In February 2017, authorities in the United Kingdom arrested a 29-year-old U.K. man on suspicion of knocking more than 900,000 Germans offline in an attack tied to Mirai, a malware strain that enslaves Internet of Things (IoT) devices like security cameras and Internet routers for use in large-scale cyberattacks. Investigators haven’t yet released the man’s name, but news reports suggest he may be better known by the hacker handle “Bestbuy.” This post will follow a trail of clues back to one likely real-life identity of Bestbuy.
At the end of November 2016, a modified version of Mirai began spreading across the networks of German ISP Deutsche Telekom. This version of the Mirai worm spread so quickly that the very act of scanning for new infectable hosts overwhelmed the devices doing the scanning, causing outages for more than 900,000 customers. The same botnet had previously been tied to attacks on U.K. broadband providers Post Office and Talk Talk.
Security firm Tripwire published a writeup on that failed Mirai attack, noting that the domain names tied to servers used to coordinate the activities of the botnet were registered variously to a “Peter Parker” and “Spider man,” and to a street address in Israel (27 Hofit St). We’ll come back to Spider Man in a moment.
According to multiple security firms, the Mirai botnet responsible for the Deutsche Telekom outage was controlled via servers at the Internet address 62.113.238.138. Farsight Security, a company that maps which domain names are tied to which Internet addresses over time, reports that this address has hosted just nine domains.
The only one of those domains that is not related to Mirai is dyndn-web[dot]com, which according to a 2015 report from BlueCoat (now Symantec) was a domain tied to the use and sale of a keystroke logging remote access trojan (RAT) called “GovRAT.” The trojan is documented to have been used in numerous cyber espionage campaigns against governments, financial institutions, defense contractors and more than 100 corporations.
Another report on GovRAT — this one from security firm InfoArmor — shows that the GovRAT malware was sold on Dark Web cybercrime forums by a hacker or hackers who went by the nicknames BestBuy and “Popopret” (some experts believe these were just two different identities managed by the same cybercriminal).
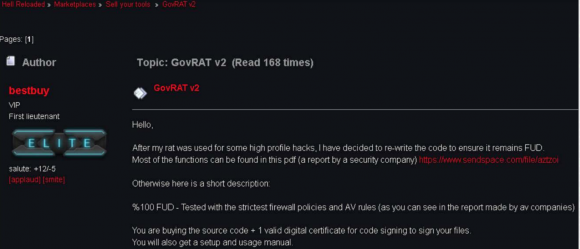
The hacker “bestbuy” selling his GovRAT trojan on the dark web forum “Hell.” Image: InfoArmor.
GovRAT has been for sale on various other malware and exploit-related sites since at least 2014. On oday[dot]today, for example, GovRAT was sold by a user who picked the nickname Spdr, and who used the email address spdr01@gmail.com.
Recall that the domains used to control the Mirai botnet that hit Deutsche Telekom all had some form of Spider Man in the domain registration records. Also, recall that the controller used to manage the GovRAT trojan and that Mirai botnet were both at one time hosted on the same server with just a handful of other (Mirai-related) domains.
According to a separate report (PDF) from InfoArmor, GovRAT also was sold alongside a service that allows anyone to digitally sign their malware using code-signing certificates stolen from legitimate companies. InfoArmor said the digital signature it found related to the service was issued to an open source developer Singh Aditya, using the email address parkajackets@gmail.com.
Interestingly, both of these email addresses — parkajackets@gmail.com and spdr01@gmail.com — were connected to similarly-named user accounts at vDOS, for years the largest DDoS-for-hire service (that is, until KrebsOnSecurity last fall outed its proprietors as two 18-year-old Israeli men).
Last summer vDOS got massively hacked, and a copy of its user and payments databases was shared with this author and with U.S. federal law enforcement agencies. The leaked database shows that both of those email addresses are tied to accounts on vDOS named “bestbuy” (bestbuy and bestbuy2).
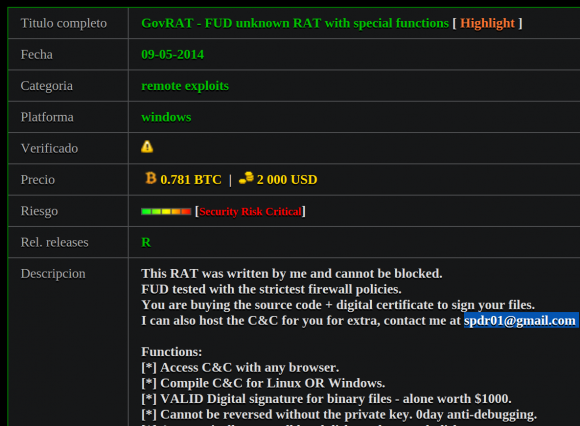
Spdr01’s sales listing for the GovRAT trojan on a malware and exploits site shows he used the email address spdr01@gmail.com
The leaked vDOS database also contained detailed records of the Internet addresses that vDOS customers used to log in to the attack-for-hire service. Those logs show that the bestbuy and bestbuy2 accounts logged in repeatedly from several different IP addresses in the United Kingdom and in Hong Kong.
