On Dec. 6, 2017, approximately USD $52 million worth of Bitcoin mysteriously disappeared from the coffers of NiceHash, a Slovenian company that lets users sell their computing power to help others mine virtual currencies. As the investigation into the heist nears the end of its second week, many Nice-Hash users have expressed surprise to learn that the company’s chief technology officer recently served several years in prison for operating and reselling a massive botnet, and for creating and running ‘Darkode,” until recently the world’s most bustling English-language cybercrime forum.
In December 2013, NiceHash CTO Matjaž Škorjanc was sentenced to four years, ten months in prison for creating the malware that powered the ‘Mariposa‘ botnet. Spanish for “Butterfly,” Mariposa was a potent crime machine first spotted in 2008. Very soon after, Mariposa was estimated to have infected more than 1 million hacked computers — making it one of the largest botnets ever created.
An advertisement for the ButterFly Flooder, a crimeware product based on the ButterFly Bot.
ButterFly Bot, as it was more commonly known to users, was a plug-and-play malware strain that allowed even the most novice of would-be cybercriminals to set up a global operation capable of harvesting data from thousands of infected PCs, and using the enslaved systems for crippling attacks on Web sites. The ButterFly Bot kit sold for prices ranging from $500 to $2,000.
Prior to his initial arrest in Slovenia on cybercrime charges in 2010, Škorjanc was best known to his associates as “Iserdo,” the administrator and founder of the exclusive cybercrime forum Darkode.
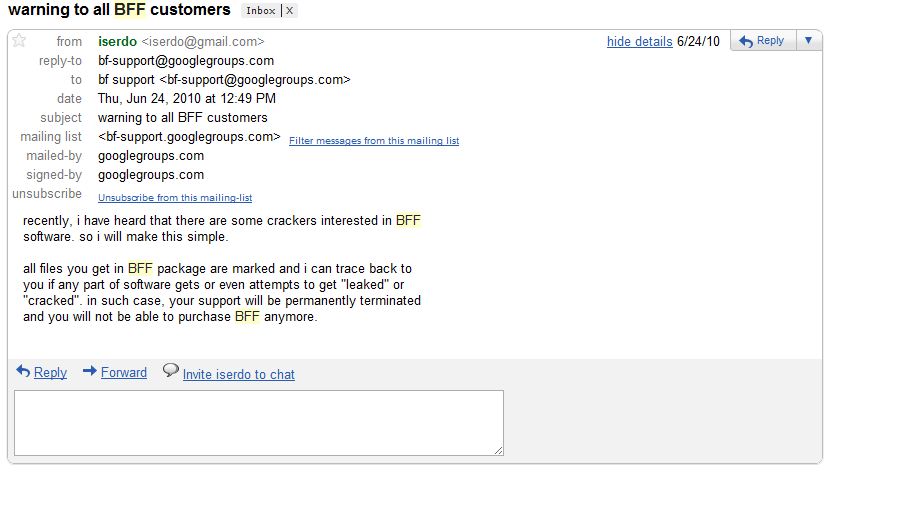
A message from Iserdo warning Butterfly Bot subscribers not to try to reverse his code.
On Darkode, Iserdo sold his Butterfly Bot to dozens of other members, who used it for a variety of illicit purposes, from stealing passwords and credit card numbers from infected machines to blasting spam emails and hijacking victim search results. Microsoft Windows PCs infected with the bot would then try to spread the disease over MSN Instant Messenger and peer-to-peer file sharing networks.
In July 2015, authorities in the United States and elsewhere conducted a global takedown of the Darkode crime forum, arresting several of its top members in the process. The U.S. Justice Department at the time said that out of 800 or so crime forums worldwide, Darkode represented “one of the gravest threats to the integrity of data on computers in the United States and around the world and was the most sophisticated English-speaking forum for criminal computer hackers in the world.”
Following Škorjanc’s arrest, Slovenian media reported that his mother Zdenka Škorjanc was accused of money laundering; prosecutors found that several thousand euros were sent to her bank account by her son. That case was dismissed in May of this year after prosecutors conceded she probably didn’t know how her son had obtained the money.
Matjaž Škorjanc did not respond to requests for comment. But local media reports state that he has vehemently denied any involvement in the disappearance of the NiceHash stash of Bitcoins.
In an interview with Slovenian news outlet Delo.si, the NiceHash CTO described the theft “as if his kid was kidnapped and his extremities would be cut off in front of his eyes.” A roughly-translated English version of that interview has been posted to Reddit.
According to media reports, the intruders were able to execute their heist after stealing the credentials of a user with administrator privileges at NiceHash. Less than an hour after breaking into the NiceHash servers, approximately 4,465 Bitcoins were transferred out of the company’s accounts.

