The Internal Revenue Service has been urging tax preparation firms to step up their cybersecurity efforts this year, warning that identity thieves and hackers increasingly are targeting certified public accountants (CPAs) in a bid to siphon oodles of sensitive personal and financial data on taxpayers. This is the story of a CPA in New Jersey whose compromise by malware led to identity theft and phony tax refund requests filed on behalf of his clients.
Last month, KrebsOnSecurity was alerted by security expert Alex Holden of Hold Security about a malware gang that appears to have focused on CPAs. The crooks in this case were using a Web-based keylogger that recorded every keystroke typed on the target’s machine, and periodically uploaded screenshots of whatever was being displayed on the victim’s computer screen at the time.
If you’ve never seen one of these keyloggers in action, viewing their output can be a bit unnerving. This particular malware is not terribly sophisticated, but nevertheless is quite effective. It not only grabs any data the victim submits into Web-based forms, but also captures any typing — including backspaces and typos as we can see in the screenshot below.

The malware records everything its victims type (including backspaces and typos), and frequently takes snapshots of the victim’s computer screen.
Whoever was running this scheme had all victim information uploaded to a site that was protected from data scraping by search engines, but the site itself did not require any form of authentication to view data harvested from victim PCs. Rather, the stolen information was indexed by victim and ordered by day, meaning anyone who knew the right URL could view each day’s keylogging record as one long image file.
Those records suggest that this particular CPA — “John,” a New Jersey professional whose real name will be left out of this story — likely had his computer compromised sometime in mid-March 2018 (at least, this is as far back as the keylogging records go for John).
It’s also not clear exactly which method the thieves used to get malware on John’s machine. Screenshots for John’s account suggest he routinely ignored messages from Microsoft and other third party Windows programs about the need to apply critical security updates.
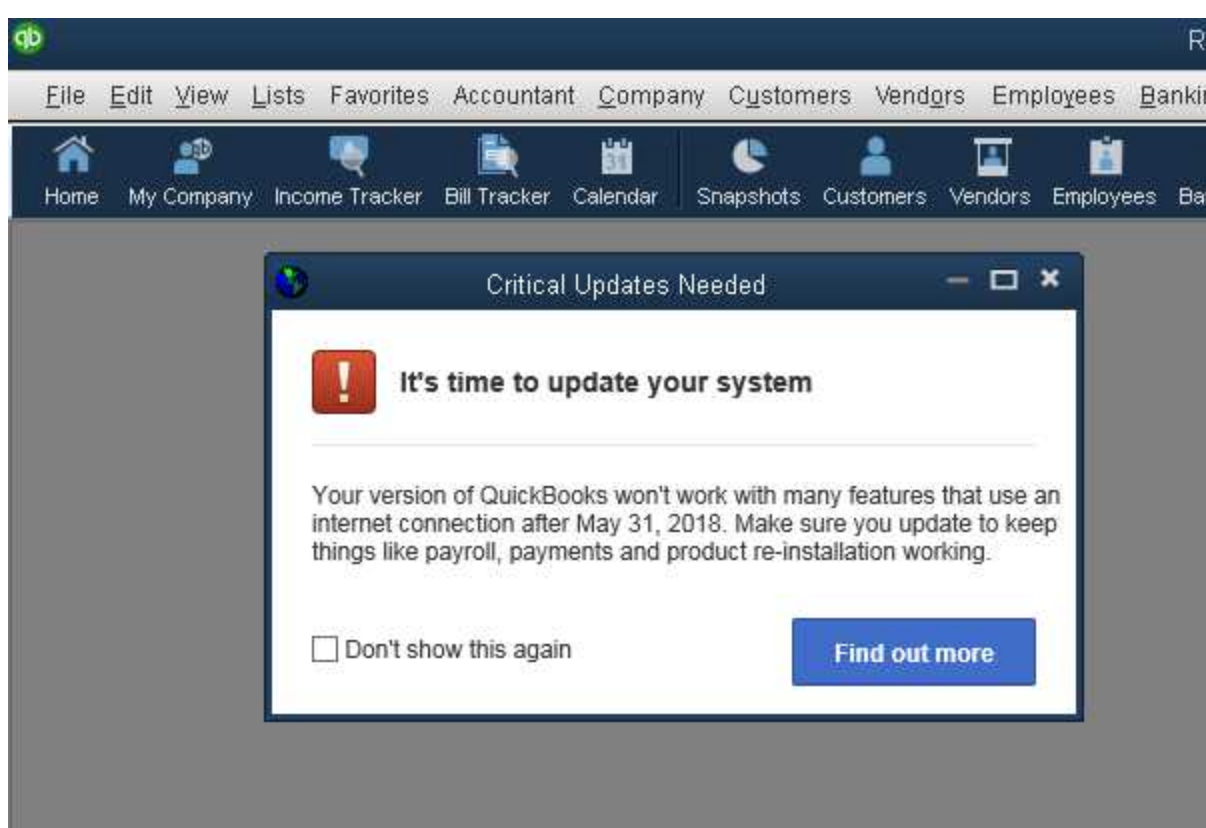
Messages like this one — about critical security updates available for QuickBooks — went largely ignored, according to multiple screenshots from John’s computer.
More likely, however, John’s computer was compromised by someone who sent him a booby-trapped email attachment or link. When one considers just how frequently CPAs must need to open Microsoft Office and other files submitted by clients and potential clients via email, it’s not hard to imagine how simple it might be for hackers to target and successfully compromise your average CPA.
The keylogging malware itself appears to have been sold (or perhaps directly deployed) by a cybercriminal who uses the nickname ja_far. This individual markets a $50 keylogger product alongside a malware “crypting” service that guarantees his malware will be undetected by most antivirus products for a given number of days after it is used against a victim.
