As thousands of organizations work to contain and clean up the mess from this week’s devastating Wana ransomware attack, the fraudsters responsible for releasing the digital contagion are no doubt counting their earnings and congratulating themselves on a job well done. But according to a review of the Bitcoin addresses hard-coded into Wana, it appears the perpetrators of what’s being called the worst ransomware outbreak ever have made little more than USD $26,000 so far from the scam.
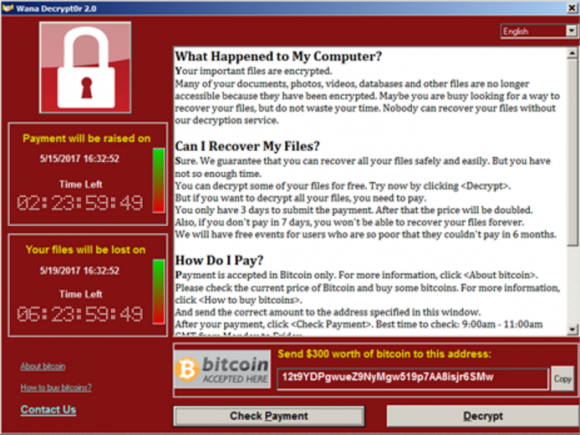
Victims of the Wana ransomware will see this lock screen demanding a $300 ransom to unlock all encrypted files.
The Wana ransomware became a global epidemic virtually overnight this week, after criminals started distributing copies of the malware with the help of a security vulnerability in Windows computers that Microsoft patched in March 2017. Infected computers have all their documents and other important user files scrambled with strong encryption, and victims without access to good backups of that data have two choices: Kiss the data goodbye, or pay the ransom — the equivalent of approximately USD $300 worth of the virtual currency Bitcoin.
According to a detailed writeup on the Wana ransomware published Friday by security firm Redsocks, Wana contains three bitcoin payment addresses that are hard-coded into the malware. One of the nice things about Bitcoin is that anyone can view all of the historic transactions tied a given Bitcoin payment address. As a result, it’s possible to tell how much the criminals at the helm of this crimeware spree have made so far and how many victims have paid the ransom.
A review of the three payment addresses hardcoded into the Wana ransomware strain indicates that these accounts to date have received 100 payments totaling slightly more than 15 Bitcoins — or approximately $26,148 at the current Bitcoin-to-dollars exchange rate.
ANALYSIS
It is possible that the crooks responsible for this attack maintained other Bitcoin addresses that were used to receive payments in connection with this attack, but there is currently no evidence of that. It’s worth noting that the ransom note Wana popped up on victim screens (see screenshot above) included a “Contact Us” feature that may have been used by some victims to communicate directly with the fraudsters. Also, I realize that in many ways USD $26,000 is a great deal of money.
However, I find it depressing to think of the massive financial damage likely wrought by this ransom campaign in exchange for such a comparatively small reward. It’s particularly galling because this attack potentially endangered the lives of many. At least 16 hospitals in the United Kingdom were diverting patients and rescheduling procedures on Friday thanks to the Wana outbreak, meaning the attack may well have hurt people physically (no deaths have been reported so far, thank goodness).
Unfortunately, this glaring disparity is par for the course with cybercrime in general. As I observed on several occasions in my book Spam Nation — which tracked the careers of some of the most successful malware writers and pharmacy pill spammers on the planet — it was often disheartening to see how little money most of those guys made given the sheer amount of digital disease they were pumping out into the Internet on a daily basis.
In fact, very few of these individuals made much money at all, and yet they were responsible for perpetuating a global crime machine that inflicted enormous damage on businesses and consumers. A quote in the book from Stefan Savage, a computer science professor at the University of California, San Diego (UCSD) encapsulates the disparity quite nicely and seems to have aged quite well:
“What’s fascinating about all this is that at the end of the day, we’re not talking about all that much money,” Savage said. “These guys running the pharma programs are not Donald Trumps, yet their activity is going to have real and substantial financial impact on the day-to-day lives of tens of millions of people. In other words, for these guys to make modest riches, we need a multibillion-dollar industry to deal with them.”




all this Circus and only 26000 $ ???
Thats really small money…to risk with federal prosecutions.
