Addressing distributed denial-of-service (DDoS) attacks designed to knock Web services offline and security concerns introduced by the so-called “Internet of Things” (IoT) should be top cybersecurity priorities for the 45th President of the United States, according to a newly released blue-ribbon report commissioned by President Obama.
 “The private sector and the Administration should collaborate on a roadmap for improving the security of digital networks, in particular by achieving robustness against denial-of-service, spoofing, and other attacks on users and the nation’s network infrastructure,” reads the first and foremost cybersecurity recommendation for President-elect Donald Trump. “The urgency of the situation demands that the next Administration move forward promptly on our recommendations, working closely with Congress and the private sector.”
“The private sector and the Administration should collaborate on a roadmap for improving the security of digital networks, in particular by achieving robustness against denial-of-service, spoofing, and other attacks on users and the nation’s network infrastructure,” reads the first and foremost cybersecurity recommendation for President-elect Donald Trump. “The urgency of the situation demands that the next Administration move forward promptly on our recommendations, working closely with Congress and the private sector.”
The 12-person, non-partisan commission produced a 90-page report (PDF) and recommended as their very first action item that the incoming President “should direct senior federal executives to launch a private–public initiative, including provisions to undertake, monitor, track, and report on measurable progress in enabling agile, coordinated responses and mitigation of attacks on the users and the nation’s network infrastructure.”
The panel said this effort should build on previous initiatives, such as a 2011 program by the U.S. Department of Commerce called the Industry Botnet Group.
“Specifically, this effort would identify the actions that can be taken by organizations responsible for the Internet and communications ecosystem to define, identify, report, reduce, and respond to attacks on users and the nation’s network infrastructure,” the report urged. “This initiative should include regular reporting on the actions that these organizations are already taking and any changes in technology, law, regulation, policy, financial reimbursement, or other incentives that may be necessary to support further action—while ensuring that no participating entity obstructs lawful content, applications, services, or nonharmful devices, subject to reasonable network management.”
The report spans some six major imperatives, including 16 recommendations and 63 associated action items. The second major imperative focuses on IoT security concerns, and urges the federal government and private industry to embark upon a number of initiatives to “rapidly and purposefully to improve the security of the Internet of Things.”
“The Department of Justice should lead an interagency study with the Departments of Commerce and Homeland Security and work with the Federal Trade Commission, the Consumer Product Safety Commission, and interested private sector parties to assess the current state of the law with regard to liability for harm caused by faulty IoT devices and provide recommendations within 180 days,” the panel recommended. “To the extent that the law does not provide appropriate incentives for companies to design security into their products, and does not offer protections for those that do, the President should draw on these recommendations to present Congress with a legislative proposal to address identified gaps, as well as explore actions that could be accomplished through executive order.”
Meanwhile, Morning Consult reports that U.S. Federal Communications Commission Chairman Tom Wheeler has laid out an unexpected roadmap through which the agency could regulate the security of IoT devices. The proposed certification process was laid out in a response to a letter sent by Sen. Mark Warner (D-Va.) shortly after the IoT-based attacks in October that targeted Internet infrastructure company Dyn and knocked offline a number of the Web’s top destinations for the better part of a day.
Morning Consult’s Brendan Bordelon notes that while Wheeler is set to step down as chairman on Jan. 20, “the new framework could be used to support legislation enhancing the FCC’s ability to regulate IoT devices.”
ANALYSIS
It’s nice that this presidential commission placed a special emphasis on IoT and denial-of-service attacks, as these two threats alone are clear and present dangers to the stability of e-commerce and free expression online. However, this report overall reads very much like other blue-ribbon commission reports of years past: The recommendations eschew new requirements in favor of the usual calls for best practices, voluntary guidelines, increasing industry-government information sharing, public/private partnerships, and public awareness campaigns.
One recommendation I would like to have seen in this report is a call for federal legislation that requires U.S.-based hosting providers to block spoofed traffic from leaving their networks.
As I noted in a November 2015 story, The Lingering Mess from Default Insecurity, one major contributor to the massive spike in denial-of-service attacks over the past few years is that far too many ISPs and hosting providers allow traffic to leave their networks that did not originate there. Using well-known attack techniques known as traffic amplification and reflection, an attacker can “reflect” his traffic from one or more third-party machines toward the intended target.
In this type of assault, the attacker sends a message to a third party, while spoofing the Internet address of the victim. When the third party replies to the message, the reply is sent to the victim — and the reply is much larger than the original message, thereby amplifying the size of the attack. According to the latest DDoS report from Akamai, more than half of all denial-of-service attacks in the third quarter of 2016 involved reflection and spoofing.