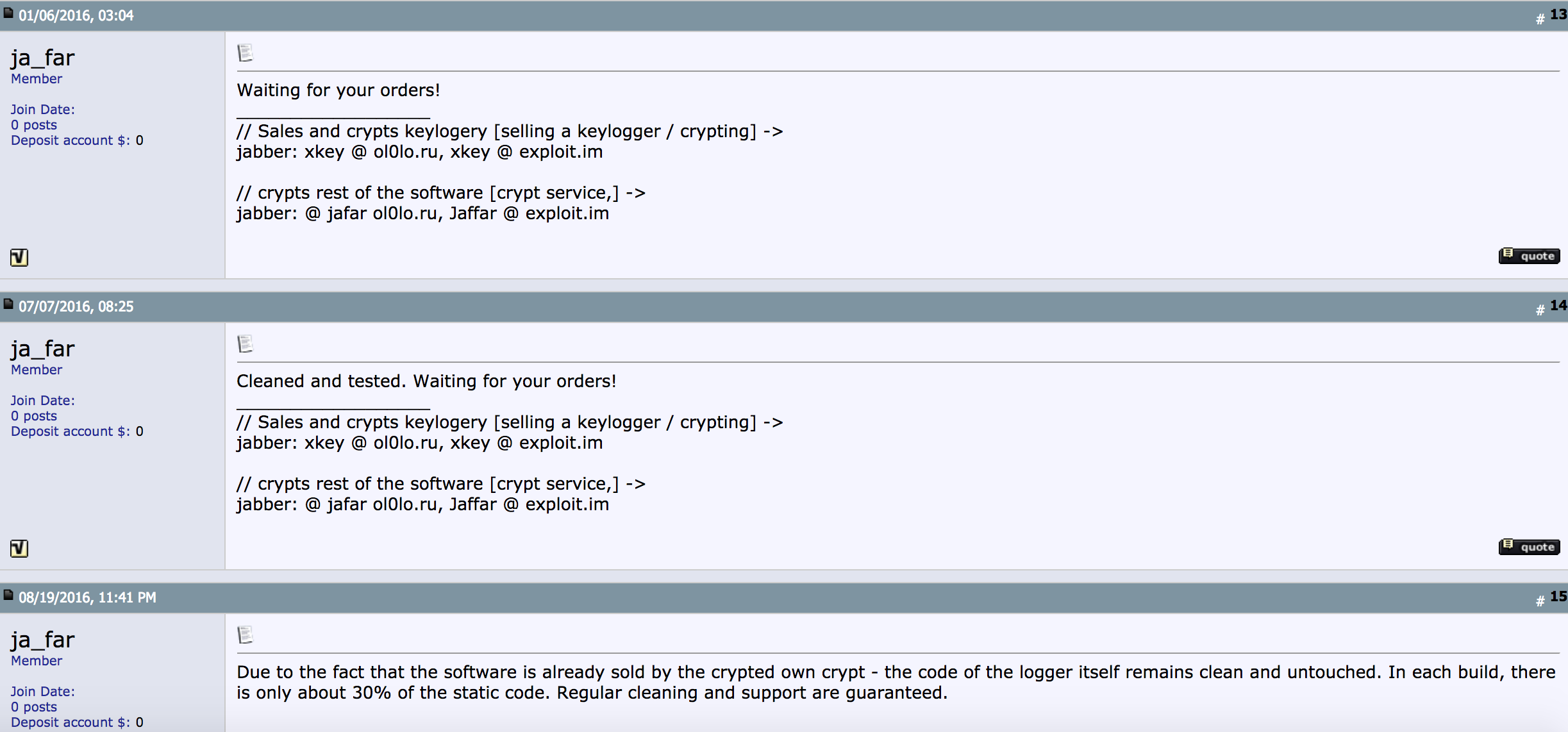
Ja_far’s sales threads for the keylogger used to steal tax and financial data from hundreds of John’s clients.
It seems likely that ja_far’s keylogger was the source of this data because at one point — early in the morning John’s time — the attacker appears to have accidentally pasted ja_far’s jabber instant messenger address into the victim’s screen instead of his own. In all likelihood, John’s assailant was seeking additional crypting services to ensure the keylogger remained undetected on John’s PC. A couple of minutes later, the intruder downloaded a file to John’s PC from file-sharing site sendspace.com.
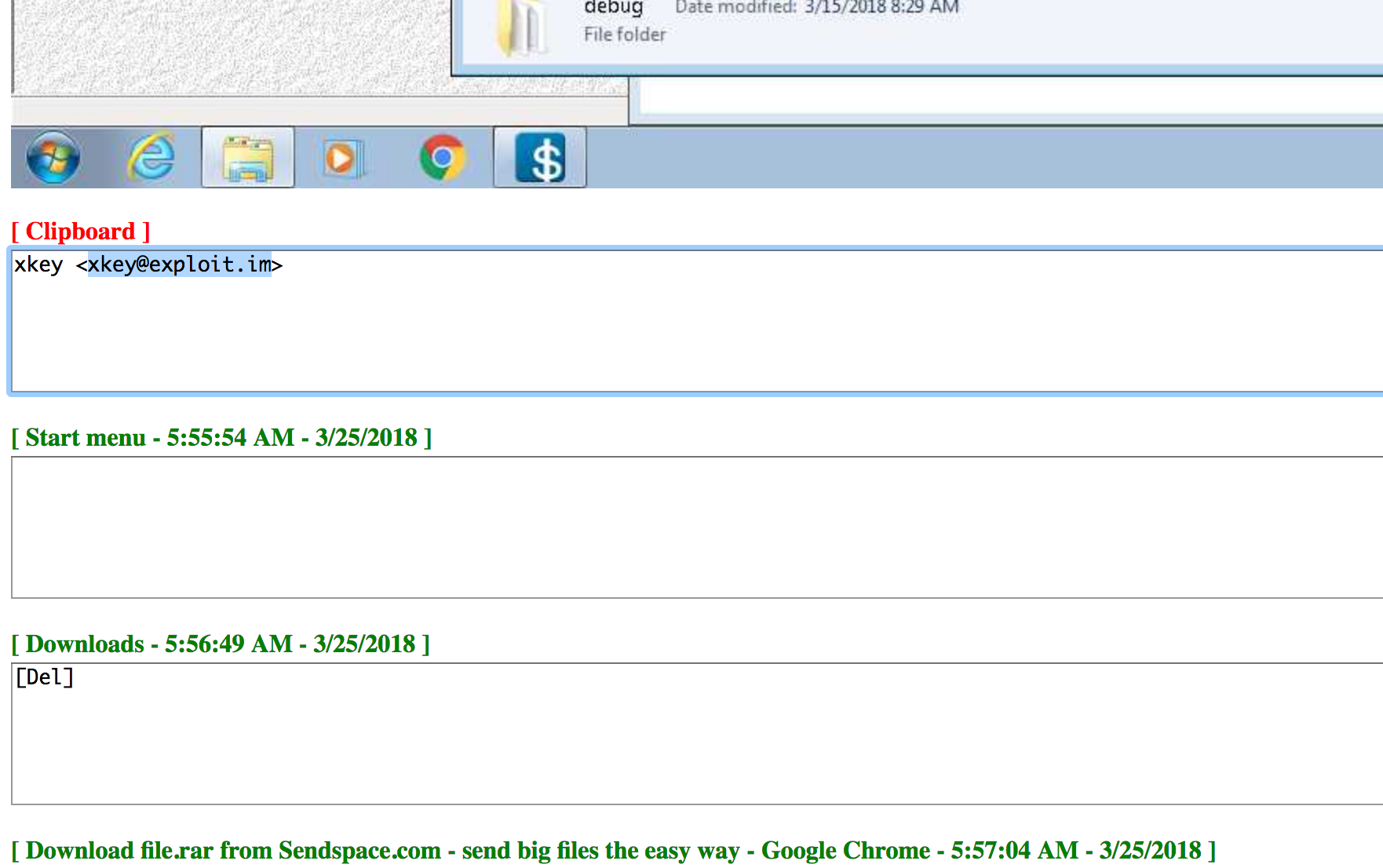
The attacker apparently messing around on John’s computer while John was not sitting in front of the keyboard.
What I found remarkable about John’s situation was despite receiving notice after notice that the IRS had rejected many of his clients’ tax returns because those