NiceHash CTO Matjaž Škorjanc, as pictured on the front page of a recent edition of the Slovenian daily Delo.si
A source close to the investigation told KrebsOnSecurity that the NiceHash hackers used a virtual private network (VPN) connection with a Korean Internet address, although the source said Slovenian investigators were reluctant to say whether that meant South Korea or North Korea because they did not want to spook the perpetrators into further covering their tracks.
CNN, Bloomberg and a number of other Western media outlets reported this week that North Korean hackers have recently doubled down on efforts to steal, phish and extort Bitcoins as the price of the currency has surged in recent weeks.
“North Korean hackers targeted four different exchanges that trade bitcoin and other digital currencies in South Korea in July and August, sending malicious emails to employees, according to police,” CNN reported.
Bitcoin’s blockchain ledger system makes it easy to see when funds are moved, and NiceHash customers who lost money in the theft have been keeping a close eye on the Bitcoin payment address that received the stolen funds ever since. On Dec. 13, someone in control of that account began transferring the stolen bitcoins to other accounts, according to this transaction record.
The NiceHash theft occurred as the price of Bitcoin was skyrocketing to new highs. On January 1, 2017, a single Bitcoin was worth approximately $976. By December 6, the day of the NiceHash hack, the price had ballooned to $11,831 per Bitcoin.
Today, a single Bitcoin can be sold for more than $17,700, meaning whoever is responsible for the NiceHash hack has seen their loot increase in value by roughly $27 million in the nine days since the theft.
In a post on its homepage, NiceHash said it was in the final stages of re-launching the surrogate mining service.
“Your bitcoins were stolen and we are working with international law enforcement agencies to identify the attackers and recover the stolen funds. We understand it may take some time and we are working on a solution for all users that were affected.
“If you have any information about the attack, please email us at [email protected]. We are giving BTC rewards for the best information received. You can also join our community page about the attack on reddit.“
However, many followers of NiceHash’s Twitter account said they would not be returning to the service unless and until their stolen Bitcoins were returned.




Apparently, background checks/HR security is not top priority at Slovenian based companies….
Please do not talk in such a tone if you don’t have a clue about Slovenia. Mid-europe country – we have quite high standards, are part of EU.
And about HR security – as far as I understand, his father is co-owner of NiceHash.
yes slovenia,ukraine russia,estonia,poland they all soviet block. soviet criminals
Yeah, and what bad label do you want by association of the worst in your country? maybe just; troll, is good enough.
O Joe, you also don’t know much about history, do you? We were part of Yugoslavia, which had no good relations to the Soviet block.
Criminals can be found everywhere, so where are you from?
Us American Rats are no better. We’re only worse because we have the “America is best” superiority complex thrown on top of our stupidity.
I don’t know any Polish hackers and all the rest are ethnic Russians. While Slovenia is the exception that confirms the rule.
Mate, you are too stupid to breath without instruction. Only incredible moroms can generalise to such extent. Congrats, you one and only…
I’ve deleted several inflammatory, xenophobic comments here. Keep it clean please, and cool it with the ethnic slurs, or you will find your comments deleted and your addresses blacklisted. Thank you.
Love your work, Krebs! Keep on keepin’ on.
It is/was his company – his father had to be listed as the official owner exactly because the son had a criminal past.
Isn’t stealing Bitcoin similar to stealing money that has been marked? Similar to when the ransom is paid in paper money that the serial numbers have been recorded by law enforcement. If try, how can these stolen Bitcoins be used?
Stolen bitcoins are mixed with clean ones in tumblers for a fee.
The bitcoins are marked but nobody selling or purchasing can spot the marking. If you steal bitcoins then trade them to someone in exchange for something, that person won’t know that the bitcoins are invalid, and frankly they aren’t invalid, they’re just being tracked by their previous owners.
The previous owners get to look on, helplessly, as they move from person to person to person to person, often times with nobody except the first hop or second hop in the chain actually being part of the crime. After that it’s simply someone who sold something that the criminal wanted to purchase.
Until there’s a central spot for people to check to see which bitcoins were stolen, its really just a big crapshoot whether the BTC involved in your purchase was obtained legitimately or illegitimately. Even if something was put in place, a central clearinghouse for information about bitcoin theft, it would be a matter of ethics for the people involved in the BTC transaction to check vs. not check. And BTC isn’t exactly a hotspot of ethical activity.
On a technical level it doesn’t matter though because transactions can’t be reversed once they’re finished. You have to catch the criminal while he’s still in possession of the BTC in order to send them back to their original owners. Not by reversing the transactions but by creating new ones.
