Reddit.com today disclosed that a data breach exposed some internal data, as well as email addresses and passwords for some Reddit users. As Web site breaches go, this one doesn’t seem too severe. What’s interesting about the incident is that it showcases once again why relying on mobile text messages (SMS) for two-factor authentication (2FA) can lull companies and end users into a false sense of security.
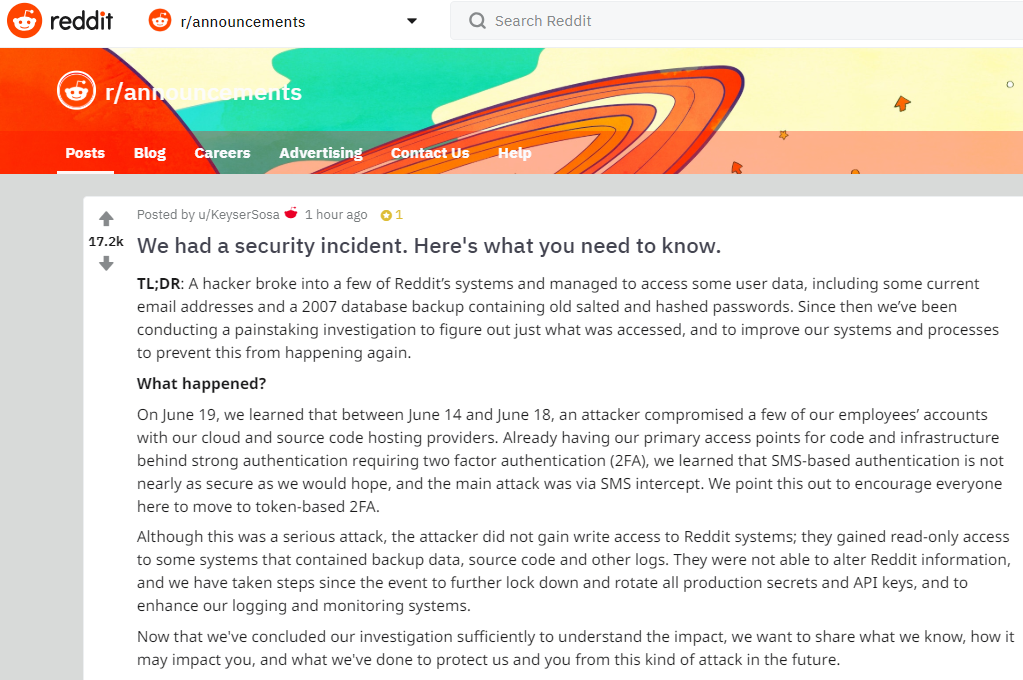
In a post to Reddit, the social news aggregation platform said it learned on June 19 that between June 14 and 18 an attacker compromised a several employee accounts at its cloud and source code hosting providers.
Reddit said the exposed data included internal source code as well as email addresses and obfuscated passwords for all Reddit users who registered accounts on the site prior to May 2007. The incident also exposed the email addresses of some users who had signed up to receive daily email digests of specific discussion threads.
Of particular note is that although the Reddit employee accounts tied to the breach were protected by SMS-based two-factor authentication, the intruder(s) managed to intercept that second factor.
“Already having our primary access points for code and infrastructure behind strong authentication requiring two factor authentication (2FA), we learned that SMS-based authentication is not nearly as secure as we would hope, and the main attack was via SMS intercept,” Reddit disclosed. “We point this out to encourage everyone here to move to token-based 2FA.”
Reddit didn’t specify how the SMS code was stolen, although it did say the intruders did not hack Reddit employees’ phones directly. Nevertheless, there are a variety of well established ways that attackers can intercept one-time codes sent via text message.
In one common scenario, known as a SIM-swap, the attacker masquerading as the target tricks the target’s mobile provider into tying the customer’s service to a new SIM card that the bad guys control. A SIM card is the tiny, removable chip in a mobile device that allows it to connect to the provider’s network. Customers can request a SIM swap when their existing SIM card has been damaged, or when they are switching to a different phone that requires a SIM card of another size.
