Not long ago, phishing attacks were fairly easy for the average Internet user to spot: Full of grammatical and spelling errors, and linking to phony bank or email logins at unencrypted (http:// vs. https://) Web pages. Increasingly, however, phishers are upping their game, polishing their copy and hosting scam pages over https:// connections — complete with the green lock icon in the browser address bar to make the fake sites appear more legitimate.
According to stats released this week by anti-phishing firm PhishLabs, nearly 25 percent of all phishing sites in the third quarter of this year were hosted on HTTPS domains — almost double the percentage seen in the previous quarter.
“A year ago, less than three percent of phish were hosted on websites using SSL certificates,” wrote Crane Hassold, the company’s threat intelligence manager. “Two years ago, this figure was less than one percent.”
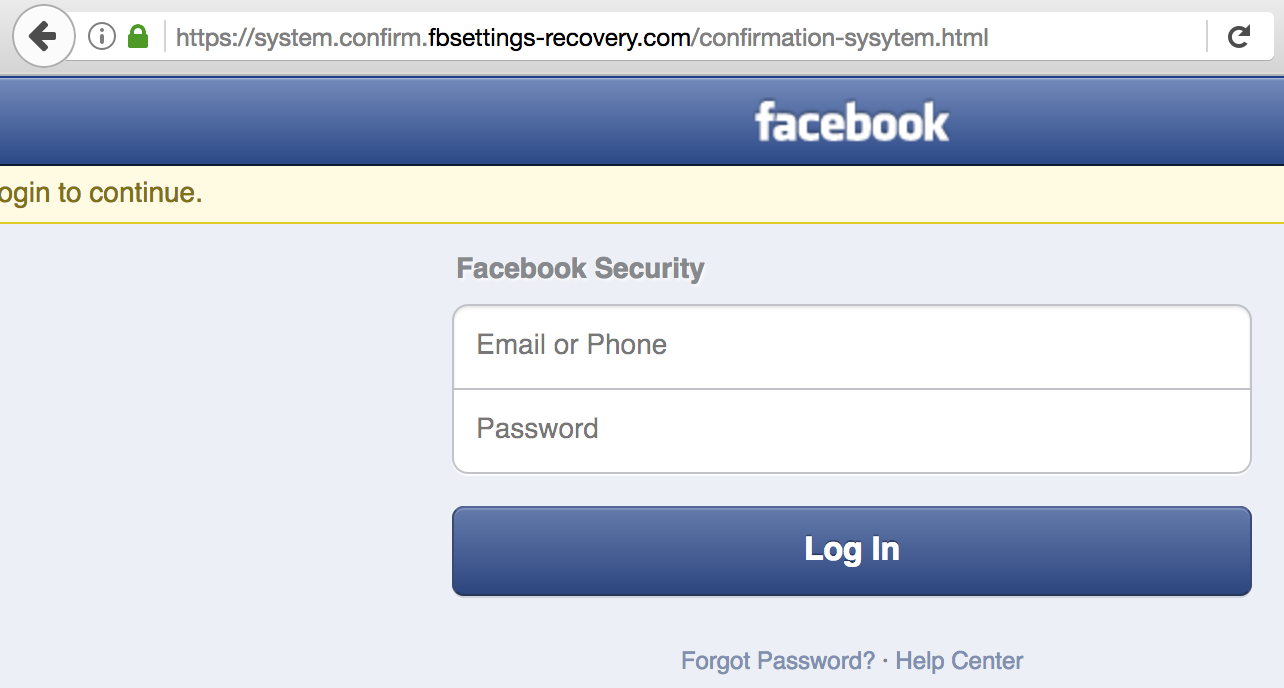
A currently live Facebook phishing page that uses https.
As shown in the examples above (which KrebsOnSecurity found in just a few minutes of searching via phish site reporting service Phishtank.com), the most successful phishing sites tend to include not only their own SSL certificates but also a portion of the phished domain in the fake address.
Why are phishers more aggressively adopting HTTPS Web sites? Traditionally, many phishing pages are hosted on hacked, legitimate Web sites, in which case the attackers can leverage both the site’s good reputation and its SSL certificate.
Yet this, too, is changing, says PhishLabs’ Hassold.