That is until people start going missing…
Then the very rich (they had more than one stash of BTC and ate all millionaires) and very annoyed (because they lost a few $million) contacts each of those people, and asks who they sold the thing to, what was the shipping address, etc. With a warrant or with a lead pipe, they get the info, and get closer to finding the thief.
Eventually they find the thief. They then likely torture the thief to take back the Bitcoin.
Just sayin’
That’s not quite how it works, but ok
Correction – the news outlet is Delo not Delo.si.. That’s just the newspaper’s website.
Another newspaper (Dnevnik) reported that he was unrepentant and refused to admit guilt at the last trial.
After he was jailed some Slovenian “intelectuals” promoted a theory that it was all a US witch hunt.
Nice work !
Morning Krebs!
Not sure where to post this. Shipping Warning. The shipping is so awful that it is a security problem .The recycled tracking numbers are sending items and wrong items everywhere. Please warn people to check on their shipped presents. They may show as delivered, are not
This is a defense of Brian’s article. I’m in the Midwest. The news here is mostly politics, very little on crime and punishment, or science and electronics. As such, no coverage of the aforementioned incedent. But it affects us all. Gives the reader a clearer picture of what’s going on in the world. Remember each news source is controlled by an editor who decides if a story is important enough to spend their resources on. Unfortunately, crime is manpower intensive, it takes a lot of reporters to cover, and sometimes they need a picture so that’s two people per article, whereas one person for a political beat where it is scheduled?
No chance that this guy essentially stole the bitcoin from himself I suppose
Found your blog so informative and so in depth. Finally got some quality in hacking news. Thanks!
“.The recycled tracking numbers are sending items and wrong items everywhere. ”
I’ve seen this. I printed two Fedex labels to ship 2 packages to different places – on different dates no less, days apart – and when I looked at the photos I took of the packages w/ label after the fact I was shocked to see the exact same tracking number on 2 separately addressed packages. I then confirmed that in the Fedex software, yep, it had somehow re-used the old tracking number.
This took a few days to get settled. “I’m sorry sir that package says it has been delivered when I track it.” – oh it was painful.
Finally they found it on a shelf near Atlanta after 10 days.
“Recycled” tracking numbers?! Doesn’t that defeat the sole reason for tracking numbers? This sounds like a scam – someone’s getting paid twice for the same “number” (local retail shipping store/independent vendors?) or getting to ship their stuff on someone else’s nickle through hacking the system.
One thing that bothered me in that interview is his total lack of self criticism or in fact modesty – a very dangerous quality for anyone working in security.
He says NiceHash did nothing wrong, other than not excluding ANY kind of human factor (which I doubt is ever _truly_ possible), yet going from a compromised developer computer to a hacked main production server still reeks of a lack of operational security. And on the question of why the coins were not in cold storage he vaguely mentions some operational difficulties with that – if I were the journalist I would ask him how come they couldn’t ever figure out that bit? Was it a lack of caution or just a lack of competence? Or perhaps just the standard startup mentality, let’s earn money first and think about details later?
He also says for example that ‘It was an outside job because no Slovenian would be capable of this level of hacking’ – as a Slovenian professional programmer I’m just a tiny bit insulted at this as I’ve met some crazily competent Slovenian professionals in my career and while I don’t know that any of them are actually malicious hackers, I feel that that statement speaks loads about his ego.
Finally, he laments about ‘his human rights being violated’ because he wasn’t allowed to own the company himself due to his criminal past (his father owns it officially). I don’t know the law enough to go into whether he should have that right after serving his due in prison or not, but invoking ‘human rights’ seems way too theatrical at that point, especially since many people just lost a lot of money through your fault – what about their ‘human rights’?
In any case, the guy did not come off as ready to own up to his mistakes or sincerely learning from them. I would keep a healthy distance from him in any matter having to do with security.
Very good points
Does that mean that nicehash is a potential virus/malware that already infected millions of computers all around the world? I’m getting really worried.
HIGHLY unlikely, was most likely a spear phishing campaign that got them access, just an educated guess. The weakest link generally tends to be a human and a single point of entry from an uneducated person with access to the lan in anyway dramatically increases the attack surface and the chances that they’ll pivot through the network.
I’m still not seeing a legitimate (not in the legal sense, but in the practical sense) need or use for bitcoin. As this case highlights they seem less secure than our current banking system which at least has some protection for consumers (varies according to where you are I guess).
While it is undoubtedly an innovative and cool piece of tech, its use so far seems to be for speculation (read, gambling) and illicit purchases under the cover of legitimate (in the legal sense) purchasing which would probably be better served using normal currency.
Maybe I’m missing something?
