Storing passwords in plaintext online is never a good idea, but it’s remarkable how many companies have employees who are doing just that using online collaboration tools like Trello.com. Last week, KrebsOnSecurity notified a host of companies that employees were using Trello to share passwords for sensitive internal resources. Among those put at risk by such activity included an insurance firm, a state government agency and ride-hailing service Uber.
By default, Trello boards for both enterprise and personal use are set to either private (requires a password to view the content) or team-visible only (approved members of the collaboration team can view).
But that doesn’t stop individual Trello users from manually sharing personal boards that include proprietary employer data, information that may be indexed by search engines and available to anyone with a Web browser. And unfortunately for organizations, far too many employees are posting sensitive internal passwords and other resources on their own personal Trello boards that are left open and exposed online.
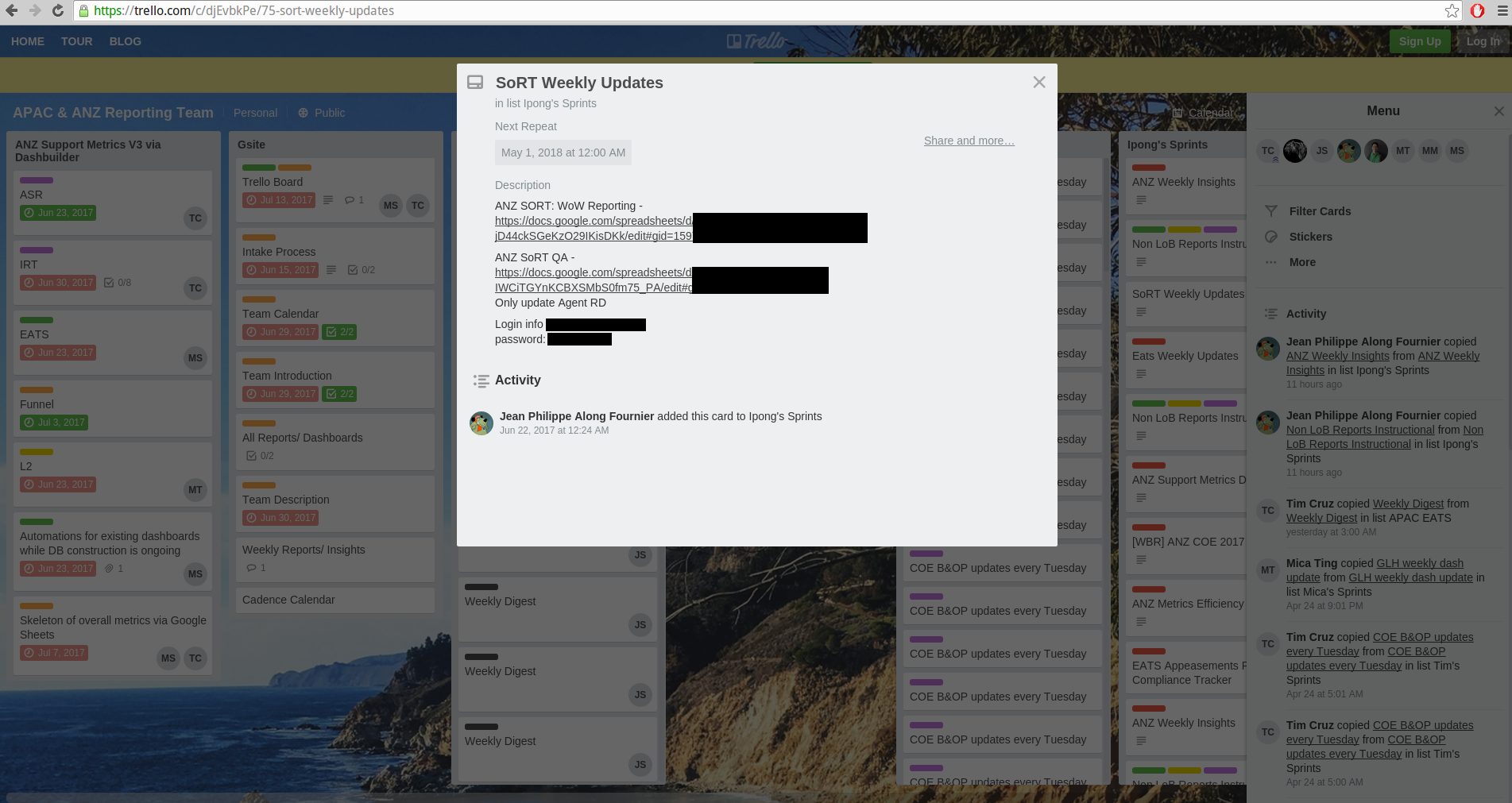
A personal Trello board created by an Uber employee included passwords that might have exposed sensitive internal company operations.
