A few weeks back, HR and financial management firm Workday.com sent a security advisory to customers warning that crooks were sending targeted malware phishing attacks at customers. At the same time, Workday is publishing on its site a list of more than 800 companies that use its services, making it relatively simple for attackers to chose their targets. This post examines whether it makes sense for software-as-a-service (SaaS) companies to publish lists of their customers when those customers are actively under siege from phishers impersonating the SaaS provider.
At its most basic, security always consists of trade-offs. Many organizations find a natural tension between marketing and security. The security folks warn that publishing too much information about how the company does business and with whom makes it way too easy for phishers and other scammers to target your customers.

A screenshot of a phishing lure used to target Workday customers.
The marketing folks, quite naturally, often have a different perspective: The benefits of publishing partner data far outweigh the nebulous risks that someone may abuse this information.
So the question is, at what point does marketing take a backseat to security at SaaS firms when their customers are being phished? Is it even reasonable to think that determined attackers would be deterred if they had to pore through press releases and other public data to find a target list?
When I first approached Workday in researching this column, I did so in regard to an alert they emailed customers earlier this month. In the alert, Workday warned that customers using single-factor authentication to access Workday were being targeted by email phishing campaigns. The company said there was no evidence to suggest the phishing a result of the Workday service or infrastructure, but rather it was the result of phishing emails where individuals at customer organizations shared login credentials with a malicious third party. In short, they’d been phished.
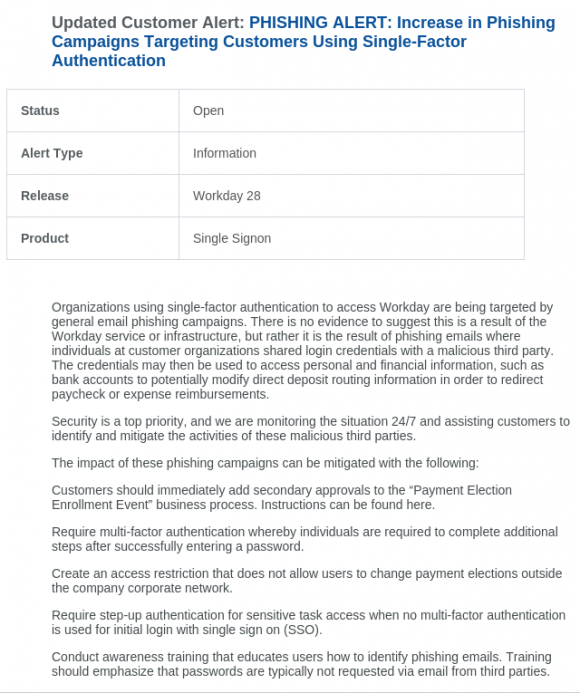
A portion of the phishing alert that Workday sent to its customers.
Workday advised customers to take advantage of the company’s two-factor authentication systems, and to enable secondary approvals for all important transactions.
All good advice, but I also challenged the company that it maybe wasn’t the best idea to also publish a tidy list of more than 800 customers on its Web site. I also noted that Workday’s site makes it simple to find an HTML template for targeted phishing campaigns. Just take one of the companies listed on its site and enter the name in the Workday Sign-in search page. Selecting Netflix from the list of Workday customers, for example, we can find Netflix’s login page:
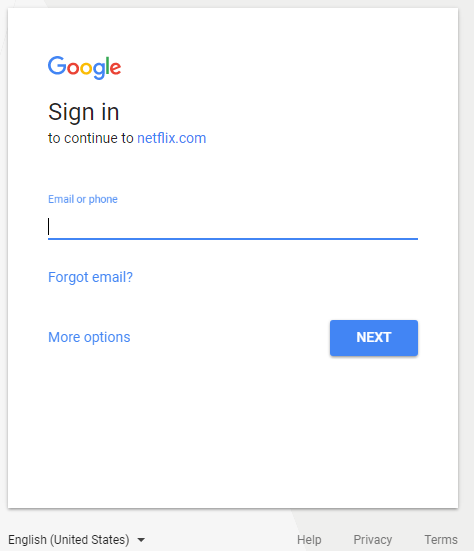
Netflix’s sign-in page at Workday.com.
That link opens up a page that allows Netflix customers to login to Workday using Google’s OAuth system for linking third-party apps to Google accounts. It’s a good thing we haven’t recently seen targeted phishing attacks that mimic this precise process to hijack Google accounts.
Oh wait, something very similar just happened earlier this month. In the first week of May, phishers began sending Google Docs phishing campaigns via Gmail disguised as an offer to share a document. Recipients who fell for the ruse ended up authorizing an app from Google’s OAuth authentication interface — i.e., handing crooks direct access to their accounts.