In many countries outside the US, $26k represents a pretty large sum, even a fortune.
JimV, like where? This is a tech crime. Bling costs the same everywhere. Some places people earn less but, the cost of manufactured goods is pretty much the same everywhere.
Considering they are probably in Russia (I assume because Mass hits where there) our government will have an extra difficult time tracking them down. I also doubt they will ever been found (unless someone who knows them turns them in) as they are most likely using anonymizing software and created the phishing email in an anonymous account. Only time will tell though.
If you think about it 26k is a ton. Expect more to follow.
Good site to follow:
http://howmuchwannacrypaidthehacker.com/
Here I am reading about the latest hacker disaster and someone offers me a link to click on. What are your credentials, Leopold? Are links offered in the Krebs columns vetted?
Gosh, where’s our trust in our fellow humans gone…
Not just cybercrime — this reminds me of the thousands of dollars of damage some thieves did to my car to steal my $300 stereo, which they probably pawned for $30.
Indeed. Office I worked at once was broken into through a window, and a handful of desktop computers stolen. So boss insisted that all internal doors were locked from then on. Next time, they just kicked in every door! Several orders of magnitude more damage, and for little extra reward. So next we need bars on the windows, metal shutters on the doors, and secure cases for every PC. Many thousand pounds of expense, and the criminals probably made about £50 on the machines they nicked..
Same idea with the copper thefts that were rampant a few years back — few dollars worth of scrap copper for the tweakers, many times that cost for the power companies to replace stolen grounding cables (never mind the safety issues until it was repaired).
Can this be? The bad guys can load bad stuff on a zillion systems in a few hours. The good guys, who knew of the security hole (and how to fix it) for a month did not get protection out and installed – and now blame their customers for not upgrading. If I thought poorly of Microsoft before, that ain’t nothing compared to my thought now.
Welcome to modern world racketerring..And roofing
The patch for this vulnerability was released 14th March – which was 3-4 weeks before the NSA hacks were released by Wikileaks that use this vulnerability. And that was three weeks before the malware was released. Soooo there was around eight weeks from release of patch to release of malware. Plenty of time for most home users to have gotten it installed, methinks, given that best practice is to have security patches install automatically, immediately. Not really sure what MS could have done over and above that TBH. They can’t force people to patch and they can’t force software on to people’s computers without their approval – that would be considered malware. Oh wait…
As shown over and over again ad infinitum, the weakest link in the security chain is between the seat and the input device…
+1
do you work in a company, really?
8 weeks is nothing.
You never deploy blindly. Never deploy on the first day so that you are not beta testing. Then you need to test your 50 applications for how hard security patches will harm business from running.
MS’s reliability has improved on Windows lifecycle, but we still face issues once a year at least, particularly with patches related to Excel.
It is a recurring unfair balance to decide on when and what to deploy.
It is a monthly process, and sometimes even more frequent depending on ongoing vulnerability exploitation in the wild.
Really no, in the life of a company, 3 to 8 weeks was not much.
Corporate IT do not let businesses work while only waiting of work to pop up. Plannings are already full for the next three months, and have limited deployment time windows.
Hopefully, we multiply protection layers to decrease risks.
Actually, 8 weeks *is* something, and that something is incompetence.
There are over 200 NHS trusts in the UK and we are told that 16 of them were affected. I used to work for an IT organisation that used to look after several NHS trusts and we patched like clockwork. On the other hand, we took on additional small NHS organisations and their IT was shambolic, often with Windows updates disabled entirely on the endpoints.
Essentially, those 16 NHS Trusts should have their IT teams disbanded and their IT budgets handed over to organisations that can provide competent IT services.
+1
8 weeks in a company that has it’s act together is plenty of time to deploy a patch to Dev environments, if no problem deploy patch to QA, if no problems deploy to Production environments.
Not that all — perhaps most — companies actually have their act together.
And some split the difference, the technical teams may have all their current operating systems patched, but the business has signed off on the risk of keeping obsolete operating systems still running because they don’t want to spend money to upgrade the applications that only run on those obsolete OSes.
