A few weeks back, HR and financial management firm Workday.com sent a security advisory to customers warning that crooks were sending targeted malware phishing attacks at customers. At the same time, Workday is publishing on its site a list of more than 800 companies that use its services, making it relatively simple for attackers to chose their targets. This post examines whether it makes sense for software-as-a-service (SaaS) companies to publish lists of their customers when those customers are actively under siege from phishers impersonating the SaaS provider.
At its most basic, security always consists of trade-offs. Many organizations find a natural tension between marketing and security. The security folks warn that publishing too much information about how the company does business and with whom makes it way too easy for phishers and other scammers to target your customers.

A screenshot of a phishing lure used to target Workday customers.
The marketing folks, quite naturally, often have a different perspective: The benefits of publishing partner data far outweigh the nebulous risks that someone may abuse this information.
So the question is, at what point does marketing take a backseat to security at SaaS firms when their customers are being phished? Is it even reasonable to think that determined attackers would be deterred if they had to pore through press releases and other public data to find a target list?
When I first approached Workday in researching this column, I did so in regard to an alert they emailed customers earlier this month. In the alert, Workday warned that customers using single-factor authentication to access Workday were being targeted by email phishing campaigns. The company said there was no evidence to suggest the phishing a result of the Workday service or infrastructure, but rather it was the result of phishing emails where individuals at customer organizations shared login credentials with a malicious third party. In short, they’d been phished.
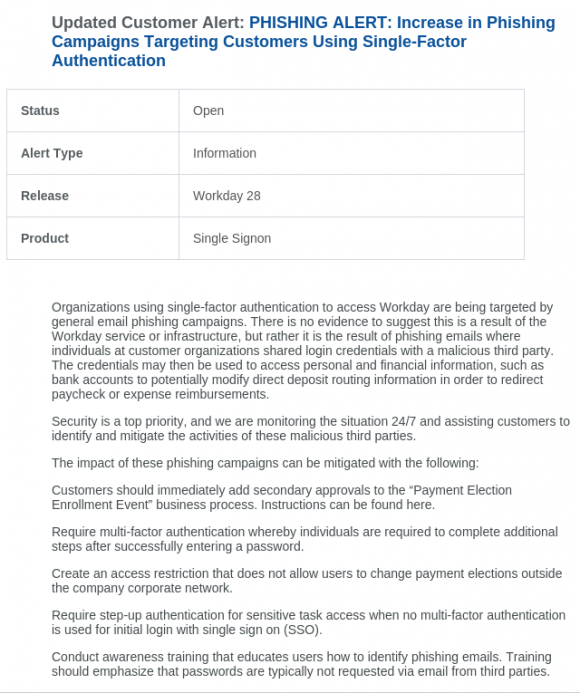
A portion of the phishing alert that Workday sent to its customers.
Workday advised customers to take advantage of the company’s two-factor authentication systems, and to enable secondary approvals for all important transactions.
All good advice, but I also challenged the company that it maybe wasn’t the best idea to also publish a tidy list of more than 800 customers on its Web site. I also noted that Workday’s site makes it simple to find an HTML template for targeted phishing campaigns. Just take one of the companies listed on its site and enter the name in the Workday Sign-in search page. Selecting Netflix from the list of Workday customers, for example, we can find Netflix’s login page:
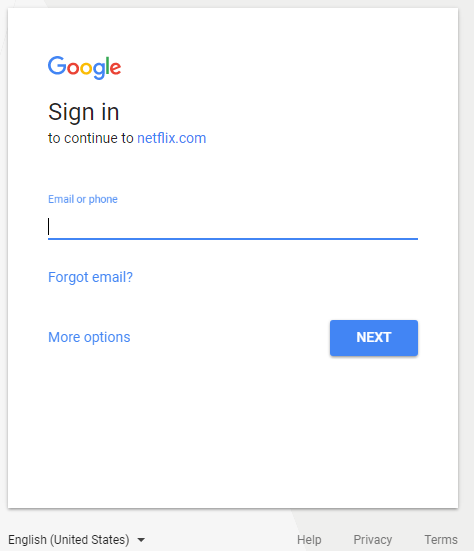
Netflix’s sign-in page at Workday.com.
That link opens up a page that allows Netflix customers to login to Workday using Google’s OAuth system for linking third-party apps to Google accounts. It’s a good thing we haven’t recently seen targeted phishing attacks that mimic this precise process to hijack Google accounts.
Oh wait, something very similar just happened earlier this month. In the first week of May, phishers began sending Google Docs phishing campaigns via Gmail disguised as an offer to share a document. Recipients who fell for the ruse ended up authorizing an app from Google’s OAuth authentication interface — i.e., handing crooks direct access to their accounts.