Before I go further, let me just say that it is not my intention to single out Workday in this post: There are plenty of other companies in its exact same position. The question I want to explore is at what point does marketing get trumped by security? For me, the juxtaposition between Workday’s warning and its priming the pump for phishers at the same time seemed off.
Workday wasn’t swayed by my logic, and they referred me to an industry analyst for the finer points of that perspective. Michael Krigsman, a tech analyst and host at cxotalk.com, said he often advises smaller companies that may be less sophisticated in their marketing strategies to publish a list of customers on their home pages.
“Even when it comes to larger companies like Workday, they’re selling so many seats that this information is highly public knowledge and very easy to get,” Krigsman said. “If you’re interested in Workday’s customer lists, for example, you can easily find that out because Workday puts out press releases, their customers put out press releases, and this gets picked up in the trade press.”
WHERE I COME FROM
Fair enough, I said, and then I explained my historical perspective on this topic. Ever since I broke a series of stories about breaches at major retailers like Target, Home Depot, Neiman Marcus and Michaels, I’ve been inundated with requests from banks and credit unions to help them figure out which merchants were responsible for credit and debit card fraud that was costing them huge financial losses.
They sought my help in figuring this out because Visa and MasterCard have contractual ways to help banks recover a portion of the funds lost to credit card breaches if the financial institutions can show that specific fraud was traced back to cards all used at the same breached merchant.
As a result, I’ve spent a great deal of my time over the past few years helping these financial institutions find out for themselves which of their cards were breached at which merchants — pointing them to underground forums where — if they so choose — they could buy back a small number of cards and look to see if any of those had a commonality (known in financial industry parlance as a “common point of of purchase” or CPP).
I’ve never sought nor have I received remuneration for any of this assistance. However, one could say that this assistance has paid off in the form of tips about CPPs from various financial industry sources that — in the aggregate — strongly point to breaches at major retailers, hotels and other establishments where credit card transactions are plentiful and traditionally not terribly well protected.
But even financial institution fraud analysts who are adept at doing CPP analysis on cards for sale in the underground markets can be blind to the breach whose only commonality is a third-party provider — such as a credit card processor or a vendor that sells and maintains point-of-sale devices on behalf of other businesses.
Nine times out of ten, when a financial institution can’t figure out the source of a breach related to a batch of fraudulent credit card transactions, the culprit is one of these third-party POS providers. And in the vast majority of cases, a review of the suspect POS provider shows that they list every one of their customers somewhere on their site.
Unsurprisingly, Russian malware gangs that specialize in deploying POS-based malware to record and transmit card data from any card swiped through the cash register very often target POS providers because it is the easiest way into the cash registers at customer stores. Interview the individual store managers who operate compromised tills — as I have on more occasions that I care to count — and what you invariably find is that the malware got on their POS systems because an employee received an email mimicking the POS provider and clicked a booby-trapped link or attachment.
Alas, Workday was unmoved by my analysis of the situation.
“Spotlighting shared success with our customers helps our businesses grow, but security is Workday’s top priority,” the company said in a statement emailed to KrebsOnSecurity. “We are vigilant about identifying issues and consulting customers on best practices — such as deploying multi-factor authentication or conducting security awareness training for their employees– in order to continually help them sharpen security and protect their businesses.”
For his part, CXOTalk’s Krigsman said he was moved by the story about the POS providers.
“So the question becomes is this a strong enough threat that this is a trade off we should make,” Krigsman said. “You make a compelling argument: On the one hand, for marketing and customer convenience purposes companies want to put this all out there, but on other hand maybe it’s creating a bigger threat.”
I should note that regardless of whether a cloud or SaaS service publishes a list of companies they work with, those companies may themselves publish which SaaS providers they frequent. As Mark Stanislav of Rapid7 explained in Feb. 2015, it’s not uncommon for organizations to expose these relationships by including them in anti-spam records that get published to the entire world. See more of Stanislav’s research here.
What do you think, Dear Readers? Where do you come down on the line between marketing and security? Sound off in the comments below.




The best part of the article is the fact that Netflix has a subdomain called https://meechum.netflix.com/ for the great late Edward Meechum. Great article Brian!
I had a small chain of customers we provide support for get targeted with “this is tech support, we need to log in to your computer” phone scams, leading to a couple of breaches. The scammers used our company name in the phone calls, and the fact that they were our customer was available on our website.
Took me an unreasonable amount of arguing to get the website changed, and they still plaster social media with that crap regularly. I’m honestly not sure it’s possible to get through to marketing/sales regarding security.
JMHO but security trumps advertising every time and security can be used as part of an advertising campaign. Publishing customer lists only enables the crooks to try hacking or phishing those sites too.
