Richard Smith — who resigned as chief executive of big-three credit bureau Equifax this week in the wake of a data breach that exposed 143 million Social Security numbers — is slated to testify in front of no fewer than four committees on Capitol Hill next week. If I were a lawmaker, here are some of the questions I’d ask when Mr. Smith goes to Washington.

Before we delve into the questions, a bit of background is probably in order. The new interim CEO of Equifax — Paulino do Rego Barros Jr. — took to The Wall Street Journal and other media outlets this week to publish a mea culpa on all the ways Equifax failed in responding to this breach (the title of the op-ed in The Journal was literally “I’m sorry”).
“We were hacked,” Barros wrote. “That’s the simple fact. But we compounded the problem with insufficient support for consumers. Our website did not function as it should have, and our call center couldn’t manage the volume of calls we received. Answers to key consumer questions were too often delayed, incomplete or both.”
Barros stated that Equifax was working to roll out a new system by Jan. 31, 2018 that would let consumers “easily lock and unlock access to their Equifax credit files.”
“You will be able to do this at will,” he continued. “It will be reliable, safe, and simple. Most significantly, the service will be offered free, for life.”
I have argued for years that all of the data points needed for identity thieves to open new lines of credit in your name and otherwise ruin your credit score are available for sale in the cybercrime underground. To be certain, the Equifax breach holds the prospect that ID thieves could update all that stolen data with newer records. I’ve argued that the only sane response to this sorry state of affairs is for consumers to freeze their files at the bureaus, which blocks potential creditors — and ID thieves — from trashing your credit file and credit score.
Equifax is not the only bureau promoting one of these lock services. Since Equifax announced its breach on Sept. 7, big-three credit bureaus Trans Union and Experian have worked feverishly to steer consumers seeking freezes toward these locks instead, arguing that they are easier to use and allow consumers to lock and unlock their credit files with little more than the press of a button on a mobile phone app. Oh, and the locks are free, whereas the bureaus can (and do) charge consumers for placing and/or thawing a freeze (the laws freeze fee laws differ from state to state).
CREDIT FREEZE VS. CREDIT LOCK
My first group of questions would center around security freezes or credit freezes, and the difference between those and these credit lock services being pushed hard by the bureaus.
Currently, even consumer watchdog groups say they are uncertain about the difference between a freeze and a lock. See this press release from Thursday by U.S. PIRG, the federation of state Public Interest Research Groups, for one such example.
Also, I’m curious to know what percentage of Americans had a freeze prior to the breach, and how many froze their credit files (or attempted to do so) after Equifax announced the breach. The answers to these questions may help explain why the bureaus are now massively pushing their new credit lock offerings (i.e., perhaps they’re worried about the revenue hit they’ll take should a significant percentage of Americans decide to freeze their credit files).
I suspect the pre-breach number is less than one percent. I base this guess loosely on some data I received from the head of security at Dropbox, who told KrebsOnSecurity last year that less than one percent of its user base of 500 million registered users had chosen to turn on 2-factor authentication for their accounts. This extra security step can block thieves from accessing your account even if they steal your password, but many consumers simply don’t take advantage of such offerings because either they don’t know about them or they find them inconvenient.
Bear in mind that while most two-factor offerings are free, most freezes involve fees, so I’d expect the number of pre-breach freezers to be a fraction of one percent. However, if only one half of one percent of Americans chose to freeze their credit files before Equifax announced its breach — and if the total number of Americans requesting a freeze post-breach rose to, say, one percent — that would still be a huge jump (and potentially a painful financial hit to Equifax and the other bureaus).

So without further ado, here are some questions I’d ask on the topic of credit locks and freezes:
-Approximately how many credit files on Americans does Equifax currently maintain?
-Prior to the Equifax breach, approximately how many Americans had chosen to freeze their credit files at Equifax?
-Approximately how many total Americans today have requested a freeze from Equifax? This should include the company’s best estimate on the number of people who have requested a freeze but — because of the many failings of Equifax’s public response cited by Barros — were unable to do so via phone or the Internet.
-Approximately how much does Equifax charge each time the company sells a credit check (i.e., a bank or other potential creditor performs a “pull” on a consumer credit file)?
-On average, how many times per year does Equifax sell access to consumer’s credit file to a potential creditor?