“An analysis of Q3 HTTPS phishing attacks against PayPal and Apple, the two primary targets of these attacks, indicates that nearly three-quarters of HTTPS phishing sites targeting them were hosted on maliciously-registered domains rather than compromised websites, which is substantially higher than the overall global rate,” he wrote. “Based on data from 2016, slightly less than half of all phishing sites were hosted on domains registered by a threat actor.”
Hassold posits that more phishers are moving to HTTPS because it helps increase the likelihood that users will trust that the site is legitimate. After all, your average Internet user has been taught for years to simply “look for the lock icon” in the browser address bar as assurance that a site is safe.
Perhaps this once was useful advice, but if so its reliability has waned over the years. In November, PhishLabs conducted a poll to see how many people actually knew the meaning of the green padlock that is associated with HTTPS websites.
“More than 80% of the respondents believed the green lock indicated that a website was either legitimate and/or safe, neither of which is true,” he wrote.
What the green lock icon indicates is that the communication between your browser and the Web site in question is encrypted; it does little to ensure that you really are communicating with the site you believe you are visiting.
At a higher level, another reason phishers are more broadly adopting HTTPS is because more sites in general are using encryption: According to Let’s Encrypt, 65% of web pages loaded by Firefox in November used HTTPS, compared to 45% at the end of 2016.
Also, phishers no longer need to cough up a nominal fee each time they wish to obtain a new SSL certificate. Indeed, Let’s Encrypt now gives them away for free.
The major Web browser makers all work diligently to index and block known phishing sites, but you can’t count on the browser to save you:
So what can you do to make sure you’re not the next phishing victim?
Don’t take the bait: Most phishing attacks try to convince you that you need to act quickly to avoid some kind of loss, cost or pain, usually by clicking a link and “verifying” your account information, user name, password, etc. at a fake site. Emails that emphasize urgency should be always considered extremely suspect, and under no circumstances should you do anything suggested in the email.
Phishers count on spooking people into acting rashly because they know their scam sites have a finite lifetime; they may be shuttered at any moment. The best approach is to bookmark the sites that store your sensitive information; that way, if you receive an urgent communication that you’re unsure about, you can visit the site in question manually and log in that way. In general, it’s a bad idea to click on links in email.
Links Lie: You’re a sucker if you take links at face value. For example, this might look like a link to Bank of America, but I assure you it is not. To get an idea of where a link goes, hover over it with your mouse and then look in the bottom left corner of the browser window.
Yet, even this information often tells only part of the story, and some links can be trickier to decipher. For instance, many banks like to send links that include ridiculously long URLs which stretch far beyond the browser’s ability to show the entire thing when you hover over the link.
The most important part of a link is the “root” domain. To find that, look for the first slash (/) after the “http://” part, and then work backwards through the link until you reach the second dot; the part immediately to the right is the real domain to which that link will take you.
“From” Fields can be forged: Just because the message says in the “From:” field that it was sent by your bank doesn’t mean that it’s true. This information can be and frequently is forged.
If you want to discover who (or what) sent a message, you’ll need to examine the email’s “headers,” important data included in all email. The headers contain a lot of information that can be overwhelming for the untrained eye, so they are often hidden by your email client or service provider, each of which may have different methods for letting users view or enable headers.
Describing succinctly how to read email headers with an eye toward thwarting spammers would require a separate tutorial, so I will link to a decent one already written at About.com. Just know that taking the time to learn how to read headers is a useful skill that is well worth the effort.
Keep in mind that phishing can take many forms: Why steal one set of login credentials for a single brand when you can steal them all? Increasingly, attackers are opting for approaches that allow them to install a password-snarfing Trojan that steals all of the sensitive data on victim PCs.
So be careful about clicking links, and don’t open attachments in emails you weren’t expecting, even if they appear to come from someone you know. Send a note back to the sender to verify the contents and that they really meant to send it. This step can be a pain, but I’m a stickler for it; I’ve been known to lecture people who send me press releases and other items as unrequested attachments.
If you didn’t go looking for it, don’t install it: Password stealing malware doesn’t only come via email; quite often, it is distributed as a Facebook video that claims you need a special “codec” to view the embedded content. There are tons of variations of this scam. The point to remember is: If it wasn’t your idea to install something from the get-go, don’t do it.
