As thousands of organizations work to contain and clean up the mess from this week’s devastating Wana ransomware attack, the fraudsters responsible for releasing the digital contagion are no doubt counting their earnings and congratulating themselves on a job well done. But according to a review of the Bitcoin addresses hard-coded into Wana, it appears the perpetrators of what’s being called the worst ransomware outbreak ever have made little more than USD $26,000 so far from the scam.
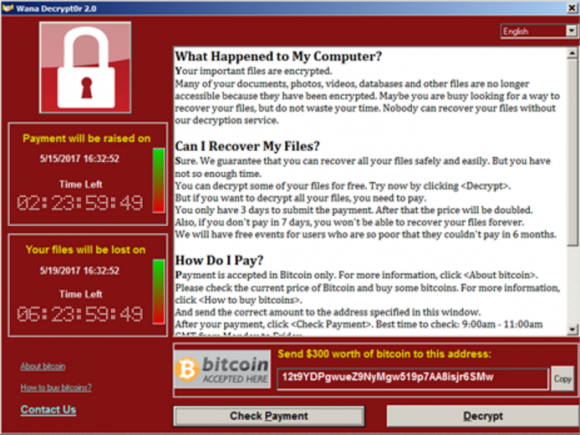
Victims of the Wana ransomware will see this lock screen demanding a $300 ransom to unlock all encrypted files.
The Wana ransomware became a global epidemic virtually overnight this week, after criminals started distributing copies of the malware with the help of a security vulnerability in Windows computers that Microsoft patched in March 2017. Infected computers have all their documents and other important user files scrambled with strong encryption, and victims without access to good backups of that data have two choices: Kiss the data goodbye, or pay the ransom — the equivalent of approximately USD $300 worth of the virtual currency Bitcoin.
According to a detailed writeup on the Wana ransomware published Friday by security firm Redsocks, Wana contains three bitcoin payment addresses that are hard-coded into the malware. One of the nice things about Bitcoin is that anyone can view all of the historic transactions tied a given Bitcoin payment address. As a result, it’s possible to tell how much the criminals at the helm of this crimeware spree have made so far and how many victims have paid the ransom.
A review of the three payment addresses hardcoded into the Wana ransomware strain indicates that these accounts to date have received 100 payments totaling slightly more than 15 Bitcoins — or approximately $26,148 at the current Bitcoin-to-dollars exchange rate.
ANALYSIS
It is possible that the crooks responsible for this attack maintained other Bitcoin addresses that were used to receive payments in connection with this attack, but there is currently no evidence of that. It’s worth noting that the ransom note Wana popped up on victim screens (see screenshot above) included a “Contact Us” feature that may have been used by some victims to communicate directly with the fraudsters. Also, I realize that in many ways USD $26,000 is a great deal of money.
However, I find it depressing to think of the massive financial damage likely wrought by this ransom campaign in exchange for such a comparatively small reward. It’s particularly galling because this attack potentially endangered the lives of many. At least 16 hospitals in the United Kingdom were diverting patients and rescheduling procedures on Friday thanks to the Wana outbreak, meaning the attack may well have hurt people physically (no deaths have been reported so far, thank goodness).
Unfortunately, this glaring disparity is par for the course with cybercrime in general. As I observed on several occasions in my book Spam Nation — which tracked the careers of some of the most successful malware writers and pharmacy pill spammers on the planet — it was often disheartening to see how little money most of those guys made given the sheer amount of digital disease they were pumping out into the Internet on a daily basis.
In fact, very few of these individuals made much money at all, and yet they were responsible for perpetuating a global crime machine that inflicted enormous damage on businesses and consumers. A quote in the book from Stefan Savage, a computer science professor at the University of California, San Diego (UCSD) encapsulates the disparity quite nicely and seems to have aged quite well:
“What’s fascinating about all this is that at the end of the day, we’re not talking about all that much money,” Savage said. “These guys running the pharma programs are not Donald Trumps, yet their activity is going to have real and substantial financial impact on the day-to-day lives of tens of millions of people. In other words, for these guys to make modest riches, we need a multibillion-dollar industry to deal with them.”