-Mr. Barros said Equifax will extend its offer of free credit freezes until the end of January 2018. Why not make them free indefinitely, just as the company says it plans to do with its credit lock service?
-In what way does a consumer placing a freeze on their credit file limit Equifax’s ability to do business?
-In what way does a consumer placing a lock on their credit file limit Equifax’s ability to do business?
-If a lock accomplishes the same as a freeze, why create more terminology that only confuses consumers?
-By agreeing to use Equifax’s lock service, will consumers also be opting in to any additional marketing arrangements, either via Equifax or any of its partners?
BREACH RESPONSE
Equifax could hardly have bungled their breach response more if they tried. It is said that one should never attribute to malice what can more easily be explained by incompetence, but Equifax surely should have known that how they handled their public response would be paramount to their ability to quickly put this incident behind them and get back to business as usual.

Equifax has come under heavy criticism for waiting too long to disclose this breach. It has said that the company became aware of the intrusion on July 29, and yet it did not publicly disclose the breach until Sept. 7.However, when Equifax did disclose, it seemed like everything about the response was rushed and ill-conceived.
One theory that I simply cannot get out of my head is that perhaps Equifax rushed preparations for is breach disclosure and response because it was given a deadline by extortionists who were threatening to disclose the breach on their own if the company did not comply with some kind of demand.
-I’d ask a question of mine that Equifax refused to answer shortly after the breach: Whether the company was the target of extortionists over this data breach *before* the breach was officially announced on Sept. 7.
-Equifax said the attackers abused a vulnerability in Apache Struts to break in to the company’s Web applications. That Struts flaw was patched by the Apache Foundation on March 8, 2017, but Equifax waited until after July 30, 2017 — after it learned of the breach — to patch the vulnerability. Why did Equifax decide to wait four and a half months to apply this critical update?
-How did Equifax become aware of this breach? Was it from an external source, such as law enforcement?
-Assuming Equifax learned about this breach from law enforcement agencies, what did those agencies say regarding how they learned about the breach?
FRAUD AND ABUSE
Multiple news organizations have reported that companies which track crimes related to identity theft — such as account takeovers, new account fraud, and e-commerce fraud — saw huge upticks in all of these areas corresponding to two periods that are central to Equifax’s breach timeline; the first in mid-May, when Equifax said the intruders began abusing their access to the company, and the second late July/early August, when Equifax said it learned about the breach.
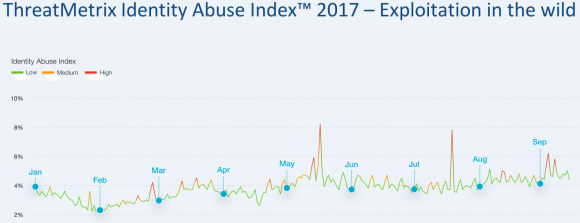
This chart shows spikes in various forms of identity abuse — including account takeovers and new account fraud — as tracked by ThreatMetrix, a San Jose, Calif. firm that helps businesses prevent fraud.
-Has Equifax performed any analysis on consumer credit reports to determine if there has been any pattern of consumer harm as a result of this breach?
-Assuming the answer to the previous question is yes, did the company see any spikes in applications for new lines of consumer credit corresponding to these two time periods in 2017?
Many fraud experts report that a fast-growing area of identity theft involves so-called “synthetic ID theft,” in which fraudsters take data points from multiple established consumer identities and merge them together to form a new identity. This type of fraud often takes years to result in negative consequences for consumers, and very often the debt collection agencies will go after whoever legitimately owns the Social Security number used by that identity, regardless of who owns the other data points.
-Is Equifax aware of a noticeable increase in synthetic identity theft in recent months or years?
-What steps, if any, does Equifax take to ensure that multiple credit files are not using the same Social Security number?
-Prior to its breach disclosure, Equifax spent more than a half million dollars in the first half of 2017 lobbying Congress to pass legislation that would limit the legal liability of credit bureaus in connection with data security lapses. Do you still believe such legislation is necessary? Why or why not?
What questions did I leave out, Dear Readers? Or is there a way to make a question above more succinct? Sound off in the comments below, and I may just add yours to the list!
In the meantime, here are the committees at which Former Equifax CEO Richard Smith will be testifying next week on Capitol Hill. Some of these committees will no doubt be live-streaming the hearings. Check back at the links below on the morning-of for more information on that. Also, C-SPAN almost certainly will be streaming some of these as well:
-Tuesday, Oct. 3, 10:00 a.m., House Energy and Commerce Committee. Rayburn House Office Bldg. Room 2123.