I’m on the fence with you. I find it odd that a future currency doesn’t have any safety measures against theft. We have a problem with theft with current physical money. It’s just odd that the creators of each currency doesn’t have a method to track it’s currency.
It’s great how it works now, but it needs to safeguard from theft before it really becomes mainstream, even if they decrease the transfer costs.
You are not relying on a third party and can decide exactly how much to send without opening the door to your whole account.
For merchants it also eliminates the risk of charge backs associate with credit card payments.
Centralising data is a massive security risk, nice hash was a centralised service hence why it was able to be hacked.
So the flaw of the decentralised currency is when it has to go through a trusted third party very ironic don’t you think!
I think 99% of the use is legitimate albeit for speculation, with the $ still being number 1 for all illicit purchases 😉
Is cash better? Sure, but it’s easily stolen from anyone carrying it or their hiding places. And the value of government cash can rapidly decline, as we see in Venezuela and much of the third world.
Or asset forfeiture, simply by traveling through the wrong county with a bunch of cash. (Really, look it up).
Are banks better? Scenario #1: Sure, but they’re backed in government currency and governments sometimes collapse. (Don’t laugh. Look at Venezuela; they had food until recently).
Scenario #2: Good luck hiring a legal defense when your government confiscates your bank accounts over a tax “misunderstanding.” It happens, so don’t scoff.
Is gold better? Sure, a thief finds your stash. Or some environmental regulation is deleted and it’s cheaper to mine for gold. Or a new source is found in some third world country with cheap labor.
Having crypto-currency in an imaginary wallet is clearly a risky way to handle some of your wealth. But so is having a box of cash in your bedroom, all your money in a bank, or a few gold coins in your freezer.
The only safe thing is to diversify your wealth, spreading it in more than one kind of currency and precious objects. Maybe invest in a few Shekels, Pounds, and a little gold, for now. You never know.
i dont undestood? im using avast and never any virus got in to my computer. my passwords never ever been compromised.and my visrus detector always gives alert to me,so what other computer users do different then me`?
Do you have $50 million worth of Bitcoin on your computer? You might be a bit more of a target in that case.
“In December 2013, NiceHash CTO Matjaž Škorjanc was sentenced to four years, ten months in prison”.
I don’t math well, but if you carry the one and square the root, my math says that he should’ve still been in prison at the time of the theft. So prison from January 2014 to October 2018. It’s not October 2018 yet.
This bullsh”t about “early release for good behavior” is nonsense.
If you get 4 years and 10 months, YOU SHOULD DO 4 YEARS AND 10 MONTHS.
I would solicit the bitcoin from the Appeals Board of the prison this adidas track suit wearing h4x0r was released from.
Until a system of incarceration is developed in which prisoners can have a personal jailor and receive gold stickers, chocolate ice cream, and fluffy dolls as rewards for good behavior, the best option remains an early release program.
🙂
Ah, so he’s still on some kind of parole basically, I missed that – well that makes the ‘my human rights were violated, booohoo’ part even more pathetic.
>If you get 4 years and 10 months, YOU SHOULD DO 4 YEARS AND 10 MONTHS.
Why? Different countries have different approaches on this, why is yours the best?
There’s so much scamming and theft right now in the cryptocurrency space that it’s almost comical. I mine crypto currencies with hardware and there’s such high demand that we are literally paying for stuff we won’t even get for 4-5 months out. So then there’s space for new technology which promises to do that same that may or may not ever materialize with minimum orders of 5-10 at $1500-$1800 paid in advance. SO then you’ve got that scam (or potential for it) and you’ve got people claiming to have hardware, charging markups ($500-$2000) and they just never ship. I’ve started ordering single units from the ones that seem legit just to test the water and not take on too much risk. The crypto space is like the wild west on all sides.
@Brooke: Yep, almost ALL are scams except for the manufacturers like Bitmain, Pinidea, etc. There seems to be non-ending amounts of websites plastered on the internet offering mining rigs at really good prices accepting only crypto’s and would bet 100% are just scams! Even off places like ebay you have both parties trying to scam each other if paying with or without crypto’s. One party tries to pay using a stolen account or if they pay legally they use the miner for a month or two and then say it was defective and try to return for a refund so they get mine for free while the return is best.
Then Nicehash gets hacked with what they initially called a very sophisticated attack. Turns out its most likely an inside job. Brilliant!
BTW: I like baikalminer.com and their new algo’s! Lots of scam sites already offering their miner so be sure to only buy direct from the manufacturer.
“So the flaw of the decentralised currency is when it has to go through a trusted third party very ironic don’t you think!”
Irony? Nah, that’s just called “stalking the watering hole”
Everyone has to bring their money to the market sometime.
Don’t invest if you are not decided to buy bitcoin.