Before I go further, let me just say that it is not my intention to single out Workday in this post: There are plenty of other companies in its exact same position. The question I want to explore is at what point does marketing get trumped by security? For me, the juxtaposition between Workday’s warning and its priming the pump for phishers at the same time seemed off.
Workday wasn’t swayed by my logic, and they referred me to an industry analyst for the finer points of that perspective. Michael Krigsman, a tech analyst and host at cxotalk.com, said he often advises smaller companies that may be less sophisticated in their marketing strategies to publish a list of customers on their home pages.
“Even when it comes to larger companies like Workday, they’re selling so many seats that this information is highly public knowledge and very easy to get,” Krigsman said. “If you’re interested in Workday’s customer lists, for example, you can easily find that out because Workday puts out press releases, their customers put out press releases, and this gets picked up in the trade press.”
WHERE I COME FROM
Fair enough, I said, and then I explained my historical perspective on this topic. Ever since I broke a series of stories about breaches at major retailers like Target, Home Depot, Neiman Marcus and Michaels, I’ve been inundated with requests from banks and credit unions to help them figure out which merchants were responsible for credit and debit card fraud that was costing them huge financial losses.
They sought my help in figuring this out because Visa and MasterCard have contractual ways to help banks recover a portion of the funds lost to credit card breaches if the financial institutions can show that specific fraud was traced back to cards all used at the same breached merchant.
As a result, I’ve spent a great deal of my time over the past few years helping these financial institutions find out for themselves which of their cards were breached at which merchants — pointing them to underground forums where — if they so choose — they could buy back a small number of cards and look to see if any of those had a commonality (known in financial industry parlance as a “common point of of purchase” or CPP).
I’ve never sought nor have I received remuneration for any of this assistance. However, one could say that this assistance has paid off in the form of tips about CPPs from various financial industry sources that — in the aggregate — strongly point to breaches at major retailers, hotels and other establishments where credit card transactions are plentiful and traditionally not terribly well protected.
But even financial institution fraud analysts who are adept at doing CPP analysis on cards for sale in the underground markets can be blind to the breach whose only commonality is a third-party provider — such as a credit card processor or a vendor that sells and maintains point-of-sale devices on behalf of other businesses.
Nine times out of ten, when a financial institution can’t figure out the source of a breach related to a batch of fraudulent credit card transactions, the culprit is one of these third-party POS providers. And in the vast majority of cases, a review of the suspect POS provider shows that they list every one of their customers somewhere on their site.
Unsurprisingly, Russian malware gangs that specialize in deploying POS-based malware to record and transmit card data from any card swiped through the cash register very often target POS providers because it is the easiest way into the cash registers at customer stores. Interview the individual store managers who operate compromised tills — as I have on more occasions that I care to count — and what you invariably find is that the malware got on their POS systems because an employee received an email mimicking the POS provider and clicked a booby-trapped link or attachment.
Alas, Workday was unmoved by my analysis of the situation.
“Spotlighting shared success with our customers helps our businesses grow, but security is Workday’s top priority,” the company said in a statement emailed to KrebsOnSecurity. “We are vigilant about identifying issues and consulting customers on best practices — such as deploying multi-factor authentication or conducting security awareness training for their employees– in order to continually help them sharpen security and protect their businesses.”
For his part, CXOTalk’s Krigsman said he was moved by the story about the POS providers.
“So the question becomes is this a strong enough threat that this is a trade off we should make,” Krigsman said. “You make a compelling argument: On the one hand, for marketing and customer convenience purposes companies want to put this all out there, but on other hand maybe it’s creating a bigger threat.”
I should note that regardless of whether a cloud or SaaS service publishes a list of companies they work with, those companies may themselves publish which SaaS providers they frequent. As Mark Stanislav of Rapid7 explained in Feb. 2015, it’s not uncommon for organizations to expose these relationships by including them in anti-spam records that get published to the entire world. See more of Stanislav’s research here.
What do you think, Dear Readers? Where do you come down on the line between marketing and security? Sound off in the comments below.




I think it’s unprofessional to blare out all your customers’ names. But i am not one to buy things based on the sole fact that Company X or Y did it and therefore so should I. I think less of them going around promoting getting on a bandwagon.
If your services are that good, they should stand on their own without you having to say, “Well, Microsoft does it, too, so you should!” So what if Microsoft does? Do you literally own a Microsoft 2.0? Nobody does. Your situation is unique and what you need isn’t what Microsoft or somebody else needs.
Also, word-of-mouth marketing and people vouching for you only works if you let the people who love your services do the talking rather than you screaming out, “Hey, here’s all the people that love me”.
