When WikiLeaks on Tuesday dumped thousands of files documenting hacking tools used by the U.S. Central Intelligence Agency, many feared WikiLeaks would soon publish a trove of so-called “zero days,” the actual computer code that the CIA uses to exploit previously unknown flaws in a range of software and hardware products used by consumers and businesses. But on Thursday, WikiLeaks editor-in-chief Julian Assange promised that his organization would work with hardware and software vendors to fix the security weaknesses prior to releasing additional details about the flaws.
“After considering what we think is the best way to proceed, and hearing these calls from some of the manufacturers, we have decided to work with them to give them exclusive access to additional technical details we have, so that fixes can be developed and pushed out,” Assange said in a press conference put on by his organization. “Once this material is effectively disarmed by us, we will publish additional details about what has been occurring.”
Source: Twitter
So-called “zero-day” flaws refer to vulnerabilities in hardware or software products that vendors first learn about when those flaws are already under active attack (i.e., the vendor has “zero days” to fix the vulnerability before it begins affecting its customers and users). Zero-day flaws are highly prized by cybercriminals and nation states alike because they potentially allow attackers to stealthily bypass a target’s digital defenses.
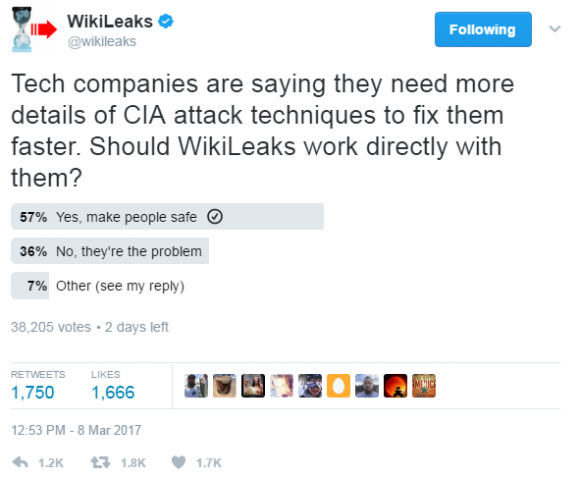
It’s unclear if WikiLeak’s decision to work with software makers on zero-days was impacted by a poll the organization took via its Twitter page over the past few days. The tweet read: “Tech companies are saying they need more details of CIA attack techniques to fix them faster. Should WikiLeaks work directly with them?”
So far, just over 38,000 people have responded, with a majority (57 percent) saying “Yes, make people safe,” while only 36 percent selected “no, they’re part of the problem.”
Assange didn’t offer additional details about the proposed information-sharing process he described, such as whether WikiLeaks would seek to work with affected vendors individually or if it might perhaps rely on a trusted third-party or third-parties to assist in that process.
But WikiLeaks seemed eager to address concerns voiced by many tech experts that leaking details about how to exploit these cyber attack weapons developed by the CIA would leave consumers and businesses caught in the middle as crooks and individual actors attempt to use the exploits for personal or financial gain. Perhaps to assuage such concerns, Assange said his vision for WikiLeaks was to act as a “neutral digital Switzerland that assists people all over the world to be secure.”
Nevertheless, even just the documentation on the CIA’s hacking tools that was released this week may offer curious and skilled hackers some strong pointers about where to look for unpatched security flaws that could be used to compromise systems running those software products. It will be interesting to see if and how often security researchers and bug hunters going forward credit the WikiLeaks CIA document dump for leading their research in a direction they hadn’t before considered.




“WikiLeaks was to act as a “neutral digital Switzerland that assists people all over the world to be secure.””
In my opinion Assange suffers from narcissism
Well, that really furthers the debate.
What does that have to do with the story? I know it scores you street cred with certain groups to wave the “Assange sucks” flag, but seriously. What does his possible personality flaws have to do with his choice to responsibly disclose these vulnerabilities?
Because being a Russian agent and a convicted rapist makes for a credible source… Funny thing about the timing of that release, just as Senate probes are starting up.
http://www.bbc.com/news/world-europe-11949341
You may want to look before claiming someone has been “convicted.”
“being a Russian agent”
Citation needed
“The Russians are coming, the Russians are coming!!!”
LOL.
While interesting to explore, neither the credibility nor the narcissism of Assange are at issue here. The proof is in the pudding they have in Vault 7.