Lay traps: When you’ve mastered the basics above, consider setting traps for phishers, scammers and unscrupulous marketers. Some email providers — most notably Gmail — make this especially easy.
When you sign up at a site that requires an email address, think of a word or phrase that represents that site for you, and then add that with a “+” sign just to the left of the “@” sign in your email address. For example, if I were signing up at example.com, I might give my email address as krebsonsecurity+example@gmail.com. Then, I simply go back to Gmail and create a folder called “Example,” along with a new filter that sends any email addressed to that variation of my address to the Example folder.
That way, if anyone other than the company I gave this custom address to starts spamming or phishing it, that may be a clue that example.com shared my address with others (or that it got hacked!). I should note two caveats here. First, although this functionality is part of the email standard, not all email providers will recognize address variations like these. Also, many commercial Web sites freak out if they see anything other than numerals or letters, and may not permit the inclusion of a “+” sign in the email address field.




So I’m thinking, IF I owned Linked In or FB or Yahoo and someone hacked my business, how much trouble would I be in if I offered a 1 million dollar bounty to have that person dropped off to an FBI office. They can afford it. And wouldn’t that tend to deter half of these nuts or would it more likely make me a bigger target?
“First, although this functionality is part of the email standard, not all email providers will recognize address variations like these. Also, many commercial Web sites freak out if they see anything other than numerals or letters, and may not permit the inclusion of a “+” sign in the email address field.”
It’s been a while since I’ve read the email RFCs, but there’s nothing intrinsically special about a + or a _ in an email address. MTAs such as Postfix allows the mail system to be configured how to handle the + (or -, which I use) if they exist (mail_delimiter in postfix). There’s nothing compelling any mail system to honor them in any special way. Either they’re specifically configured to as in the above, or the + is treated no different than any other ASCII character in the email address.
The + sign is a legacy space character in URL encoding. That’s probably why it bugs webmail. If you want to experiment sometime, try changing “%20″s to “+”s, shouldn’t have any problem reloading the same page.
Brian’s, “Also, many commercial Web sites freak out if they see anything other than numerals or letters, and may not permit the inclusion of a “+” sign in the email address field.”
rsmith’s, …”webmail”…
Not only website and webmail, I’ve had commercial companies that are unable to send from their “non-web-based” email systems to email addresses with a “.” before the “@”. Yet, the creation of a user profile on the website accepted “.” before the “@”.
There are many email implementations, especially in web input forms, that do not adhere to the email standard.
Most of the time, they reject perfectly valid email addresses because of the inclusion of the special characters + or -. Even though the standard allows the characters, the web page implementation won’t allow them.
It’s amazing how difficult it is to explain that to a given company (and equally difficult to get them to do it right).
Childish, If we have the ability to use private, public keys. Why we are still using passwords and haven’t drop them all together to start working with authentication based in encoded challenge/responses thus avoiding all the fuss about phishing as there would be no point on phishing an public key encoded seed.
Using a “+” in an email looks like a good idea, and I started using it with gmail once I found out about it.
However, not all websites’ signup pages honour the legality of the +, arguing that it isn’t valid (it isn’t valid to the right of the @, but it is valid to the left) ,and will deny that email address during registration.
Even worse, some allow you to register and successfully send you the confirmation email that you click on, but then you are unable to log on to your validated account because the login page validates emails differently to the signup page.
I’m going through this hell with Virgin Media at the moment. I can request a password reset with their system, click on the link and change the password, but it still fails to log me in afterwards 🙁
Nice idea in theory, but I don’t bother with it anymore due to the amount of hassle I have with various organisations with fancy-looking but poorly implemented systems.
I now have my own domain, with postfix running on my own server. I can use any value I like to the left of the , so krebsonsecurity@mydomain.com, equifax@mydomain.com etc. (obviously not actually mydomain.com, but you get the idea), using a different email for every registration I sign up for.
Gmail is terrible for privacy anyway. Google reads all your email contents and then creates custom ads. Remember if a product is free, then YOU are the product. Some paid email providers, like Fastmail, let you have unlimited aliases and then you can do the same as you do with your custom domain, create a new email address for each sign-up. Merchants have canceled orders or required extra verification because of this. The only reason I can think of is that they are using some form of meta-data analysis from Google analytics or Facebook to verify a person, kind of like an Equifax for email. Since I block all tracking and use unique emails, they can’t verify so easily. Which is exactly what I want. I don’t want to be tracked. My data belongs to me. And if they cancel my order, then I will just go to another store than honors my privacy.