The conference call for my group considering our 5600 physical and virtual servers and desktops took more man-hours than the actual work to finish patching few remaining vulnerable servers (40/1600) and the virtual desktops (which were scheduled to receive the patch the coming Wednesday and instead had it moved up to Friday evening). Not perfect, but not that bad…especially compared to the corporate overlords in Europe who were scrambling LOL.
The network I run in a Township has 130 workstations. I hate leaving group policy to install patches on demand. On Wednesday we have 3 or 4 systems that are choking on the updates.. But,,, this updating may have saved us.. Just do the updates people.. I also have to say that we constantly show screenshots of the bad email caught in our filters.. Scares the crap out of them and makes them a little smarter.. They take home that information.. Good information also spreads like a virus.. Thanks B. Krebs for your awesome site and information!
Well, in my case, Microsoft unrecoverably screwed up my Windows Update over a year ago, along with thousands of other people. So I haven’t been updating my system. I just did all the updates manually today.
Point being, don’t always blame the computer owner. In fact, don’t ever blame them: Microsoft has a duty to create update systems that always work, work automatically, and work even for the guy with an 80 IQ. If they don’t, Microsoft is responsible for when the internet gets taken down the next time due to flaws in their systems.
Well, them and the half of Russia & India that are running off one 12-year-old pirated DVD of XP.
drw writes: “Soooo there was around eight weeks from release of patch to release of malware”
Oh?
Did that patch release include Win Xp? One of the hardest hit OSes in this attack? Ah-ha. See the flaw in your statement yet?
Why should it include XP? When you agreed to the terms of the XP license on your machine, did the terms include infinite support?
“Not really sure what MS could have done over and above that TBH”
What are you, stupid? This whole problem was CAUSED by Microsoft’s crappy code. It’s clear from this that M$ does NOT have proper QA and testing and don’t even read the compiler warnings. Instead, they clearly work on the principle of “it compiled so ship it so we can get paid”.
And don’t whinge that “it’s impossible to write secure code” when M$ has never even tried: That’s as contemptible as Trump whining that “Who knew Healthcare is so HARD?”
Many years ago we had a case where the Corvair was “unsafe at any speed” and it led to GM finally learning a hard lesson after years of milking the public. It’s time that M$ gets to learn that selling crapware that’s clearly not “fit for purpose” will lead to being held responsible for the damages they ultimately cause.
We have a pilot, test then release cycle. Figure 11-14 days before a patch gets pushed out under normal circumstances. Now, add to it this:
1. Some clients want to turn off pcs after hours, but don’t want patching during day, only 1 day per week. Oh, and they forget to leave the machines on that one day most of the time.
2. Some run 24×7 and have to be manually patched. Sometimes it can be a month before we are allowed to patch.
3. These are computers we are talking about. Roughly 10% fail to patch for myriad technical reasons.
Just a few reasons why even responsible companies can be at risk (FYI, we manage about 2k computers, none affected by this malware.)
@Peter, How would you have handled the situation, other than MS (the good guys?) making it available via Windows/Microsoft update back in March, for all current versions of Windows?
1) Force the patch on every current Windows version without any exceptions, similar to what is done with Win 10?
2) Disable all current versions of Windows unless & until it was patched?
3) Continue to offer/push/require security updates for all versions of Windows back to Win 98 or perhaps earlier?
4) Something else?
If anything it would seem that MS’ culpability is allowing or not catching the flaw/bug/vulnerability in the first place. A flaw that existed for many years, and only now has come to light. Well it is likely that at least the NSA (are they the good guys too?) knew about the flaw (and perhaps MS did also at the behest of the NSA). So it was good while it lasted. The NSA isn’t going to admit to anything, nor should they.
For anyone that had their current versions of Windows set up with the recommended automatic updates turned on, then they would not have been hit. Now MS is offering updates to Win XP & 8.1 (Vista?). So seems they are doing the right thing.
I suppose “something else plus all of the above” comes to mind. I’ll take some guidance from the rules typical of product liability. If you sell ladders when you know, or should know, they tip in ordinary use, then you are obliged to both take corrective action and face up to the harm done. (Unless you sell guns!) In the larger frame we share the problem of having created a broad publicly available facility without enforceable structure. Imagine if any vehicle you care to devise and manner of usage were allowed on a broad private network of roads.