Like the NSA leak before it, this so-called treasure trove of potentially the entire arsenal of the CIA’s wasn’t even stolen by Russian agents or anyone else. It was GIVEN to WikiLeaks by a US government employee or contractor.
We certainly have enemies from within and without!
neither has been proven in a court of law, innuendo will only take you so far
To be fair the only reason we don’t have a resolution on whether he is or isn’t a rapist is because he has failed to allow it to come to a resolution, which he justifies by using innuendo and falsehoods. Since he uses them turning around and using them on him seems like fair play, although it’s a case of an eye for an eye making the whole world go blind.
It sounds like Ecuador may be tiring of him, so we may have a resolution on that point soon. Pawns like Assange and Snowden make for great political theatre but eventually people grow tired of seeing CATS and the run comes to an end. I worry about what will happen to Snowden once that happens. Assange will just end up in the hands of Sweden, which isn’t a bad fate.
Is he a rapist? We don’t know.
Are there powerful people out there who want to throw him in jail and prevent him from leaking details about their illegal activities?
Yes, we are absolutely certain of that.
Which makes the answer to the first question most likely “No”.
Is he a Russian agent? No one else has ever accused him of this. This speculation is as useful as wondering if he is a Martian agent.
“Because being a Russian agent and a convicted rapist makes for a credible source…”
From Wikipedia on rape as defined in Sweden:
“That change in the legislation… made the legal definition of rape [in Sweden] one of the widest legal definitions in the world… The low conviction rate could be explained by the reduced legal distinction between rape and permitted intercourse, leading to greater challenges for the prosecution to prove its case, according to Petter Asp, Professor of Criminal Law at Stockholm University.”
In other words, one of the best countries in the world to smear someone with a phony sex crime for political purposes.
Oh, and I forgot to add the NO ONE would EVER commit perjury against him that could NEVER be proven as such since only two people were present during the alleged “rape”, him and the accuser, right? I mean, what possible motive could they have for ever doing that, perhaps on the behest of some other persons or entities?
Get real…
I am sorry, but I thought that Inocent until proven guilty still applied in a free world! Steve must have evidence (legal or otherwise) that a) he is a rapist b) he is a Russian spy!
I guess in today’s society Trumpisms are becoming a vogue.
Regardless, if WikiLeaks is willing to cooperate with the security industry to make our world a little more secure, what is wrong with it!
I vote no cooperation with Assange. Even if the tech companies don’t cooperate he will release the code he has and then they can fix the leaks. The additional exposure time will be the time to fix the problems. Cooperating with Assange gives him creds and status which is what he values most. He wants to be a player; the arbiter of what’s good or evil, right or wrong. In the old days we called that a monarch.
This is probably the best possible solution. Defang the CIA by getting their exploits patched, but doing so without exposing people to actors that don’t already have the exploits. Hopefully many of these will fix vulnerabilities used by the NSA, Russians, and other actors. Hoading zero-days only makes sense if you assume your enemies are too dumb to find them. That is rarely the case. It’s better to protect everyone.
Bigger question is why didn’t the CIA notify manufacturers of the zero days after the breach was discovered last year?
Michael,
This is a topic that will never have a straight forward answer. The one thing that we have to take from all of this is that instead of Mass Surveillance Taps the NSA was utilizing we can see from the release so far that the CIA was actually having to target the specific devices of their targets. Now of course we can see they had procedures in place depending on the device but from what I’ve read it appears physical access and/or being on the same network as the target was needed, no in all cases I bet. Ultimately it boils down to this, you either
A. Ensure you’re practicing good Personal Security by keeping system updated, utilizing Encryption Products, Securing Internet Connection with utilizing a VPN, utilizing Malware Protection, ETC. (Which ultimately if you are being targeted by them this won’t matter because their going to get the information one way or other.)
or
B. You don’t take Personal Security serious
I’m not faulting them for this as I did with the Mass Surveillance the NSA was doing. (Still Doing).
That’s really the only question, Michael. People are arguing about whether or not the CIA is hacking them, but that’s the wrong premise.
The problem is that ANYONE could have discovered these flaws, especially state actors, that may have enabled them to compromise any number of key individuals in American government, media, business, etc.
The CIA and NSA should have silently notified the companies of these flaws. It’s one thing if they exploited them in that window between discovery and patching, but it’s entirely another to weaken their own country’s defenses simply to further their own ends.
