Richard Smith — who resigned as chief executive of big-three credit bureau Equifax this week in the wake of a data breach that exposed 143 million Social Security numbers — is slated to testify in front of no fewer than four committees on Capitol Hill next week. If I were a lawmaker, here are some of the questions I’d ask when Mr. Smith goes to Washington.

Before we delve into the questions, a bit of background is probably in order. The new interim CEO of Equifax — Paulino do Rego Barros Jr. — took to The Wall Street Journal and other media outlets this week to publish a mea culpa on all the ways Equifax failed in responding to this breach (the title of the op-ed in The Journal was literally “I’m sorry”).
“We were hacked,” Barros wrote. “That’s the simple fact. But we compounded the problem with insufficient support for consumers. Our website did not function as it should have, and our call center couldn’t manage the volume of calls we received. Answers to key consumer questions were too often delayed, incomplete or both.”
Barros stated that Equifax was working to roll out a new system by Jan. 31, 2018 that would let consumers “easily lock and unlock access to their Equifax credit files.”
“You will be able to do this at will,” he continued. “It will be reliable, safe, and simple. Most significantly, the service will be offered free, for life.”
I have argued for years that all of the data points needed for identity thieves to open new lines of credit in your name and otherwise ruin your credit score are available for sale in the cybercrime underground. To be certain, the Equifax breach holds the prospect that ID thieves could update all that stolen data with newer records. I’ve argued that the only sane response to this sorry state of affairs is for consumers to freeze their files at the bureaus, which blocks potential creditors — and ID thieves — from trashing your credit file and credit score.
Equifax is not the only bureau promoting one of these lock services. Since Equifax announced its breach on Sept. 7, big-three credit bureaus Trans Union and Experian have worked feverishly to steer consumers seeking freezes toward these locks instead, arguing that they are easier to use and allow consumers to lock and unlock their credit files with little more than the press of a button on a mobile phone app. Oh, and the locks are free, whereas the bureaus can (and do) charge consumers for placing and/or thawing a freeze (the laws freeze fee laws differ from state to state).
CREDIT FREEZE VS. CREDIT LOCK
My first group of questions would center around security freezes or credit freezes, and the difference between those and these credit lock services being pushed hard by the bureaus.
Currently, even consumer watchdog groups say they are uncertain about the difference between a freeze and a lock. See this press release from Thursday by U.S. PIRG, the federation of state Public Interest Research Groups, for one such example.
Also, I’m curious to know what percentage of Americans had a freeze prior to the breach, and how many froze their credit files (or attempted to do so) after Equifax announced the breach. The answers to these questions may help explain why the bureaus are now massively pushing their new credit lock offerings (i.e., perhaps they’re worried about the revenue hit they’ll take should a significant percentage of Americans decide to freeze their credit files).
I suspect the pre-breach number is less than one percent. I base this guess loosely on some data I received from the head of security at Dropbox, who told KrebsOnSecurity last year that less than one percent of its user base of 500 million registered users had chosen to turn on 2-factor authentication for their accounts. This extra security step can block thieves from accessing your account even if they steal your password, but many consumers simply don’t take advantage of such offerings because either they don’t know about them or they find them inconvenient.
Bear in mind that while most two-factor offerings are free, most freezes involve fees, so I’d expect the number of pre-breach freezers to be a fraction of one percent. However, if only one half of one percent of Americans chose to freeze their credit files before Equifax announced its breach — and if the total number of Americans requesting a freeze post-breach rose to, say, one percent — that would still be a huge jump (and potentially a painful financial hit to Equifax and the other bureaus).

So without further ado, here are some questions I’d ask on the topic of credit locks and freezes:
-Approximately how many credit files on Americans does Equifax currently maintain?
-Prior to the Equifax breach, approximately how many Americans had chosen to freeze their credit files at Equifax?
-Approximately how many total Americans today have requested a freeze from Equifax? This should include the company’s best estimate on the number of people who have requested a freeze but — because of the many failings of Equifax’s public response cited by Barros — were unable to do so via phone or the Internet.
-Approximately how much does Equifax charge each time the company sells a credit check (i.e., a bank or other potential creditor performs a “pull” on a consumer credit file)?
-On average, how many times per year does Equifax sell access to consumer’s credit file to a potential creditor?
-Mr. Barros said Equifax will extend its offer of free credit freezes until the end of January 2018. Why not make them free indefinitely, just as the company says it plans to do with its credit lock service?
-In what way does a consumer placing a freeze on their credit file limit Equifax’s ability to do business?
-In what way does a consumer placing a lock on their credit file limit Equifax’s ability to do business?
-If a lock accomplishes the same as a freeze, why create more terminology that only confuses consumers?
-By agreeing to use Equifax’s lock service, will consumers also be opting in to any additional marketing arrangements, either via Equifax or any of its partners?
BREACH RESPONSE
Equifax could hardly have bungled their breach response more if they tried. It is said that one should never attribute to malice what can more easily be explained by incompetence, but Equifax surely should have known that how they handled their public response would be paramount to their ability to quickly put this incident behind them and get back to business as usual.

Equifax has come under heavy criticism for waiting too long to disclose this breach. It has said that the company became aware of the intrusion on July 29, and yet it did not publicly disclose the breach until Sept. 7.However, when Equifax did disclose, it seemed like everything about the response was rushed and ill-conceived.
One theory that I simply cannot get out of my head is that perhaps Equifax rushed preparations for is breach disclosure and response because it was given a deadline by extortionists who were threatening to disclose the breach on their own if the company did not comply with some kind of demand.