“…like Fastmail, let you have unlimited aliases…” And, gmx.com, which I use.
“That way, if anyone other than the company I gave this custom address to starts spamming…” The use of “+” isn’t an entirely throwaway email address if the spammer removes the identifier after the “+” to then have a “root” email address; I prefer and recommend throwaway alias email providers against spammers.
Another option for aliases is Abine’s Blur add-on. It makes it pretty easy to create a temporary alias and the destroy it after it is no longer needed. They offer a free version of their service.
Unfortunately the add-on no longer works properly with Firefox ESR but it’s fine with Quantum. AFAIK it also works on Chrome.
I get the absolute worst phishing emails. As in retarded, not dangerous.
I can’t imagine how fully-functional adults in any internet-having country are so bad at their chosen scam. If they can’t even manage 2 lines of computable English language why are they targeting English speakers at all? It’s madness.
The government should honeypot-phish all known emails of importance and keep a score on your clicking habits. If you fall for it, you’re branded. Then you have to go to an 8 hour class like driver’s ed for email. Something draconian like that ought to help, nothing else has a chance. People are allowed to be dumb.
The argument used to be that phishers were deliberately looking for the thick and the gullible. That might be changing.
Actually, often the bad grammar and spelling are intentional. They don’t want to bother dealing with “smart” people, so they use it to weed out cautious folks looking out for stuff like this.
Actually, often the bad grammar and spelling are intentional. They don’t want to bother dealing with “smart” people, so they use it to weed out cautious folks looking out for stuff like this.
The maroons at Mozilla haven’t done us any favors when they made everything in the address bar gray, except the primary domain.
Also, I only do plain text in my MUI. Any company (that I care to correspond with) that sends me a HTML email gets a nastygram in reply. If they refuse to comply with my plain text request, I find another company to do business with.
That’s the point though. The subdomains are used as a way to confuse users into believing that it really is google[.]com when in fact it’s some thing not at all owned by Google. By highlighting only the primary domain, the goal is to focus the user’s attention on the real domain. It’s not perfect, but I’d argue that it at least helps in the average case for this scenario.
I’m perfectly ok with parsing URL’s myself. I don’t need any help from the browser.
btw, it also obscures the https, which is just as important to me.
Sure, they put that pretty, green padlock up there… If I choose to believe it can never be spoofed. (I don’t)
I could probably fix it temporarily, with a userchrome.css. It’s a losing battle though. The code monkeys at Mozilla, with their silly every 30 minutes revision schedule, screw it up faster than I can put it back the way I want it.
Your efforts are misguided. HTML is not the problem, and avoiding HTML messages will do little to avert the risk. Plaintext emails can still contain links and attachments.
Tell that to the millions of OutaLuck users that get pwned every year by embedded and obscured URL’s and attachments.
An email is communication using written words, not an art project.
I don’t need, or want pretty colors or fancy fonts and formats when using textual communication. It contributes nothing to the efficiency of the medium.
Now, get off my lawn! 😉
I am among the 80% that thought the lock meant I was at the website I thought I was at. I had never heard of the + sign. And more. Thank you Brian, again, for the umpteenth time.
To those commenters who think people are dumb, please, many of us are smart at things you maybe are not good at. The thing that makes KrebsonSecurity so popular and so readable is he never talks down to those of us who are vulnerable to the evil-doers’ schemes, and he manages in his columns to interest both the very experienced users and the vulnerable ones who just want to send emails and get their banking done, and that is quite a feat.
This is a great point. While I suspect many of Brian’s readers are knowledgeable with technology and security, they may not be talented in other areas (e.g., auto mechanic, medicine). We all have our strengths and I appreciate Brian’s straightforward explanations.
Totally agree with your statements @Judy. Blaming people who don’t follow the pulse of security for not understanding evolving trends is absolutely a problem. I taught an introductory security course this fall at my undergrad and very much attempted to address this kind of behavior. I believe the onus is on the security industry to make things more usable for end users, not to shame users for missing the distinction between “safe” and encrypted.
