The U.S. Justice Department on Tuesday unsealed the guilty pleas of two men first identified in January 2017 by KrebsOnSecurity as the likely co-authors of Mirai, a malware strain that remotely enslaves so-called “Internet of Things” devices such as security cameras, routers, and digital video recorders for use in large scale attacks designed to knock Web sites and entire networks offline (including multiple major attacks against this site).
Entering guilty pleas for their roles in developing and using Mirai are 21-year-old Paras Jha from Fanwood, N.J. and Josiah White, 20, from Washington, Pennsylvania.
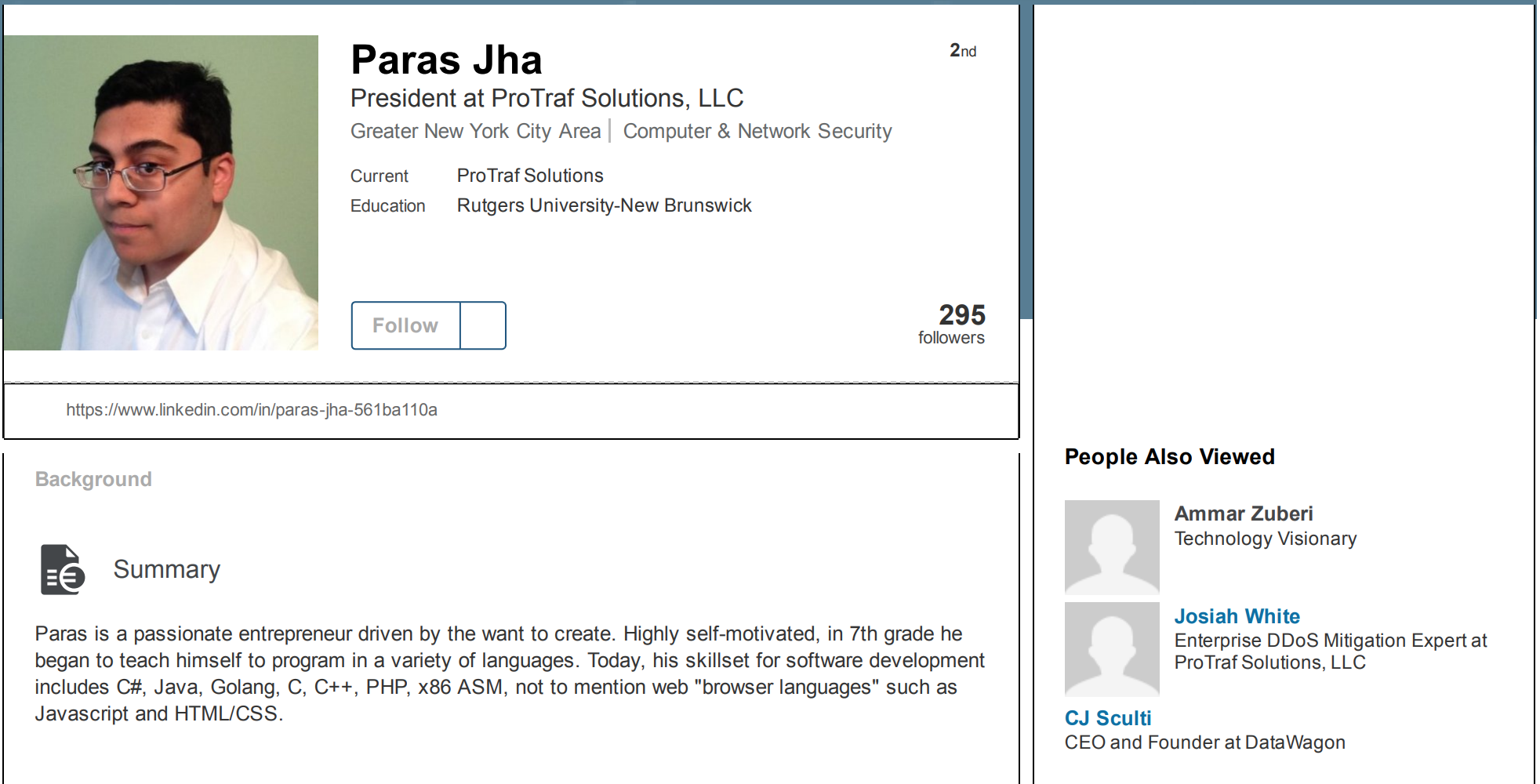
Jha and White were co-founders of Protraf Solutions LLC, a company that specialized in mitigating large-scale DDoS attacks. Like firemen getting paid to put out the fires they started, Jha and White would target organizations with DDoS attacks and then either extort them for money to call off the attacks, or try to sell those companies services they claimed could uniquely help fend off the attacks.