As a potential customer, there are instances where knowing a vendor’s customer roster is indeed valuable. For example, if you are shopping for an IaaS provider there is a distinct difference between a provider with a list that is comprised of mom and pop shops and one that lists Fortune 500 companies as customers. Being a small company, it is encouraging to know an IaaS provider has passed muster for a company with deeper pockets and a lot more at stake.
Not necessarily. It could just mean that the big Fortune 500 bought a trial of your software and that does technically make them a customer. It doesn’t mean it’s in active use or even the scale or scope of the software’s use. It’s a meaningless statistic.
My comment uses the IaaS (Infrastructure as a Service) industry as the example. Investing on cage space or even just a full rack and not “use it” would be highly unlikely.
Krigsman’s quote reads “One the one hand,” should read “On the one hand,”.
It doesn’t matter since their SSL certificate will contain a subjectAltName dns= entry for every client they host.
That will depend a tremendous deal on how they are implementing SSL – you can easily have this information obfuscated if you have SNI implemented with individual domain vhost records.
However, yes, public ssl records are incredibly useful for this and with the availability of crt.sh the SSL history of any given domain has become tremendously more transparent and much more easily mined for information.
Hi Brian. My two cents worth is:
Too many companies give out too much information via the Web – period. When I can do a basic Whois search and find an email address i.d. to a sysadmin, that’s being ignorant about the true realities of cyber hacking. From my perspective, management teams don’t have a grasp about what an APT can do to their business through researching the Web. From public records, private websites, social sites and “announcements”, the blackhat community is alive and well. I am also not one to purchase services from XYZ company just because they did business with a fortune 500. It depends upon my specific business needs and not what the Marketing department thinks I should do to solve a problem. Then again, I am a contracting CCISO and love to help solve problems. James.
Completely agree with your statement.
Agree with your findings and have seen many higher level executives not really care about the security. I also found that, few organizations using same credentials for all websites and when data breach happened on one website, they hardly change credentials on other websites. Isn’t it important?
Security through obscurity isn’t security? it should’t matter that these are published. That said… seems like too many vendors aren’t taking security seriously.
For a determined attacker this is probably true, but for this type of threat we’re not talking about an actor who is targeting a single company, so security through obscurity is probably sufficient. They are looking to attack a wide swath of targets indiscriminately at the lowest cost possible. Keeping information private adds extra work which they are not likely to put in when others make their information public. You don’t have to be the fastest antelope in the herd, just not the slowest.
Good question to debate Brian. As someone looking to buy a product or service, knowing that a company has done business with a fortune 50 gives them credibility – to a point. I personally want to speak with someone who has used it before I move to evaluate it further. In my opinion it’s fine for a company to be more vague and say “we do business with 6 of the Fortune 50” and then let me ask for a reference I can speak to. That may help a little but it wouldn’t be too hard to figure out who those companies are. In the end, I’m not sure we’d win a battle with marketing as they need to advertise to drive business. I think in this area we are going to have to rely on innovative technology and user education to prevent workers from falling prey to phishing attacks.
Security always trumps marketing…always.
Looking for product recommendation…consider posting to a trade listserv asking for suggestions or feedback on specific vendor. This is something we do in the financial sector. Someone will ask “has anyone used XYZ vendor? If so, contact me off-list.” I have found this invaluable.
If you going to kill the snake cut off the head !!
Thats the only way to do it !!
I think the customers have an option in contracting to not allow SaaS vendors like WorkDay put their logo on their site. At my previous employer we went through an implementation of WorkDay and they consulting us in InfoSec on this. We opted to not put our logo on their site. Just checked, and it still isn’t there.
Rich – Can you forward the link, please?
Sure. You can check here: https://www.workday.com/en-us/customers.html#?q=
Just don’t use it to find your next phishing target 😉
Can also get the list of companies along with a whole bunch of uneeded data through their API they use to get the list of customers https://api.mktg.workday.com/v1/solr/us1?requestType=search&api=customer&q=&rows=1000 … needless to say this is a perfect example of excessive information disclosure.
Marketing by “Monkey see, monkey do.” — it’s incredibly common and powerful, and decision makers are always comparing themselves to other companies. Many execs would see it as prestigious to place their logo on Workday’s site, and brag via news release. It seems chintzy to me, but there are so many other ways to assemble a client list. Attempting to conceal a business relationship is security theater unless we expect senior execs not to brag in writing anymore.
“Spotlighting shared success with our customers helps our businesses grow, but security is Workday’s top priority,” – uh, clearly not.
New / Small business really struggle to get themselves noticed in the big wide internet world. Landing a big name can really help people look again rather than passing you by. Whether that’s founded in common sense or stupidity is irrelevant, it does work from a marketing perspective.
I’ve made the security case on this before, but leadership in these kinds of businesses tend to be in more of a “if we don’t sell stuff soon we’re bust” mindset, where security takes a back seat as being surviving with risks > not surviving securely.