-I’d ask a question of mine that Equifax refused to answer shortly after the breach: Whether the company was the target of extortionists over this data breach *before* the breach was officially announced on Sept. 7.
-Equifax said the attackers abused a vulnerability in Apache Struts to break in to the company’s Web applications. That Struts flaw was patched by the Apache Foundation on March 8, 2017, but Equifax waited until after July 30, 2017 — after it learned of the breach — to patch the vulnerability. Why did Equifax decide to wait four and a half months to apply this critical update?
-How did Equifax become aware of this breach? Was it from an external source, such as law enforcement?
-Assuming Equifax learned about this breach from law enforcement agencies, what did those agencies say regarding how they learned about the breach?
FRAUD AND ABUSE
Multiple news organizations have reported that companies which track crimes related to identity theft — such as account takeovers, new account fraud, and e-commerce fraud — saw huge upticks in all of these areas corresponding to two periods that are central to Equifax’s breach timeline; the first in mid-May, when Equifax said the intruders began abusing their access to the company, and the second late July/early August, when Equifax said it learned about the breach.
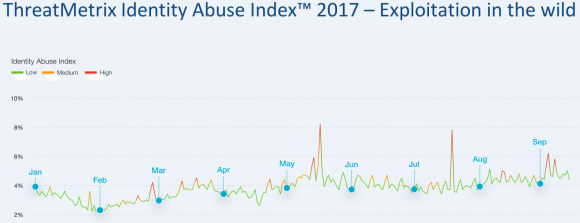
This chart shows spikes in various forms of identity abuse — including account takeovers and new account fraud — as tracked by ThreatMetrix, a San Jose, Calif. firm that helps businesses prevent fraud.
-Has Equifax performed any analysis on consumer credit reports to determine if there has been any pattern of consumer harm as a result of this breach?
-Assuming the answer to the previous question is yes, did the company see any spikes in applications for new lines of consumer credit corresponding to these two time periods in 2017?
Many fraud experts report that a fast-growing area of identity theft involves so-called “synthetic ID theft,” in which fraudsters take data points from multiple established consumer identities and merge them together to form a new identity. This type of fraud often takes years to result in negative consequences for consumers, and very often the debt collection agencies will go after whoever legitimately owns the Social Security number used by that identity, regardless of who owns the other data points.
-Is Equifax aware of a noticeable increase in synthetic identity theft in recent months or years?
-What steps, if any, does Equifax take to ensure that multiple credit files are not using the same Social Security number?
-Prior to its breach disclosure, Equifax spent more than a half million dollars in the first half of 2017 lobbying Congress to pass legislation that would limit the legal liability of credit bureaus in connection with data security lapses. Do you still believe such legislation is necessary? Why or why not?
What questions did I leave out, Dear Readers? Or is there a way to make a question above more succinct? Sound off in the comments below, and I may just add yours to the list!
In the meantime, here are the committees at which Former Equifax CEO Richard Smith will be testifying next week on Capitol Hill. Some of these committees will no doubt be live-streaming the hearings. Check back at the links below on the morning-of for more information on that. Also, C-SPAN almost certainly will be streaming some of these as well:
-Tuesday, Oct. 3, 10:00 a.m., House Energy and Commerce Committee. Rayburn House Office Bldg. Room 2123.
-Wednesday, Oct. 4, 10:00 a.m., Senate Committee on Banking, Housing, & Urban Affairs. Dirksen Senate Office Bldg., Room 538.
-Wednesday, Oct. 4, 2:30 p.m., Senate Judiciary Subcommittee on Privacy, Technology and the Law. Dirksen Senate Office Bldg., Room 226.
-Thursday, Oct. 5, 9:15 a.m., House Financial Services Committee. Rayburn House Office Bldg., Room 2128.




Questions to Mr Smith…
– In dealing with Mandiant in March, did you narrow the scope of the investigation so as not to expose certain weaknesses in the company’s security that you had already been made aware of?
– Why was the investigation in March “a top-secret project” and one that you were overseeing personally ?
Brian, As recently as this week, Trans Union will not let you use their site, even if you are a registered user, to access their credit freeze or lock function without first signing up for and paying for their credit monitoring service. This is against federal law. Yet their phone support says you must use the online system to place a freeze or a lock. While this may be a glitch, as they say, it has been a glitch for weeks. The arrogance of these firms and their abuse of the very resource that gives their reason to be, us, is appalling. This is another vast US swamp that needs to be drained!
Brian, I’m curious as to your thoughts on this. At what point if any is regulation needed to limit the volume of information any one company can deal in? Regulating a company to say 10 million or 15 million or whatever the number may be would dramatically reduce the absolute lunacy of these breaches where multi-hundred million records are compromised? Or if not limiting the company for fear of hindering their bottom line at least requiring logical limitation where no one division or database within the company, etc can have info on more then 10 million users, so at least the bad actors would have to work harder vs just breaking a single database or system. It’s just hard to wrap my mind around why a company is even allowed to deal in this much data in the first place, they’ve proven relentlessly they cannot manage and secure it effectively.
There are 4-5 major credit bureaus and perhaps 30 minor ones. They all probably have terrible security.
It’s incredibly unlikely that adding more would increase the overall security.
As a general rule, the more lines of code, the more bugs. While most programs (short of “Hello world”) will never be bug free, adding programs is unlikely to improve things.
And increasing the number of agencies that banks, or humans have to deal w/ would probably make things worse.
Artificially imposing limits on them is unlikely to yield any good benefits. Trying to require them to be “regional” is a disaster (my credit is spread across a number of states — at least two distinct regions). Forcing a cap on records or monitored people would break the industry entirely, and not in a good way. There are valid reasons for businesses to want to have a sense of a person’s credit before choosing to issue new credit. But the controls are in the wrong place. By default it shouldn’t be easy for anyone to apply for credit in the name of an arbitrary person.