CLICK FRAUD BOTNET
In addition, the Mirai co-creators pleaded guilty to charges of using their botnet to conduct click fraud — a form of online advertising fraud that will cost Internet advertisers more than $16 billion this year, according to estimates from ad verification company Adloox.
The plea agreements state that Jha, White and another person who also pleaded guilty to click fraud conspiracy charges — a 21-year-old from Metairie, Louisiana named Dalton Norman — leased access to their botnet for the purposes of earning fraudulent advertising revenue through click fraud activity and renting out their botnet to other cybercriminals.
As part of this scheme, victim devices were used to transmit high volumes of requests to view web addresses associated with affiliate advertising content. Because the victim activity resembled legitimate views of these websites, the activity generated fraudulent profits through the sites hosting the advertising content, at the expense of online advertising companies.
Jha and his co-conspirators admitted receiving as part of the click fraud scheme approximately two hundred bitcoin, valued on January 29, 2017 at over $180,000.
Prosecutors say Norman personally earned over 30 bitcoin, valued on January 29, 2017 at approximately $27,000. The documents show that Norman helped Jha and White discover new, previously unknown vulnerabilities in IoT devices that could be used to beef up their Mirai botnet, which at its height grew to more than 300,000 hacked devices.
MASSIVE ATTACKS
The Mirai malware is responsible for coordinating some of the largest and most disruptive online attacks the Internet has ever witnessed. The biggest and first to gain widespread media attention began on Sept. 20, 2016, when KrebsOnSecurity came under a sustained distributed denial-of-service attack from more than 175,000 IoT devices (the size estimates come from this Usenix paper (PDF) on the Mirai botnet evolution).
That September 2016 digital siege maxed out at 620 Gbps, almost twice the size of the next-largest attack that Akamai — my DDoS mitigation provider at the time — had ever seen.
The attack continued for several days, prompting Akamai to force my site off of their network (they were providing the service pro bono, and the attack was starting to cause real problems for their paying customers). For several frustrating days this Web site went dark, until it was brought under the auspices of Google’s Project Shield, a program that protects journalists, dissidents and others who might face withering DDoS attacks and other forms of digital censorship because of their publications.
At the end of September 2016, just days after the attack on this site, the authors of Mirai — who collectively used the nickname “Anna Senpai” — released the source code for their botnet. Within days of its release there were multiple Mirai botnets all competing for the same pool of vulnerable IoT devices.
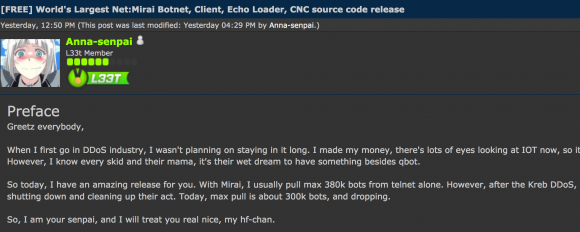
The Hackforums post that includes links to the Mirai source code.
Some of those Mirai botnets grew quite large and were used to launch hugely damaging attacks, including the Oct. 21, 2016 assault against Internet infrastructure firm Dyn that disrupted Twitter, Netflix, Reddit and a host of other sites for much of that day.
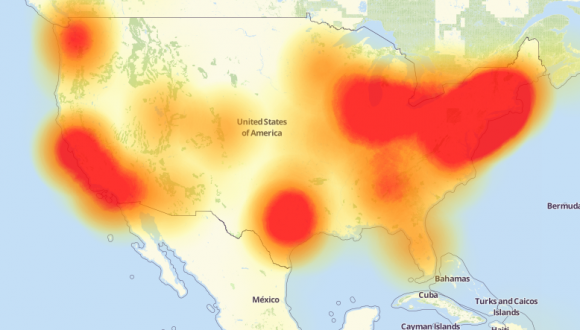
A depiction of the outages caused by the Mirai attacks on Dyn, an Internet infrastructure company. Source: Downdetector.com.