At least groups like the NSA’s TAO where they implanted their own physical access implants weren’t ignoring existing vulnerabilities that anyone could exploit – they were at least adding their own to only target machines that only they (at least in theory) could exploit.
You win the Best Comment Award.
Because the CIA was exploiting these vulnerabilities to spy on friends and foes alike. It would not be worth its annual budget if it found then reported zero-days to anyone, let alone the very people who would issue patches.
The CIA is a spy agency legally tasked with foreign intelligence gathering. So what if they have to suffer through our rants coming from a Samsung TV to catch some terrorists.
What government agency does that now? I know from experience that most agencies have to avoid looking like they are favoring one company over another. They tell Apple about an iPhone hole, then later that same hole is found on Android you will have people screaming about how they are favoring Apple and how corrupt the government is. They can’t win, so they have no reason to help.
That said, I’m not so naive that I think they aren’t happy to exploit these problems.
Because US citizen’s security is not a concern of the CIA, it has other agendas.
https://www.cia.gov/about-cia/todays-cia/what-we-do
“What We Do
CIA’s primary mission is to collect, analyze, evaluate, and disseminate foreign intelligence to assist White House the President and senior US government policymakers in making decisions relating to national security. “
I won’t repeat what others have said about the CIA’s job description, but I would add what I’d like to see done by the executive branch (under direction from the President):
Coordinate CIA/NSA information with DHS. Have DHS looking for specific patterns of vulnerability exploits, and if they spot those patterns (and it isn’t the CIA/NSA), then that means someone else is exploiting it.
The CIA/NSA should have disclosures written up and ready to release via private channels to vendors, but hold on to them.
At that point that DHS has detection of an “exploit in the wild” the CIA/NSA should be notified, and the related pre-written disclosure should be released to the vendor(s).
The problem with IoT is that manufacturers are putting devices out there with ZERO security/privacy controls which makes it easier not only for the CIA, but all types of malsubjects to take advantage of these zero-days vulnerabilities. Today, it might just be your TV, camera, etc, but in a few years it will be EVERYTHING! We created a Frankenstein when we gave these common appliances the capability to “communicate”.
This is interesting. WikkiLeaks is putting the public and vendors first. It is not often we see someone trying to do the right thing.
I am certain the techniques at issue were already well circulated in the hacking underworld. The publication may make the information a little easier to obtain, but no other damage. I look forward to the patches.
In the meantime, I have a lot of reading to do.
I’d agree if they hadn’t done a poll first. They knew what the right thing was, they just wanted to stick their finger in the air and see which way the wind was blowing.
Very interesting that so many chose to respond with “No, they are the problem.”
Is there evidence to suggest hardware/software makers get paid to allow for their products to be exploitable by state actors?
I am familiar with state actors intercepting shipments, but I am not familiar with any cases where companies explicitly made their own products vulnerable due to State pressure or something of that kin.
Thanks for any replies!
Another concern of mine is how Wikileaks can insure that these “Zero Days” are kept safe from hackers. I believe many people will try to go directly to Wikileaks for this trove of tools/vulnerabilities, and I am concerned that given such incentive, some will prove successful.
If you do some searching you’ll find examples of this actually. Here it is from Intel:
https://plus.google.com/+TheodoreTso/posts/SDcoemc9V3J
I remember there was a heavy duty router manufacturer that had built in exploits outed (presumably from their own employees on purpose) and had to patch them shortly thereafter as well.
Most U.S. PC manufacturers have security holes in their own software they put on every PC (whether that can be ascribed to malicious intent or to ineptitude is debatable) – so with a new PC the best thing you can do is back it up, reformat the disk and install Windows etc. from scratch leaving off the vendor software.
http://fortune.com/2015/11/25/dell-second-security-certificate-flaw/
That’s right, it was Juniper systems (they do commercial scale routers etc.):
https://www.wired.com/2016/01/new-discovery-around-juniper-backdoor-raises-more-questions-about-the-company/
Presumably the govt would have wanted back doors in Cisco’s stuff as well…as the Snowden docs showed most of these Mfr’s were quite willing partners in all this. Apple was really the only one where the government was trying to surreptitiously compromise them to put backdoors in their products:
https://theintercept.com/2015/03/10/ispy-cia-campaign-steal-apples-secrets/
It’s not that “hardware/software makers get paid to allow for their products to be exploitable by state actors”, it is just more expensive and time consuming to develop a secure product, cutting into the profit margin and maybe missing the window to get the latest piece of crapware out to market first.