Note: I’m not generally pro any of these groups.
I’m definitely pro-regulating these groups.
Great information. Thank you. I would just like to comment on “…many consumers simply don’t take advantage of such offerings because either they don’t know about them or they find them inconvenient.”. Some people may not choose MFA offerings because of the type of MFA being offered, for privacy reasons. Many MFA offerings require disclosure of a phone number and some people may not want to disclose that information. If a different form of MFA, e.g. token based, might result in broader acceptance.
Since this site is targeted at Americans, Google Voice will let pretty much any US resident (with access to a distinct phone number) apply for a free Google Voice number. You can forward it straight to another phone or use it as a VOIP system w/ text messages being forwarded (or sent as email).
Providing this number instead of your primary number might help address some privacy concerns. Yes, it means Google will know you’re using 2FA, but hopefully they already know that because you’re already doing that w/ them… And the beauty of 2FA is that a token is in general, a token is only good once.
In the long run, NIST has said that SMS auth isn’t acceptable. Going forward, U2F [1] seems like the future: it has hosting support; two browsers (Chrome, Opera*) support it today, one supports it in their alpha channel (Firefox), and one is committed to implementing it (Edge). The remaining big browser (Safari) does not comment on future work as a general rule.
[1] https://en.wikipedia.org/wiki/Universal_2nd_Factor
I would like them to ask the following:
1) how quickly can Equifax implement a system where people can require that Equifax deletes the person’s data from their system?
2) What reasons (aside bankrupting equifax) would Equifax offer not to offer such a service?
3) if Equifax were to be required to offer the above service. Could they offer an offline archive service and how quickly could Equifax restore from this offline service.
So, we call Equifax/Experian/TransUnion/Innovis “credit bureaus”. But it’s probably best to think of them as “Credit Search Engines”.
If someone posts a web site calling your name “Mudd”, then hopefully your name really is Mudd [1]. But, if Google indexes the web and finds the site calling you Mudd, should you be able to tell Google to delete their search record(s) for Mudd?
Europe has created a “right-to-be-forgotten”. And most people laugh at it (see the Streisand Effect). The issue is not the fact that Google found someone calling you Mudd, it’s that someone called you Mudd.
The fact that you can “Google yourself” and discover that someone called you Mudd is actually a feature. And an important one. It enables you to contact the person who called you Mudd and dispute it.
There’s really not much of a difference between what Google does and what a credit bureau does. Both are basically large, searchable, and indexed databases of information — one for the web and one for credit. One distinction is that in general, bureaus charge for searches, whereas Google does not. In both cases, “you’re the product”. Note: there’s a nice caveat, you’re entitled to a free “search” of your own record annually — thanks to the Fair Credit Reporting Act (FCRA) [2].
Imo, it would be worse if companies privately discussed my credit w/o providing any way for me to learn about their slander and seek to correct it. Keep in mind that “More than one in five consumers have a “potentially material error” in their credit file that makes them look riskier than they are.” [3]
Anyway, to close out Mudd. There are two Mudds you need to know about, and crossing their information-files (as credit bureaus are wont to do) would be a serious travesty. The first is Samuel Mudd [4], and while you might think his involvement with John Wilkes Booth is the reason for the expression “if your name is mud”, you’d be wrong (it predates him too). The second is Harvey Seeley Mudd [5] for which HMC [6] is named.
Disclaimer: a long time ago, I received advertisements from their university, I recall an even catchier motto ~if you’re name is mudd you better be good~ or something, but I can’t find it (this was literally “before Google”). I neither applied nor attended. But I still remember them to this day.
[1] https://www.hmc.edu/
[2] https://en.wikipedia.org/wiki/Fair_Credit_Reporting_Act
[3] https://www.brookings.edu/research/the-real-problem-with-credit-reports-is-the-astounding-number-of-errors/
[4] https://en.wikipedia.org/wiki/Samuel_Mudd
[5] https://en.wikipedia.org/wiki/Harvey_Seeley_Mudd
[6] “the most amazing college you’ve never heard of,”
I will be trying to get into 1 or two of these hearings – equifax says I was not an account that was accessed in the hack. I already have credit activity report coming in from the OPM hack. Interesting times.
On Thursday the 28th, I froze my TransUnion credit info, without any flack at all suggesting a lock. I’m over 65 (free freeze in California) with low limit credit, so perhaps that spared me the sales/propaganda.
“On Thursday the 28th, I froze my TransUnion credit info, without any flack at all suggesting a lock.” – KFritz
In the last two weeks I had no issues with any of the companies suggesting I should sign up for monitoring or a lock as I setup a freeze. One forced me to go online, the others allowed me to call. Chex Systems allowed me to get a free report via phone, but the freeze required using the Net.
So far only TU has confirmed by US mail that a freeze is in effect and gave me my pin number.
Did anyone actually get a letter telling them that their Equifax records were hacked? Didn’t they promise to do that (eventually)?
I am not getting anywhere. They say I was, so I got to fill a page out, sort of. Been 2 to 3 weeks, still no reply from them. Computers are shut down. I enrolled. That’s it. I don’t know what to do? ?
Freeze by phone. Brian has posted an article w/ the instructions.
My question:
Should credit bureaus face legal liability to consumers when they distribute reports containing false information about them?
So, the question is who’s at fault.
Let’s say a Cellular company records information about a customer and the customer fails to pay their bill on time.
The Cellular company reports this to a credit bureau.
You eventually find this black mark on your credit report.
Where should liability be?