returns had already been filed by fraudsters, for at least two weeks John does not appear to have suspected that his compromised computer was likely the source of said fraud inflicted on his clients (or if he did, he didn’t share this notion with any of his friends or family via email).
Instead, John composed and distributed to his clients a form letter about their rejected returns, and another letter that clients could use to alert the IRS and New Jersey tax authorities of suspected identity fraud.
Then again, perhaps John ultimately did suspect that someone had commandeered his machine, because on March 30 he downloaded and installed Spyhunter 4, a security product by Enigma Software designed to detect spyware, keyloggers and rootkits, among other malicious software.
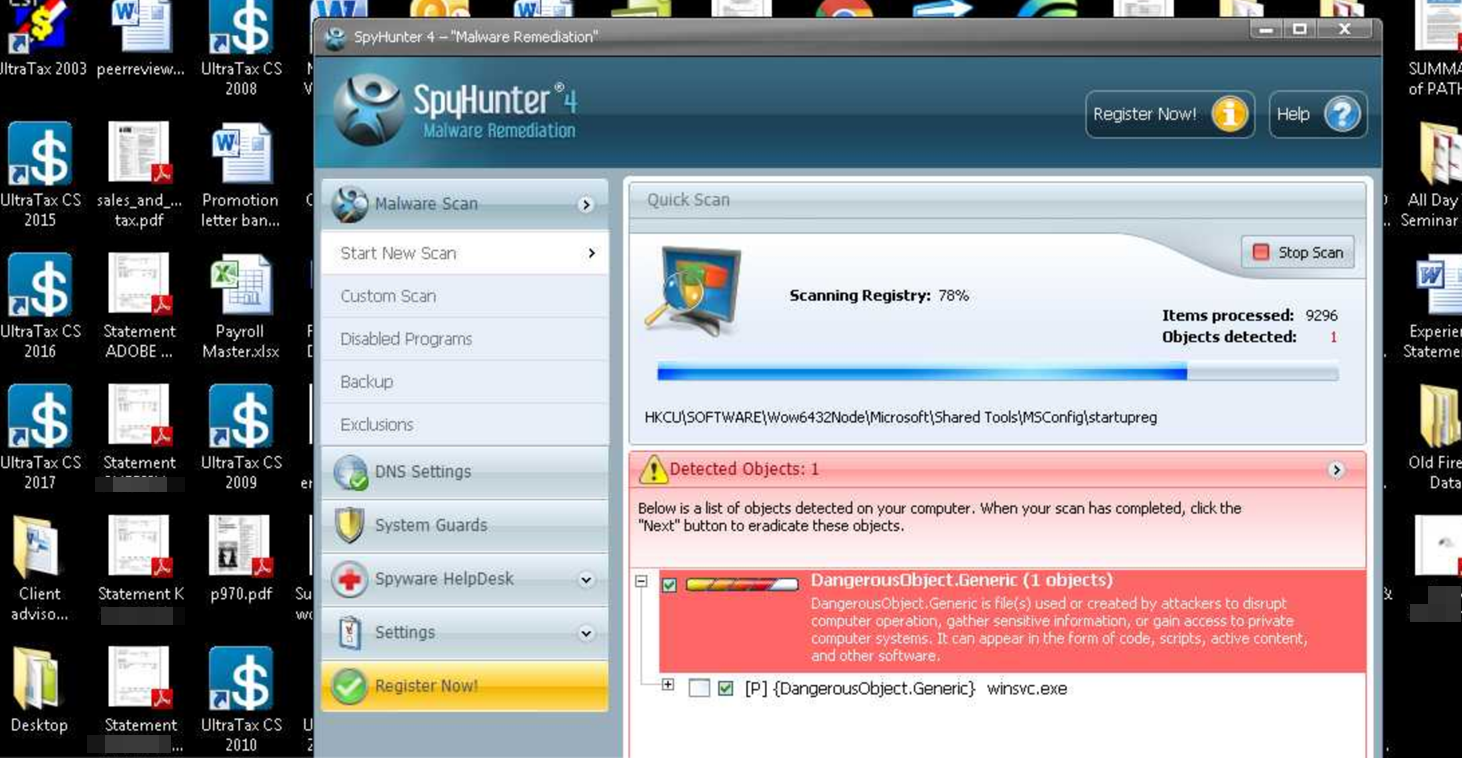
Evidently suspecting someone or something was messing with his computer, John downloaded the trial version of Spyhunter 4 to scan his PC for malware.