One basic step that many ISPs and hosting providers can but apparently are not taking to blunt these spoofing attacks involves a network security standard that was developed and released more than a dozen years ago. Known as BCP38, its use prevents abusable resources on an ISP’s network from being leveraged in denial-of-service. BCP38 is designed to filter such spoofed traffic, so that the reflected traffic from the third party never even traverses the network of an ISP that’s adopted the anti-spoofing measures.
However, there are non-trivial economic reasons that many ISPs fail to adopt this best practice. This blog post from the Internet Society does a good job of explaining why many ISPs decide not to implement BCP38. Ultimately, it comes down to cost and to a fear that adoption of this best practice will increase costs and prompt some customers to seek out providers that do not enforce this requirement. In some cases, U.S.-based hosting providers that allow spoofing/reflection have been sought out and recommended among miscreants involved in selling DDoS-for-hire services.
In its Q3 2016 State of the Internet report, Akamai notes that while Chinese ISPs occupy the top two sources of spoofed traffic, several large U.S.-based providers make a showing here as well:
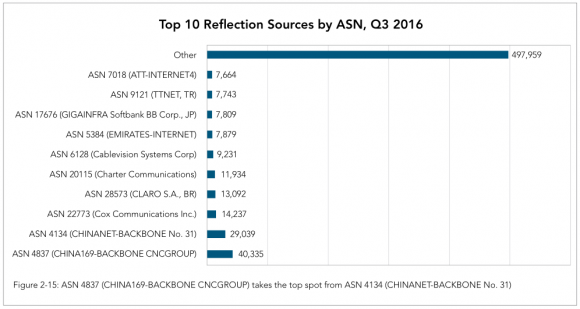
Image: Akamai.
It is true that requiring U.S. hosting providers to block spoofing would not solve the spoofing problem globally. But I believe it’s high time that the United States led by example in this arena, if only because we probably have the most to lose by continued inaction. According to Akamai, more than 21 percent of all denial-of-service attacks originate from the United States. And that number has increased from 17 percent a year ago, Akamai found. What’s more, the U.S. is the most frequent target of these attacks, according to DDoS stats released this year by Arbor Networks.




The 12-person, non-partisan commission creates a 90 page report and nothing will change.
More than likely; that activity licked off in 2011 (5 yrs ago now!) to study what looks like the same thing (if not an affiliated issue) sure has paid off too.
The panel said this effort should build on previous initiatives, such as a 2011 program by the U.S. Department of Commerce called the Industry Botnet Group.
The number one priority for the incoming “president” will be self-enrichment. Unless it’s plated in gold or wearing a skirt, Mr Sweet Potato Head can’t focus on it for more than a few seconds.
“…according to a newly released blue-ribbon report commissioned by President Obama.”
If anyone should know, it should be Obama. This incompetent excuse for a president presided over the WORST cyber security breaches of the Federal government in history. Now he wants to tell an incoming administration what they need to do. That’s rich!
Almost as rich as your delusional drivel.
He inherits a system that is pathetic, at-best, and actually tries to enact change but is met with stiff resistance from a do-nothing Congress yet it is all on him lol.
75% of all government IT budgets are spent maintaining legacy tech. It has been that way since the internet began.
Facilitating institutional change takes years.
I would also like to note that those breaches you refer to happened because of contractors.
You know, those “can’t go wrong and soooo much better than the gummint” guys the budget slashing Congress shoved down our throats.
More than half of the population responded with disapproval of Obama’s policies this election. His cavalier attitude in the IT field is a small part of that disapproval. The bottom line is: NO president can be excused for a lax defensive posture concerning the country because that is part of his job description. It happened on his watch and he is culpable. It is worth noting that the entire electrical grid is at risk and he has not seen fit to push for that fix either, even though it would cost a pittance compared to all those “shovel ready jobs” he saw fit to blow billions on. What has Obama done to rectify the situation? NOTHING except tell the new president he should be responsible, and correct the security problems exposed on Obama’s watch. Now, the new president inherits Obama’s mess well after the damage is done.
Obama is incompetent and remains so to this day.
You immediately display your ignorance when you start with a line that claims more than half the population showed their disapproval of Obama in the election. Less than half the population of the country even voted. And Donald Trump received less than half of those votes. Less than 20% of the United States population voted for him. If you cull that to only those 18 years of age and over, you still only get around 25% of the population.
