WikiLeaks on Tuesday dropped one of its most explosive word bombs ever: A secret trove of documents apparently stolen from the U.S. Central Intelligence Agency (CIA) detailing methods of hacking everything from smart phones and TVs to compromising Internet routers and computers. KrebsOnSecurity is still digesting much of this fascinating data cache, but here are some first impressions based on what I’ve seen so far.
First, to quickly recap what happened: In a post on its site, WikiLeaks said the release — dubbed “Vault 7” — was the largest-ever publication of confidential documents on the agency. WikiLeaks is promising a series of these document caches; this first one includes more than 8,700 files allegedly taken from a high-security network inside CIA’s Center for Cyber Intelligence in Langley, Va.
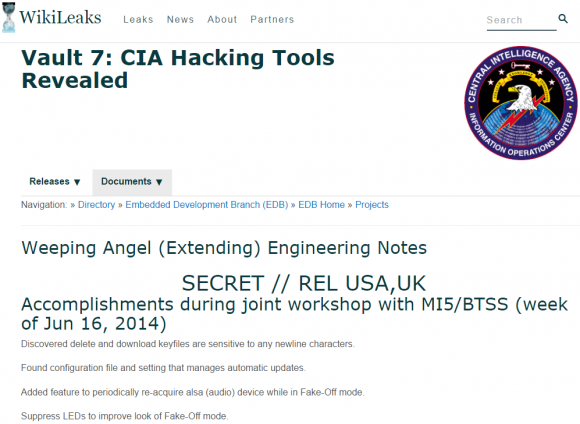
The home page for the CIA’s “Weeping Angel” project, which sought to exploit flaws that could turn certain 2013-model Samsung “smart” TVs into remote listening posts.
“Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized ‘zero day’ exploits, malware remote control systems and associated documentation,” WikiLeaks wrote. “This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA. The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.”
Wikileaks said it was calling attention to the CIA’s global covert hacking program, its malware arsenal and dozens of weaponized exploits against “a wide range of U.S. and European company products, includ[ing] Apple’s iPhone, Google’s Android and Microsoft’s Windows and even Samsung TVs, which are turned into covert microphones.”
The documents for the most part don’t appear to include the computer code needed to exploit previously unknown flaws in these products, although WikiLeaks says those exploits may show up in a future dump. This collection is probably best thought of as an internal corporate wiki used by multiple CIA researchers who methodically found and documented weaknesses in a variety of popular commercial and consumer electronics.
For example, the data dump lists a number of exploit “modules” available to compromise various models of consumer routers made by companies like Linksys, Microtik and Zyxel, to name a few. CIA researchers also collated several pages worth of probing and testing weaknesses in business-class devices from Cisco, whose powerful routers carry a decent portion of the Internet’s traffic on any given day. Craig Dods, a researcher with Cisco’s rival Juniper, delves into greater detail on the Cisco bugs for anyone interested (Dods says he found no exploits for Juniper products in the cache, yet). Meanwhile, Cisco has published its own blog post on the matter.
WHILE MY SMART TV GENTLY WEEPS
Some of the exploits discussed in these leaked CIA documents appear to reference full-on, remote access vulnerabilities. However, a great many of the documents I’ve looked at seem to refer to attack concepts or half-finished exploits that may be limited by very specific requirements — such as physical access to the targeted device.
The “Weeping Angel” project’s page from 2014 is a prime example: It discusses ways to turn certain 2013-model Samsung “smart TVs” into remote listening devices; methods for disabling the LED lights that indicate the TV is on; and suggestions for fixing a problem with the exploit in which the WiFi interface on the TV is disabled when the exploit is run.
ToDo / Future Work:
Build a console cableTurn on or leave WiFi turned on in Fake-Off mode
Parse unencrypted audio collection
Clean-up the file format of saved audio. Add encryption??
According to the documentation, Weeping Angel worked as long as the target hadn’t upgraded the firmware on the Samsung TVs. It also said the firmware upgrade eliminated the “current installation method,” which apparently required the insertion of a booby-trapped USB device into the TV.
Don’t get me wrong: This is a serious leak of fairly sensitive information. And I sincerely hope Wikileaks decides to work with researchers and vendors to coordinate the patching of flaws leveraged by the as-yet unreleased exploit code archive that apparently accompanies this documentation from the CIA.
But in reading the media coverage of this leak, one might be led to believe that even if you are among the small minority of Americans who have chosen to migrate more of their communications to privacy-enhancing technologies like Signal or WhatsApp, it’s all futility because the CIA can break it anyway.