Spyhunter appears to have found ja_far’s keylogger, because shortly after the malware alert pictured above popped up on John’s screen, the Web-based keylogging service stopped recording logs from his machine. John did not respond to requests for comment (via phone).
It’s unlikely John’s various clients who experience(d) identity fraud, tax refund fraud or account takeovers as a result of his PC infection will ever learn the real reason for the fraud. I opted to keep his name out of this story because I thought the experience documented and explained here would be eye opening enough and I have no particular interest in ruining his business.
But a new type of identity theft that the IRS first warned about this year involving CPAs would be very difficult for a victim CPA to conceal. Identity thieves who specialize in tax refund fraud have been busy of late hacking online accounts at multiple tax preparation firms and using them to file phony refund requests. Once the IRS processes the return and deposits money into bank accounts of the hacked firms’ clients, the crooks contact those clients posing as a collection agency and demand that the money be “returned.”
If you go to file your taxes electronically this year and the return is rejected, it may mean fraudsters have beat you to it. The IRS advises taxpayers in this situation to follow the steps outlined in the Taxpayer Guide to Identity Theft. Those unable to file electronically should mail a paper tax return along with Form 14039 (PDF) — the Identity Theft Affidavit — stating they were victims of a tax preparer data breach.
Tax professionals might consider using something other than Microsoft Windows to manage their client’s data. I’ve long dispensed this advice for people in charge of handling payroll accounts for small- to mid-sized businesses. I continue to stand by this advice not because there isn’t malware that can infect Mac or Linux-based systems, but because the vast majority of malicious software out there today still targets Windows computers, and you don’t have to outrun the bear — only the next guy.
Many readers involved in handling corporate payroll accounts have countered that this advice is impractical for people who rely on multiple Windows-based programs to do their jobs. These days, however, most systems and services needed to perform accounting (and CPA) tasks can be used across multiple operating systems — mainly because they are now Web-based and rely instead on credentials entered at some cloud service (e.g., UltraTax, QuickBooks, or even Microsoft’s Office 365).
Naturally, users still must be on guard against phishing scams that try to trick people into divulging credentials to these services, but when your entire business of managing other people’s money and identities can be undone by a simple keylogger, it’s a good idea to do whatever you can to keep from becoming the next malware victim.
According to the IRS, fraudsters are using spear phishing attacks to compromise computers of tax pros. In this scheme, the “criminal singles out one or more tax preparers in a firm and sends an email posing as a trusted source such as the IRS, a tax software provider or a cloud storage provider. Thieves also may pose as clients or new prospects. The objective is to trick the tax professional into disclosing sensitive usernames and passwords or to open a link or attachment that secretly downloads malware enabling the thieves to track every keystroke.”
The IRS warns that some tax professionals may be unaware they are victims of data theft, even long after all of their clients’ data has been stolen by digital intruders. Here are some signs there might be a problem:
- Client e-filed returns begin to be rejected because returns with their Social Security numbers were already filed;
- The number of returns filed with tax practitioner’s Electronic Filing Identification Number (EFIN) exceeds number of clients;
- Clients who haven’t filed tax returns begin to receive authentication letters from the IRS;
- Network computers running slower than normal;
- Computer cursors moving or changing numbers without touching the keyboard;
- Network computers locking out tax practitioners.




Real good article , very informative,
i have a different worry: public notaries.
if you have a full-time job, not everyone needs the services of a CPA, but you are required to use a notary for various legal services (inheritance, civil marriage, divorce, buying a house, etc.)
In our country here (Romania) there’s no law that forbids the use of obsolete operating systems and many public services still use Windows XP or 2003 server on internet-connected computers. Yes, even public notaries and the national fiscal administration.
The EU GDPR is entering in effect next month and many branches of the public administration are still using obsolete and no longer maintained technology. *sigh*
Well, if places like Equifax, JPMorgan, and Fidelity have been breached in the past to some extent, are the web-hased services any more secure or are they just a bigger target?
I have passed this onto my dad for his CPA.
I agree with techvet, reader, BSH, and others.
The problem is multifaceted, for starters most help desks of major tax program out source to foreign countries who could not careless about USA laws. They would sell that sensitive information in a New York second and the same goes for out-sourced payroll service like a huge one that begins with A and ends with P.
Second, most of the large tax program sellers are owned in a monopoly like fashion and have the same initial portal which has a C in its name, where credentials are inputted. It is not clear who they outsource to. This not good.
Worse, because of the huge server side need for major tax programs much data is sent over the wire supposedly “Securely” but there are many cases of MITM attacks on HTTPS including some well known AV vendors of foreign origins.
This problem is multiplied by CDNs and others who run transparent proxies which strip SSL and inject cross site scripts for backup and other purposes.
Worse, some CPAs depend upon yahoo and gmail for communication which is scanned for advertising.
A lot of tax preparation programs connect directly to office 365 and may use flash by default. Tax programs also connect directly to banks and brokerages for 1099 data which is uneven in security safety as seen by Fidelity breach. Due to the wide number of entities and backup location companies cloud based tax preparation is not very safe. AJAX dependant tax programs in the background is another attack surface including unsafe browsers.