On the bright side, it looks like disputes are done via the bureaus as opposed to contacting the company that created the data.
You may hate the bureaus, but as someone who constantly gets email from various incompetent cellular vendors about their customers acting as if that’s me (because someone entered my email address), I’d rather not have to deal w/ dozens of incompetent cellular vendors. 4 incompetent credit bureaus is more than enough points of contact.
Breaches should certainly incur liability (whether that’s Sonic or Equifax or …), but reporting something that someone else reported… As long as your report is frozen and no one sees it before you dispute it, I don’t think that liability should fall w/ the middle-man.
If it turns out that a certain vendor (pick your hated Cellular/Cable company) has a huge percentage of bogus reports, then ideally the middle-man will start penalizing that company, since they’re wasting its time/money on all these disputes.
These processes are fairly similar to how credit card works. If a merchant makes a bogus charge to my credit card, and I dispute it (initially, I actually am supposed to make a good faith effort to complain to the merchant directly), and get when I nowhere, I can contact my credit card issuer and dispute it, and they’ll fix it for me. If a certain merchant makes a large number of bogus charges to accounts, the credit card company will start to penalize it. (At the very least through chargebacks, but eventually by increasing the processing/servicing fees.)
Sure, the credit bureau should be liable for distributing false info about you. But in turn, they should have recourse against whoever submitted that info, if it wasn’t their fault. They could easily achieve that via contract terms. You’re wronged by the credit bureau, they know the source of the info and can go after them.
I would ask them how they think SSNs ever made sense for authentication and why they still think so, even though they gave away 143 million SSNs to attackers?
And if I ever got a chance to talk to the committees, I would pitch a structural reform for creditors to encrypt data about me with my public key, and anyone who wants to read my data would need my private key, which means they’d need my permission.
I laid it all out in a video presentation at:
http://dgregscott.com/143-million-reasons-credit-reporting-industry-reform-part-2/
– Greg Scott
Brian, saw your following article:
https://krebsonsecurity.com/2017/08/flash-player-is-dead-long-live-flash-player/
but the comment section on that article has been disabled, so my apology for posting my question here.
I am using a Windows 7 Pro PC, how do I remove Adobe Flash Player completely from my PC? i.e., I don’t want any traces of Flash Player (files, folders, LSOs, registries, etc.) on my PC. Thanks.
helpx.adobe.com/flash-player/kb/uninstall-flash-player-windows.html
Last I know there’s a separate Adobe app specifically for removal.
You should be able to remove it from the Add/Remove Programs panel in Windows 7. There is also an uninstaller that Adobe makes available here:
https://helpx.adobe.com/flash-player/kb/uninstall-flash-player-windows.html
Finally, if you use Google Chrome as a browser you should know that it bundles its own version of Flash. To disable it inside Chrome, type or cut and paste “chrome://settings/content” into the address bar (without the quotes), and click on the Flash result. Then move the slider button to the left next to the setting “allow sites to run Flash”.
Hi Claire –
Here’s a link from Adobe on how to get rid of the flash player. Note the caveats.
https://helpx.adobe.com/flash-player/kb/uninstall-flash-player-windows.html
– Greg
Thank you.
Why did you run an F5 load balancer as a WAF (web application firewall)? What was your RFP process to ensure superior product selection? Who configured it? Were the alerts being monitored? What about a database activity monitoring or a database firewall? Why didn’t you have a database firewall to detect and prevent unauthorized downloads of confidential information? What is Equifax’s DLP strategy? …yada, yada, yada… I’ve been a CISO for a few years and have had the displeasure of working for incompetent companies and cultures over the years. I’ve seen my share of charlotins over the years, especially in the financial service industry. I’ve met the heads of almost every major Wall Street firm and worked there myself and am flabbergasted by the level of incompetence and ego displayed, not to mention the misdirected obsession of the regulators on risk, risk, risk… Risk didn’t hack your system, a hacker hacked your system. Risk didn’t run the wrong products to protect consumers, an incompetent CISO more interested in music theory did. Risk didn’t set up an insufficient patch management program or vulnerability reporting methodology. I’ve seen it all and just walked away. I protected one of the highest volume ecommerce websites in the world for a decade without a single hack. I know the scewed PCI regulations like the back of my hand, which favor credit card companies over merchants. Today I protect national critical infrastructure for a segment of society, but I refuse to deal with the politics and egos of the financial services industry, which consists of the highest paid people in the world with the least effective impact on protecting individuals. Everything Equifax and the likes has coming, they deserve and from what I’ve read and heard, they were grossly incompetent. Far beyond basic negligence threshold. So when the lawyers and attorney generals are done with them, let them go the way of Enron and Worldcom, Washington Mutual, Bear Stearns and all the others… Its the process of natural selection which must take place. In fact AIG should be gone too, but Goldman Sacks is so plugged into running all levels of government, not only didn’t they take a loss but they make 100% on the dollar. Ourtrgeous. Well at least they fired their 3 piece suit CISO a few years back before they went the way of Equifax. My diatribe.
Wow, that was real. Thanks for sharing and protecting. Probably the best post to an article ever.
Why wasn’t every social security number either tokenized or protected by a salted hash or at a minimum a salted sysmetric algorithm??? How many state privacy regulations was Equifax in breach of?
Great point! The follow on question is “Why don’t we have laws regarding data governance that explicitly state Highly Confidential (PI) must be encrypted/tokenized at rest?”
We must tokenize or otherwise encrypt credit card information because the major CC bureaus require us to do so or not process transactions.
Maybe the Feds need to adopt a similar (but more technically stringent – PCI doesn’t go far enough is some areas) program for consumer information. It could be built on the existing guidance and audit backbone (ISA/PCIP/QSA) with expanded data type and class coverage.