Adding to the problem is the consumer, who is either ignorant or just doesn’t care about security, and who is gobbling up the cheap products. Convenience trumps security for the average Joe, until something happens to them, then the sky is falling and “Why didn’t company XX do a better job!”. Quit buying cheap crap, let the manufactures know this is an unacceptable practice, and maybe things will get better. Maybe.
Spot on!
I don’t think this happens in the US, but it definitely happens in China. That is why it is critical that independent third party QA validation of hardware designs and software are critical before installing something made by Chinese and sold by Chinese to go into your enterprise.
Don’t if this true but Appvision.net — says they make mobile apps 100% tamper-proof! They say they lock the mobile apps binaries.
This is basically irrelevant in the context of the Wikileaks stuff – where the exploits aren’t for individual apps, but rather for the operating systems – cause once someone has your OS, they can watch / log whatever you type, say etc. on that phone / PC regardless of the app.
“Perhaps to assuage such concerns, Assange said his vision for WikiLeaks was to act as a “neutral digital Switzerland …”
Nice play on words. I caught it.
‘Mr Assuage’ attempts to remind Switzerland what a neutral stance looks like?
So the question is how much does this help or hurt the end user? I think most of us already knew that security agencies like the NSA had access to our data even through cooperation with technology companies. I would also guess that many bad guys knew enough to avoid traditional technology paths so as to mask detection. WikiLeaks simply placed a significant risk on the end user in order to prove what we already knew. I think what this also will bring is more distrust of the technology companies who have continued to say our data is secure when in fact it is not. It will also hamper any positives to gathering data for the real noble purpose of protecting us for terrorism. Although as I have said leaves me wondering if any terror group has not already taken steps to avoid this exposure already. Since our government security is so bad, they simply had to use a blanket collection process rather than focus on the potential threats. This to me never seemed to be real effective in the first place, and it now has proven to be a problem on grounds it violates a persons privacy.
should they decide to collaborate with wikileaks, will the manufacturers be in legal hot water for accessing classified information?
It ‘appears’ they had to declassify it, in order to use it on the public internet:
https://wikileaks.org/ciav7p1/index.html#ANALYSIS
“If CIA implants, Command & Control and Listening Post software were classified, then CIA officers could be prosecuted or dismissed for violating rules that prohibit placing classified information onto the Internet. Consequently the CIA has secretly made most of its cyber spying/war code unclassified.”
The truth of the above statement is currently unconfirmed, but it does sound reasonable.
Something about pointing things at your feet, moving fingers and having holes in feet afterwards, springs to mind 😉
If they did the responsible disclosure thing as required by the president, they wouldn’t be in this mess.
(Actually, if they purposefully disobeyed a direct order from the president, what is the punishment for that? Sack the entire CIA mgmt? Close the agency down and merge it with one who can obey the Law? Imprison the CEO for direct violation of a presidential order – is that treason? If nothing is done to the top mgmt, it will just happen again and again and again, ad infinitum – put all the CEO’s down in Guantanamo for a while, strip them and their entire family of their assets, and these violations will cease immediately! Until a big stick is waved in front of these morons *and* used frequently and in full force of the Law, nothing will change. The fact we’re at this point after the Snowden affair is testament to that.)
So now during a football game when I yell at my TV – I can assure my wife they really “ARE” listening to me!! 🙂
my mom has senile dementia, she rails at CSPAN politicians all day long, so i am getting her a Samsung smart TV for her next birthday…
We have to keep one thing in mind. The world can be a dark and dangerous place. Certain actors don’t play by our rules. The CIA might not be a sinless angel, but remember who we have to deal with. Satan in the flesh in many cases, who will stop at nothing to destroy democracy and the freedoms that we now enjoy. Fairness and transparency only aid their cause. Whoever leaked what the CIA does, and how they do it, removes the advantage that we have over the enemy. Do some intelligence agencies hold to every tenet of the Constitution, and place fairness and equal application of the law over safety? I thank God they don’t. They aren’t out to violate the rights of honest well intentioned citizens. They are engaged in active warfare against those who wish Americans harm. Ethics, morals, and higher callings are not in the enemy’s lexicon.
This ain’t Disneyland folks. It’s the real world with real enemies who could give a damn about good intentions, inalienable rights, or freedom as we know it. Whoever took it upon themselves to expose our tools and procedures has committed nothing short of high treason. Period. If it’s the enemy who did it, shame on us for not preventing it. If it was an insider, contractor or otherwise, they should be help accountable for endangering lives and liberty.