There just too many sites in the tax loop which degrades security as other posters have pointed out to make today’s cloud tax programs safe. this also goes for lawyers, notary public and many other service companies.
Last, the IRS and state agencies are not the best in security and maybe the worsted as many of Brian Krebs stories have noted. If the IRS lets anybody on the planet see your SSN or EIN it is another hole in the safety dike. A lot of security work needs to be done before paper files are completely gone.
I am in agreement of what you wrote however it should be noted that the IRS has most of the information which they can file tax return (known as return- free filing common in other countries) for most taxpayers and the taxpayer can approve it. However many of the tax firms spent $ trying to derail it simply they are making money and want to keep it that way.
Most CPAs are not the best of the bunch in terms of security as noted by “John” in the article because he ignored many warnings to update his system and decided to use a free ware scanning software to detect what was happening with his computer system. As in all cases, spear phishing is the easiest way to compromise the computer system because the user failed to heed warnings or think twice before responding.
What you left out is that paper filing can be compromised as well. I have seen stories of people stealing the mail to find things like that just to get information.
The ‘problem’ is by design. None of it should be there, in the first place… Then, there would be no headache. Imagine that.
(How many times must it get hacked to pieces, before introduction of a hardware-key for example. An electronic certificate – god forbid, as that would take -some- maintenance. Ah, whatever. :))
I would think this advice would apply to attorneys and insurance agents as well. Come to think of it mortgage banks and brokers too.
They all have confidential info about their clients that would be devastating if released info the wild.
Any place where you need to enter a personal or corporate ID.
The healthcare world in the US is rife with mismanaged data. HIPAA only covers some patient rights. Look at providers and linkages between providers and hospitals and patients.
The US is trying to band-aid ™ this instead of addressing it head on. There is absolutely no way to maintain real privacy when so much information can be gathered or inferred.
I worked for a non-profit once that was under HIPAA rules, and I guarantee we did everything in our power to keep malware out of the system, and every tool we could get a hold of to back that up!! We very rarely got malware inside the perimeter, except for the occasional mobile device from our clients and care providers. The head office knew we had an infection some where almost immediately by using the tools of the trade, and he could call me to visit the machine to remove it ASAP.
This is why I shake my head every time I read an article on KOS and just mutter under my breath, “such amateurs!”
Not to mention mortgage servicers – home inspectors, title insurance companies, appraisers, real estate agents, …
I used to work, many years ago, for an obscure back-end mortgage processing company that was, at the time, used by many of the well-known mortgage banks. We got thousands of mortgage applications running through our systems. The software was the worst spaghetti I’ve ever seen, held together with duct tape. The fact that the system crashed a few times a day when special characters in the data caused SQL syntax errors wasn’t enough to set off security alerts.
We’ve seen evidence of this type of crime victimizing people by using their details to commit fraud outside of the IRS last year.
The CPA really should be outed publicly by someone, as their lack of proactive security process (avoiding updating software) indicates they aren’t even performing minimal due diligence in terms of his clients’ data security.
And if we dox the wrong guy, we’ll be sure to say how sorry we are before moving on to the next victim.
C’mon, Brian. This a-hole CPA John will probably not going to disclose that he had a breach to any of his clients and will continue telling them that “it’s Obama’s fault” or some other nonsense like “we take your security very seriously…” Moreover he will probably continue doing the same irresponsible thing the next year and the year after, if no one exposes him.
But it is Obama’s fault…
“John” probably suspects something, but he probably doesn’t get the magnitude of the infection or the problem unless he reads this article. Shaming and creating an example out of him isn’t the answer. He stopped the problem relatively quickly compared to many in industry.
Also, there is no guarantee the updates would have solved the problem. Although, that is a first step that often gets ignored.
I work IT at a medium sized CPA firm. We hired a new CPA who brought over several clients from her old firm when that firm was purchased by a larger firm. She ran into two clients from her old firm that were victims of identity theft. One sent her a letter from the old firm notifying them of a breach that caused said issue.
When asked about how IT was handled at the old firm, she said one of the CPA’s handled IT “on the side” for a 40 person firm!
I am pretty sure CPA “John” probably running a similar situation. Smaller CPA’s try to handle everything themselves to save costs until it comes back to haunt them.
Good story again, yup, it’s still that time of the year. And happens quarterly to many small businesses. What many may not realize is, most of the CPA businesses are mom and pops. They are the it staff. And what security training was “here is the shredder” . Up till a few years ago, computers were not a CPA thing. The internet was not required for the 2014 return cycle. So there is a lot of catching up for cpa’s. It will take a while. Even the major player companies were caught off guard in 13 when Intuit started updating their program on the internet.
They may not of responded back, because it’s that business is booming,. And they don’t know you or how you could help them. Or what your specialty is.
Got to disagree with “Up till a few years ago, computers were not a CPA thing.”
I started working IT at a CPA firm in 2000. At that time the firm had been “computerized” for 5 years. Internet was (and is) required for software updates to tax and accounting programs (sometimes multiple per week). There is no way a CPA could function without a computer and the internet for well over a decade.
Looking back to 2000, my job was 90% keeping the computers working and 10% security. Today I think the numbers have switched.
Right, probably, one of the larger offices but not in Podunk.ark.
Remember, what kind of adding machine you had at the same time. What types of telephone conferences you had then. And how data was stored then. Look at how you learned of problems in a network at Sears or mom and pop. Then look at who has the resources to learn what happened? Sears or map?
Or, who to task the problem too? Or know who the experts in the field? Shucks, a map is probably using the company they purchased the computer from, a best buy solve the problem, if they were lucky. A local junior college or high school , because not everywhere has access to it firms, they are generally in , with a Texas accent “in new York city”. Remember not everywhere is “”. But, mom and pops are. And they hold just as many records as the big guys, but, you big guys in it, are not in the local news, or local paper, AR in the local talk circuit, so, how are they supposed to know your name? Not every college, even today has a dedicated library with your name there. Not every library has a copy of the wall Street journal daily. Or weekly. Remember there is a world outside of it that has never heard of you. So how are they to know of you? Or, that it’s an solvable problem, that could be fixed with a particular patch? That they never heard of. Get off the high horse, you are part of the problem, not a solution.