I read in the British press that due to underfunding, 90% of the hospitals there are to some degree still using Windows XP and Server 2003. This is why they were so heavily impacted.
Where I used to work I was responsible for managing WSUS. I normally would wait to approve Windows Updates after they had been out for a month, unless if something was super critical. This was done because Microsoft once or twice a year would push out an update that would trash one major system or another. After a week or two the bad patches would be silently fixed.
I’ve seen much of this too, yet people in the medical community have all reported their machines run Windows 7.
It’s worth mentioning that the UK is currently in an election period, so alot of people are trying to exaggerate the prevalence of Windows xp within the NHS as evidence of the government not providing it enough funding (and hence support the opposition).
The modern hospital is full of computers that is attached to a variety of testing and monitoring devices that require pretty dedicated software and drivers to run the equipment. My experience with this equipment is dated (over 10 years ago), I found many of the vendors failed to understand their role in IT life cycle support, that they needed to maintain that software and offer updates to customers as the computers running these devices required upgrades, it’s not a one time sale and install to be forgotten about.
And no organization has an unlimited budget, with the size of UK NHS budget I’m sure there was enough money to upgrade anything with XP if it was prioritized, but when weighing all the risks verses cost saving and new capabilities, upgrading XP apparently just lost out…
The modern hospital has a very small number of purpose-built machines that include an older Microsoft OS that they are wary of patching. These machines do not have Outlook installed on them!!!
The modern hospital has thousands of workstations with a small number of standard local applications that remotely access important health-related applications and so are easily re-imaged in minutes and should likewise be receiving the latest MS patches as soon as they are released.
St Barts – the only significant NHS Trust heavily affected by this “cyber attack” had a large number of non-updated and non-patched workstations. The time they are taking to re-image their PCs seems to indicate they are not well-equipped in the skills, systems and processes that are required in this area.
The rest of the panic is about the chaotic IT environment that pertains in GP surgeries and other micro IT environments on the periphery of frontline healthcare.
It is about funding a properly run IT department to make sure the system is up to date to prevent something that is preventable.
I think these ransomwares are linked with the same group or individual. responsible for WannaCry.
ZeroLocker (2014)
M4N1F3STO (2016)
Zyka (2016)
CIA Special Agent 767 (2016)
WannaCry (2017)
M4N1F3STO, CIA, and Zyka ones can all be linked by the bitcoin address 1GmGBH9ra2dqA8CgRg8a8Rngx4qHb2hLDW
If victims actually pay the ransom, do they get thier files back?
What about with previous incarnations of the “Wana” family?
Wouldn’t count on it. Although it appears it is technically possible to decrypt those files, with only three different bitcoin addresses the ransomware authors won’t have a way to determine who paid the ransom and who didn’t.
Sounds like you don’t know how bitcoin works.
Actually, yes, they di grt their fikes decrypted. Tgey run these ops like a company and reputation is important. If word got out they didn’t “honor” their end of the deal, criminals or not, victims would not pay. Why pay if you wouldn’t get your files back anyway. Their reputation to decrypt upon payment is very important to maintain.
Replying to self: A Symantec spokesperson on Australian TV subsequently claimed that those who paid the ransom had NOT had their files decrypted. Also I believe that in ransom cases in general only about 25% of victims who pay get their systems back.
More: but Mikko Hypponen says some actually do get decrypt codes.
https://twitter.com/mikko/status/864107673146490880
Hey Brian – thanks for this article. I also put together some Q and A on my author website at http://www.dgregscott.com.
– Greg
This is true if economic crime generally and one if the main reasons it’s illegal. Every time I have been a victim of theft, the value I lost was vastly greater than the value the thief obtained. In a couple of instances, the thief got no value at all, but I lost days or weeks of work. That’s why voluntary exchanges are generally efficient and involutary ones often aren’t.