Many sites now require two factor authentication. It’s a pain sometimes but getting hacked or phished is a much bigger pain so I use it. Having good security on your computer also helps a lot but when an email comes in that is not one you are familiar with, it is a good idea to check the properties and see where it is actually coming from – although that doesn’t always work either. If in doubt, throw it out or delete it.
Maybe they should put pressure on their POS providers if they are so concerned about security. I agree that making the phishers job easier by publishing these lists makes the marketing ploy look much less inviting. Seems like if you going to do that, you need to jack up your security game plan to help your customers on that end of the risk scale.
Security takes priority over a company marketing it’s pfishabity. Just sayin’.
To get a more balanced response of security vs marketing we need to poll the users on the (fictitious) sister web site Krebs on Marketing.
Such a poll would undoubtedly find “security guys worry too much” as the #3 result, just behind, #2 can you help me reset my password? and #1 how do I connect my iphone to the company wifi?
All this talk of polling made me want to add a poll to the bottom of this post. I just did that. Vote!
Graphics keys linked to proprietary variable matrix is a better way to secure transactions across the internet. Mobiles can be ported and authentication apps can be key-logged. 2nd factor fails if first factor is compromised BK has been writing about authentication weaknesses for years but no one is listening. Using personal information in identity procedures is reckless it exposes users to identity theft. It is easily phished or can be accessed through compromised databases BK has been writing about this for years but no one is taking action to implement alternatives to protect users it easier to simply blame the customer and claim it is their responsibility.
I’d say that reasonable security needs outweigh the desires of marketing. If there’s no sales because the providing the end product leads to client insecurity, then eventually there will be no money to invest in marketing activities.
The reality is that many phishers are determined, professional organized crime outfits. In the face of such an adversary, withholding customer or vendor lists—even if possible—would likely be a temporary nuisance instead of being a critical step in erecting a defensible security posture.
very un-krebs like to ridicule a company encouraging pushing clients to 2FA or MFA. however, i agree this is a very complex dilemma between security and marketing. I would also suggest that another company making a product decision based simply on seeing another large company on a public website is a bit overblown.
Focusing on omitting customer publication on SaaS provider websites is like trying to create security through obscurity. It appears the pawn is simply being pushed to another square on the board and not offering any real protection.
Follow the money would be the operative phrase. Marketing serves as the foundation for organizational profit centers. Unless a commercial organization is a MSSP, PSSP, security appliance or software OEM, information security is a cost. Revenue generation, in most cases, holds a superior position to funding costs of operation. Yes, I applaud the argument that without proper information and related resource protection an organization may lose market attraction and/or intellectual property that enables revenue generation. This argument, sadly, is often but a footnote to financial statements — therefore of little visibility to investors.
Great article
A service provider will (usually) only publish customer lists if their customers agree to be on publicly available lists. Usually there are options to act as a reference for a provider WITHOUT being on publicly available lists. So I’d add that a certain amount of responsibility lies with SaaS customers as well.
I would be livid if a supplier publicly announced I was a customer without permission.
What happened to privacy and non-disclosure?
As a business I don’t want to give my competitors my customer list. A stupid thing on workday’s part.
reminds me of ‘ i never mentioned israel or the name israel’.
Integrate some security thinking into Marketing department. The honest analysis of risk should point them in the direction they need to go. From a conversational point of view “we server 100 of the top 500 companies in sector X” is just as convincing as naming each and every company. Knowledge of who is doing what and with whom is very powerful. Personally all my time with any marketing department seems to boil down to how much information can we shoot out and how fast, without regard for how small bits of ‘NON PII” can be assembled over time by adversaries. Ignorance is dangerous to everyone involved.
woow
http://www.dailymotion.com/video/x5lvunn_federal-court-convicts-former-us-rep-of-fraud_news
Great article Brian, and you are asking good, pointed questions that we all should consider. Many of my clients and employers, past and present, specifically restrict this kind of “publicity” in their contractual agreements. Admittedly, it remains relatively easy to search out customers of SaaS providers, but I am in favor of making it more difficult for bad actors to “find” us. Thanks for another great piece.
I find that I prefer the service providers that DO NOT list their customers on their website or marketing media. I have often explicitly requested as such in contract negotiations.
Reason: The less any attacker knows about the partnerships my organization may have other business entities the better off we will all be for many reasons.
Goes back to a lesson I learned in my many years in the military:
Do not give the enemy a target unless doing so would make them a target.
Excellent article. I appreciate how you laid out the background as well to many of the issues going into this balancing act between marketing and security.
With respect to Workday.com listing 800+ customers, I consider that excessive for marketing purposes. No customer is going to scroll through all 800 in order to make a decision whether or not to enroll in Workday.com services.
Workday.com itself highlights ten customers when you first go onto their Customer page, nicely highlighting the range and diversity of business sectors they’re servicing. Well and good.