-Wednesday, Oct. 4, 10:00 a.m., Senate Committee on Banking, Housing, & Urban Affairs. Dirksen Senate Office Bldg., Room 538.
-Wednesday, Oct. 4, 2:30 p.m., Senate Judiciary Subcommittee on Privacy, Technology and the Law. Dirksen Senate Office Bldg., Room 226.
-Thursday, Oct. 5, 9:15 a.m., House Financial Services Committee. Rayburn House Office Bldg., Room 2128.




How about quizzing him about unloading his stock options stockholders could suffer the consequences? Or questions to shine a light on the fact that his penalty for failure is a $90 million exit package?
William — Mr. Smith was not alleged to have committed insider trading connected to the breach. That was alleged against the company’s chief financial officer, as well as presidents of other business units inside Equifax.
Granted, as head of the ship at the time, it’s still not a bad line of questioning for Mr. Smith.
and the CEO and CFO/Controller never talk about important issues…
like someone stealing all your data… rolls eyes. Suits will get a pass but John Doe with 32 Grams of plant will get 2-10 years… out system is a joke that stopped being funny in the 80s.
I allege that it is insider trading. As there was clear information that they were breached. Any and all large sales of stock by anyone that knew of the breach was indeed getting out before the ship sank. Trading “after” full disclosure, maybe they can get away with, but not a second prior.
The fine should be; all earnings from the insider trading, and it should all go to compensating victims of fraud from the breach. But this is the US where businesses are protected and consumers are throw to the wolves, so it’ll never happen.
It seems prudent to ask how him details about their security program including budgets, number of personnel, number of contractors, etc. They have about 40 open positions with the tagline “information security”.
Given that credit freezes/thaws/etc are roughly $10 a pop and given how often Equifax knows people need their credit reports accessed each year, how much revenue does Equifax stand to gain as a result of their terrible security from all 143 million people freezing their credit as they are now basically required to freeze their credit? Same question for Transunion, Experian, and Innovis.
We are talking about something in the neighborhood of $5B and this completely ignores any losses due to actual identity theft that occurs.
With such a massive impact on the economy coming from the established credit bureau industry which has a history of a healthy amount of free market competition, please explain why federal legislation is not appropriate and necessary to address the problem? If you feel legislation is not appropriate at this time, please explain what else could possibly go wrong before federal legislation would be completely justified?
I did a freeze with the four bureaus suggested by Krebs sometime last week and Eqifax didn’t charge me for the freeze. Apparently they decided to not make a charge before the announcement this week. Trans Union and Experian charged $10 each, Innovas didn’t charge. Experian web site charged my card and then croaked, forcing me to go through the hassle of sending in a letter with my name, SSN, DOB, and address information, along with a rent or insurance receipt, a photo copy of my drivers license, and a check payment.
Under the Gramm-Leach-Bliley Act, if a consumer establishes a business relationship with a consumer reporting agencies (for instance, by signing up for credit monitoring or “credit lock), the CRA is allowed to sell the consumers’ personal financial information to nonaffiliated third parties (e.g. anyone!), unless the consumer opts out.
Will Equifax promise to make the standard opt-in for information sharing with third parties so that in signing up for more security, they don’t end up with less privacy?
Here’s one more: what’s the basis for Equifax’s estimate of how many records were affected, or are all records that were in the breached system assumed to be affected?
The Equifax response to the leaks reminds me of the response we always got from a certain storage vendor when problems arose… if only you’d buy more of x, the problem would go away…
I hope they stop treating this as a sales opportunity and really try to fix the core problems.
Why is credit monitoring only offered for 12 months? A stolen SSN and birth date can be mis-used for a lifetime, addresses and licenses can be mis-used for much more than 12 months.
Given the level of negligence at Equifax, why is the CEO leaving with a handsome golden handshake?
Equifax has said that senior execs John Gamble, Joseph Loughran, and Rodolfo Ploder were not aware of the breach when they sold stock ahead of the disclosure. Why were they not aware?
Dealing with this breach should have been an “all-hands-on-deck” effort. How and why was the response kept secret from the company’s CFO? How does this failure not constitute negligence on Equifax’s part?