The bitcoin wallets that the worm uses are hardcoded into it – so someone has created a Twitter page that watches all three (get an entry for each payment) with a total every 2 hours. It’s only up to $69k or so at this point on Tuesday:
https://twitter.com/actual_ransom/
If the NSA and CIA were no spending so much money creating these viruses then nothing would have happened because this type of enterprise is a sure money loser given the massive investment required to create a virus. It was obviously designed to wreak havoc in enemy hospitals which breaks the Geneva Convention once more.
Microsoft created the virus. The CIA and NSA found it. It was patched before the CIA and NSA information become public.
The virus is spread by people clicking on email attachments – ‘Clinical Results’ in the UK NHS – why are the media not screaming “Don’t click on zipped attachments”?
E-mail is only one of the attack vectors. It also spreads by scanning for vulnerable systems via SMB1, even on the open internet.
Thanks for the information, Brian. Do you know if the ransomware behaves differently when the user has admin rights than if they don’t?
UAC can be bypassed with 3-4 lines of code. It’s a known flaw but still not fixed. So the question is seamless.
IT security firm saying that the BTC addresses, which every infected user saw on the screen, were hard-coded? That’s the true disaster.
The world got off cheaply – on balance the extortion ring has done everybody a big favor for a pittance of payback. The ransom should be deducted from sloppy, overpaid IT Managers’ performance pay.
So my understanding Shadow Brokers got some US gvt code, Feds arrested a Martin pack rat assumed not the thief and will be spending a large portion of his life in jail. Thieves modify the code to lock up as many computers as they can for 26,000. Hospitals???? Such stupidity, its beyond comprehension.
if any crime occurs then someone need be quilty.
for feds its easy to blame on one person all crimes.
get real,thats how it works !!
I think the low take could also have something to do with the complexities of buying bitcoin if you are not already set up / in the system. Especially if you are outside the US. Processes involving registrations and ID photos with credit card numbers showing are not easily navigated through if you’re not tech ssavy and have suddenly developed a huge paranoid streak about anything on the internet if all your files have just been encrypted… (Have been there in the past with a client who thankfully had decent backups so paying wasn’t an option but they got interested in the process).
You do not need to register and use known exchangers such as Poloniex or Kraken. Just with a wire transfer and a rep system in a known website and you get the bitcoins (see LocalBitcoins’ website)
And outside the US? And with no “rep” on an existing website? Internet browsing Joe Public trying to buy bitcoins in a rush to get their stuff back don’t think this easy…. Try it from scratch for yourself…
I’m touched by the moving words of Mr. Phillip Misner from Microsoft Security Response Center.
To prevent, protect and raise awareness, it is necessary to estimate the damage that this virus will cause and to charge this amount from the US Government and Microsoft.
Microsoft has created a “flaw”, a port for the NSA to spy on governments and businesses around the world. When the “software”, created by the NSA, to use that port was hacked, the NSA informed Microsoft that it released a patch to “fix the flaw”. And did it quietly, not to arouse suspicion.
This distinguished company still tried to get high gains with the misfortune of others by selling patch to OS prior to the W7. Until a young Englishman created a key to unlock hijacked computers. And this patch became free.
Do you want to criminalize the hacker who is hijacking computers? Wrong! Be grateful to him as you should be to Snowden.
By honest competition and true capitalism.
That’s just ridiculous. Thank the hackers? (Sorry, let’s call them criminals not hackers). These are crimes, pure and simple, and they need to be heavily punished. “Yesterday someone broken into your house and stole all your possessions, proving that your security system doesn’t work; please thank them.”
I like Brian’s comments in that regard; don’t look at this as a $26k crime, but a $1bn crime…maybe more. They stole $26k but burned down the $1bn house.
Frankly, bitcoin needs to go. Untraceable currency drives crime; this has always been the case.
Todd,but there is many many innocent btc.users !!
These things are quite different from braking into your home.
US laws allow these contracts. However these actions if proved are far more “criminalized” in the rest of the world.
It’s more like you pay for security system, special keys and so one. But the government and in this case also Microsoft are giving the pins for the alarm, disable the cameras, give the physical keys to your locks, say how much money and gold you have in there, are you at home or not – to the open world – everybody interested in it.
And when someone robs, he brokes your heart?