I run a couple of VPS servers rented in the Netherlands. These lines are all it takes to make the site https:
listen 443 ssl;
ssl_certificate /etc/letsencrypt/live/inwtx.net/cert.pem;
ssl_certificate_key /etc/letsencrypt/live/inwtx.net/privkey.pem;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers
‘ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:D$
if ($ssl_protocol = “”) {
rewrite ^ https://$server_name$request_uri? permanent;
}
My site uses a Let’s Encrypt cert. There is no personal validation as to who I am. This also goes for a most purchased cert – no validation.
@Judy
Yes I second those thoughts!
@ everyone else
I’m a bit of a geek as in security things interest me, but I’m not an IT professional. I’m kicking around the idea of getting into it(Comp Tia Cert maybe?) but I’m just not sure I’m smart enough. I come here & go to Bruce Schneier’s site almost everyday & I try to keep up with “Security Now”.
Anyway, I knew the lock meant it was encrypted, but I hadn’t considered the idea of the “bad guys” using it too!
Thanks for the tips Brian!
Thank you Brian for a most valuable tutorial. The trouble you took to write it should save more serious trouble for many.
What about clickable things that a mouse hover wouldn’t reveal? Say, a button with a script.
downside in using “+” is it makes it’s not as easy to keep up with sites like haveibeenpwned.com to monitor your email being leaked. Any suggestions there? or will people just need to pick one option over the other?
You can ask troy to add that feature: https://haveibeenpwned.uservoice.com/forums/275398-general/suggestions/6774229-enable-search-and-notifications-for-email-addresse
If you have your own domain, haveibeenpwned.com supports proving you own the domain and being notified as a wildcard.
What’s the best way to hover over a link on a mobile device?
not familiar with Android, but for iOS, long tap on link until menu pops up giving you options to ‘open’, ‘share’, etc. the full URL will be displayed there. Gets harder to check if there’s redirection in the link. Can try sites like unfurlr.com to see where the link ends up
Often you can hold your finger on the link and it will pop a screen on your device that will then show the link or allow you to copy the link so that you can analyze it in a document/note.
Another reason is that web browsers are now starting to display “not secure” on any site that has a form. This obviously makes any phishing site that requires data entry a bit less enticing to users. It’s just so easy to fix with a free SSL certificate and using the certbot scripts. You can even automate the renewal before the cert expires. This is great for legitimate sites, but phishers are taking advantage of it.
Since we’re on the topic of the ‘+’ sign and phishing, here’s a trick that not many know.
If you receive an email with a potentially suspicious bit.ly link, you can copy that link, paste it into your browser, append a ‘+’ sign to the end of the link and hit enter.
That will take you to an analysis of the link, what the actual destination is and how many recipients clicked on it.
Wish other URL shortening services would provide the same feature.
As long as you’re copying and pasting links, why not just paste them into VirusTotal’s URL scanning engine?
https://www.virustotal.com/#/home/url
Because as useful as VT is, it only provides a binary (good/evil) result.
I need more analysis than that in terms of final destination, history, click volume…etc
Agree with Tim. VirusTotal is the first place I check. But it should be used as one check among many. It *often* shows a URL as clean when it is not and sometimes shows a URL as suspect when it is legit.
Know your cert fingerprints. Certs can be spoofed but their fingerprints cannot. Compare the fingerprint from Amazon’s legitimate cert to the cert of the suspicious phishing site. If they don’t match, it’s not Amazon’s site
This is totally unreasonable.
The browser / cert industry is moving toward certs with a lifespan of 60 days or less (and dropping).
