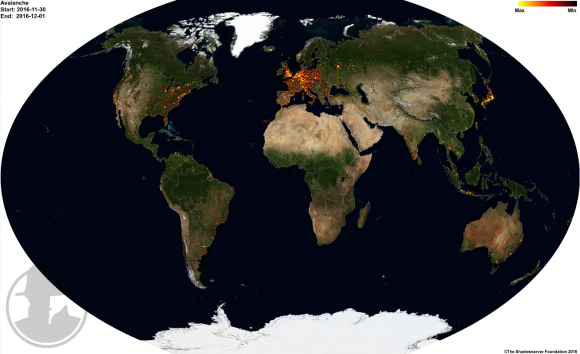
At the time of the takedown, the Avalanche cybercrime infrastructure spanned more than 180 countries, according to The Shadowserver Foundation, a nonprofit group that helped authorities gain control over the Avalanche domains. Read more on Shadowserver’s role in this effort here.
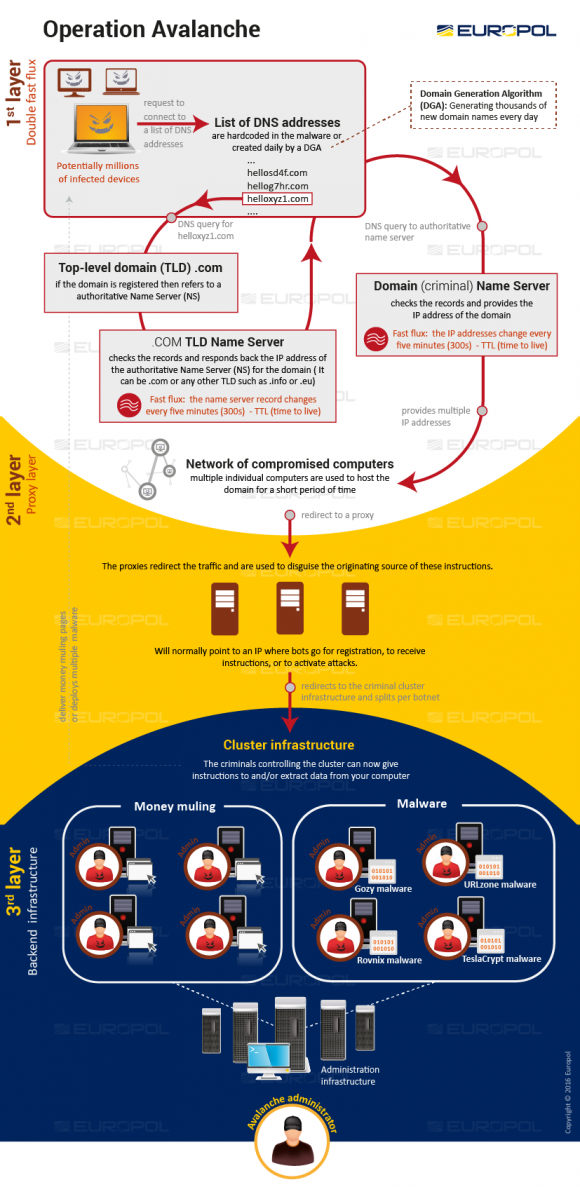
The Avalanche crime infrastructure. Image: Europol




Nitpick: “in the United States, United Kingdom and Europe”
The UK still is part of Europe, the last time I checked.
@Joe….For now, until Brexit is completed.
Brexit much
Last time I checked the UK is leaving the European Union not continent…
derrrp
They drifted out to the Mid-Atlantic, so I guess they’re their own continent.
The UK is a group of islands. Europe is a continent. It’s in any half-decent atlas check it out.
The European continent includes the British islands, Iceland and others. The UK will always be part of Europe, whether you like it or not…
What??? I dont ndestood nothing
Servers cloud ….??? Im old school person.
Someone can explain what hell is here writed here…
Where was crime here ??
Did someone killed someone??
Common people dont undestood anymore nothing!!!
“The criminals used the stolen information for fraud or extortion.”
Huh?
And perhaps that’s part of why they make it so complex, to try and avoid being understood or defeated.
Crimes were thing like identity theft, or draining your bank accounts from stolen passwords.
In the end, you can take away that this joint investigation has shut down a major cybercrime ring.
No need to understand any details to understand that.
Sir, you will understand perfectly after you answer one of their phishing emails or are otherwise negatively affected in your wallet by their malware.
So crimes aren’t crimes unless someone dies? That’s your argument?