Perhaps a future cache of documents from this CIA division will change things on this front, but an admittedly cursory examination of these documents indicates that the CIA’s methods for weakening the privacy of these tools all seem to require attackers to first succeed in deeply subverting the security of the mobile device — either through a remote-access vulnerability in the underlying operating system or via physical access to the target’s phone.
As Bloomberg’s tech op-ed writer Leonid Bershidsky notes, the documentation released here shows that these attacks are “not about mass surveillance — something that should bother the vast majority of internet users — but about monitoring specific targets.”
By way of example, Bershidsky points to a tweet yesterday from Open Whisper Systems (the makers of the Signal private messaging app) which observes that, “The CIA/Wikileaks story today is about getting malware onto phones, none of the exploits are in Signal or break Signal Protocol encryption.”
The company went on to say that because more online services are now using end-to-end encryption to prevent prying eyes from reading communications that are intercepted in-transit, intelligence agencies are being pushed “from undetectable mass surveillance to expensive, high-risk, targeted attacks.”
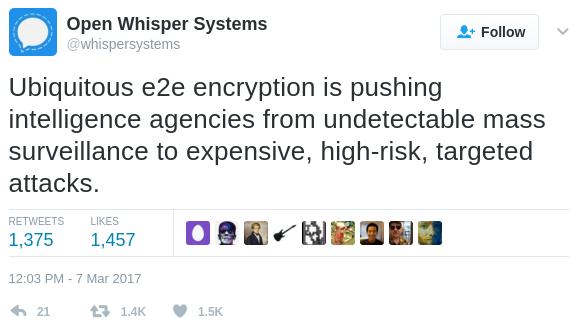
A tweet from Open Whisper Systems, the makers of the popular mobile privacy app Signal.
As limited as some of these exploits appear to be, the methodical approach of the countless CIA researchers who apparently collaborated to unearth these flaws is impressive and speaks to a key problem with most commercial hardware and software today: The vast majority of vendors would rather spend the time and money marketing their products than embark on the costly, frustrating, time-consuming and continuous process of stress-testing their own products and working with a range of researchers to find these types of vulnerabilities before the CIA or other nation-state-level hackers can.
Of course, not every company has a budget of hundreds of millions of dollars just to do basic security research. According to this NBC News report from October 2016, the CIA’s Center for Cyber Intelligence (the alleged source of the documents discussed in this story) has a staff of hundreds and a budget in the hundreds of millions: Documents leaked by NSA whistleblower Edward Snowden indicate the CIA requested $685.4 million for computer network operations in 2013, compared to $1 billion by the U.S. National Security Agency (NSA).
TURNABOUT IS FAIR PLAY?
NBC also reported that the CIA’s Center for Cyber Intelligence was tasked by the Obama administration last year to devise cyber attack strategies in response to Russia’s alleged involvement in the siphoning of emails from Democratic National Committee servers as well as from Hillary Clinton‘s campaign chief John Podesta. Those emails were ultimately published online by Wikileaks last summer.
NBC reported that the “wide-ranging ‘clandestine’ cyber operation designed to harass and ’embarrass’ the Kremlin leadership was being lead by the CIA’s Center for Cyber Intelligence.” Could this attack have been the Kremlin’s response to an action or actions by the CIA’s cyber center? Perhaps time (or future leaks) will tell.
Speaking of the NSA, the Wikileaks dump comes hot on the heels of a similar disclosure by The Shadow Brokers, a hacking group that said it stole malicious software from the Equation Group, a highly-skilled and advanced threat actor that has been closely tied to the NSA.
What’s interesting is this Wikileaks cache includes a longish discussion thread among CIA employees who openly discuss where the NSA erred in allowing experts to tie the NSA’s coders to malware produced by the Equation Group. As someone who spends a great deal of time unmasking cybercriminals who invariably leak their identity and/or location through poor operational security, I was utterly fascinated by this exchange.
BUG BOUNTIES VS BUG STOCKPILES
Many are using this latest deluge from WikiLeaks to reopen the debate over whether there is enough oversight of the CIA’s hacking activities. The New York Times called yesterday’s WikiLeaks disclosure “the latest coup for the antisecrecy organization and a serious blow to the CIA, which uses its hacking abilities to carry out espionage against foreign targets.”