My gripe with Microsoft is the continuing failure to act when the hazard is increasingly apparent. It seems their management and talent resources have gone to the bottom line whereas they could have fostered the appropriate collective (governmental?) capacity.
Microsoft can’t help itself. What it says and does seems automatically disgusting. That said, these hackers are guilty of attempted murder and should be tracked down and killed. People keep saying that this sort of thing cannot be prevented. Oh, yes it can.
I know of a number of small businesses that leave the cash drawer open so if someone breaks in they don’t damage the cash register. Sometimes they even make it visible from the door or a window.
You people are ridiculous and obviously have no empathy for the engineering community. Yeah, this is Microsofts fault for not patching a 16 year old operating system because of course they should be devoting millions of dollars to development for a product that hasn’t made them a dollar in a decade. That makes sense. I just forgot they’re a profit driven business in a free market economy and mistook them for a philanthropic non-profit with unlimited funding. Oh and of course it’s their fault you haven’t upgraded your OS’ for 16 years.
That’s pocket change for companies if you ask me. All this hype and only $26K? Blah…
I agree with you 26k its pocket change.
zeus trojan was much bigger like 20miljon.
Only 26K so far. But if only 5% of the total machines infected pay. That is 2250*300 so, $675K. If everyone paid it would be 13.5mm
I think same way..but i think its just warm up.
its like they studied the ground
now everybody knows they are just poor loosers..got 26k only.
Nick is right. It hit late Friday. Wait until Monday when businesses first realize the impact of the malware and decision makers here from their IT people (who have been working all weekend.) The decision point for non-critical infections is six days away. Many will wait until the last minute hoping someone will find a work-around.
Ultimately, however, the perps will remain poor. Bitcoin is no longer anonymous as it once was. Once they sell a single portion of a single bitcoin they will be tracked down. Bitcoin mixers don’t work with large amounts. And since every nation is a victim, there won’t be any safe havens.
The authors of the extortionist, trying to avoid detection in sandboxes, made it possible to quickly stop the spread of the worm by registering a domain with a specific name. Only because of this it was possible to slow down the spread of the worm. At the moment, infections are only carried out in networks that do not have Internet access. But without access to the Internet, the extortionist has nothing else to do but to encrypt the files with a key wired into it beforehand. This will create a decryptor for machines that did not have access to the Internet during the attack.
An organization called shadow broker has been linked by several investigators to this attack. It seems most likely from prior attacks conducted by Shadow Broker that they are a front for Russian government hackers.
They could be attacking the British health system to gauge the effects of a crippling cyber attack on that system in conjunction with say, a nuclear attack. The ransom ware is most likely just a cover.
Why Russian government hackers should violate Ministry of Internal Affairs and Investigative Committee? These two are the most damaged in Russian Federation.
Er, well I’m pretty sure just the nuclear attack itself would be enough to cripple the NHS!
The interesting thing is if this could be done then just ask for a much smaller amount with some more convenient method, even if ultimately via bitcoin.
$300 is a lot, so you might think twice. But if you could get everything back for $25 now, $50 with a delay, would you hesitate?
Even if everything can be restored, it would take time and effort, likely exceeding $25.
If the ransom is priced less than even the hassle value of restoring from backup, it would more likely be paid at a much higher rate. At $25, how many would just simply give a credit card?
Give your credit card (details) to someone that is demanding money to release your encrypted files? That seems like a real smart move……
I think shutting down BitCoin would go a long way in deterring ransomware.
knife can be used for cooking food or killing.
so dont blame btc..its 100% unfair ,many honest bitcoins users
out there. Some use btc daily bases.
That’s practically impossible because:
1. Bitcoin isn’t centrally hosted, so you can’t go after any one person or entity to shut it down.
2. The individuals using crypto-currency have a vested interest in keeping their transactions anonymous, and will just move on to one of the thousands of other crypto-currency variants if Bitcoin is somehow taken down.
3. If some entity tries to shutdown every single crypto-currency in existence, the sad reality for them is that for every currency you take down, 10 more will take their place, guaranteed.
This is also ignore the encryption and anonymity features of all crypto-currency’s, which is a whole ‘nother beast entirely, one which would need to be tackled for each and every currency this theoretical entity tries to take down.