The technical support logs from vDOS indicate that the reason the vDOS database shows two different accounts named “bestbuy” is the vDOS administrators banned the original “bestbuy” account after it was seen logged into the account from both the UK and Hong Kong. Bestbuy’s pleas to the vDOS administrators that he was not sharing the account and that the odd activity could be explained by his recent trip to Hong Kong did not move them to refund his money or reactivate his original account.
A number of clues in the data above suggest that the person responsible for both this Mirai botnet and GovRAT had ties to Israel. For one thing, the email address spdr01@gmail.com was used to register at least three domain names, all of which are tied back to a large family in Israel. What’s more, in several dark web postings, Bestbuy can be seen asking if anyone has any “weed for sale in Israel,” noting that he doesn’t want to risk receiving drugs in the mail.
The domains tied to spdr01@gmail.com led down a very deep rabbit hole that ultimately went nowhere useful for this investigation. But it appears the nickname “spdr01” and email spdr01@gmail.com was used as early as 2008 by a core member of the Israeli hacking forum and IRC chat room Binaryvision.co.il.
Visiting the Binaryvision archives page for this user, we can see Spdr was a highly technical user who contributed several articles on cybersecurity vulnerabilities and on mobile network security (Google Chrome or Google Translate deftly translates these articles from Hebrew to English).
I got in touch with multiple current members of Binaryvision and asked if anyone still kept in contact with Spdr from the old days. One of the members said he thought Spdr held dual Israeli and U.K. citizenship, that he would be approximately 30 years old at the moment. Another said Spdr was engaged to be married recently. None of those who shared what they recalled about Spdr wished to be identified for this story.
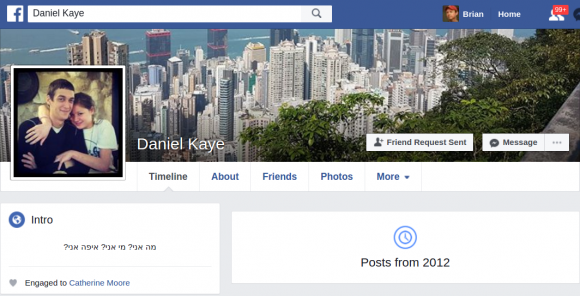
But a bit of searching on those users’ social networking accounts showed they had a friend in common that fit the above description. The Facebook profile for one Daniel Kaye using the Facebook alias “DanielKaye.il” (.il is the top level country code domain for Israel) shows that Mr. Kaye is now 29 years old and is or was engaged to be married to a young woman named Catherine in the United Kingdom.
The background image on Kaye’s Facebook profile is a picture of Hong Kong, and Kaye’s last action on Facebook was apparently to review a sports and recreation facility in Hong Kong.
Using Domaintools.com [full disclosure: Domaintools is an advertiser on this blog], I ran a “reverse WHOIS” search on the name “Daniel Kaye,” and it came back with exactly 103 current and historic domain names with this name in their records. One of them in particular caught my eye: Cathyjewels[dot]com, which appears to be tied to a homemade jewelry store located in the U.K. that never got off the ground.
Cathyjewels[dot]com was registered in 2014 to a Daniel Kaye in Egham, U.K., using the email address danielkaye02@gmail.com. I decided to run this email address through Socialnet, a plugin for the data analysis tool Maltego that scours dozens of social networking sites for user-defined terms. Socialnet reports that this email address is tied to an account at Gravatar — a service that lets users keep the same avatar at multiple Web sites. The name on that account? You guessed it: Spdr01.
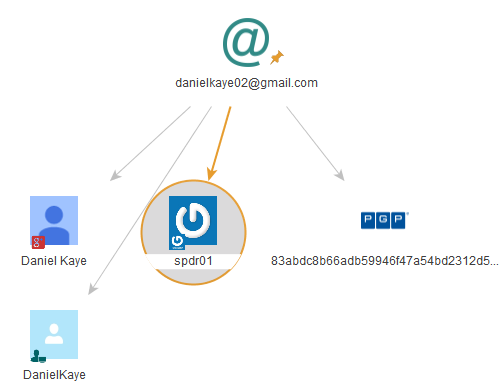
The output from the Socialnet plugin for Maltego when one searches for the email address danielkaye02@gmail.com.