KrebsOnSecurity spent the past week using Google to discover unprotected personal Trello boards that listed employer passwords and other sensitive data. Pictured above was a personal board set up by some Uber developers in the company’s Asia-Pacific region, which included passwords needed to view a host of internal Google Documents and images.
Uber spokesperson Melanie Ensign said the Trello board in question was made private shortly after being notified by this publication, among others. Ensign said Uber found the unauthorized Trello board exposed information related to two users in South America who have since been notified.
“We had a handful of members in random parts of the world who didn’t realize they were openly sharing this information,” Ensign said. “We’ve reached out to these teams to remind people that these things need to happen behind internal resources. Employee awareness is an ongoing challenge, We may have dodged a bullet here, and it definitely could have been worse.”
Ensign said the initial report about the exposed board came through the company’s bug bounty program, and that the person who reported it would receive at least the minimum bounty amount — $500 — for reporting the incident (Uber hasn’t yet decided whether the award should be higher for this incident).
The Uber employees who created the board “used their work email to open a public board that they weren’t supposed to,” Ensign said. “They didn’t go through our enterprise account to create that. We first found out about it through our bug bounty program, and while it’s not technically a vulnerability in our products, it’s certainly something that we would pay for anyway. In this case, we got multiple reports about the same thing, but we always pay the first report we get.”
Of course, not every company has a bug bounty program to incentivize the discovery and private reporting of internal resources that may be inadvertently exposed online.
Screenshots that KrebsOnSecurity took of many far more shocking examples of employees posting dozens of passwords for sensitive internal resources are not pictured here because the affected parties still have not responded to alerts provided by this author.
Trello is one of many online collaboration tools made by Atlassian Corporation PLC, a technology company based in Sydney, Australia. Trello co-founder Michael Pryor said Trello boards are set to private by default and must be manually changed to public by the user.
“We strive to make sure public boards are being created intentionally and have built in safeguards to confirm the intention of a user before they make a board publicly visible,” Pryor said. “Additionally, visibility settings are displayed persistently on the top of every board.”
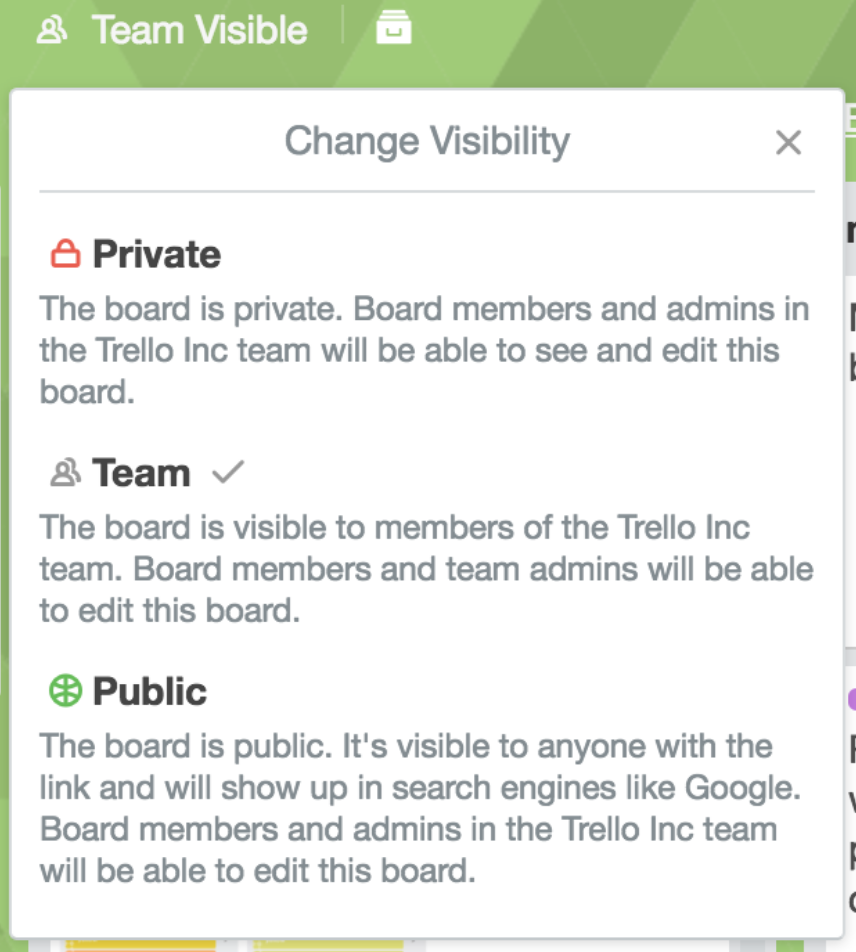
If a board is Team Visible it means any members of that team can view, join, and edit cards. If a board is Private, only members of that specific board can see it. If a board is Public, anyone with the link to the board can see it.