Richard Smith retired a very wealthy man, a bit of a sc#m sucker if you ask me.
Ask him what steps he, personally, is taking or would take to now protect his (presumably) compromised data.
Has the person responsible for the delay in patching Apache Struts been taken out and shot?
We’re probably talking about an overworked IT employee with 1000s of things to do, all of which “must be done yesterday”, no authority on priorities.
How will this help?
The appropriate questions to ask in this area include
“What are your configuration management procedures regarding patching and/or updating 3rd party software?”
“What is the average interval between your learning of the existence of a patch and your implementing it on your production systems?”
“How large is your configuration management team? Is it comprised of personnel who are separate from your software development team and your operations team?”
My guess is that, assuming Equifax has a CM team, Apache Struts wasn’t considered under their purview. The software development group adopted and configured the Struts framework, then its maintenance and support fell between the cracks.
Regarding synthetic ID theft, when the Equifax hack was discussed on Twitter, host Becky Worley said she gets annual credit reports for her children. That is synthetic ID theft uses social security numbers that are not active. Still I wonder why any credible credit card company, bank, etc. would give credit to a minor. Or are the credit checks that poorly run?
Here is a question that you might throw onto the list:
Given the sensitive nature of the data you keep on individuals, and the potential devastation of identity theft, why did you not encrypt the data?
That is a great question – it gets my vote. Encrypting data at rest is in PCI requirements and just a smart practice. Oh wait, this is the credit bureau whose dumpster fire caught fire.
Sorry, that question isn’t worth answering.
The answer is that there really isn’t any good way to do that given their business model.
Here are the general use cases for their services:
1. Entity {that does business w/ consumer} reports {credit status} (“paid on time”, “didn’t pay on time”) on a monthly basis. They include {name, dob, address, ssn, amount, account#}
2. Entity {that offers credit w/ consumer} needs to check {credit status} in order to calculate credit risk. They include {name, dob, address, ssn}
3. Consumer was declined for credit, needs to check to see which Entity in 1 provided incorrect information. They include {name, dob, address*5, ssn}
Notes:
A. dob can be incorrect
B. name can be fuzzed (Jim Smith v. James Smith. v. Jim E Smith}
C. address can be fuzzed (742 Evergreen Terrace, 742 Evergreen Ter., 742 Evergreen, 742 Evargreen Terrace, 742 Evergreene Terrace, Evergreen Terrace 742, 744 Evergreen Terrace), the zip code could be wrong/omitted, the state could be wrong/omitted (I’m not sure what portion of readers recognize these addresses, but the specific city is present in 34 states. OTOH, the city could be Riverside, which is present in 50…).
D. generally the SSN is /less/ likely to be corrupt (but it can be!)
E. people move, so addresses aren’t very permanent
F. people change their names (marriage, divorce, Prince [1])
If the data is “encrypted”, how exactly do you expect any of 1, 2, or 3 to work? There were 140,000,000 records breached. Imagine if that was their entire database (I don’t think it is). Imagine it took 1 second to perform a record check between a “key” and a row. It would take on average 70,000,000 seconds to find the right row — more than 2 years.
OK, so perhaps we can make it better? How? keep in mind A, B, and C. Perform a fuzzy search for all possible matches on A/B/C?
James Smith [2] gives you 38,000 records. (See other comments for notes about names, and dob.)
Say you need to consider 38,000 records, that’s 10 hours. Just for a simple insert/update that you’re performing monthly. And you’re probably doing that for 5-10 accounts for each James.
In order to be able to look things up, it needs to be possible to perform lookups. And given how flaky most of the possible fields are, a single fairly stable field is incredibly valuable. Even if it gets corrupted occasionally (it does!).
[1] https://en.wikipedia.org/wiki/Prince_(musician)
[2] https://blogs.ancestry.com/cm/calling-james-smith-10-most-common-first-and-surname-combinations/
I guess I need a new good pointlist of what I should do because they suck. They probably COULD have bungled it worse by just doing literally nothing. But …. boy they tried to make it as bad as they could.
Can you explain what *I*/someone should do with this new information as if I am a fiveyearold moron? Like what can I do RIGHT NOW to fix/protect my situation.
I HAD a freeze which proved to pretty much be worthless given the fact anyone could’ve unlocked it apparently.