Then as you scroll down the page, there’s another 24 customers, many with quotes extolling Workday.com’s services. Also illustrative of the industries and sectors that find such services useful.
Unfortunately, all that is followed by a button to “Load More>” customers.
In this case, I think their marketing department should pick which 34 customers best represent the customer base, and perhaps explicitly list and describe their service markets.
In my opinion, what’s there on Workday.com’s website constitutes poor marketing coupled with what I perceive is a lack of marketing focus. It’s easier to list everyone than to try and formulate a message underlying the Customer web page, then pick which customers best represent their customer base. After all, someone might get offended or consider the selection process a mistake.
Workday.com is also making their prospective customers work too hard to figure out whether Workday.com is servicing others in the same industry or sector. That translates into losing prospects as they browse for alternatives.
Bottom line, I believe Workday.com’s marketing department is not improving their impact on prospects by including such a large customer base, but instead are discouraging them.
Combine all that with your article, Mr. Kreb, and I would say that Workday.com is being irresponsible with their customers security by painting 800+ targets rather than 34.
Poor marketing. Poorer security practices in their marketing. Unfortunately, most companies’ marketing departments need concern themselves only with attracting customers, not operations, and that’s not confined to computer service providers.
Thank you for your work, Mr. Kreb. Very much appreciated.
And now my apologies, Mr. Krebs. I’d always read it as “Kreb’s On Security” and should have checked prior to posting.
While I’m inclined to agree that they shouldn’t post their lists in the interests of security… I think we can agree that all discussions in the past is that one can’t rely on security through obscurity.
They have a reasonable market purpose behind publishing their lists. It validates that their company has clients, isn’t going to fold in the middle of a contract, and probably does generate leads.
That said, it cuts down one step for any attacker who is performing recon. It makes more sense defensively to make the attackers probe to find out their target’s environment, not easily discover a trusted outsider.
Where this leads is to the need to have a validated communications channel. Which is easier said than done. The easiest and best thing that can be done is for Workday and the other SaaS providers to make their 2factor offerings a requirement and not merely a suggestion.
In answer to the question: While it is true the lists make it easier to attack and as such they probably shouldn’t be naming every and all customer. The answer is no, it doesn’t mean the lists come down because removing them doesn’t remove or reduce the threat. Nothing stops the phishers from sending a Workday themed email to all companies, regardless of whether they actually are a customer. So removing the lists only increases the difficulty for a targeted phishing attack.
We’ve been adding language to all our cloud contracts requiring breach notification of a customer on our associated cloud platform. Thinking there is if one gets breached there is an increased likelihood others will also, of course depends on the platform. Legal departments resist this so we have been successful maybe 30% of the time, and that is being generous.
The quintessential quandary for corporations: We can do the right thing OR we can make money.
My last job they thought it was cool, likely the marketing department to put everyone’s name and title on an about us page.
This lead to endless attempts to get us to pay bogus invoices. I had to educated the AP people in how to carefully check headers to see if it actually came from the CEO etc.
I did so well I’d get preemptive calls. Until such time I got marketing to take down everyone and only the first name of executives without their titles.
“Where do you come down on the line between marketing and security?” I think if they were to send this post to their outside counsel, I’d guess they would get a quick education on the difference between negligence and gross negligence and related liability:
“Gross negligence is a *conscious and voluntary* disregard of the need to use reasonable care, which is likely to cause foreseeable grave injury or harm to persons, property, or both. It is conduct that is extreme when compared with ordinary negligence, which is a mere failure to exercise reasonable care.”
Brian, you are not going to win this one.
Look at this purely from a business perceptive. If a Workday customer gets phished, what is the financial impact to Workday? Almost nothing. Other than giving the customer expressions of sympathy for being phished and assigning junior employees to handle press inquiries from you.
The only impact to Workday is that future unsolicited emails to customers will be suspected of being a phishing email. I use Workday as an example, but this really applies to all service providers.
As an aside, I think it would be nice if companies who were aided by Brian would hit the Donate button on the blog as a thank you for his assistance. Or maybe hire him as a guest speaker to executives and the security team. Or buy a box of his books.
Ah, yes, workday. My company uses that, among other things.
Can ANYONE tell me why a freakin’ HR and other document system could *possibly* require flash?
Other than, perhaps, people in HR really want to make music videos….
A customer-centric company would not publish its customer list. How much, if any, benefit accrues to the customer when the vendor crows about a newly signed customer? It should be the customer’s prerogative to publicize the vendor it is using.
The reality, of course, is that there is so much leakage of what should be private data that criminals are likely to be able to discover this information through other means. But that doesn’t mean firms should not make an effort to prevent crime.
Just because my home can easily be burglarized does not justify my giving up and leaving my door open.
I don’t trust any company that says ‘security is our top priority’. Because it’s not.