Interestingly, updates made to Trello’s privacy policy over the past weekend may make it easier for companies to locate personal boards created by employees and pull them behind company resources.
A Trello spokesperson said the privacy changes were made to bring the company’s policies in line with new EU privacy laws that come into enforcement later this month. But they also clarify that Trello’s enterprise features allow the enterprise admins to control the security and permissions around a work account an employee may have created before the enterprise product was purchased.
Uber spokesperson Ensign called the changes welcome.
“As a result companies will have more security control over Trello boards created by current/former employees and contractors, so we’re happy to see the change,” she said.
KrebsOnSecurity would like to thank security researcher Kushagra Pathak for the heads up about the unauthorized Uber board. Pathak has posted his own account of the discovery here.
Update: Added information from Ensign about two users who had their data exposed from the credentials in the unauthorized Trello page published by Uber employees.




A whole generation of software services have been designed with these flaws, which makes it so difficult to tell what can be seen by third parties and not providing explicit opt-ins to publicly visible data.
All… if not now, ALL DATA IS ACCESSIBLE
@Prince Charles:
Krebs quotes a Trello spokesperson as saying they endeavor to make it clear what can be seen by third parties and to provide explicit opt-ins. The article includes a screenshot which seems to support that claim.
Do you have reason to believe the spokesperson’s claim is inaccurate?
I mean that many major online social media and sharing sites, such as FB, Linkedin and so on all make it very difficult for an average user to control the level of visibility of their data and understand what can be seen and by whom.
And yes, I am sceptical about Trello’s (and the others) altruism in this regard.
There are many things wrong with that screenshot from a user interface design perspective. First, the “lock” symbol should have some indication that this is the *preferred* option. Second, the public option should be in red, with a highlighted “WARNING” in yellow with a red background so that the user of the board is drawn to notice it. The “WARNING” sign should NOT go away or change color even if the user selects the board to be public.
Great observation. I’d also venture to say they have the colors backwards. Should be green, yellow, red like a traffic light.
Also a bit scary that Trello employees can read everything.
1. Entering proprietary data into a “solution” owned by a second company that is not a business partner.
2. Improper setup of Trillo accounts.
3. Insufficient oversight of Trillo accounts by Uber management.
4. Sharing account credentials, and that by way of posting on accounts instead of by secure, party-to-party comms. (e.g. email or phone).
There’s alot wrong here. (Uber, in particular, has a history of playing fast and loose with assets.)
TarekOkail and Eric bring up good points.
“I’d also venture to say they have the colors backwards.”-Eric
I agree. I am wondering if this whole platform is just a doxing site or scammer site. What was Trello’s real business model?
“scary that Trello [admin] employees can read everything.”-Eric
Yes it is. These employees could pipe this data out to any site for a few dollars more. Everybody that is adding passwords to the site is just multiply their employer’s attack surface.
I think William Grants monitoring of outbound connections is a good idea. But, the logs and even the outbound connections could be encrypted and they are on Trello’s servers. That could be hard to get into [the logs would be hard to get to but the outbound connections not so hard].
Vb’s robot txt is not a sure thing. Many bot indexers-scrappers just blow right past the robot txt file. I guess trello’s servers would have to have and ACL list and controls to do the job. I doubt Trello is going to do it.
The pages that are publicly visible have the title “Private Team” and “Personal”.
Do you consider that “making it clear” to users?