Another typical scheme involves mobile number port-out scams, wherein the attacker impersonates a customer and requests that the customer’s mobile number be transferred to another mobile network provider. In both port-out and SIM swap schemes, the victim’s phone service gets shut off and any one-time codes delivered by SMS (or automated phone call) get sent to a device that the attackers control.
APP-BASED AUTHENTICATION
A more secure alternative to SMS involves the use of a mobile app — such as Google Authenticator or Authy — to generate the one-time code that needs to be entered in addition to a password. This method is also sometimes referred to as a “time-based one-time password,” or TOTP. It’s more secure than SMS simply because the attacker in that case would need to steal your mobile device or somehow infect it with malware in order to gain access to that one-time code. More importantly, app-based two-factor removes your mobile provider from the login process entirely.
Fundamentally, two-factor authentication involves combining something you know (the password) with either something you have (a device) or something you are (a biometric component, for example). The core idea behind 2FA is that even if thieves manage to phish or steal your password, they still cannot log in to your account unless they also hack or possess that second factor.
Technically, 2FA via mobile apps and other TOTP-based methods are more accurately described as “two-step authentication” because the second factor is supplied via the same method as the first factor. For example, even though the second factor may be generated by a mobile-based app, that one-time code needs to be entered into the same login page on a Web site along with user’s password — meaning both the password and the one-time code can still be subverted by phishing, man-in-the-middle and credential replay attacks.
SECURITY KEYS
Probably the most secure form of 2FA available involves the use of hardware-based security keys. These inexpensive USB-based devices allow users to complete the login process simply by inserting the device and pressing a button. After a key is enrolled for 2FA at a particular site that supports keys, the user no longer needs to enter their password (unless they try to log in from a new device). The key works without the need for any special software drivers, and the user never has access to the code — so they can’t give it or otherwise leak it to an attacker.
The one limiting factor with security keys is that relatively few Web sites currently allow users to use them. Some of the most popular sites that do accept security keys include Dropbox, Facebook and Github, as well as Google’s various services.
Last week, KrebsOnSecurity reported that Google now requires all of its 85,000+ employees to use security keys for 2FA, and that it has had no confirmed reports of employee account takeovers since the company began requiring them at the beginning of 2017.
The most popular maker of security keys — Yubico — sells the basic model for $20, with more expensive versions that are made to work with mobile devices. The keys are available directly from Yubico, or via Amazon.com. Yubico also includes a running list of sites that currently support keys for authentication.
If you’re interested in migrating to security keys for authentication, it’s a good idea to purchase at least two of these devices. Virtually all sites that I have seen which allow authentication via security keys allow users to enroll multiple keys for authentication, in case one of the keys is lost or misplaced.
I would encourage all readers to pay a visit to 2fa.directory, and to take full advantage of the most secure 2FA option available for any site you frequent. Unfortunately many sites do not support any kind of 2-factor authentication — let alone methods that go beyond SMS or a one-time code that gets read to you via an automated phone call. In addition, some sites that do support more robust, app- or key-based two-factor authentication still allow customers to receive SMS-based codes as a fallback method.
If the only 2FA options offered by a site you frequent are SMS and/or phone calls, this is still better than simply relying on a password. But it’s high time that popular Web sites of all stripes start giving their users more robust authentication options like TOTP and security keys. Many companies can be nudged in that direction if enough users start demanding it, so consider using any presence and influence you may have on social media platforms to make your voice heard on this important issue.




Real good 2FA primer ! I primary use TOTP-based methods
I would really love to use a security key. Where do I plug it into on my iPhone/iPad?
I also need to have it plugged into my phone, tablet, desktop, and laptop. At the same time.
How do I do this?
(Seriously, if I could make this work, I’d use a key for all my key accounts. There are probably 20-40 that I’d like to secure this way.)
You plug in the key to authenticate, then remove it. It doesn’t need to be attached the whole time you’re using a site. And the keys for mobile devices use Bluetooth or NFC. No plug required.
Thanks. I check these out.
For your phone, you need to get a fob/key that has NFC (Near Field Communication) like the Yubico Neo, and a phone that has NFC capability.
Until recently this was only available on Android phones, but Apple has recently just started supporting it.
With an NFC fob, you just touch it to the back of the phone – no physical port necessary.
Really quite convenient.