What if someone needed to get medical treatment and someone cleaned out his bank account, preventing him from paying for that medical treatment, at which point he died? Is it a crime then?
You’re going to have a hard time getting anything more than laughs or derisive comments with this viewpoint.
Wow – ok so if i leave a banana peel on the sidewalk and someone slips on it cracking open their melon then I can be charged with murder? Sheesh – with all the cause and effect chains going on out there you got me wondering just how many people HAVE I killed?
You can’t leave the house anymore, it seems.
So, on average you wouldn’t be charged w/ 1st degree murder. But you might be eligible for manslaughter, and there’s almost certainly a chance for someone to go after you for civil damages (“wrongful death”).
Here’s an excerpt talking about Roman law [1]:
«An issue which crops up under Roman law (and thus under Continental civil law) is the meaning which needs to be given to the concept of ‘casus’ (‘accident’). Roman-law sources suggest two meanings here. In the first instance, these sources teach, an ‘accident’ refers to some natural phenomenon (‘act of God’), such as a lightning strike, flood, earthquake or compact impact. Further, an ‘accident’ may involve some misfortune, an unfortunate confluence of circumstances or ‘allgemeine Lebensrisiko’.
To figure out the place ‘casus’ occupies under (Roman) private law, let’s revisit my two earlier examples. If a person slips and falls after a heavy rain shower and breaks his leg, that person must bear the risk of his loss. The fact that the person slipped and fell is a risk which everyone runs in daily life. Another party cannot be made to pay for the damage. The situation might be different if an individual slips on a banana peel which was deliberately put on the floor. There is a very good chance in that case that someone else will be liable for the loss suffered. …»
Sadly, finding a good article about throwing bananas in American law seems hard (most articles discuss negligence of the party responsible for maintenance; there are some Books, but copying from them is hard).
Here’s an Australian article [2] indicating that it could be Manslaughter:
«… the example propounded by Smith and Hogan-” of the person who discards a banana peel on the footpath. It is unlawful under the litter laws, and if it is a well-used public footpath. it is dangerous. Therefore, the authors conclude, it will be manslaughter by unlawful and dangerous act if someone slips on the banana peel and is killed in the fall. …»
The US, Canada, and Australia are all Common Law. It isn’t unreasonable for a Judge to reach a similar conclusion in these countries.
[1] http://link.springer.com/chapter/10.1007/978-3-319-26300-7_13/fulltext.html
[2] http://www.austlii.edu.au/au/journals/SydLawRw/1974/4.pdf
Very educational, Brian. And great news about the bust. This should create a little healthy paranoia for online scammers everywhere. I wish we had the motivation to use tech as well as the scammers do. Then we might consider news like this to be less surprising.
I think “kuzjo” understands what this post is about very well. Why else would he even be here…? E-hay eeks-spay ommon-k am-mer-spay! Recognize it not you do. I’m disappointed that so many would take his post at face value. *sigh*
As my Grandpappy used to say, “Couldn’t have happened to a nicer bunch of guys.” He was big on sarcasm. Well, you had to be there.
Now if only Europol, would only go after the scumbag scammers in India, Pakistan and Bangladesh,
Maybe those darn numismatics as well. Those guys are DANGEROUS!
I can’t believe no one’s mentioned the philatelists yet!
And let’s not forget the oenophiles!
Well, none of those places are in Europe so they might have a difficult time since they don’t actually have any jurisdiction there.
Brian, there a book here to be written, a-la Spam Nation
Great read as always Brian, appreciate the work
I loved spam nation & happy to see it are up running again…u are a wonderful teacher…tnx bjb
Thank You for keeping everyone up-to-date on everything.
So fishing is illegal. Who would have guessed. Now, the punishment after conviction. Slap on the wrist? A job with government fishing services? But this was just the server group. Kinda like the post office, bring all the ads? Fishing for sales, nothing illegal yet, but now, did they catch Anny of the “mailers” of the illegal stuff? Hope they are getting closer.
Probably their Phishing license just expired and the government wants them to buy a new one, with the appropriate baksheesh attached. Might not hurt to get new Phishing gear, including a new Trolling motor.
It is good to see police are working to stop some of these internet thieves. It is even better to see there is some success. Thanks Brian for reporting the good news as well as the bad news.
You have a most unusual business model and tremendous courage.
Five people and 39 servers… Geez.
I’m in the wrong business.
So let’s break this down:
Avalanche existed for seven years. It took the Authorities four years of those seven to take Avalanche down. So Avalanche went undetected for three years even though there were huge numbers of compromised domains under its control.