The only way to defeat the crypto-currencies is to criminalize any use of crypto-currencies in all countries of the world (as we want to do in Russia).
Crypto currencies value is based on trust and liquidity. If trust is eroded they are weakened. If there are barriers to use (liquidity) they are weakened. Starting a Crypto currency takes time and effort. Switching Crypto currencies takes time and effort. They already have a somewhat tainted reputation. High profile cases like this are not helping the reputation and may provoke a knee jerk action by authorities which may hurt “innocent” Crypto holders too. Governments still have many tools they can wield. A defence of switching to yet another Crypto currency is hardly a guarantee of protection.
They took down the NHS, that’s terrorism. They’re using bitcoin, that’s money-laundering in furtherance of terrorism. So tracking down a few thousand people who’ve bragged about mining and advocated bitcoin, then locking them up for a few weeks offshore under a security certificate, can be done.
Security services have taken over entire networks before: they’re all over the darknet and all over Tor already. So they can easily take over cryptocurrencies. Don’t think these people are stupid, and don’t think this fat kid from Petropavlovsk is going to live long.
Cryptocurrency goes away within the week. It’s a heatscore now, it’s radioactive. Governments will come down hard on what’s no more than a money-laundering system used by foreign criminals.
so bitcoin is the target here and not nsa for providing the exploit.
u dont understand IT much i see..
Multi version backup is still the best way to assure that you have a non encrypted version of your important files. If it is not ransomware, a dying hard drive or something else will byte you sooner or later.
I am not blaming victims, I am saying there are simple and inexpensive steps that can be taken, and really should be taken.
Don’t make it sound so simple. I have tried many, many home backup and network solutions, NAS, etc Most suck. Seriously suck. And the good ones are expensive and complicated.
Tired of hearing how every computer user must take specialized training on every backup and OS strategy out there (which changes every year). Technocrats have the answer for everything, more and more expensive and complicated technology! The average work-a-day individual doesn’t have time to baby sit their computer 24/7 tweaking, fussing, on an on.
The technocratic elite created this problem by making porous, unstable, one-off software designs – mostly so they can grab your personal information and sell it to 3rd parties or give it to the government to tack your activity.
The sheer magnitude of s/w updates required to keep systems stable and safe is outpacing anyone’s ability to manage.
It’s the arrogance of the elite who put blind faith in their mad skillz that is creating this problem.
As a 30+ year embedded dev, I know what I am talking about. Until we demand change, expect more crap.
But closed systems and state sanctioned corporate monopolies tell me that the worst is yet to come. We don’t have the courage to challenge conventional thinking and start punishing corporate executives in monopoly positions who insist on having access to my daily activity but then cause chaos when these features are exploited to cause worldwide damage.
Speaking of Russia, if you have nothing to hide, you have nothing to fear? Must be why Trump is so open with his tax returns.
We need safe secure systems.
cryptoprevent should stop most or all of these types of ransomware.
It resides in the registry and prevents modifications that are required by most of the ransomware to work.
Its free if you manually download updates and very reasonable if you purchase it which gets you automatic updates.
The banality of evil.
Maybe we should go back to paper files. Or atleast stop connecting infrastructure and medical systems to the internet ????
How does ransomware actually know which files to encrypt ?
Everything in the user profile ?
What if files are outside the user profile.
I’d be curious if there is any discrimination at all.
Everything on all disks with given extensions.
And this is why I think that authors are not from Russia – they didn’t encrypt 1c files. 1c is an accounting program which is used by almost all businesses there. Other crypters know about it and encrypt 1c files.
how much is crypter?full back ?
It wouldn’t be the first time people have left hints or clues to throw off law enforcement in tracking down the point of origin. E.g. mirai.
Wanna cry not cryptic 1c files means nothing.
North Korea is often suggested as a source. So far, they seem not to have cashed in any of the bitcoins.
They use a list of specific extensions:
http://blog.talosintelligence.com/2017/05/wannacry.html#h.9fka23gomuo8
Yeah, because Donald Trump isn’t “going to have real and substantial financial impact on the day-to-day lives of tens of millions of people”? Right….
I don’t understand, how in these times important London hospitals run in your servers the oldest windows xp o. s.