Having a computer to use for work and being remotely competent in the details of all operations (including security) are vastly different. And I dont need to remind you how many big accounting and auditing firms have fallen victim to huge breaches, even recently. They dont take it as seriously as they should because its Other Peoples Money and the cost of noncompliance has been low. Now that they are under attack we will start to see that change.
So I look to see about Spyhunter 4.
When I tell Firefox to go to enigmasoftware.com I get the message :
“The owner of http://www.enigmasoftware.com has configured their website improperly. To protect your information from being stolen, Firefox has not connected to this website.”
False alarm, or carelessness on part of Enigma Software?
try “https://www.enigmasoftware.com”
My copy of Firefox let me in…
Actually that is what I tried.
The “s” was left off in my post.
Web-Of-Trust gives almost anything related to Spyhunter 4 or Enigmasoftware a big fat RED rating – I wouldn’t trust them and I wouldn’t touch them with a 10 foot pole!
Better to stick with a known fighter like Hitman Pro. As far as that goes you could put Keyscrambler Pro on board and avoid the problem of undetectable malware. It wouldn’t hurt to put a good HIPS on board also in case malware tries to modify Keyscrambler – I’ve never seen successful evidence of malware being able to do anything more that turn it off though. So it is always a good idea to keep your eye on the system area icon and make sure the “K” is the right color for the situation, and running. They keep updating it to resist malware manipulation though, so I’ve noticed it is getting better and better over time. You have to have the top edition if you want to cover MS Office documents or as many other software applications as possible.
For a minimum HIPS, a lot of people like Winpatrol PLUS which uses more modern methods than the polling the free version does. I’ve even been tipped off by modern malware with the free version, as you know if something has been modified, it is time to start scanning with anti-malware to find out what is causing it.
If you are using a browser to run web based documents, there is NO SUBSTITUTE for IBM’s Rapport. If your bank doesn’t provide it, you may have to message IBM on their site to get a download. I used to get mine from eBay, but that has been a while back.
I am not a shill and don’t work for anyone, so don’t even go there.
Everyone should consider if those the guys are who sued bleepingcomp last year or the year before for labeling them as malware or other junk.
They ran this scam in Australia last year. Hacking into Tax Agents and filing returns on clients behalf. Following that, contacting the unexpected windfall recipients demanding money be repaid:
https://www.smh.com.au/business/consumer-affairs/lets-go-to-europe-ato-refunds-people-who-have-not-lodged-tax-returns-20170724-gxhcaf.html
Started seeing it soon after tax lodgements opened up at the end of the financial year. Looks like they’ll be back again for round 2 come July.
My CPA had HIS own tax return stolen. That was 2 years ago. So far so good with mine. Maybe he learned a lesson…
I know several small CPA operations that have excellent IT security. What do they have that these others don’t? They care.
A person such as “John” might be in direct violation of his CPA oath and potentially the law, e.g., per state regulations on a registered CPA (for starters).
Any one of the three basic protections every business with fiduciary responsibilities should have, would probably have stopped this keylogger. Hint: a real firewall, enterprise (& paid for) malware software, and updating (including modern applications and OS).
Firewalls are not “set and forget” devices at the enterprise level. They have to be configured and maintained, and it requires a level of knowledge that a regular person would not know. They do keep a lot of ‘casually malicious’ traffic out, but anything else? Better to have a basic ‘set and forget’ consumer grade firewall and have constantly and automatically updated anti-malware software that scans on a daily or even hourly basis, with real-time web browser protection, malicious behavior detection, and malicious download prevention to stop a lot of the ‘drive by’ hacks.
Agreed. I did not mean the firewall is enterprise. A leading brand sub $1000 unit (including a couple of years of the update service contract) would do. Support will do optimized settings for you. And I did not presume that the amateur would be putting all this in place. A decent professional could keep everything well set up for a few hours labor charge a year.
Expecting a firewall to keep your users from messing up your systems is a fool’s game. Nice idea, but users need training, testing, then retraining. On a schedule.
I am of course talking about a firewall that is “outbound only”. If you have ports open to the Internet, talk later.
Untrained users will always be the biggest risk you have. Train them. Test them, train them again.
One of my favorite sayings is this: a computer sitting in a closet an duntouched by a human doesn’t get a virus.
A computer used by a 12 year-old will get one pretty quickly.
We are all somewhere between those two.
First question any potential clients should ask of their CPA should be, are you connected to the Internet and why.
There’s no reason why any PC in a CPA office needs Internet access. Print returns snd mail them. Nothing requires electronic filing, tell clients they can wait for their refund check.
It’s not worth a fast refund to risk data security. And a CPA who is incapable of preparing a return without Internet access is an incompetent hack, merely a data entry monkey.
As with most industries, I don’t expect there is a viable tax preparation business model that doesn’t require IT.
Professional tax preparation software (even QuickBooks) now requires regular Internet access, like it or not.
Internet access isn’t so much the problem as is irresponsible IT configuration and usage.
I’ll disagree, with good reason.
It’s quite easy to transmit filings with paper to the tax authorities by print/mail.
Professional software can be updated by CD-ROM that comes in the mail.
I know this because I use a CPA that doesn’t use the Internet at all on his work PC. Same for his partner.
They have a few cables to share and backup files between them, but it’s all local. No wifi, no dialup.
It’s not foolproof. A fire or burglary could occur. But they won’t become a news headline with their simple ways.
I have no idea where you live but the IRS and 95% of the states have mandates for tax preparers to file electronically. Unfortunately Brian, any uniformed person can comment on something they have no knowledge of.
95% of 50 states is 47.5.
Which half state are you referring to?
As for mandates, take a look at form 8948. (1)
You call yourself a CPA?