They could even adopt the tiered system based on quantity and type of information retained.
This is an interesting question.
At the end of the day, there are:
1,000,000,000 possible SSNs (including ITINs — afiau they share a number space — for simplicity, let’s call them SSNs for the duration of this comment).
Let’s say that the SSN for each record is salted in line with your suggestion. (The value of salting is to prevent recycling of hashing information for lookups of other records of the same type.)
They leaked approximately 140,000,000 potential SSN-like numbers.
Because they’re salted, essentially each record has to be cracked independently.
There are perhaps 5 commonly suggested secure hashing algorithms:
PBKDF2, argon2, bcrypt, scrypt, …
For passwords, the usual constraint is “acceptable time delay for user with correct password to be allowed in”. If it took you a year to unlock your house with your house key, and you were planning to go into your house 2-4 times a day, you’d be really upset. For passwords, the acceptable delay is probably ~1 second (probably less, but as a general rule, any software that takes longer than 5-10s to respond is considered broken by normal users, and there are other delays including general network latency that eat into your budget).
For simplicity of analysis below (there are *way* too many tune-able variables above), let’s assume PBKDF2 is selected with a fixed time goal at a fixed point in time (5 years ago). Argon2 was published in 2015 so it wasn’t even a possibility then.
*Updating a hashing algorithm requires waiting for a match for a record and then rehashing everything. If a record doesn’t get updated often, then this may take a while (one could of course brute-force the stale records the same way a hacker does — or intelligently by adding risk and recording the last time a raw record was updated, w/ e.g. month granularity — the risk is that a hacker could then reduce their keyspace for searching, assuming they also get access to this table — I don’t think anyone does this, the risks almost certainly outweigh the rewards). Roughly, this means that there will /probably/ be records w/ stale algorithms in the database even if one chooses to update the algorithm, and also there’s a disincentive to do so, so, we’ll assume they’re lazy and don’t update their algorithms. (Technically, one could update records using a current hash-cost at each access, but, I’ve never heard of anyone doing this, and this time is cost that someone is paying for, I don’t expect the bureaus to elect to pay for it.)
Say the bureau picks a 1-second hashing penalty for its operations. Their computers aren’t going to be current (let’s guess they’re 5 years old — i.e. from when they picked their algorithm). With some hand waiving, a current computer could check that same one token in 1/10 the time (Moore’s law at one point said CPU power doubled every 18 months, 5 years gives us a bit over 3 cycles, which works out to a 10-fold improvement in cpu power for equivalent class hardware). A hacker isn’t going to use equivalent class, they’ll probably use GPUs which allow for parallelism.
There’s actually a thesis project [2] covering cracking our chosen algorithm on GPUs. The thesis paper roughly suggests [3] that a GPU can perform its work 40 times faster than a CPU.
What follows is back-of-the-napkin calculations. This isn’t my area at all.
[Disclaimer: I’ve made a number of errors trying to copy the numbers through this post. It wouldn’t shock me if I’ve made additional embarrassingly simple serious mathematical errors in my calculations below.]
Naively, 1 modern GPU five years after our hash was selected can perform 400 checks in one second. For the entire SSN space, that means a single GPU could search it in 25,000,000 seconds (~290 days).
But, the leak wasn’t the entire SSN space. It was 140,000,000 IDs (~1/7th of the space). A single GPU could search that space in ~97 days.
This is a very paralellizable task. 8 GPUs/computer, 12 computers ~ one day. Given that there’s value in stealing this information, it’s fairly likely that there’s value in renting (or stealing!) the CPU/GPU power to perform this.
From this, we can hopefully conclude that the protection gained against an interested attacker is pretty minimal given the value of the data being protected.
That assumes that storing hashed SSNs is viable. Let’s investigate that assumption:
So, the problem with this model, is that most likely the SSN is used as the key to a table for lookups/insertions. i.e. A data provider (a person’s cell phone carrier) provides a record saying “SSN xxx-yy-zzzz paid their bill late”. The bureau wants to quickly add that record to their database. If all they have is an unsalted SSN for insertion and no idea which user that corresponds to, they’d have to crack their database to perform the insertion (and that’s expensive, as we assume that insertions are fairly common). If the records weren’t salted, then the hash of the SSN would immediately yield the answer (and it would mean that one could calculate all of the hashes at once, more or less wiping out their perceived value). Ok, so maybe they have some hints:
Let’s say that the bill is for “James Smith”, the bureau can try the salts for each of the 38,313 James Smiths in the US [4], that takes 38,313 seconds on their 5 year old hardware (~10½ hours). And that’s assuming that the Cellular provider has the correct name (and doesn’t know that there should be a middle initial). The bureau is doing these inserts/updates constantly. It can’t afford delays like this.
Essentially, the SSN is being used by the bureaus to merge two database tables because it’s convenient. If the field becomes hashed, then it’s no longer convenient, and their business becomes pretty untenable.
They’re obviously not going to do that…
Going back to James Smith one more time. Let’s say there were no SSNs, how would credit work? Should the 5th James Smith have the credit score of the 1st one? Obviously not. What if two James Smiths happen to have lived in the same apartment building? Should their scores be merged? Obviously not. Some identifier needs to be used to avoid conflating these people. (If you don’t like the example of Smith, you can envision Maria Rodriguez, Zhang Wei Lee, or Ji-woo Kim in an appropriate ethnic area.) At one point part of an identifier was a person’s birthday. And if there are only 10 people, that’s fine. When you pass 23 [5], the odds are even that there’s a simple collision on birthdays. Aha, you might say, but we also include their birth year! Great, meet Joanna Rivera [6] of Florida who sadly was merged at birth with Joannie Rivera (also born in Florida on the same day). And just for reference, the SSA considers this a possibility, it’s the second explanation for why they’ll issue a new SSN [7].