I’ve previously used OTG cables when my security key was required on a google site. I’m not sure if this works with all sites/phones though.
How about an option to block access from non-US IPs? It would obviously not stop everything but would cut out some of it.
They could use VPN and subvert the IP
You would be surprised the amount of hacking a little geo filtering stops. I also filter datacenters, which stops many VPNs. But what this does is reduces the chatter from bots so that log files are human readable, AKA old school. It is not real security, but still useful. It never hurts to reduce attack surface.
I spent some time studying TOTP in order to implement it in a website. That project didn’t happen, but here is my core dump:
Redhat has an app called FreeOTP. You can “sync” the codes from the app to a Linux PC and see how time based codes work. I don’t recall the Linux command line programs offhand, but it wasn’t that hard to find online. The instructions generally say you have 30 seconds to enter a TOTP, but really this is guard banded on two sides, so you set up a 90 second window with three codes.
My recollection is a yubikey doesn’t contain a real time clock. It depends on the clock in your computer.
Now the really old RSA now Verisign “football” shaped OTP have a real time clock, but not a great one. These generate a six digit code, but apparently one digit is used in timing.
This. I always hear whining about how this security layer and that security layer can be bypassed – but that’s not a good argument against using it. Like everyone else, absent a specific personal / political / religious motivation most attackers reach for the low-haging fruit. At some level of skill and resource commitment, any layer can be bypassed (especially if someone is willing to use good old-fashinioned “lead pipe” hacking). If a layer offers a decent cost/benefit/hassle ratio, we generally try to implement it.
So, does this mean instead of a cheatsheet with 100 passwords, some of them requiring 2FA, I should carry around a knapsack of fob keys? Jeez.
Nope. You can use the same key at multiple sites that support keys. And if you’ve got a backup key that you’ve also enrolled, you should definitely not be carrying that around with you but it should instead be someplace safe.
Someplace safe – think 3rd key offsite at some distance. Consider a house fire, as devastating as it is – should you also be permanently locked out of Email and all key-locked resources?
In the case of Google / Gmail, you can still submit a request to recover your accounts after a “cooling off” period of a few days. Remember that any device you previously logged into is still logged in. You just can’t log in from a new device.
Not saying a perfect storm of loosing, all at the same time, both keys and all assets that have been logged in can’t happen, but it seems to be an outside likelihood.
You shouldn’t need a cheat sheet for your passwords, either. Use a password manager (I’m a LastPass user) and you’ll only need to remember one password. There are so many benefits to a password manager that it’s something you should really consider. All of my passwords are as long and as complex as the website will allow and I have no idea what any of them are once they’re set. LastPass also does a security audit checking your password strength, age and if you re-used any. If it finds an issue it can automatically change a password on a lot of sites. I’m sure many others offer something similar, I just don’t have any experience with them.
Password managers are awesome but they are the keys to the kingdom. Your password to get into your manager needs to be excellent and you need to set up 2FA. You should also still use 2FA on all websites even though you’ve got some crazy auto-generated password from your manager. A complex, incredibly difficult to remember password isn’t any good if someone somehow gets it. 2FA helps in that situation.
Thanks! The password manager route has been on my mind for awhile. Very helpful advice!
Glad to help. 🙂 There are a lot of options when it comes to password managers so browse around a bit. I know, for example, that a lot of people love KeePass. This is something you’ll be using a lot so you want to make sure it’s something you like. Interface is super important.
Another cool thing with these is that they can typically import usernames and passwords you’ve stored in your web browser. What I did was import everything and then change them all … and then I shut off password storage in Chrome, etc, because it’s not as secure as it should be.
I used Lastpass until I noticed THEY were themselves hacked 3 times in 3 years. Although some gurus noted how quickly they recovered, I decided to go back to a notebook full of passwords!
LastPass has always addressed these issues publicly and has corrected them quickly. This shows a willingness to make the changes necessary to remain as safe as possible in an ever evolving threat landscape. The thing about software is it’s probably got some issue somewhere. Hell, it may be something that can’t be leveraged until some later date. A company being open and honest about this stuff is a good thing.