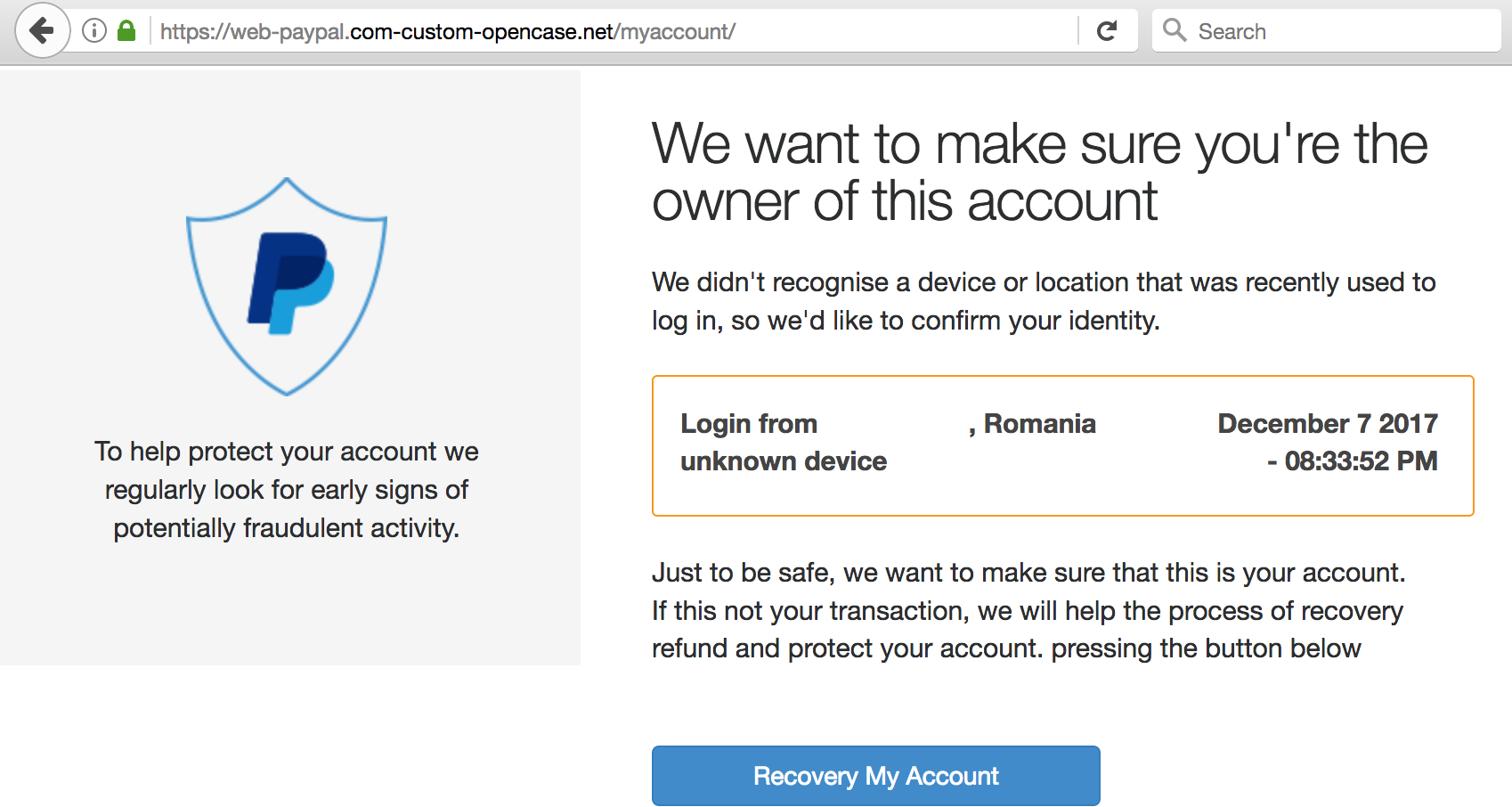
Anyone else see red flags in the first graphic? (“Paypal”)
“If this is not your transaction, we will help the process recovery refund and protect your account. pressing the button below”
Button text: “Recovery My Account”
Help the process recovery refund? Huh?!
The word “pressing” follows a “.”, so I expect it to be capitalized.
*Recovery* my account?!
Michael–totally. Interesting point made by Garyk above:
“Actually, often the bad grammar and spelling are intentional. They don’t want to bother dealing with “smart” people, so they use it to weed out cautious folks looking out for stuff like this.”
This was in response to someone saying they get a lot of phishing emails riddled with spelling errors. I had really never thought of it that way.
I don’t understand how to examine the URL. In the example what is the actual destination?
The example URL in 1st paragraph of “Links Lie” is discomforting to me for a reason not mentioned: it is HTTP, not HTTPS.
Is it mandatory for all phishing sites to have horrible grammar and spelling?
The ultimate phish would be to place a recommended operating system patch onto a whales computer.
that and system is misspelled in the facebook web address.