Try engineering firms. I have a DOS box and a Win ’95 still in service … BUT they are never used to ‘surf the net’
I work in IT team of a texas based hospital. We too were affected by this ransomware. Nurses in ICU were unable to access their files. They didn’t know which medicine to give. Patient’s life was at risk. It was scary, really scary.
It would be doubly scary for patients. This is why such attacks should be made capital crimes and the perps hunted down and killed.
An while all this happens, Microsoft is making millions in Windows’s users licensing their copies.
I think the real kidnaper is the Redmons company.
Long life to open source!
LINUX, originally written/started on Windows and targeting the same x86 architecture uPs.
Everyone is at the one foot level here flapping about the “small” amount of $26K.
Go up to the 1000 foot level and take a second look. Here a small patch with a simple attack program caused a worldwide panic.
Why? Is there another motive behind the curtain? It’s a given that IS departments are generally slow in deployment, so that is an advantage. (Why can they deploy so fast after an issue, but sooo slow before?) Plenty of good scrips out there. That is advantage. Create a panic—yes. Real reason….?
Hmmm….
That was my first thought. If it’s not NorKs, then it makes for a nice distraction not that the fit has really hit the shan on the Rissian Connection
Attention USA IT workers: What aspect of “backups” don’t you understand?
Attention USA computer companies: What part of “customer education” don’t you understand?
Ransomware is not something new. No one should pay a ransom for their data. I know that may be harsh, but paying the ransom only ensures that this problem will continue. If you have not made backups and get hit, the pain you feel from the data loss will guarantee that you never fail to back things up in the future.
We need “Cyber Walls” around the USA and around data centers and other places of information distribution that can start catching threats like this.
We are lucky in that our clients have no need of web traffic from outside the USA. This means we can block their sites and their email from most non-domestic traffic. There are still threats and hacking attempts, but we deal with much less than we did in the past. We also block user access that originates from hosting company IP ranges. We can’t block SMTP traffic from most hosting systems, but we have proprietary spam detection methods that keep things at a more manageable level.
How manageable? Well, for one thing our client’s web contact forms don’t use CAPCHAs.
And without giving too much away, our protection strategy does NOT involve expensive hardware and software. It did take some time to refine, but it’s shockingly low tech.
It is dangerously naive to believe that a “cyber wall” around any country, which is very unfeasible in the first place, especially for the country with the most international interests of all, the USA, would seriously protect systems inside its borders from malware. There are plenty of domestic threats.
+1.
I’d also, mainly, like international inplementation of “cyber walls” closer to some of the international perp countries, state-sponsored perps, organized perps–international “septic” control closer to the point where I/WE sometimes KNOW it originates.
“Domestic threats” fall under domestic jurisdication of the domestic rule of law. Non-domestic may or may not fall under the wishes of domestic law–repeated idea of international extradiction.
Any news or rumours about how this thing spread through the NHS so quickly? Out of all the hundreds of IT guys working on fixing this there must be some noice or clues about how it got in and how it spread
The other little gem that emerged from this situation was that in the NHS a lot of the computers were still Windows XP. And I just bet if you looked inside say Telefonica there’s a lot of XP there too.
From the final sentence, “…we need a multibillion-dollar industry to deal with them”.
Recent widerspread knowledge of a vulnerability, same widespread free ride-use of the Internet to use the vulnerability. From the reports I’ve read, the multibillion- dollar industry wasn’t what diminished Wana ransomware. As is often the case, the multibillion- dollar industry is protecting smaller enclaves of the Internet.
We live in a world where a job is hard to find and a high income job is almost impossible. A world where most security jobs requires a polygraph, extensive background checks, no criminal record, no drug record, etc. At the same time we have a materialistic society that values money above all. Many people would kill for this money. And, this is the conditions in the USA; imagine how bad it is in third world countries.
Is it really a surprise that this is happening or is it a surprise that there is not more of this occurring?
Communist just finishing off now.
long life for L. Trotsky
So don’t be a dumbass, get a decent education, don’t get a criminal record and drug record, and work for an honest living like everyone else.
“I’m going to get rich the easy way, by demanding ransom from hospitals” is the kind of attitude that gets zero respect from anyone who has to work for a living.