Some other things to consider: When someone marries/changes their name, should their credit start over from scratch? (There are two other cases where the answer is stranger: Witness Protection and Anti-stalking.) The normal answer is “no” — someone w/ good credit shouldn’t lose their credit for marrying, and someone w/ bad credit shouldn’t be able to get a clean slate by changing their name. Should a person be able to get new credit/lose their history by moving? (What if they’re homeless?) In general, the answer should be no. For credit to work, it needs to be durable in the face of a number of changes. If you’re curious, errors wrt the date of birth of people also happen.
Essentially, a number that everyone can agree to use to track an individual was going to evolve into existence because there’s a real need to correlate people across organizations.
——————–
Another approach is that the first time the bureau gets a record for someone they issue their own ID and then send that out to be used instead. At this point, you’re basically trading the SSN for someone else’s private number. Sure, if the number space is bigger, it might help a bit, but it’s still a number that’s going to be used everywhere, and it’s *going* to a leak.
——————–
The best path forward is to treat this number as public (from a security perspective) — acknowledge that it’s a public identifier and not a valid private authenticator. And make it easy for people to freeze their credit files and hard for unauthorized entities to access/unfreeze them.
[1] https://stackoverflow.com/questions/11298184/about-how-fast-can-you-brute-force-pbkdf2
[2] https://github.com/WOnder93/pbkdf2-gpu
[3] https://github.com/WOnder93/pbkdf2-gpu/blob/master/thesis/thesis-final.pdf
[4] https://blogs.ancestry.com/cm/calling-james-smith-10-most-common-first-and-surname-combinations/
[5] https://en.wikipedia.org/wiki/Birthday_problem
[6] http://www.wptv.com/money/id-analytics-40-million-social-security-numbers-associated-with-more-than-one-person
[7] https://faq.ssa.gov/link/portal/34011/34019/article/3789/can-i-change-my-social-security-number
I tried to freeze my credit via “trustedidpremiere” as Equifax advised. Almost every day I get an email telling me more information is requested. What happened to the “registration process”??? I would like to see the former CEO held liable for the hacks and the delay in reporting such hack.
I also would like a complete overhaul of all three credit bureaus, and this includes the newer small one name Innovus.
NO MORE USING SOCIAL SECURITY NUMBERS.
Unfortunately as CEO of a company that has failed so significantly at protecting the data it “owns”, I don’t expect questions posed to him by anyone, Congress or kindergarteners, will results in any new revelations about how or why ( we already know why it happened and regulations, and audits and oversight will fix that for a short time until those becomes routine and ultimately relaxed again) What he does know particularly well, is the syndicate style of operations that make up the credit bureau “industry” . This is an industry which doesn’t serve anyone but itself The problem is that ( as Colbert and others point out) the credit bureaus ( not just Equifax, but the other 3) have monopolies on gathering and harvesting data on all of us so they can sell it to others who ultimately want to sell us something. We are not their customers, we are their products. It’s a great business model, as long as they have to answer to no one about their practices. So a new norm exists, with respect to the process of establishing and extending credit to Americans which centers on the ability to accurately establish the identity of those Americans which in one fell swoop was handed over to the bad guys. So the questions: What changes must be made to the industry to allow Anericans to have control of what these companies alone have full control of ? Credit freeze aside, his former company has changed the way Americans can reliably identify themselves and others, what operational changes must be made by all credit bureaus to change from solely serving the creditors ( who pay them) and serve the consumers who didn’t fully realize until now that they were enabling them to be paid? As a business executive, if anyone lets him into a boardroom again, what would he advise the credit bureaus to do from this point forward to reliably identify credit consumers?
For your data, Mr. Krebs: I froze my and my husband’s credit at all four bureaus as you suggested. Thank you. Additionally, I have been the victim of identity theft four times in my life in which my information was used in a felonious manner. In one case at least, the person using my ID was arrested twice. I’m still demanding takedowns from every arrest and mugshot site on the Internet nine years later.
Based on the evidence that Equifax failed to update a security patch for Apache for 4 1/2 months, why should consumers EVER have to pay for a credit freeze considering your company’s incompetence has compromised all of your customers financial information?
I thought it was nine (9) weeks that it went unpatched.
Nope.
Apache Struts CVE-2017-5638 original release date: 03/10/2017 [1]. FWIW, Apache Struts 2.3.5 dates to late 2012 [2], so afaict it’s theoretically possible that someone was silently exploiting this against some site for years… But that’s the zero day window, let’s focus on the declared window…
«Equifax has said it discovered the data breach on July 29. On Friday, it said it waited until it “observed additional suspicious activity” a day later to take the affected web application offline.
And on August 2 Equifax contacted Mandiant, a professional cybersecurity firm, to help the company assess what data had been compromised.
With help from Mandiant, Equifax was able to determine a series of breaches had occurred from May 13 through July 30, the company said.» [3]
It was apparently exploited starting 9 weeks after the CVE was published and continued for 11 weeks.
[1] https://nvd.nist.gov/vuln/detail/CVE-2017-5638
[2] http://web.archive.org/web/20150715102740/http://struts.apache.org:80/downloads.html
[3] http://money.cnn.com/2017/09/16/technology/equifax-breach-security-hole/
It went 9 weeks between being published as a CVE and when the exploitation started. It took another 11 weeks before they discovered and took down the service. We have no idea when it was patched.