Plus, if anyone is waiting on the government to do the common sense/intelligent/right thing when it comes to technology or cybersecurity, you might as well be a dog barking at a tree waiting for the tree to get out of your way. You’re asking a group of people who’s average age ranges from 57 (Congress) to 62 (Senate). Any of you tried to get your parents or grandparents to even install anti-virus on their PCs?
And ultimately, there’s a reason Congress’ approval rating has been abysmally low: it’s predominantly a bunch of old, self-interested people who would rather point the finger at the other guy and say “He’s not doing his job!” than any sort of ACTUAL governing body.
Half of this comment chain is “Obama didn’t” this and “Trump won’t” that. People need to come to terms with the fact that, in a world of 24 hour news cycles where facts are now based on how people feel rather than on actual data, government is and will remain completely ineffective. You could put a German Shepard in the White House and you’ll get the same amount accomplished.
let’s hope we do get a dog in the White House. Last time I checked, my dog was pretty useful for the amount I pay her.
51% of the public voted against Trump; they were just not scattered around correctly for an electoral college victory.
This article should have “Donald Trump” in every sentence. Krabs, keep up with the rest of the media!
In seriousness, nice article. I like seeing content on gov. involvement in teh interwebz.
Fireeye will get lots of revenue from this!
Jim
Not only FireEye, all those front runners in cyber security business will benefit.
While the spending may be a justified one and though we cant squarely blame those cyb-sec companies of ineffectiveness, My regret is that the end result is almost the same every time a breach happens.
Unless ALL those involved show involvement and commitment, the Government & Companies will keep on spending the money of tax payers / share holders and the cyber criminals will keep on stealing.
@Jim – FireEye don’t make ISP scale devices. Their largest appliance will only do 8 Gbps of IPS
Brian
This has reference to your reply to me on my comment in the Deutsche Telekom post. I think even if the incoming President formulates guidelines, implementing those guidelines will be in the hands of ISPs and other related companies right up to the end user companies.
But, if these companies are not willing to follow the guidelines – due to various reasons, mainly financial – then nothing will happen. It seems if they do then I think most – though not all – of these attacks can be repulsed. Are they able but not willing OR willing but not able?
According to an article in CSOONLINE, (http://csoonline.com/article/3146122/compliance/whos-responsible-for-data-compliance-25-of-executives-dont-know.html) 47% of senior & C-Level executives are unsure which level of data compliance standards apply to their organizations.
You can take a horse to the creek to drink, but you can’t make it drink.
Why wasn’t it a priority for the 44th prez? Perhaps that famous desk sign now reads, “The buck no longer stops here.”
“…nonharmful devices…”
Who determines what is nonharmful and what isn’t…..and based on what criteria? There isn’t a single device, machine, or connection anywhere on the internet that could not by defined as harmful in some way.
The online advertising industry is so blatantly obvious in how harmful it is and no one will ever consider it to be a threat. Atleast no one that will ever be part of this ‘blue-ribbon panel’. Infact, advertising will be promoted, held in high regard, and lauded as crucial to IT development.
Will IoT be seen as ‘harmful’? I doubt it will by this ‘blue-ribbon panel’.
Will the commander and chief see ‘harmful’ in purposely having his military be hacked by anyone (including the enemy)?
lmao….people worry so much about Obama, Clinton, Trump, Reagan, or Bush with access to the nuclear button while completely ignoring the back doors intentionally put in that allow any enemy smart enough into the system.
Will it ever really be considered ‘harmful’ to allow high ranking government officials to use Ashley Madison?
—————————-
The result will more likely be that whatever is considered ‘harmful’ will actually be the end user (the mass populous) the ability to think and decide for themselves what is best for their lives.
Brian,
Everyone is missing the boat on the IoT debate. While I agree a byproduct of the real issue – device insecurity – is DDoS attacks, the real problem is the fact that vendors don’t provide basic security protections for IoTs and IP enabled industrial controls. I lump these two technologies together, because IoTs like IP enabled industrial controls are devices that use IP communication as an ancillary service – and are usually implemented in on a traditional hardware device.
We really should be focus on “product safety” and not “product security.” There are many instances in Hospitals where IoTs or IP enabled industrial controls are wide open and don’t have basic security mechanisms. When approached, vendors continuously contend that these devices were not built with security in mind, are legacy systems and security controls could crash the system.