Hey Prince Charles, is this how I will also live out my golden years? From being royalty to posting comments on message boards?
$500 bounty!? Someone can get way more on the black market for the breach of the data of their sh**y company.
And you could make a lot more money robbing banks than working at McDonald’s, but most of us have a moral compass that points us in one direction over the other.
Yea, bug bounty programs are generally just a joke. Strictly a matter of warm and fuzzy “feel good” PR for the companies involved. Only the whitehats that would have reported the bugs anyway are even gonna sign up.
How much would Equifax have paid for the bug that ended up costing them millions of dollars and the CEO his job? A couple of thousand? Ten thousand? Probably not even that.
Companies and also governments are simply not willing to pay to get their systems and software properly tested. But if you are reading Brian’s blog, then you already knew that.
Shadow IT strikes again…
Exactly! It could mean there is a need that’s going unfulfilled in the organisation, and semi-smart people are finding workarounds to get the job done.
Sharing passwords is a bad idea, and it’s common when the friction to follow correct processes is high, or IT turnaround is long.
SecureMySocial offers multi-patented technology that warns people in real time if they are sharing passwords and other sensitive materials in social forums. Check it out…
Why does Trello even allow its boards to be indexed anyway? Fair enough you can make a board public, but public to those with the link is a step above public and easily discoverable.
Tell me how you’d solve the problem of making publicly accessible web pages non-indexable without requiring that all access be credential controlled.
Though maybe you should first answer, what do you think “indexable” means?
robots.txt could be added to the public Trello boards and prevent them from being indexed.
https://en.wikipedia.org/wiki/Robots_exclusion_standard
The truly sad thing about this story is that–if he had the time–Brian could probably write one like this every day for the rest of his life (until passwords die–right). There are so many services and devices out there, and users are so careless.
The other scary part is when these login credentials were reused somewhere else… think about it.
Brian,
How can we search Trello for any company specific information?
Thanks
Time to start reviewing outbound logs and see how much Trello (and other tools) are being used at some state agencies.
Security breaches and frauds and hacks and all kind of things happening only becouse people use non secured things !!
Use the same tools as criminals and you will be safe.
And btw…if intututions like equfax or similar companies letting some hacks and data breaches happening ?? Why you as regular joe even worry about it ?? Life is simple just find out whos guilty if anything happening and make some person to have responsebility. Regular joe is working 8-5 daily he has no clue about what goimg on. So then why he even care about it.
If people who work in goverment and in special intutions cant have full responsebility to do good job then whos guilty ?
Like in england we all remember how wide open the banks leaved doors…and crooks and fraudsters just took the advanched of the situation.
Or other example if banks gives you credit card with big credit limit without even care about if you pay back or not ?
Then who is guilty ?? All of this sounds like joke no any serious smart logically thinking person should not take it seriously non of the cyber crimes non of the breaches.
Becouse those things can only happening when doors are wide open. If you leave door open wide then who you blame ?? Shut the the door and specially ijn usa get the people use 2 factor security and no hacker or cracker or who knows who cant touch nothing. I guess if the world will be without open doors in the system we would have more violent crimes coz all this crooks and fraudsers will take the money just other way.
But i guesss what then we will have police state too..coz life will be so much fulled with violance that we cant imagine that
Login credentials posted on Trello are still visible in search engine results even after the boards have been made private.
It’s stuff like this that makes us move to multifactor. Literally had employees storing and sharing passwords via Dropbox.
Not sure if it was mentioned, but if an attacker is able to hijack the invite link to a private board, it will give the attacker the ability to view the board without having to register/login as well. Trello should be banned by all! heh
Apparently, this problem has existed for a while and Trello knew about it all this time!
Article from last year:
https://www.gizmodo.com.au/2017/06/trello-scrambles-to-rescue-users-who-foolishly-used-its-service-to-store-passwords/
It’s really nice to see some discussion on improving the platform itself (as why boards are indexed, or UI improvements to provoke less confusion).
However, what’s bother me the most is that no one took a look at the problem from the other side – employees security awareness. I’m not talking about this case – but just in general (as this story can teach some lessons).
1. Had employees been trained to use new platform, especially how to set data to private/public/etc?
2. Had employees been taught about other alternatives for secure data sharing/storage. Did anyone specified which data can or cannot be post on the external system (as passwords)?
3. If the only usage of this platform was publishing private information – why not hosting it on own (preferably with internal access only) platform?