That said, if it turns you off there’s plenty of other options out there – including analog. The thing about a notebook, however, is that it’s still vulnerable to things like: being misplaced, being stolen, fire, water, coffee, your grandkid with a crayon, the dog, the cat … you get the idea. LastPass and other companies can address the threats to their product. Last I checked, Mead doesn’t have a loss proof, theft proof, overwrite proof notebook in development.
The main thing is to understand your attack surface. What sounds like a great option may be … but it also may just be something you haven’t fully thought about. Once you do you can make the best choice for you at that moment but that choice will still carry risk (but you understand it). Anything less is just guesswork and a prayer.
My solution to the notebook idea has been to use an encrypted LibreOffice spreadsheet. Then I still have the convenience of one password in conjunction with secure password storage on a USB dongle. I’m not a believer of storing passwords on the cloud when so many things on the ‘cloud’ get hacked regularly. The downside to this method is that you have to install LibreOffice on the devices you use the dongle on. However, since the loss of a version of LibreOffice that actually decrypts encrypted documents on Android, this method only works on PCs and Macs. Couldn’t comment on iDevices as all I have is an iPod…
Don’t use the max amount. If the max is 100, try 98 or 97. Why let someone know the number of characters?
What open source solutions are there for 2fa? And do any of those have any significant adoption?
Yes, there are open source implementations of TOTP and HOTP. There is quite wide use of these protocols.
There is also open source hardware implementations of U2F.
https://www.amazon.com/U2F-Zero/dp/B01L9DUPK6
Fido is an open standard and most likely the one to win out as it has support from big players.
Cool. Is there an open source hardware implementation?
Nevermind, I understand better now.
But, several websites that use Authy or whatever other “better than SMS” option, they have SMS as a fall back option.
Just today, I tried to log into google and it asked me to confirm yes on my phone to continue. Well, nothing happened when I clicked yes, so I clicked on the option to send me an SMS instead.
Doesn’t having that SMS fallback option completely negate the usage of the better options?
If there is a vulnerability in the SMS recovery system (like the one explained in this article), then yes.
Apple does the exact same thing. If I forgot my iPad or an iPhone at home, I can bypass the 2FA token system simply by hitting the “I didn’t get a passcode” button and receive a text instead.
All this sophisticated spy verses spy stuff. I’m still leery of the old fashioned fake link in the next “Krebs On Security” email. That would be an accomplishment that all real hackers would like to hang on their belt.
I think the holy grail of miscreant pranks would be to post a fake article here, with links to Goatse.
(If you’re too young to remember Goatse, don’t look for it).
Greg – when I get one of Brian’s interesting botmails, I open a browser and go to krebsonsecurity.com to read the latest message. I’ve just got a habit of not clicking on the links to anything. Yes, it’s awkward at times.
AT&T Wireless practically invites SIM fraud and number porting fraud by securing prepaid accounts with only a 4 digit numeric “passcode.”
AT&T doesn’t even send an SMS message to warn when someone incorrectly enters that “passcode” online or contacts their CS reps by phone.
While AT&T Wireless postpaid accounts can be secured by long passwords and a second security passcode, hijacking their prepaid accounts for SMS interception is trivially easy.
One big problem with App-based authentication is that there is always a chance of loosing access to the phone, e.g. if the phone gets damaged/lost/stolen, you forget your phone password (maybe because you don’t need it too often due to fingerprint login) or do a factory reset without thinking of all security codes on it or the phone wipes itself after a number of failed login attempts. For SMS-based authentication you can always get a new SIM/phone (via a legitimate SIM swap) and have access to your accounts again. For Hardware- or App-based security tokens this doesn’t work and so there needs to be some way of backup authentication / account recovery process, which can also be targeted by attackers.
For corporate accounts this can be solved by going to your administrator/IT department to recover the account. But for free accounts (Email, social networks, …) there is no support desk where you can walk in, identify using an ID card/drivers license/passport and recover your account. So they have to rely on automated processes – and these automated processes also have to cover a lost phone.
Authy for example offers the possibility to put a backup of your accounts in the cloud. This poses another risk of course, but deals with more likely risk of loosing access to your phone and thus accounts.
Apologies for the obvious question but what happens when someone steals your physical security key ?
Presumably there will be a period of time when they have total access ?
Then they also need to “steal” your password, as that is the other part of 2-factor authentication.
The factors referenced are:
* Something you know (for example the password)
* Something you have (for example the key, your phone etc.)