Untraceable currency drives crime? Just like guns kill people, cash causes crime? Unfortunately, those 3 things are inanimate and can do nothing without a human involved. Criminals cause/drive crime. Quit blaming things that are not the problem. Liberty requires privacy and bitcoin and cash are examples of currency that is usable in private. Now, if you want to,blame someone, blame MS for insecure software and blame the NSA for not notifying MS when they discovered the exploit, instead of seeing it as an opportunity to violate the privacy of millions.
You said it all. With every new flaw fixed, they add 10 new. SMB is a 5-year old joke.
The real criminals here are the managers of clinic. My health records are exposed on an outdated machine? This is bad, very bad! I would even say those files *need* encryption! All this b/c a bunch of corrupt politicians keep cutting funding. This cannot go on.
Hello Brian,
seems the bad guys were smart enough to rotate different BTC wallet addresses; to measure total proceeds, you would need to collect all alternating pop-up banners and add up the different wallets:
9 BTC now ($15k):
https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
12.7 BTC now ($21k):
https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
I only noticed the varying numbers when I compared the wallet addresses myself.
Many Regards from Berlin,
TJ
A neat/clean analysis of wannacry : https://blog.nviso.be/2017/05/15/wcry-ransomware-additional-analysis/
\T,
SMB file sharing is a nice, respectable feature to use across a private network. Why would anyone allow open SMB ports be exposed to a public internet ip?
IT department funding is less an issue here. I don’t run a company, but if funding is tight then make it a priority that at least one person on staff knows something about firewall and router configuration security features.
Many small businesses still don’t see the value in spending money on security. I work for smb’s and it is very hard to get many to actually invest in security, and proper data backups, bop and dr. I’ll also say that many it consultants are woefully outdated on their knowledge and even activate security holes into client networks for pure convenience sake. One large it firm in the south who supports hundreds of medical practices used to routinely open port 3389 for remote access. I suspect they aren’t the only exception to common sense
Apparently they also take payment in pre-paid Visa & iTunes cards (held up to the webcam). They netted $860 worth from one victim.
Obviously they used multiple bitcoin addresses … not sure how a security expert would not know this. Proceeds are much more than 26k
I worked at a “modern” hospital that is well renowned for research and teaching doctors. It too had multiple vendors of proprietary systems for machines involved in prolonging life but those were not on the net then anyway. Pharmacy distribution machines were on our network as were end user and PC or Xterminals and Macs.
In the mid 9o’s it had all current flavor of Windows including NT4 and Apple and Unix and IBM mini and dumb VT terminals etc. There was no cohesive design and they didn’t know where most of the IP’s were assigned.
Cat 3 connections in the oldest Cat areas and even some DOS machines and windows 3.11 and hard orange garden hose and thin ethernet. We as the IT group were one of 2 under that did not have access to the actual routers under control of a Campus network.
Our network of the one of the two had incompetent people in charge promoted due to small network in acct dept setup with coax bus and the fact he was a minority. Woman too promoted that new NetWare as admin but clueless in windows NT.
The entire thing was monitored by a BERT engineer. It froze my download for PDF file for Cabletron hub as they didn’t know what that type of file was then and the size I would imagine. Next day it was released to view. But that network did get hacked too a number of years ago and it doesn’t surprise me at all.
Between injection methods and RATs there is many ways to get in. I think the DNC and other communist group that was exploited along with what were probably at times emails on phones with SS7 exploits or access if you have access to SS7 anyway is an example of people you would not want running your country. They click on anything and twice.
For all the promises of the most transparent government ever we heard we only got it in the end from WikiLeaks and their ignorance in clicking and / or SS7 anyone one can listen in on or absorb texts / email and audio as man in middle.
This just shows how many people do not update and even IT people often would rather test updates on one machine before installing KB12344578 on everything and find out everyone is BSOD or offline. Whats worse is its one of our 3 letter agencies tools that got leaked but as we have seen even bash was found to have a hole a while back after everyone claimed it was secure.
Welcome to the pitfalls of technology. Whats next going back to 2 cups and a string?