What should I do now. Sign up for their scam “monitoring?” How should I handle a freeze now? Should I go unlock and relock with all the others for new pins?
Brilliant !
You should also ask the CEO to identify ALL outside counsel providing strategic cyber security risk services to Equifax at any time over the past year. All of those law firms should then be asked whether they were ALSO providing similar legal services to either Apache Foundation or other clients who were either responsible for the vulnerability or concerned about their own risk of liability for exposure to the vulnerability. If there’s an overlap in clients within any one law firm (and there almost certainly will be overlap within many of the AmLaw 200 law firms), the next question is what information sharing agreements, disclosures and waivers of potential conflicts did the law firm have in place with each of those clients, including with Equifax? This could reveal a potential legal malpractice claim if any of the lawyers inside the firm were actually aware of (or should have been aware of) the vulnerability in order to meet their obligation to provide competent legal services to ANY of their clients. If they were aware (or should have been aware) of the vulnerability for any ONE client, did the firm use that knowledge to the benefit of EVERY client, including Equifax? If not, why not? To emphasize your point Brian, was it malice or mere incompetence that caused the law firm to stove-pipe information and fail Equifax?
Does Equifax support adding a SSN password or some type of blockchain lock so customers whose SSN and other PI has been stolen can be made whole? If not, how does Equifax plan to allow customers to ever be made whole again?
How does Equifax plan to help people who have fraudulent tax returns submitted to the IRS? (Neither a credit lock nor freeze will help with false returns.)
How does Equifax plan to help people who have fraudulent Medicare and Social Security benefit claims submitted? (Neither a credit lock nor freeze will help with these fraudulent claims.)
Ask Smith if by “retiring” or “stepping down” he is not sctually being fired, and as a result won’t lose his severance or retirement packages and stock options?
If he gets to keep his golden parachute then his gross negligence is being rewarded.
How big was your golden parachute and what do you think you did to deserve it?
It’s been published elsewhere that he left with no severance or other additional payments. On the other hand, according to the Yahoo Finance entry for Equifax, Mr Smith earned $4 million in compensation in 2016, and exercised $39.5 million in stock options.
That Yahoo story is being widely quoted as “proof” that Smith is getting a golden parachute, but near as I can tell it is pure conjecture. You are correct: Any remuneration he may receive still must be approved by the board. Indeed, according to the company’s SEC filings, Smith will not receive his 2017 annual bonus and any obligations or benefits owed to Mr. Smith under the employment agreement will be deferred until the Board completes an independent review of the breach.
Thanks for that info, Brian. It is worth knowing that the Equifax board is looking at doing something about his 2017 remuneration. Wonder if they will try to claw back gains from the 2016 stock options?
Brian, that’s a great set of question and I hope someone is able to get them into the hand of the legislators who will be asking questions. While I wouldn’t expect Smith to be able to answer this question, I’d like to know what information was shared with the other credit bureaus before the public disclosure? What was shared with other financial industry partners before the disclosure?
In short, I have little faith that the other credit bureaus have any less exposure than Equifax and perhaps they haven’t disclosed an attack publicly. When will the next shoe drop? Should executives from those organizations be ordered to testify as to their ability to prevent similar exposures of consumer information?
Brian,
We have provided the following information to the office of a committee member concerning some of the revenue from the data breach to Equifax: Based on individual state security freeze laws, if only 10% of the affected population asks for a breach after the free enrollment period, revenue to Equifax will be $86.1M. Revenue to Transunion and Experian from 10% of the affected population is: $172.2M. These numbers are for freeze placement and do not include lift fees for future credit applications.
Jane Carpenter
Maine Identity Services, LLC
What other 1st, 2nd or 3rd party data maintained in Equifax servers may have also been compromised?
What other service providers selling data have Equifax data contained in their environments that may also be impacted by this breach/hack?
Ask the captain of the sinking equifax
“What would it take and how long to sink the ship for good?”
No point in plugging thousands of holes in a sinking ship – move on and save everyone time/tax dollars!
When (re)freezing our credit with the major credit reporting agencies immediately following the news of the Equifax breech, I encountered an offer for a credit lock from one of the agencies as I tried to get a freeze in place there. I do not remember the agency.
I do recall reading about the lock and believing it at that time to be little more than a marketing scam, especially since I couldn’t seem to get to security freeze from the page with the lock offer. I just dismissed it out of hand, went back to square one and bought the freezes (mine and my wife’s).