The leak of the Mirai source code led to the creation of dozens of copycat Mirai botnets, all of which were competing to commandeer the same finite number of vulnerable IoT devices. One particularly disruptive Mirai variant was used in extortion attacks against a number of banks and Internet service providers in the United Kingdom and Germany.
In July 2017, KrebsOnSecurity published a story following digital clues that pointed to a U.K. man named Daniel Kaye as the apparent perpetrator of those Mirai attacks. Kaye, who went by the hacker nickname “Bestbuy,” was found guilty in Germany of launching failed Mirai attacks that nevertheless knocked out Internet service for almost a million Deutsche Telekom customers, for which he was given a suspended sentence. Kaye is now on trial in the U.K. for allegedly extorting banks in exchange for calling off targeted DDoS attacks against them.
Not long after the Mirai source code was leaked, I began scouring cybercrime forums and interviewing people to see if there were any clues that might point to the real-life identities of Mirai’s creators.
On Jan 18, 2017, KrebsOnSecurity published the results of that four-month inquiry, Who is Anna Senpai, the Mirai Worm Author? The story is easily the longest in this site’s history, and it cited a bounty of clues pointing back to Jha and White — two of the men whose guilty pleas were announced today.
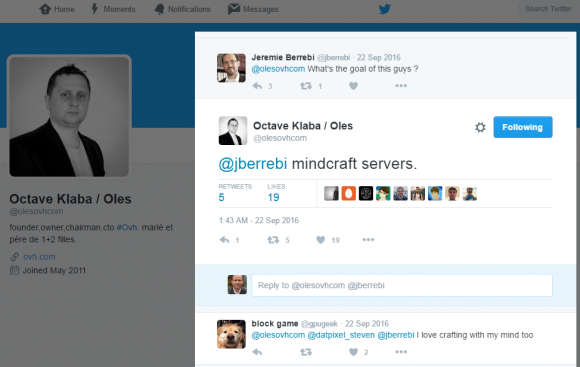
A tweet from the founder and CTO of French hosting firm OVH, stating the intended target of the Sept. 2016 Mirai DDoS on his company.
According to my reporting, Jha and White primarily used their botnet to target online gaming servers — particularly those tied to the hugely popular game Minecraft. Around the same time as the attack on my site, French hosting provider OVH was hit with a much larger attack from the same Mirai botnet (see image above), and the CTO of OVH confirmed that the target of that attack was a Minecraft server hosted on his company’s network.
My January 2017 investigation also cited evidence and quotes from associates of Jha who said they suspected he was responsible for a series of DDoS attacks against Rutgers University: During the same year that Jha began studying at the university for a bachelor’s degree in computer science, the school’s servers came under repeated, massive attacks from Mirai.
With each DDoS against Rutgers, the attacker — using the nicknames “og_richard_stallman,” “exfocus” and “ogexfocus,” — would taunt the university in online posts and media interviews, encouraging the school to spend the money to purchase some kind of DDoS mitigation service.
It remains unclear if Jha (and possibly others) may face separate charges in New Jersey related to his apparent Mirai attacks on Rutgers. According to a sparsely-detailed press release issued Tuesday afternoon, the Justice Department is slated to hold a media conference at 2 p.m. today with officials from Alaska (where these cases originate) to “discuss significant cybercrime cases.”
Update: 11:43 a.m. ET: The New Jersey Star Ledger just published a story confirming that Jha also has pleaded guilty to the Rutgers DDoS attacks, as part of a separate case lodged by prosecutors in New Jersey.
PAYBACK
Under the terms of his guilty plea in the click fraud conspiracy, Jha agreed to give up 13 bitcoin, which at current market value of bitcoin (~$17,000 apiece) is nearly USD $225,000.
Jha will also waive all rights to appeal the conviction and whatever sentence gets imposed as a result of the plea. For the click fraud conspiracy charges, Jha, White and Norman each face up to five years in prison and a $250,000 fine.
In connection with their roles in creating and ultimately unleashing the Mirai botnet code, Jha and White each pleaded guilty to one count of conspiracy to violate 18 U.S.C. 1030(a)(5)(A). That is, to “causing intentional damage to a protected computer, to knowingly causing the transmission of a program, code, or command to a computer with the intention of impairing without authorization the integrity or availability of data, a program, system, or information.”
For the conspiracy charges related to their authorship and use of Mirai, Jha and White likewise face up to five years in prison, a $250,000 fine, and three years of supervised release.