The WikiLeaks scandal also revisits the question of whether the U.S. government should instead of hoarding and stockpiling vulnerabilities be more open and transparent about its findings — or at least work privately with software vendors to get the bugs fixed for the greater good. After all, these advocates argue, the United States is perhaps the most technologically-dependent country on Earth: Surely we have the most to lose when (not if) these exploits get leaked? Wouldn’t it be better and cheaper if everyone who produced software sought to crowdsource the hardening of their products?
On that front, my email inbox was positively peppered Tuesday with emails from organizations that run “bug bounty” programs on behalf of corporations. These programs seek to discourage the “full disclosure” approach — e.g., a researcher releasing exploit code for a previously unknown bug and giving the affected vendor exactly zero days to fix the problem before the public finds out how to exploit it (hence the term “zero-day” exploit).
Rather, the bug bounties encourage security researchers to work closely and discreetly with software vendors to fix security vulnerabilities — sometimes in exchange for monetary reward and sometimes just for public recognition.
Casey Ellis, chief executive officer and founder of bug bounty program Bugcrowd, suggested the CIA WikiLeaks disclosure will help criminal groups and other adversaries, while leaving security teams scrambling.
“In this mix there are the targeted vendors who, before today, were likely unaware of the specific vulnerabilities these exploits were targeting,” Ellis said. “Right now, the security teams are pulling apart the Wikileaks dump, performing technical analysis, assessing and prioritizing the risk to their products and the people who use them, and instructing the engineering teams towards creating patches. The net outcome over the long-term is actually a good thing for Internet security — the vulnerabilities that were exploited by these tools will be patched, and the risk to consumers reduced as a result — but for now we are entering yet another Shadow Brokers, Stuxnet, Flame, Duqu, etc., a period of actively exploitable 0-day bouncing around in the wild.”
Ellis said that — in an ironic way, one could say that Wikileaks, the CIA, and the original exploit authors “have combined to provide the same knowledge as the ‘good old days’ of full disclosure — but with far less control and a great many more side-effects than if the vendors were to take the initiative themselves.”
“This, in part, is why the full disclosure approach evolved into the coordinated disclosure and bug bounty models becoming commonplace today,” Ellis said in a written statement. “Stories like that of Wikileaks today are less and less surprising and to some extent are starting to be normalized. It’s only when the pain of doing nothing exceeds the pain of change that the majority of organizations will shift to an proactive vulnerability discovery strategy and the vulnerabilities exploited by these toolkits — and the risk those vulnerabilities create for the Internet — will become less and less common.”
Many observers — including a number of cybersecurity professional friends of mine — have become somewhat inured to these disclosures, and argue that this is exactly the sort of thing you might expect an agency like the CIA to be doing day in and day out. Omer Schneider, CEO at a startup called CyberX, seems to fall into this camp.
“The main issue here is not that the CIA has its own hacking tools or has a cache of zero-day exploits,” Schneider said. “Most nation-states have similar hacking tools, and they’re being used all the time. What’s surprising is that the general public is still shocked by stories like these. Regardless of the motives for publishing this, our concern is that Vault7 makes it even easier for a crop of new cyber-actors get in the game.”
This almost certainly won’t be the last time KrebsOnSecurity cites this week’s big CIA WikiLeaks trove. But for now I’m interested to hear what you, Dear Readers, found most intriguing about it? Sound off in the comments below.




We’ve got a national debt that is probably beyond ever fixing, a healthcare system that is completely out of control, unemployment rates going up, country tearing itself apart, yet we still find ways to spend billions of dollars per year within our security agencies and it ends up being leaked out. That to me is intriguing. The CIA is in the business of doing clandestine investigations, yet they can’t even protect themselves. They’re probably monitoring this right now and will show up at my door soon 🙂 All I can say is the crazies are running the asylum.
somebody went bad – not much technically you can do about that problem…
Great article as always Brian, well researched and well written. It will be interesting to see what the fall-out will be from all of this.
Weeping Angel makes for some interesting and worrying reading.
Unfortunately, whatever your politics are, this is going to hurt a lot of regular companies and consumers because, as you note, a large number of zero-days will result or worse, in many cases no patches available at all ever.
Can I even trust my electric toothbrush?
Any one know where I can get a zip file of the whole C.I.A. leaked database?
arstechnika has a link
Somebody needs to upload it to Mega.nz and provide links for download
what goes around comes around….when will people learn that connecting implies risk and you just can’t ignore it.
Profound quote: “…when the pain of doing nothing exceeds the pain of change…” I will be able to use that one. Thanks Brian, good article.
OK, if you can assess the tipping point.