Daniel Kaye did not return multiple requests for comment sent via Facebook and the various email addresses mentioned here.
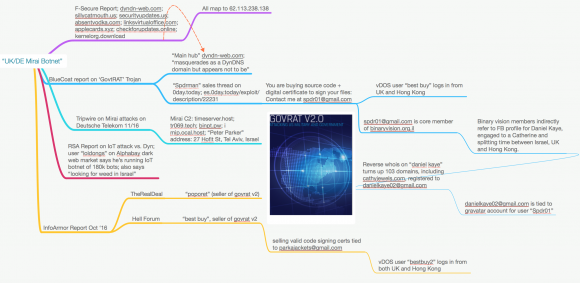
In case anyone wants to follow up on this research, I highlighted the major links between the data points mentioned in this post in the following mind map (created with the excellent and indispensable MindNode Pro for Mac).




GREAT WORK
Hi Brian, will you be passing your findings onto the authorities? Great article and job as always!
I guess they can read this story like everyone else.
Nice work. Is he still in custody?
No idea. The authorities in UK and Germany aren’t saying anything for now.
Brian,
Did you try requesting comment from the fiance` (or x fiance`)? She might have interesting things to say.
xoxo
Yes, I tried that too.
What about her parents?
See: https://www.facebook.com/cath.moore/posts/10153109954359903
To find:
https://www.facebook.com/richard.w.moore.73
Both GMail account have hits on HIBP. For the DanielKaye02 account, the most interesting source is probably the Nulled forum. I’m sure that’d be enlightening.
https://haveibeenpwned.com/api/v2/breachedaccount/danielkaye02%40gmail.com?truncateResponse=true
For the other account, it has hits as well – Most usefully, LinkedIn. With the Rapportive extension, if you start a message in Gmail to the target email address, Rapportive will find their LinkedIn account. This is the account registered with that email:
https://www.linkedin.com/in/sp-dr-980b44b/
Interestingly, Moshe Ben Abu, founder and CTO of Cyvera which just sold to PAN for $200M endorses our friend for all of his skills.
That was meant to be a top-level comment, apologies for any confusion!
The report of his arrest made it clear that it was carried out on behalf of the German authorities – “The BKA said it wanted to extradite the 29-year-old to Germany to face charges of computer sabotage.” There have been no recent news stories about this so I assume he is no longer in UK custody.
Real good article Brian
Great investigative journalism, as always.
Great work Brian! It baffles me every time how far you have to go to find info like this. You truly are good at it, and love reading your articles.
Great article Brian, it´s amazing how deep can you investigate with just some tiny pieces of information.
Great investigation, great reading.
Great work Brian !! As an Intel Analyst, loved to see this kind of analysis !!
Excellent work.
Brain, great job mapping all this.
Lots of breadcrumbs were left around the Internet, which is not good
for someone engaged in the culture of malware, cyber espionage, and DDoS.
The more you hack, the more trail you leave.
thanks to domaintools for giving you such an account. Without it its hardly possible to do this sort of research.
It appears that non-US citizens don’t use good OPSEC because they aren’t so conscious of their state’s laws or efforts of foreign LEA/whitehat investigators.
With the increase in this quality research, will it teach a new generation of Russian, Israeli, Chinese hackers to cover their tracks more?
It’s a similar analogy to the “forensic files” television shows. I guess no criminal can leave zero trace behind, however, I’ve seen a lot of cybercriminals get DOX’d from using previous online aliases (which is so stupid).
Love your quality reporting Brian Krebs. This is my favorite site on the whole net.
I guess by your definition, everybody from the USA is some master super hacker. I hate that kind of stupid arrogance.
Or its just that the guys who aren’t very good are the ones you hear about.
Just food for thought.
Thanks Brian.
Using the same alias on multiple sites is toddler level OPSEC
He isn’t the author of GovRAT, FYI.
Daniel?……. lul
Very interesting article and a great investigation\or, Thank you!
Great work, I love reading your cyber-crime mysteries.
Who indeed? Inquiring minds (a lot of very good ones, too) really want to know…
Do you have your own DNSDB account or is someone running those queries on your behalf?
SPDR is also an ETF full of bonds.
(Bloomberg Barclays Aggregate Bond ETF)
By using his tools, law enforcement is not an option and will broke Internet.
Great reading as always. Thanks
Every time Email is the weakest link .
Every single time .
If you dont want to get caught by Brian dont use the same email address ever – or Brian will get your sorry ass sooner or later .
You make us proud! Any backlash from reporting this?
This is an article in the german magazine Spiegel about this case:
http://www.spiegel.de/netzwelt/netzpolitik/telekom-hack-prozess-gegen-29-jaehrigen-briten-hat-begonnen-a-1159071.html