1. http://www.irs.gov/pub/irs-pdf/f8948.pdf
One of the problem with snail mail is that it takes up to 4 weeks to process the return as they are input in the system by the IRS employees. That takes lots of time and considering the fact the Congress has cut the IRS budget forcing the agency to push to have it filed electronically.
I’m afraid that the software vendors themselves have made it impossible NOT to use the internet in a modern CPA firm – license checks, login authentication, updates, etc all require the internet.
Then you have all of the web-based research, state and federal websites, client Quickbooks Online, etc, etc, that the CPAs have to access.
It’s hard for me to even begin to understand how you could think that any CPA firm could exist without the internet. My client calls me withing 30 seconds if their internet goes down – they can scarcely function.
The screenshot you’ve posted for QuickBooks is not a warning to get a security update. Rather, it is representative of Intuit’s use of extortion to force you to keep buying new versions of the software every three years.
This screenshot shows the warning you receive if you don’t upgrade — they turn off your ability to import data from all your bank and credit card accounts and use that to reconcile your accounts. I recently saw the same warning on my copy of QuickBooks, and had to shell out another $200 to be to keep using the functionality I originally bought.
I’m puzzled by a quandary faced by any customer of a business that might be hacked.
How does a customer (meaning, anyone with no particular standing) find out how secure a business’s computer systems are?
The only external test I can think of is the Qualys SSL Server Test at
https://www.ssllabs.com/ssltest/
I know that a rigorous review would go far deeper. There is, for example, guidance from NIST for small businesses at:
https://nvlpubs.nist.gov/nistpubs/ir/2016/NIST.IR.7621r1.pdf
How can a customer verify how closely any one business follows guidance like this?
You can ask, but most businesses will not tell prospective customers their security strategy, either out of caution or their ignorance.
If they won’t tell you anything, only an on-site visit will work. Look for extra wifi signals on your mobile device and Internet cables connected to their walls. If you see evidence of either, they’ll be breached; it’s just a matter of time.
Existing customers have a smidgen of legal/moral rights to demand explanations and information. But if you’re just Mister Nobody, you have no rights, so pretend to be a reporter.
Addendum: if it’s a small business owner, check on their membership and participation in professional or trade groups, if they mentor kids or help in the local food pantry, are active in community or religion, if they do educational refresher courses, etc.
Those who are actively trying to improve themselves and their communities are more apt to be aware of ways to protect their customers and care enough to try.
Without considerable digging and some scanning you cannot. I have found that this tool helps quite bit with regard to web based services:
https://observatory.mozilla.org/
Good job for the uninitiated. Thanks as always.
Want to not be too alarmist however. The Qbooks thing wasn’t a “critical security update” so let’s not call it that. Don’t want people to get freaked out more than they need to be . Not everything is a “do or die” job — and we need people to understand that as much as we need them to underestand the severity of real issues.
Thanks again
update/adding: instead of people freaking about every single thing (like the Quickbooks alert someone else noted above) , we as a country need everyone to focus on what is important, and skip the unimportant.
This is to keep “brainspace” available. Many customers simply are led to believe “Russians” and “hackers” and they shut down. We can’t have that.
What we need is pragmatic people who aren’t all freaked out 99% of the time – so they can do common-sense things like training their employees, doing testing to make sure employees are listening, and other things sensible.
I’m afraid too many people are already shutting down and passing off responsibility to outsourcers. And few good sustainable things come from that.
Take responsibility, train, test, and all will be good enough. Keep up the good work.
I’m not going to bash John because:
The malware was/is supported to be not detected.
He likely gets hundreds if not thousands of documents mailed to him, links to googledocs type public storage, likely many are password protected compressed files – preventing detection by most filters.
Most people think they are to small to be targeted and don’t have corporate quality security, which unfortunately is needed for targeted business.
Most people think they are safe if they don’t browse beyond their (imaginary) safe space.
Small businesses must be the easiest target to hack.
I almost started a small business, craft and online store, but the security/liability/cost of transactions just makes it impractical. :/ So it’s only a hobby that dies due to hackers just existing, and profiteers exploiting that.
A lot of business owners rushed to the conveniences and utility of ubiquitous Internet access without the experience and knowledge to appreciate the risks and disadvantages. They are like the novice craftsman who sees a hammer as a useful tool, without considering its use as a murder weapon. (1)
How many businesses (and political campaigns) jumped to join Facebook in recent years, only to later realize that it’s a lousy platform for advertising? (2) (3)
You’re right. It’s easy to poke fun and find fault in something bad happening to a business owner. It’s easy to forget they’re just ordinary people doing the best they know to do.
It’s good, however, to learn from mistakes and appreciate the experiences of others.
1- https://ucr.fbi.gov/crime-in-the-u.s/2016/crime-in-the-u.s.-2016/tables/expanded-homicide-data-table-4.xls
2 – https://mashable.com/2012/11/28/jerry-maguire-social-media-marketing
3 – Facebook couldnt even help their preferred candidate with discounted advertising rates! https://mobile.twitter.com/boztank/status/968577962223136768
This is especially difficult because many tax preparers are from one or two person companies, and don’t have the benefit of an I.T. department keeping them secure.
I am an individual with a limited budget for security. I maintain several computers and portable devices by myself. Yes, I have to plan when to run a full system scan, and when to do a full system backup, and how to do full disk encryption, and how to secure system backups somewhere out of harm’s way.
If I ran a business, I’d apply the same skills to my home and my business. And if I’d talk to household members about these issues as well (and carefully isolate casual computer users to their own network).
It’s hard, but it’s doable, and a vigorous, active businessperson has the chops to do it. If they are interested. I just don’t really know how to assess the ability of a business to implement a good security plan and stick to it.
(But when I ask the counter person at a medical facility about encryption, and they give me a blank look, I get a pretty clear indication that the staff are ignorant.)