Wow, this is a very big deal!
From a brief review of Wikileaks yesterday I was shocked to learn that the CIA purposely chose to make the code for weaponizing zero-day exploits unclassified information – meaning anybody with access could legally copy or clone the software and put it to use. Now, we’ll have to see if that code sees the light of day on Wikileaks. Not that the actors couldn’t be held accountable for the damage caused by using an exploit, but they could not be prosecuted for simply using the code as they might be for publicly posting classified information. The use of “obfuscation” or chatting in coded jargon as a key strategy to keep the code under wraps had me thinking back to Tony Soprano and Analyze This. Quite fascinating indeed.
if it is true that this cache of code and instructions has escaped from CIA control into the hands of various third parties, we are looking at a whole navy of submarines with screen doors.
navy being: USA IT infrastructure
I’m interested to know how this escaped and how they ever thought they could keep it secret…
“…how they ever thought they could keep it secret…”
slap a classified label on it, get people to sign they won’t leak it…wait that describes a certain ex-secretary of state
So, Apple was right to refuse to build a backdoor into iOS for the government claiming that, if the good guys have a backdoor then it will eventually fall into the wrong hands. I mean, if the CIA can’t maintain control over those tools, then how could they expect anyone else to maintain control of them? Thank you, Apple.
“Three can keep a secret, if two of them are dead.” – Benjamin Franklin, I think.
“No computer is safe” – Abraham Lincoln
“I hope our wisdom will grow with our power, and teach us that the less we use our power, the longer we can all play Bejeweled.” — Thomas Jefferson
“Don’t believe everything you read on the internet” -Ghandi
“I drank what?!?!” -Socrates
“Only the abacus is completely secure” – Alan Turing
Perfectly expressed.
However, I would add the phone was eventually cracked by forensic tools anyway, so the FBI request was unnecessary…
and if the CIA already had an exploit to crack that phone, why didn’t the FBI know about it?
If they did, why the song and dance with Apple anyway?
Because they wanted to set a legal precedent whereby they would be able to compel Apple to break into phones for them in the future. Of course they could break into the phone whenever they wanted.
When it became apparent that they could actually end up setting a precedent where they were not able to do this, they withdrew.
They will surely try again when a better case comes up, maybe a pedophile or something equally emotionally compelling. You don’t support pedophiles, do you? We *need* to get into this phone to stop pedophiles…
In my humble opinion what Mr. Omer states as what’s surprising: “What’s surprising is that the general public is still shocked by stories like these.” is not the real story. I would submit that what I glean from this is that the agency that is actively looking for ways to hack devices are themselves guilty of not protecting their own critical data from other hackers.
Like the DNC e-mails, this was a leak, not a hack. Someone from the inside transported the information out (leak), not attacking from the outside to obtain illegitimate access (hack).
Agreed. Wikileaks called it an “isolated high security network” This implies an air-gapped network. Obviously a cleared employee walked out the door with it.
The clear message that operation weeping angel sends is:
Don’t blink!
I am not only NOT shocked about these revelations, but I would bet that many of the white hats in the IT community already know about some of these tools and the vulnerabilities too! I’m sure their will be a mad scramble in all the intelligence agencies in all countries to discover new vulnerabilities soon.
The more I see this, the more comical making a big deal about Hillary’s private server seems less and less relevant – as no matter what email service you use, it will get cracked by someone.
JCitizen, nobody makes a big deal about using a private server. Even Hillary can do that. It’s when you start to send classified information through your own server, that’s when there’s a problem.
Maybe the PC mantra inside the Beltway in the wake of 9/11 that the intelligence community needed to go from “need to know” to “need to share”, is now recognized as a bad idea. Interesting that Private Manning, Edward Snowden, and if Wilileaks is to be believed that this dump came from a contractor, were not the primary gatherers or consumers of highly classified intelligence.
We may need to go back to talking to people in person,and unplug the tv when your not using
Nobody is talking about the identity of the personnel.
Wikileaks now has this ( but have redacted it for publication) Is it safe to assume the Russians have it too, and they now have insight into how each individual thinks.
Tie this to the OPM data and the USIC is on very shaky ground.
If you’re trying to cheer us up with this, you can stop now.It’s not working…
Brian, you have again taken something complex and made it understandable to someone like me, who is not a tech person. Rare talent that you can be proud of!
Thank You
The DNC is a private, not public, organization. Why would the Obama administration set the U.S. government on some multi-million dollar, CIA led, retaliation against anyone for hacking a private organization that failed to protect itself?