MB, you would cravenly abandon your ideals and destroy freedom and democracy for your own safety. Cowards like you are a far greater danger to this country than those enemies you fear, as you would destroy it from within while playing the patriot. Nathan Hale: “I only regret that I have but one life to lose for my country.” Patrick Henry: “Is life so dear, or peace so sweet, as to be purchased at the price of chains and slavery? Forbid it, Almighty God! I know not what course others may take; but as for me, give me liberty, or give me death!” You: “Screw the Constitution! I’m scared!” Way to go, patriot.
How does spying on foreign entities say “screw you” to our constitution…
I’m so sick of people blaming terrorists. They haven’t done nearly as much damage as the crazies with guns. The fact that my personal conversations are being recorded to protect me from terrorism is just ridiculous.
Look at the statistics.
Terrorism is just a way of implementing draconian laws and keeping idiots in fear.
Some of us think the alphabet agencies are also “the enemy”. I don’t think they do what they do to “protect” us.
I’m sorry the CIA was hacked, but it’ll cause them to shore up their security. That’s a good thing. And all the exploits in these Things of the Internet, their manufacturers are going to have to beef up security and keep it updated if they wish to survive in the market. Capitalism can solve all ills if allowed.
Hacking is what the CIA is paid to do. If Samsung TVs and I-phones can be hacked, that means the Russians, Chinese, Iranians, etc. also can hack them, as well as smart teenagers around the world. Hacking is the problem of the 21st century and the CIA and NSA should be experts on all the vulnerabilities of our devices. Anyone who is shocked by the disclosure of the CIA hacks has been asleep for the last ten years.
BTW isn’t it odd that no one hacks the Russians or the Chinese.
Obviously the Russians and Chinese and anyone else we’re remotely interested has been hacked (remember when it was outed that we hacked the personal phone of our ally the German Chancelor?).
The Russians have gone back to type writers and paper for really important things within their government…because of us and our friends.
They do, but we don’t hear about it.
😀
its all circus. Fake.
bs. Russia and Usa fcking together
other world.
Btw…United Kingdom is 100% owned
established by russians.
LONDON is owned by russia and established
by russia.
usa is ownwd by israel and Vatican.
Simple is that !!
They run the world like racketeering.
So Jewish people and the Catholic church are collaborating to run the US? That’s a pretty lofty assumption.
Regardless of your personal stand points on surveillance, saying that the Intelligence Community should report zero-days is one of the silliest things a person could imply is the correct thing to do.
That’s their job. To be good spies and good spies have to keep good secrets.
Also, so many people outside of the “know” constantly make comments with little to no context of how the IC actually works… although I’m not here claiming that I do know; I’m just trying to state an obvious point:
What the IC does, the IC does in secrecy. Even if they were disclosing zero-days to companies, the general public would likely never know. It’s either being done under gag orders and NDA’s or IC affiliated companies which aren’t easy to trace back to the IC.
Well, it really depends on what you think is in the best interests of the country in general.
These agencies primary purpose is to spy and want to do it as easily and quickly as possible – this gets them bigger budgets – so its in their interest to horde these exploits and not tell the manufacturers about them.
However if you take a step back and look at it – these exploits are obviously being used by our enemies as well (they’re not just known by the U.S. cause the other guys are smart too). So you end up with an electronic fortress wall around the U.S. systems (& everyone else) but with open holes in it so our guys can spy on others – but that means the bad guys will come right through those same holes (cause their smart too). The intelligence agencies are okay with this.
I would argue its actually in the U.S.’s larger interest to have a secure electronic fortress wall around its systems and the spying agencies have to do the harder work (like they did before) for intelligence gathering – it just won’t be as easy for them, but the country & its citizens will be more secure overall and I think that is more important. JMHO….
This sounds a lot like the ‘I have a firewall, therefore I am protected’ story of the 1990’s. We need it all.
“good spies have to keep good secrets”
didn’t work out so well, did it?
The only things I have to say about this is;
Its an intelligence agency.
Their job is to spy. Its to keep the bad crap off your turf. IF people truly knew how many terrorist activities were thwarted over the years that didn’t make major news, they would shut up and let the agencies do their jobs.
It gave too much information to contractors and other people as well.