This is a developing story. Check back later in the day for updates from the DOJ press conference, and later in the week for a follow-up piece on some of the lesser-known details of these investigations.
The Justice Department unsealed the documents related to these cases late in the day on Tuesday. Here they are:
Jha click fraud complaint (PDF)
Jha click fraud plea (PDF)
Jha DDoS/Mirai complaint (PDF)
Jha DDoS/Mirai plea (PDF)
White DDoS complaint (PDF)
White DDoS/Mirai Plea (PDF)
Norman click fraud complaint (PDF)
Norman click fraud plea (PDF)




Brian,
Great story. We shall see what sentences are imposed.
In the 2nd paragraph of PAYBACK, did you mean “appeal the conviction” rather than “appear”?
Awesome post. One typo though:
Jha will also waive all rights to appear the conviction
s/appear/appeal
plead guilty`? well why not if the sentences are soft.
sometimes is better to plea rather then wait for trial forever.
do your jail time,and after just forget and live your life.
FUCK YES! Throw them in jail each for 10 years. Do not let them off easy. Fuck these people.
its not murder,or violant crime its still white collar.
i guess max 5 years.
who not if they earn millions of dollars,well the few years int the jail is just the price they go to pay.-thats it
Their criminal proceedings are just the beginning.
Their actions caused by Mirai and releasing the source code has caused millions of dollars of downtime, IT costs, etc.
They need to have the book thrown at them.
Jha, could become Head Dead of Computer Science,
at any correctional institution; thus providing job skills
to his fellow inmates.
Bachelor of DDS Science
Another good read !
Nothing too much happens with some basic restrictions, fines, etc. Nice to read about “they got’m” and so on. BUT:
Harsh jail sentences, and ‘taking’ of property ‘in rem’ (which I don’t actually like at all), etc., all based on real damage amounts, and tripled…and all is widely announced in all sorts of media, is probably the only way that there is some real deterrence against the perps; …Unless some politician well-up the government feeding chain gets hit with major problems from these nasty criminals.
Maybe we’ll see a turn-around. I’m not counting on it.
The “Who is Anna-Senpai, the Mirai Worm Author?” article is by far my favorite article you’ve written on this site. This is a great follow up and a look forward to reading more details as they come to light. Thanks for sharing.
Thank you! Wired just ran a piece that has some good background reporting on the FBI investigators in this case and the hoops they had to jump through.
https://www.wired.com/story/mirai-botnet-minecraft-scam-brought-down-the-internet/
Congratulations on the mentions in that Wired article. I know its nothing new for you to write for or to be mentioned in high-profile publications, but its always fun and interesting to see your work in the limelight.
PS: Your IMDB profile needs updated: http://www.imdb.com/name/nm6920900/
I know I’ve seen you as a guest in at least one show I’ve streamed. I can’t recall the name of the show though. Was it “Cybercrimes”, “Dark Net”, something else? I’m sure there are at least a couple of documentaries, interviews, etc that you’ve been in that are missing from IMDB. 🙂
Hrm. There are several, but not all are public. E.g, Viceland recently interviewed me twice for their Cyberwar series; one about Russian hackers and another about Mirai. But I think those are behind a subscription wall of some kind.
Here’s the IoT/Mirai episode (again, you have to log in via your broadband provider:
https://www.viceland.com/en_us/video/cyberwar-the-internet-of-things-apocalypse/595f964eb03021fb47ebb299
There is also
PBS Newshour: https://www.pbs.org/newshour/show/outdated-internet-browser-gateway-cyber-attacks
Cybercrimes with Ben Hammersley, Episode 5 (Stuxnet): https://www.netflix.com/watch/80063652?trackId=14277283&tctx=0%2C4%2C7e2a1cb8-651c-4ac7-95ef-faf3e2bb6cae-10935795
Probably a bunch more I can’t recall right now.
Alaska was mentioned! That never happens!
They always leave us off the map at conferences and competitions…
T_T
Saw this on Fox news at 9 on channel 04. Anchorage
Alaska, Alaska, ALASKA!
… Also, Aloha, Hawaii!
It seems like the gov’t offered this deal with plans to eventually recruit these guys.
NSA perhaps?