Had the government merely looked around I’m sure that they could have found many cases where actual government systems have been hacked and attacked.
All in all the biggest leaks seem to be the people in the system. Our own citizens and foreign agents are stealing classified materials by the truck load (including, famously, the designs of our nuclear stockpile), but we are busy worrying about private entities that won’t even take fundamental precautions.
Yes, this is a threat, but I believe we have our priorities all wrong. We should be concentrating on protection, retaliation is not an effective strategy because we already exploit all we can.
Old-Timer, it does not matter that the DNC is a private organization that was part of an attack. When part of the political process in this country is potentially compromised by a foreign government, then it is a concern for all.
What happens if that foreign agent has access to material that could be used to blackmail a future Senator?
Mike, perhaps a U.S. Senator should not put themselves in a position to be blackmailed?
Having one’s own government intercepting communications between citizens without proper authorization and leaking classified information like a sieve is more of a threat to our nation than anything involving some political committee. The political class always takes care of itself – I wish they cared as much for the ordinary citizens.
What is shocking is that my profession writes software that has zero day exploits. That is totally unnecessary. Many of these exploits are due to programmers using entirely unsafe languages like C. C like languages should have been abandoned 30 years ago. Unless we resort to languages that are safe by design we will have zero day exploits based on stupid mistakes programmers make with these languages.
Haven’t looked at the files but find it fascinating – the CIA has exploit developers and field operatives that may need to access this documentation from the field served up from deniable caches scattered geographically around the web. It would be pretty damn easy to track an agent if he’s “phoning home” to Langley to pick-up exploit files. So in that regard, I am hesitant to jump to judgment of them “losing control” of it.
Made me think of a parallel we rarely hear about but must be rampant….How many civilians do something not too dissimilar at work, using private or trial accounts on web applications like Google Drive, Tableau or others to speed up collaboration or invite in others who cannot join the company network? Do they clean up access when team members move on or a project is over?
Thanks Brian – appreciate your reasoned approach and initial assessment.
Those CIA and FBI knows alot and the top guys knows about it all. What is the meaning of “confidential” when I’m working in the same organization? Boss will tell you that it is “classified” cos he knows that would lead to him if he should let you have it. Or have you all forgotten bout SNOWDEN? That gentleman revealed lot of things from inside NSA. That we taught they,re protecting us. Then how you will be cut off if caught is just handy for them. I’ll say this; if these things/ information are not really happening or real, it won’t be leaked. I believe now some junior staff are under surveillance or monitored. Those “big guns” know this is not a falsified information and they will not stop searching for the origin or informant.
Ransomware here we come.
I’m interested in knowing how all this classified information was removed from the CIA environment without being noticed? Especially after the Snowden and Manning incidents, didn’t the CIA have any detective / preventive mechanisms in place to prevent the extrusion of sensitive data? Or was it as low tech as walking out with it on a thumb. This is obviously due to insider threat, but was there collusion? Just seems to me that even in highly classified, advanced so-called “high-security” environments there are security holes big enough to drive a bus through.
Sounds like many of these are physical exploits. They have to be outside the CIA network. How do you think someone gets to them in the field ? A nice subtle connection to CIA.gov followed by 30 years in the gulag?
Probably exactly as low-tech as walking out with a thumb drive. Depending on how vigilant the exit process is, there are even body cavities in which to conceal it. Of course USB connections SHOULD all be secured on such systems. But these are hackers by definition. Where there’s a will……
It sounds like a pretty desperate operation, considered the life span of current technology.
Thank you Brian, awesome article!
If Edward Snowden was upset about the kind of work his agency was performing he should not of been working there, so no he is not a whistle-blower, there’s nothing here that is shocking.
Whoever gave this information to WikiLeaks should be prosecuted to the full extent of the law.
Interesting comment in the Wall Street Journal –
“Note how Wikileaks never seems to disclose Chinese or Russian secrets.”
Ha HA exactly what we should ALL be asking!
Motivation of the disclosure was???????
Good for all mankind? I don’t think so.
Just like following the money will catch the crook, find the motivation for the disclosure and you may get to peek at the real answers.
Too funny that so many people have alternately called Assange a plague or a hero. Sean Hannity, Trump. etc….
I’m sure we will get to churn this media event till the butter overflows.
It shouldn’t be hard to find the culprit. 1st reaction I heard was “It was the Russians” and 2nd reaction was “We will find the contractor who did this”. That narrows it down to a Russian contractor. Simple really.