While that may be a legitimate excuse it’s no longer acceptable. A year ago, the FDA released an alert that a certain insulin pump should taken out of service because it could be hacked – giving the hacker the ability to change insulin levels remotely. That’s a product safety issue not a security issue.
That example is only the tip of the iceberg. Many devices in hospitals, utilities and other industries are woefully insecure. The IoT issue has only highlighted how many devices are secure. Like seat belts and break lights for cars, IoT devices should have a basic level of security – it’s a product safety issue. Regardless how it’s done, vendors’ feet must be held to the fire to bake device security into its product.
Is there any legitimate use for reflection/spoofed traffic?
I don’t know the answer to that. But if not I think they (Congressional bill, not FCC) should set a deadline for implementation of the standard that blocks that. That bill should have “teeth” to it: That is, it should mandate that ISPs operating in the USA not permit their users to access content of any ISP(domestic or foreign) who have not implemented the protocol. My suggestion is based on certain assumptions, but without teeth of some type for non-implementation it won’t go anywhere.
90 pages? For a person who deals with 140 characters at a time? Get real!
Bruce, are f’real? C’mon man, be an adult and learn how delegating authority works. (IF you ever get into a management position and out of an “individual contributor” job that is.)
Brian Krebs should have been a principal member of that blue-ribbon committee. It’s really too bad that he wasn’t.
Yes.
with the greatest of respect, Brian should fix the headline , even if it has to be gutted. The headline is misleading.
“DDoS, IoT Top Cybersecurity Priorities for 45th President” is totally wrong. clickbait.
Obama spouting at Trump does not make it fact.
Why does it nowhere mention producer´s liability for commercial software vendors?
If the industry does not take care of their products, make them pay! Isn´t the US THE country in the world, famous for exactly that?
Why does it nowhere mention producer´s liability for commercial software vendors?
If the industry does not take care of their products, make them pay! Isn´t the US THE country in the world, famous for exactly that?
So, a recommendation for the next president?
The real question is: why has not already been any action in this area by the government?
it’s a lot easier to tell someone what to do than do it yourself?
it shifts future, and even current, blame?
all the above?
I agree with you, and what bugs me most of all is that the headline “DDoS, IoT Top Cybersecurity Priorities for 45th President” seems click-bait at worst, and at best wrong.
the article itself doesn’t say Trump has it as a priority.
what the article says is Obama is telling Trump it SHOULD be a priority.
so the headline is wrong. clickbait.
Nearly fake news. No?
This “liberty” that publishers of content take is part of the dumbing down.
Again, “DDoS, IoT Top Cybersecurity Priorities for 45th President” is wrong. DDoS, IoT Top Cybersecurity *ARE NOT* Priorities for 45th President.
Might be. Might not be. But for the headline to read that is wrong.
Have there been instances of DNS registrars being DDoS’d? I’ve been taking steps to implement multi-DNS providers (Ultra and Dyn) but I am concerned that’ll be all for naught is the Registrar with the SOA records gets DDoS’d. Are my fears valid?
So many attacks in the news at the moment, I know its this time of year and loads of people are online with it being near christmas, but is it me, or are we seeing more online attacks now then ever before?
Wow, it appears some number of your readers are still heavily impacted by the recent election, and cannot offer any valuable comments or insight to further this interesting and critical topic. Let me try to be more constructive:
I tend to support a government that offers research, guidance, awareness, and education to the otherwise uninformed citizenry. So anything that helps people understand the threats, advises them on ways to minimize risks and deal with impacts, and reports on who behaves well and who doesn’t is a good thing IMHO. I am not fond of Brian’s suggestion “One recommendation I would like to have seen in this report is a call for federal legislation that requires U.S.-based hosting providers to block spoofed traffic from leaving their networks.”. Let each of them decide what is best, but let us know who is helping deal with the problem and who is making matters worse. Then we can either decide to use that information to our benefit or ignore it to our peril.
Centralized control over stuff has never (in all history) turned out better than letting people have more control over actions and outcomes. Yes, defense and a few other things need to be managed by the government, but forcing entities to do the right thing imposes requirements on that central authority that are *never* fulfilled at all or at least not very often. IMHO anything that informs us, educates us, then puts us in control is a good thing. Anything that tries to control us is bad.
In this case if spoofed traffic were kept from entering the network we would not have as large a problem. This is a technical issue, not a political issue. It is so simple it is ridiculous to debate it.
A simple fix is there, all they have to do is implement it.
No spoofed traffic should be the policy for all ISP’s.
And all network admins too!
Next target ====> VPN’s <==== that host attack traffic.