I have learned nothing since then to change my mind about the lock.
What a bunch of bull-crap. These agencies should not be allowed to have our credit without our permission. No other financial institution is allowed to, they should also be held to the same standards. Who gave them permission anyways?
What is the company doing to protect the affected people from all the other crimes other than Identity Theft that people have now been exposed to?
Social Engineering and phishing primarily – which are used in over 90% of successful hacks. How do we protect seniors who are not equipped with knowledge to know who to trust, what are the scams and where is the real help.
The Freeze is the only way to go, but Identity Theft is not the only vulnerability we are all exposed to.
“…seniors…”
As Mr Krebs says, “…and if the total number of Americans requesting a freeze post-breach rose to, say, one percent…”
If I use the one percent number, that leaves 99% of 143 million=142 million breached unfrozen credit files. 142 million owners still don’t know an Equifax breach happened–whether senior or not–don’t care to monitor, freeze, or lock their files, or know where to begin. I personally know people that don’t take any further steps beyond knowing there was an Equifax breach.
Not a question; but, waiting for 142 million and greater fraud reports to start happening.
Rhetorical, as my feeling is already a miserable reponse will be given: How is the industry prepared for 142 million–even instantaneously–or a much greater number, or infinite number of fraud reports? Note: As the personal information may be used for more than one instance of fraud–even infinite–or non-credit crime.
Rhetorical, as Equifax has already displayed a huge lack of following any good standards: Mr. Smith, are you aware in some forms of employment the disclosure of information is “treasonous”? Even, “subversive” in sabotaging the data system to be breached?
Non-rhetorical:
What information protection standards were being followed if it wasn’t PCI-DSS, any standards?
My experience at the IG is that when everyone in government is investigating a problem – no one is investigating the problem; most of this will be political grandstanding and the streaming version of photo-op.
For issues this big the Senate and House should form one investigative committee and staff it with people who know something about what they are doing, but I’m not holding my breath.
What are you doing next week, Brian – can you squeeze in a government gig?
+1
I didn’t get a say in whether Equifax had my PII, and they were criminally negligent with it. How does that not run afoul of privacy laws? **Where’s the ‘Opt Out’ button for these embarrassingly irresponsible companies?**
would like to see all three of them out of business permanently –
Banks can calculate credit scores themselves.
Well from the W-2 breach from Experian, I already had a credit freeze on all three credit reporting agencies and I feel so much better … not! What stops someone from un-freezing the credit? Oh that’s right a letter or phone call.
My question “Will equifax hire proven security professionals for their C positions?” After the credentials of the former CISO and CIO came to light I can’t help but wonder how they got their jobs when they were horribly underqualified
YUP what I have found in the 20+ in the industry is the “C” and “E” Bands credentials have no technical skill. They are not a lead-by-example resource. Most of the skillset that I see in these empty-suits are High Performing Salesman or have managed large teams. They themselves are “cloud-thinkers”. They have no idea what it takes to get things done when they say ‘make it happen’. It’s this level of disconnect I consistently see in these upper bands and its quite frankly scary.
So when you have a new “C or E” band hired you’ll also see them start bringing in their ‘boys’ that have worked for them before. This is the “cadence”.
Question for Mr. Smith: When the new system is in place that they replace our SS# with a different numeric identifier. And when companies pull our credit in the future that the new systems APP alerts us gives us the option to ALLOW or DENY via the app or email. This way we know real time when someone is pinging our credit. (Instant Credit Freeze button too).
Again, nothing about the current SEC investigations about the insider trading of the golden parachute exec’s.
Example: If I were to manage a team or company and something like this happened on my watch I’d expect to be Canned with no big check. PERIOD!
When companies agree to these terms (Golden Parachutes) it’s really a get outta jail free card and a pat on the back for screwing up. Kinda like getting a trophy for showing-up. Isn’t that the same mentality that is performing a complete dis-service to our youth today?? It just sends the wrong message!
If you work hard AND are Successful then you should be rewarded. If you screw-up or don’t take responsibility for your team and their actions you should be shown the door. No trophies and no big check to fall back on. The boards of these same companies layoff staff to balance their budgets so they can meet the expected stock holders expectations…yet they are paying out Millions to have these schmucks walk-away?? Why are these big checks not in contention?