It is NOT difficult to have good basic security and it IS a requirement of the duties. CPA’s especially, are constantly being informed of the kind of things that should be done for IT security. They may choose to ignore it or not spend the money.
Very good security can be obtained on an annual cost that is less than one month’s rent on the office. But it isn’t about the IT only: as pointed out above the User must care, and follow safe practices (training etc., readily available).
When it comes to securing data whole drive encryption is a must! As far as accessing websites and everything else you must keep your credentials secure and strong. Malware protection is a must and given the proliferation of mobile devices people must deploy a remote wipe and data breach protection solution like http://www.drivestrike.com most of these solutions are very inexpensive especially given the consequences of a data breach. I just don’t understand how these people call themselves professionals…
You guys do realize that the IRS itself had its database of tax preparers hacked in January and that the information has been for sale on the dark web ever since, right?????
There is no absolute protection, just like there is no absolute protection at home—you just need to make it more difficult to go after you than the next guy and be EXTERMELY vigilant about problems. Post signs; use a burglar alarm, lock your doors, etc., but if someone wants in bad enough, they will get it. That’s why both preventative AND detective internal controls are so important.
Is there a silver lining implicit in this scam? This is a more difficult and much more labor intensive process than simply filing phony returns for a previously unregistered IRS accounts. Does this mean that there’s less opportunity for the simpler scam? If so, that’s progress, however uneven.
Lets get down to the real issue. The US income tax system is archaic and unnecessary. It is used by politicians who think they can control the masses. In a free country there is no place for such control and no use for having to report income to the government.
Except that reporting is a way to offset the cost of the budget to those who can afford to pay. The other option would be to require every person in the US to pay ‘their portion’ which is around $22k a year. Might be a bit difficult for those who barely make that. I’m not sure many four person families could spare $88k from their budget.
Estimate taken from https://www.usgovernmentspending.com/per_capita (I have not vetted the data myself…)
Obviously an issue that the accountant’s endpoint was compromised, but the larger issue around fraudulent tax returns is that the IRS and states do a poor job of authenticating and getting taxpayer authorization to process returns. Fraud is the result.
For years, tax agencies accepted knowledge of a static identifier, your Social Security Number, as proof that your return was legit and processing authorized. Over time, widely shared SSNs leaked and became poor “secret passwords” as they were misused by fraudsters. Tax agencies tried adding static PINs, and now ask for Drivers License information. Still static, still widely shared, still poor substitutes for passwords. We will get a temporary improvement, then more fraud.
I used to be responsible for cybersecurity and fraud at a large financial institution, I’ve seen this movie too many times, and left that job to solve problems just like this. What’s needed are secure 1-time PINs that are GENERATED BY THE TAXPAYER, cryptographically bound to the SSN, and that provide explicit authorization to process the return.
We absolutely have the technology to do this easily. Correctly implemented, this same authorization approach can be used to address insurance fraud, account takeover fraud, and even limit data sharing at places like Facebook and the credit bureaus.
It’s time we stop trying to address a modern tax-fraud problem with 1980s technology. Consumer authorization is what’s been lacking
Brian — Great article that I’m passing along to our accountants.
But for most businesses QuickBooks online is no substitute for the desktop version, and there are a huge number of complaints from people who made the switch, with many feeling they were misled by Intuit’s marketing of the online version. (Classes don’t work the same, ditto for drilling down in reports, the database seems to be flat …)
Since the data format is completely different switching back without data loss is very difficult once you’ve used the online version.
That’s not good news for users of QuickBooks Desktop for Mac. Intuit is no longer developing QuickBooks Desktop for Mac and will stop supporting the last edition of it (2016) on May 31, 2019. So those users will have to switch to QuickBooks Online or the Windows version of locally-installed QuickBooks.
Thank you for sharing such great information. It’s a pleasure to visit here.
CBS News just ran a segment on this exact issue:
https://www.cbsnews.com/live/video/20180413003919-irs-issues-warning-about-potential-tax-scams/
Pay attention to the Mom&Pop CPA lady who can’t fanthom the idea that she got hacked even though “all her clients had their returns hijacked”
Brian’s (this) article was the first thing that I thought of while watching. She is either in denial or is in CYA mode.
Hey Brian, can you give us the contact information you used to send those sites to facebook? The reporting system is broken. And even when a person (and not a silly algorhythm) sees the report, they are usually just contract employees (with short contracts) who don’t know, or don’t care about what they are doing. After 48-72 hours, your report will get an automated polite thank you and no further action, regardless of the report. When I report a page or a group I get zero response or action. Facebook could be so good, but they have lost control. They do not have security in place for over 2 billion users. When I had to guess between ignorance and complicity I used to guess complicity. They knew what was going on and refused to do anything about it. When I listened recently to Zuckerberg testify, now I’m thinking ignorance. Those sites you report point to ignorance. But in that ignorance, Facebook continues to feed the sheep to the wolves online. That will be their legacy.
Please move this comment over to the Facebook article. Sorry I posted in the wrong place.
The best thing when identity thieves hack your account, NOT to have this account at all 🙂
The more information you publish about your self on internets, they easier become to find you and/or for example hijack your account.
Such people operates mainly with publicly available information, so here comes another conclusion – if you want to be hacked one day, publish as much information as you can!
Best regards,
Markus
Journalist at ScanForSecurity.com
“I continue to stand by this advice not because there isn’t malware that can infect Mac or Linux-based systems, but because the vast majority of malicious software out there today still targets Windows computers, and you don’t have to outrun the bear — only the next guy.”
Ehhhh…
It could be because I despise anything that even seems to promote the myth of the “malwareless mac”.
It could be because I dislike half-measures though too.
Which is another way of saying: If I had a choice between a CPA who understands computers well enough to know how to protect one, and one who only knows to “buy a mac” when he has problems, guess which one I’m going to pick.
I know that means I’m probably excluding a whole lot of good CPAs who aren’t computer literate, but the fact of the matter is: continuing to supply crutches to people who can’t (or refuse) to adapt is Legacy Support.