Their initial solution was taking down the service, which is a good first step, but it’s theoretically possible they never restored the service, in which case it could technically still be unpatched today.
Questions for Mr Smith may not be answered with any degree of honesty or empathy. Don’t expect justice Bernie Madoff style.
Before Mr Smith testifies before Congress, his lawyers will prepare him to answer questions so as not to incriminate himself and to make him look as much a victim of the breach as the 143 million Americans and unknown number of non-Americans.
As far as Mr Smith is concerned, his job as CEO was to create wealth for the company’s stockholders, grow the business and make Equifax profitable. That he did in spades. He sees himself as a success. He has boasted about how he got all the data for free and sold it at an obscene profit.
He will state that the hackers are to blame for the breach, not him. In regards to the response after the breach itself, he will probably say it could have been handled better, but (and there is always a BUT), not any differently or faster than he himself ordered. Dealing with a state-sponsored sophisticated attack is complicated. He will reject any accusation of incompetence. This man is arrogant.
The hard questions should be for the lawmakers…
Why is it lawful for Financial Institutions to hand over private customer information to credit reporting companies?
Is there not an expectation of privacy when it comes to private data being stored by any company?
Why is it lawful for a private company to send payroll info to a credit reporting bureau for them to profit from ?
Why are credit reporting companies allowed to charge fees to consumers for the secure management of their private data when they never authorized them to have it in the first place?
When will the Government stop the use of SSNs as being used as ID for anything other than government services?
Will the government review the corporate charter of credit reporting companies – will the government withdraw permission for them to operate as they do today by introducing stricter regulation or will they be reclassified as a utility?
We’re missing the biggest risk of the Equifax breach, the future phishing that this data will enable. As you’ve highlighted everything needed to steal ones identity, open new lines of credit or file fraudulent returns is out there.
Credit monitoring or freezing services can’t even be a tourniquet for the real intent and purpose of this breach, which is to be able to create authentic lures and more aggressive phishing campaigns that will target every company and organization the 143MM people affected are associated with.
Why can’t the government reissue SSNs? While they are at it, can they reissue with a little more variety? I understand scoping is a nightmare. All of these breaches boil down to protect stupid mechanisms with predictable patterns. The previous comments on tokenization are great, but since everyones SSN is essentially compromised (let’s be honest…it is), then maybe the SSA, Credit Bureaus, Insurance Providers, and FIs basically foot the bill and fix the problem. Keep in mind, first 5 digits are a variety of where your SSN was issued and what year, and the last 4 numbers are random. Let’s stop pretending like this is a “secret” unique identifier.
On a small scale, the SSA can reissue an SSN.
Practically, renumbering everyone would be pretty painful and wouldn’t solve many problems.
There’d need to be a fairly easy to use/access database for the correspondence mapping. Anyone who expects that to be kept secret is naïve.
The most important thing about an SSN that people have to understand today is that it isn’t a secret. People need to understand that it’s used primarily as a lookup. Once we stop pretending that it can be used for authentication, we can start moving forward.
It’s unclear what the right authentication approach would be. It might be a smartcard. It might be a smartcard + physical locations that can perform secured affidavits / notary services. But whatever it is, it will have to be something where there are places around the world that can be used to validate that a person is who they claim to be and that they want to authorize a certain action.
And, of course, we’ll need some way for people to void and replace that object, as it will be lost, stolen, and destroyed in disasters (natural and man-made — does climate change count as man-made?). And we’ll need some protection against pranksters voiding other people’s cards.
Also, keep in mind that the SSN is in principle designed for the elderly to receive benefits. If your relative is 112, you don’t want to rely on them to remember a password to unlock their benefits.
Passwords work really poorly when used less than once a year. And much worse in the elderly.
I personally have 3 SSN like things (each country I’ve lived in has issued me their own equivalent identifier, and some have issued me temporary ones first). In general, I use my SSN very rarely, and mostly because it’s faster than finding the bank-id to perform a “this is my account number” — its value is that it’s short — it’s shorter than my name. But my bank doesn’t treat that number as an authenticator, it’s equivalent to my bank account number (which is also not an authenticator), it’s just an identifier. (My bank asks me stupid KBA questions that anyone can guess.)
Disclaimer: I used my SSN today to freeze one of the lesser credit bureaus, that’s an anomaly for me.
When did I sign up to be the customer of any credit bureau? If I start my own, can I collect this information?
INFOSEC is not taken seriously and when government (OPM, etc.) and business (Yahoo, etc.) can lose massive amounts of information that they deemed ‘necessary’ and ‘sensitive’ without repercussion or reimbursement of the individuals involved (since you must prove that you have taken a loss to sue). By the time it is known that we have taken a financial or personal loss (SWAT, intrusion, etc.) it may be too late. Stolen data can not become safe again.
Hi Brian,
Following a breach, the consumers typically have a way to avoid doing business with the companies, such as Target, Sonic or Wendy’s. However, with Equifax’s handling, are there ways we can cease doing business with the bureau? Can I demand Equafax stop tracking, and selling my credit information?
or can we place the credit freeze, and when credit information is needed, we only un-freeze the other two bureaus? and ensure they no longer profit from our information?
Thanks,
Tsailing
The information the credit bureaus maintain include:
– publicly available records, including court judgements, deeds, marriage and birth records, driving histories and traffic tickets, and election records, and some tax records
– information that consumers voluntarily provide to creditors, banks, mortgage brokers, insurance providers, public utilities, etc.
– information gathered by creditors and shared by their partners, including consumers’ behavioral histories, such as regularity of payments, outstanding balances, frequency and locations of credit card uses, etc.