This should be the only email that I receive from a site: “We have a message for you. Log in to your account to read it.”
I blame a lot of the sites that make their crappy marketing emails actually look like phishing. So it’s no wonder that it’s easy for phishers to make their emails look the same. In an ideal world, sites should never send a link in an email. And users should never click on a link in a email.
I’m sorry; I just don’t understand this part of Brian’s post here:
The most important part of a link is the “root” domain. To find that, look for the first slash (/) after the “http://” part, and then work backwards through the link until you reach the second dot; the part immediately to the right is the real domain to which that link will take you.
Would it be possible to post a graphic example or two of what Brian suggests here?
Here’s an example URL:
https://www.subdomain.example.com/somedir/someotherdir/somepage.html
What brian is saying is find the first slash after the https://, which in the example is between .com and somedir.
Then move left two periods, which in the example is between subdomain and example.
The part immediately to the right of that period is the real domain, which is example.
Another example URL (from the Links Lie section):
http://bankofamerica.com.someotherpagethatsnotbankofamericacombut.youprobablywouldntbeabletotellthatunlessyoucutandpastedthelinksomewhereandreadfromtherighttotheleftfromthefirstslashafterhttpslash.slashandthengo.backwardsfromtheretothesecond.dot/
The real domain is backwardsfromtheretothesecond
James, I can’t make you a picture right now, but I can try to help.
Let’s look at the URL in the (fake) paypal screenshot (used[dot] instead of “.”):
https://web-paypal[dot]com-custom-opencase[dot]net/myaccount/
Part of the URL looks like “paypal.com” –that is part of the trick.
What Krebs is saying:
1) go to the first slash after “https://” — this is the “/” right between “.net” and “myaccount”
2)work backwards to the second dot (right to left) — this takes us to “.” between “web-paypal” (left) and “com-custom-opencase”(right)
3) the part immediately to the right of the dot from (2) is the “root” domain: “com-custom-opencase” — this does not look like paypal to me!
I hope that helps a bit. I think there are exceptions to this rule.. some sites in the UK end “.co.uk” For instance, if you looked at https:\\www.example.co.uk\– following Krebs’ rule, you get the answe “co” but the real root domain is “example.”
In hindsight, it would have been better to provide a link to the wiki that explains what a domain name is, then explain subdomains.
https://en.m.wikipedia.org/wiki/Domain_name
Once you own a domain name, you can create any subdomain name. Typically most websites at least create the subdomain of www.
What would also help would be the use of fonts that don’t make l (el) and I (eye) look similar. That is some sites will use typos that look like the correct word. For instance PayPaI versus PayPal look similar in some fonts. On desktop machines, I force all the fonts to be Google roboto mono. On websites I own, I set the css to use monospace fonts.
Brian, would changing the DNS settings on home routers to the Quad9 DNS servers help consumers reduce the exposure to this type of phishing? Your thoughts on this would be greatly appreciated.
“Most phishing attacks try to convince you that you need to act quickly ”
It’s called “Confirmation and Pretexting”
Another great, informative article. Thanks
criminals never sleep guess criminal lifestyle is expensive to keep it. hookers and luxury cars not cheap,once they sleep money finish.so they must work hard
but my question is,crooks??tell me isit even worted anymore?
The fake link of Bank of America is cute.
I didn’t see the cPanel move to provide all hosted sites with free SSL mentioned, so I will. Auto-SSL is something they came up with and it tries to encrypt ALL subdomains on a server running cPanel with certs from cPanel via Comodo. (But if you call Comodo they may still not be aware of it despite my informing them when I called with a support question).
So a previous “barrier” to using HTTPS has been removed for many sites.
The sheep maybe getting smarter, but the wolves have always been smarter and will maintain their lead over average users.
Unrelated note: Last week I got a call from the infamous “Windows Support Group” who call you and tell you your PC has a virus and malware and even offers “proof”. The story is not new how they convince the unwary to go to a site and hand over remote access to your computer. I never went all the way with them, but I think they are selling legit computer support in a very unlegit way.
Anyway, the news is that in this last call, they sent me to a page on support.microsoft.com and had me use a link there which took me to logmein Rescue. They then gave me a code so they could take over my PC. The scam is not new, but the use of an actual page and link on Microsoft’s site is and could fool many users.