Wanna fight the injustice of teh ebil capitalism? Go get yourself a gun, go to the rich part of town, and threaten rich people at gunpoint, if you’ve got any balls. Otherwise you can take your Russia Today propaganda and stuff it, sunshine.
Amazing how nearly everyone here is missing the point.
This isn’t just about money. It is about fame and raising a giant middle finger to NSA and Microsoft.
It is ironic that profit/loss models are being used to assess the value of this mess.
They designed a “product” that was publicized, over night, all over the world and exploited a known vulnerability. What value do you assess to this? Microsoft and Apple would pay millions.
No doubt it was an exploit intended to be kept secret by NSA and Microsoft for use in a cyber attack. What goes around, comes around. As they say.
The only 100% certain outcome of this event is that we will learn nothing from it.
For sure, no one will challenge our misguided notions about the assumed benevolence of Microsoft and NSA.
The elite can always afford to buy another computer and pay someone to maintain it.
Expect more of the same.
Is it me or does this low dollar amount show that IT has learned a valuable lesson about ransomware over the last couple of years? It shows that even though they may not have patched, they didn’t need to pay, meaning they have figured out that backups and Shadow Copy are your best weapons in the fight against ransomware. Good job IT guys!
InfoSecPinas @InfoSecPinas May 13
More
“Infected with #WannaCry? The password for the zip file is: WNcry@2ol7 :D” #ransomware #wannakill #WCry via @official_roy #infosec
I suspect that the perpetrators’ revenues would be much higher save the fact that it takes time to set up a BTC wallet and to have it funded, and the deposits confirmed. A target of the ransomware who did not already have a funded BTC exchange account would be unlikely able to pay the ransom in the first three days. Perhaps they could within seven days. Let’s see how this plays out in the next few days.
Yes they learned. But they will attack again.
13 may friday and friday night..was special date(satanists-hexacon)
Brian – Just to remind you. You could have prevented this attack had you had the courage to publish the August 2007 article. Just as Digicash had bit the dust with our emergence, this ridiculous blockchain/DLT/cryptocurrency detour with its 2+ billion of malinvestment would have never seen the light of day had you, instead of being part of the solution, not wimped out and submitted to becoming part of the problem.
Doug
Huh?
“… devastating Wana ransomware attack…”
Brian, you and anybody else who thinks that a mere 75K machines, or even 200K machines being hacked/ransomed is “devastating” had better think again, because there is much much worse ahead.
Remember, there was just one tiny flaw in this ransomware which allowed it to be trivially turned off, in bulk, via one single “weak link”… which, fortunately, some researcher noticed and took control of. The criminals who launched this will be back, and they won’t be making THAT mistake again.
Maybe it won’t be this specific strain of badware, but one day we are all going to wake up, unfold the morning papers, and learn that one hundred or two hundred *million* systems have been compromised, by yet another zero-day, but one that’s been wrapped in a rather less flawed package which is not so trivially defeated.
On that day, you’ll pick up the phone to call your friend to tell him the news, and you will hear nothing. No dial tone, no fast busy, nothing. So then you’ll turn on CNN to see what they have to say about all this, and your flatscreen will be dark, not because your TV has been hacked…
although that’s possible too… but because there will be no signal coming down the line from Comcast, or Cox, or whoever. And it won’t be because any part of their distribution networks have been hacked. It will be because the machines that control their satellite links will have fallen victim. Everything is interconnected, and nothing works unless everything works.
On that day, emergency rooms -everywhere- will shut and people -will- die.
This WanaCry thing is just a very small early warning of what is inevitably coming. It is not at all a stretch to say that civilization, as we know it, has come to rely upon untold BILLIONS of lines of code, very little of which has ever been formally validated. As a result, the entire planet, and every nation, is and remains just one buffer overflow coding error away from digital Armageddon.
Multiple researchers have confirmed that such variants are out now.
…new variants of WanaCry.
but why we keep critical systems in the network?
In the hospital can make 2 different networks primary and second.
primary connected with global internet.
second network only inside hospital network.
and buffer server with one backup server …buffer will be between primary and second network.
Yes, you hit it! Two major networks. They are called “Production” and “Admin.” The twain shall never meet!!!