They don’t offer jobs to these guys anymore, I believe Albert Gonzalez made some decision makers realize giving sociopaths government jobs is usually going to remembered as a Bad Decision
Are you JOKING?? Nearly ALL who end up in “leadership positions” in American government are sociopaths. They HAVE to be. Our owners DEMAND it. They are the living definitions of the word COWARD. They slavishly (if not mindlessly) truckle to the powerful as vigorously as they demonize and victimise the powerless. And all for their thirty pieces of silver. If that’s not sociopathic, then the term has no useful meaning.
🙂
There are too many sociopaths in government already….
. .. . .. — ….
Brian, this reporting is fantastic work of yours.
Will be interested to see if the punishment is harsh or soft. It never seems to be in between.
Thanks, VB. I have a hard time believing Mr. Jha or any of the defendants will see real time behind bars, although the prosecutors in NJ are really gunning for this kid, it seems.
The investigative article titled “Who is Anna-Senpai, the Mirai Worm Author?” was a fascinating read. I was glued to it for its entirety so much so that it has gotten me inspired to pursue the subject on a professional level.
And to think of the impact that article has had on this whole investigation is a fair retribution for the attack on this website.
Good job Brian.
I hope they’re not getting charged simply for the creation of Mirai. Creating software should never be a crime. If you go down that road you open the door for companies to go after security researchers for exposing their incompetence.
They aren’t being charged for mere software creation. Read the actual documents before you get all indignant. They’re being charged for massive damage done to Rutgers, infecting hundreds of thousands of machines they don’t own, defrauding advertisers for many thousands of dollars, and so on and so on.
Did you bother to read the court documents?
“The object of the unlawful conspiracy was to infect computing devices with
malware for the purpose of enlisting those devices into a botnet that could be used to engage
in criminal activity, including advertising fraud, and particularly clickfraud. “
The possible sentences seem light considering what they did, especially since they probably won’t get the whole five years.
Curious about this passing comment:
“firemen getting paid to put out the fires they started”
As an anthropologist who started working in cybersecurity a few months ago, much of the work in the field sounds like firefighting to me. However, this specific analogy to pyromaniac firefighters fell on deaf ears when talking with colleagues in the US. Still, the fact that attackers and defenders tend to have very similar characteristics is well understood.
Are the connections between cybersecurity and firefighting ever discussed in your circles?
Thanks!
So, I spend a lot of time fighting fires in IT, and I do talk about it that way.
While working on software w/ security vulnerabilities, we called fixing them “fire drills”.
I don’t think we talk about fire fighters. And in general I don’t think software developers do the other parts.
As a general rule, if you contribute to a software project, you won’t get a bounty for spotting the bug you created (or reviewed). And if you were found to have intentionally created a bug, your reputation would be ruined.* And further, there are more than enough projects with security bounties available for someone who is involved in bug/bounty hunting.
* Ken Thompson being the exception: “Reflections On Trusting Trust” http://web.archive.org/web/20010410053444/http://cm.bell-labs.com/who/ken/trust.html
What, it wasn’t Russians?
He had to give up 13 Bitcoin as part of the plea deal, but had earned about 200 Bitcoin from his illegal activity? Granted, his illegal profits were split 3 ways or so but that still sounds like he’ll leave prison with hundreds of thousands of dollars in ill-gotten gains, especially with the recent spike in Bitcoin prices. What gives?
By the time he gets out, bitcoin will have crashed.
I think with his plea deal there’s a 250k$ fine that will also shrink the ill-gotten gain.
That face needs some serious deep tissue massage.
I hope he gets the attention he needs in prison.
“According to my reporting…” – I think you reach a new status when you are able to credibly attribute yourself. Well done, as always.
This Crypto-Currency business is as dark and seedy as it gets, I love it 🙂 Unfortunately shady scum like Baby Kim, ISIS, Politicians, and Trial Lawyers like it too 🙁
https://itsecurity-tips.blogspot.com/
You rock, Brain! An investigative reporting in the truest sense of the word. Read the Wired article, fascinating…but you dug deep and created the cracks.
By the way, isn’t the “pyro/fireman” metaphor just a slick way of saying “Extortion racket” – one of the oldest games in the neighborhood. I suspect the prosecutors in Jersey are quite familiar with the nuances of that game.
So happy these dungeon-dwellers have finally been convicted. Best thing I’ve read today.
Excellent. Let’s hope they get 10 years
… (better) 10 years for each server or single IOT device attacked. This was very deliberate and monetized.