Why did it take the Authorities so long to act on this? And when the Authorities finally did act, why did it take them four long years to stop this, especially when there were only five people controlling just 39 servers?
If this is the Multi-National Government entity that’s supposed to be protecting us when the “Big” one comes – we’re in for deep trouble.
I have a slightly more optimistic view. I have no doubt whatsoever that national borders and jurisdictions played a bit part in slowing this down. They could probably figure out the technical side in months. Over time this kind of cooperation should get easier as every country realises it’s in their interests.
– Coming to you from the mid-atlantic. Pretty sure Nigel Farage is his own in-continent.
The problem with knee-jerk reactions is you rarely do things right.
They have to actually catch the people behind the ring, not just shut down their servers. The people will just regain control of the botnet and start over if you don’t catch them.
It takes time to do things right. Doing things quickly normally results in lousy results (which you would be complaining about) and more work overall since you have to start over from scratch with the new setup.
I love reading your articles. Thank you! Please be so kind and if you can, find a responsive theme for the website. It is so painful to read on a mobile.
Using the current version of Chrome for Android, I can request desktop site and the text flows nicely.
Some mobile browsers have “reader” modes, but I can’t find that mode in chrome://flags today 🙁
Amen
US-CERT incidentally issued an advisory on this only yesterday!
https://www.us-cert.gov/ncas/alerts/TA16-336A
Only 5 arrests?:-( I heard private prison shares are up?)
I monitor the amount of spam coming in to my email accounts. There are a couple of them that are really old and I used them for a lot of other websites back in the day, so they get a steady stream of the usual spam. I have noticed the last week or so they are getting hardly any spam compared to what they were getting, say, a couple of months ago. I wonder if this is related. Anyone else notice the same thing?
I’ve noticed a wild fluctuation in the amount of spam going to my junk accounts. I would not be surprised if a lot of this was completely automated, so the crooks could concentrate on not being apprehended while their business drove on. They have so many backup plans to the server farms, that it would be extremely difficult to stamp them all out totally. Many of the command and control servers are only hosted for three months at a time; so even the backup CAC hosting changes radically. I wouldn’t be surprised if some of those had automated commands set on a timer in case the “administrator” was out to “lunch”.
I’d like to take this post as an opportunity to give kudos to Brian’s illustrative chart in this article – it is a great chalk board to the high-jinks of the crooks!
This is good news.
That entire domain generation / fast-flux / reverse proxy system seems identical to that used by the Spamit rogue pharmacy affiliate program, and somewhat similar to what EvaPharmacy is still using today to host their rogue pharmacy and fake Rolex / replica websites.
I’d like to think that it was all part of the same operation(s) but I have my doubts. After Spamit shut down all the tech people behind it were still freelancers for anyone with this kind of malicious intent.
Still: good to see action being taken.
SiL / IKS / concerned citizen
I recommend the death penalty for these 5 scums. If we do that, the Internet will suddenly become a much better place.
Anybody find the lack of fraudulent servers in China and Russia disconcerting?
If you check the shadowserver article (link Avalanche) you can see servers in both China and Russia.
We will be publishing more supporting information in the coming days, but here are some initial statistics:
Jurisdictions: 30
Arrests: 5
Premises searched: 37
Servers seized: 39
Servers taken offline through abuse reports: 221
Countries with victim IP’s: Over 180
Domains blocked or delegated to Shadowserver’s sinkholes: Over 800,000 in over 60 Top-Level-Domain‘s (TLD’s)
According to local news in Ukraine, this one who was arrested yesterday with shooting – released by local court -)
Agree with Traian. This is painful to read on a mobile. Pls react
Thank you so much for the article on the Avalanche bust. A lot of bad guys are out of business at least for now. I hope they all get caught (if they haven’t already) and pay a penalty for the harm they’ve done to so many people.
So did the Ukrainians really botch their charges on the suspected ring leader? Not much out there on how this is unfolding. https://www.bleepingcomputer.com/news/security/judge-releases-avalanche-network-leader-despite-police-shootout/
Norton Security Full Version Free
Norton Protection Common offers thorough defense from online dangers to preserve your pc, your identification and fiscal details protected against cybercrime. In contrast to free of charge contra–infection application together with other security solutions, Norton leverages our global hazard intelligence and advanced technological innovation to eliminate and find dangers-the entirely new ones.
Receive the complete variation free of charge here:
www.zippyshare.com/v/jqeF4Cdj/file.html