If you have something to hide, they will come after you. If your amongst the millions that lead a boring life – then you’ll have to ramp up your bad side to get a knock on the door from the Feds.
People will complain about anything mainstream. Dirt sells with the big news cesspools, and they know how to push the news addict’s buttons.
No matter how or what they want these agencies to conform to, they absolutely won’t. They break a promise? So what. They are here to protect and attempt to play the political games.
end.
No matter what their goal, hoarding exploits can never be a responsible method of pursuing it.
Suppose they learned that an interaction between aspirin and vitamin C could be lethal. Would keeping this a secret, so they can use it to kill bad guys be a good idea?
At what point doesn’t Julian ASSanage understand that he’s in receipt of stolen property with this “leaks”. If one has something stolen, and another finds it, they have a moral obligation to return it. However, somehow Mr. ASSange equates that his moral compass being higher, he can take stolen property and damage the value of it. Mr. ASSange claims to know the balance of the entire world and all the repercussions of his actions. His motive is to make a name for himself regardless of the damage he causes.
Assange may be all he is called and maybe even more. But he has been deliberately demonized to discredit the quality/authenticity of wikileaks work output.
And yet, Bill Cosby raped like 60 more women and is still walking around free as a bird.
For better or worse, we have Statute of Limitations for a reason. For rape or sexual assaults, it is between 3-30 years in most of the US (some states have no SoL, however, but most are in the 3-10 year range).
http://www.motherjones.com/politics/2014/11/rape-statutes-of-limitation-maps-table
I’m not aware of the laws in Sweden, but most places toll (pause) the Statute of Limitations once a person has “run from the law.” But, so long as law enforcement had access to an accused person and did nothing about it for beyond the SoL, that accused person cannot be charged.
Memories fade, and for all but the worst crimes, the SoL protects us from “bad witnesses.”
1. One of the first commentators hit in on the head – Assange is a narcissist flake.
2. There is not a shred of evidence so far the CIA deployed any of this in the US against US citizens.
3. If the CIA could develop this, what makes the bunker mentality crowd think the Russians and Chinese have not similarly developed such tools, AND deployed them against Americans?
4. “Amazon and Google know a lot more about you than the CIA or NSA because Amazon and Google actually care.” – Robert Gates
Wake up, all govs spy in one form or another even without the IoTs. Ever heard of taxes and bank accounts? No, the nsa\cia isn’t going to willfully disclose new zero days. They aren’t and never will be a consumer protection org. Lol, no gov exists to protect you. That doesn’t mean they are out to get you, but use common sense. Why did anyone think they weren’t spying on you.
Wouldn`t releasing the Zero-Days publicly lead to a rush of script kiddies trying to exploit them until theyre fixed?
Releasing them to selected tech companies is a good thing for long-term security probably but handing these weapons to everyone seems risky to me.
Big SALE: Please visit our store for Brand New & Genuine Windows Server 2016 Standard & Datacenter License with latest version OS with 60% discount: http://www.halfrain.com/Buy-Windows-Server-2016 or http://www.coreyz.com/Buy-Windows-Server-2016
I think they should report these Zero days to tech companies.
Something like what Project Zero does would be cool.. Report the zero day to the company and if they fail to provide updates, release the vulnerability after X days.
Just my 2¢
Wikileaks may have finally opened up peoples eyes to what is really going on in our world. Everybody thinking our government is out for us and they us terrorism as there excuse to spy on us. It’s all garbage its all about control. The NSA, FBI and the CIA are all the same. Wake up people save our country now or its over. Also a safe search engine that doesn’t track you, a good old fashion private search engine Lookseek.com. Have a awesome day.
Two rather glaring things seem to be overlooked in all of these comments:
1. the producers of hardware and software need to be accountable for the security of their products, and the consumer needs to be vigilant in their demands for same, and use their wallets to remind them of their obligation. All the rest about who finds the flaws, exploits them, notified vendors and such is secondary. Given the chance to make money creating inferior products and letting others find flaws, most companies will follow that path. Only we have the power to stop this behavior.
2. How many readers have been in possession of critical information about the wrong-doings of some company or agency, and tried to let someone know through some whistler-blower process? I have, and it doesn’t work in almost all cases. You can google some heartbreaking cases where individuals thought they were protected but instead were persecuted. So the unanswered question is: what is a person to do who believes somebody or some entity is doing really bad things, but has no one to tell because they will be seen as the problem rather than the problem itself?