Since all this information is obtained either through public records or voluntary consumer behaviors, there is no way you can entirely avoid dealing with credit reporting bureaus.
The best you can do is freeze your files at the bureaus, stay out of trouble with the law, and minimize your use of financial institutions and public utilities.
In short, Reader is right.
If you specifically don’t like Equifax and somehow think its competitors are better (they aren’t) or that other countries have stronger protections (they don’t — Canada’s for instance are weaker by far, and the UK’s are even weaker than Canada’s), you can move to another country where Equifax doesn’t do business [1].
A better (personal) strategy is moving to a state w/ stronger consumer protections (in general this is either California [2] or New York [3]).
But, while it might be nice to be protected, if you live outside of CA/NY, your voice is more valuable reaching out to your congressional delegation and demanding stronger protections and accountability (and voting for a different president…).
If you live in Alabama, South Dakota, or the Northern Mariana Islands, you should write to your regional legislature and demand notification protection [4]. Otherwise, you can review the laws for the other 48 states, D.C., and 3/4 territories in the National Conference of State Legislatures’s table [4]. …
Big databases of valuable information will be breached, because there’s value in breaching it. The best things we as consumers can do are:
1. Decrease the value of the data (e.g. by freezing our reports, making them less useful).
2. Demand better notification.
3. Demand stronger oversight.
4. Demand harsher penalties to executive/board level and companies as a hole.
[1] https://en.wikipedia.org/wiki/Credit_bureau
[2] https://www.bna.com/new-california-data-n57982067883/
[3] https://its.ny.gov/breach-notification
[4] http://www.ncsl.org/research/telecommunications-and-information-technology/security-breach-notification-laws.aspx
Demand all you want, your words will not change anything, it is quite clear big business have already bought out all the politicians in the US. Money is doing all the talking.
Lock isn’t the same thing as a freeze. The “lock” is near worthless as its not covered under law and who knows where liability lies if the lock doesn’t work as designed.
The “lock” has been a service the different agencies have been selling for awhile. Equifax has been selling a service where for $4.95 a month you could “lock” your credit at all three agencies. But its not the same thing as a freeze as any company that has a previous relationship with you will still be allowed access to your file. For example if you have a checking account at bank X, a “lock” won’t keep someone from taking out a credit card in your name at bank X.
Consumer reports had a good right up on what equifax is offering in its “lock” and why it isn’t as good as a freeze:
https://www.consumerreports.org/credit-bureaus/why-credit-freeze-is-better-than-credit-lock/
Why aren’t they telling us who had their ssn compromised, who had ssn and DL compromised, and who had ssn, DL, and credit card compromised? We deserve to know HOW each person was affected as each situation warrants different response.
Government regulation of businesses such as these needs to come back in a big way – a breach of this magnitude and their response is beyond unacceptable!
There IS significant government regulation of this industry. Mostly it is designed to protect the industry from you and me. I’m a big Bruce Schneier fan, the only effective way to regulate industry is through liability and insurance.
And hold you congress-critters liable also. Never for a second think that they think that they work for you.
@Brian, “Sept. 7.However,” is missing a space.
(I’ve been meaning to write this for a while, but first I had to read through the comments to see if anyone noticed…)
(Great article as always — I like your questions. I’m still thinking about what I’d ask).
Being a veteran cybersecurity executive and practitioner I have a burning question in my mind about the breach that I haven’t heard anyone broach yet. It isn’t about the data theft but more around data integrity. We all know this is also a serious risk once data has been tampered with. How are consumers to be assured that the proprietary credit score algorithm that calculates credit score is still intact or ever was for that matter? This score affects many peoples lives so the company should be asked to produce forensic evidence this score is indeed legitimately still intact and not tampered with.
According to the WSJ, Equifax had a team in place for patch installation, what makes you think that they didn’t attempt to patch the Adobe Struts flaw back in March when it was released? Could it be that they needed more time to patch, rewrite, and test the older apps developed with older version of Adobe Struts and given the documented mass hacking attempts within 48hrs of the patch release, it was already too late with the hackers breaching their system? If I’m not mistaken, Equifax hired Mandiant back in March to investigate a possible breach and they couldn’t find anything. Mandiant is not cheap and is considered the best in the forensics business. If this was a sophisticated Chinese government hacking job as the WSJ suggests, they could have very slowly siphoned the Equifax data over weeks without being detected. I’m curious to hear of the cybersec defenses Equifax had in place to prevent a data breach, in addition to what exactly took place in regard to the Adobe Struts patch job since the entire allegation of incompetence revolves primarily around this one issue.
We are missing the point in this breach. The very fact that someone can use data stolen from Equifax to impersonate me for financial gain is THE issue. Social security number and other sensitive information should not be used as a means of authentication. We must implement a national solution that securely authenticates individuals (e.g., using biometrics and MFA).
This is the issue that the hearings should be focused on. Until the fallacy of using SSN as a means of authentication is addressed these breaches will continue. It is time for Congress to devalue SSN and other similar data by replacing them as means of authentication with a much better means of authentication.
Biometrics can be problematic too. The OPM had a hack a couple years back, where data including fingerprints was compromised.
And people are now using 3D printers, which can print off fingerprints, and then be used to unlock phones.
https://3dprint.com/153234/3d-printed-fingerprints-security/
>Why did Equifax decide to wait four and a half months to apply this critical update?
That one’s easy. Onerous change control process. At any big financial institution, change control is a strict and rigorous process that can mean it takes weeks to months to implement something. There’s a running gag about working for AIG, even as a contractor: bring a book for your first 3 weeks. That’s how long it takes for them to get you a laptop and system access to do your job. Equifax won’t be much different.