* Something you are (usually indicates biometric stuff, like your fingerprint, iris, etc)
So if it is just 1-factor where it is something you have, it can, just as you say, be stolen and they would have full access.
But 2-factor means that you need something else also to authenticate, usually something you know (a password).
Worth noting is that multiple cases of the same factor does not make it 2-factor. If you have multiple passwords to log in (for example a secret question or similar) or multiple devices that you have (for example a TOTP and SMS), it still means that you have 1-factor.
Kind Regards,
Henning
OK, but Brian states this in the article:
After a key is enrolled for 2FA at a particular site that supports keys, the user no longer needs to enter their password (unless they try to log in from a new device). The key works without the need for any special software drivers, and the user never has access to the code
So if you “no longer need to enter their password”, how is this now 2-factor? Can’t someone steal your device and use it, since you don’t have to use a password? Where do the “something I know” part come in?
@NK, well you should block your device with a pin / password / pattern / biometrics, etc. In that case if your device is lost or stolen the data you have on it is protected. You only use the 2FA when you first log in. If the device you are using is not private, then you should always logout.
Or, as we joke,
* Something the user forgot
* Something the user lost
* Something the user had amputated
Right now my favorite trade-off is Apple’s FaceID – fast, reliable, and reasonably high effort to bypass in most cases.
The government uses chip cards instead of keys and you need both a card and a PIN to access your account. A USB key solution should require something similar. So don’t attach a too easy to figure out PIN/password to the key and you should be good.
Well, this is the reason it’s two-factor- usually a password and the fob. Unless you’re the target of some really sophisticated and determined hackers, it seems unlikely that you’re going to have both the fob and your password stolen at the same time- so “total access” is unlikely in cases of what I guess we’ll call “casual hacking”.
Not sure what the recovery/deactivatyion method for these fobs is like, but one would hope they aren’t also vulnerable- because that would be the next place to be tested, and indeed traditional account recovery methods are often a route to breach.
Nonetheless, I find myself intrigued by the idea.
They would also need your password and userID.
Only if they also have access to a physical device that has already been authorized, or they also have your password. And in most cases, your physical device may have its own access control they have to get through- a pin, password, fingerprint, etc.
This is why nearly all sites also require a username + password in addition to the key. That is why mobile devices do not unlock with an NFC key – losing the key and mobile device gives full access. Getting to LastPass on the mobile device first requires the standard mobile device unlock sequence.
Most sites require you to enter a password as well as have the token. Sometimes it is only required for the first login from a new device.
Let me preface this by saying I’ve not done a lot of research into the physical key scenario. That said, I don’t think so. I believe initial logins on specific devices require the password and the key. So if you log into Facebook on your computer (let’s call her Susie) for the first time, you’ll need to enter your password and use your physical key. The next time all you’ll need is the key. Now some baddy steals your key, does that give them instant access to Facebook? No, because they don’t have Susie. They could put the key into their computer (let’s call him Hector) but they would still have to follow the same process you used for your first login on Susie.
Of course, they could use social engineering in a crazy coordinated attack to pull your password. They may have broken into your house and stolen not only your key but Susie as well. But, in that second scenario, you’ve protected Susie with a strong password and encrypted her drive, right?
What if “Susie” is a cell phone and Susie is stolen. There are hundreds of youtube videos on how to defeat, or bypass, the unlock screen of most cell phones. Encrypting the hard drive is not a cell phone option.
Cell phones are typically encrypted by default. I’m positive iPhones are. The same rules apply here: Set the best, most complex password you can and use whatever other tools are available to increase security.
Phones can definitely be brute forced but there’s some defensive measures you can take. There’s a default setting on iPhones, for example, that will wipe the phone if the password is entered incorrectly 10 times. If that’s not good enough you can always log into iCloud and remotely wipe it to be sure (assuming you get to that step before your account credentials are changed).
The point here is that nothing is perfect. There’s a risk to everything and there’s no magic pill to make it all better. The physical key is great unless someone somehow gets that and your password or that and your device. Using a token generated by an app on your smartphone is slightly less great because, as you pointed out, someone can get your phone and then they have the token (plus a lot more – like your email) but … there’s some other ways to defend after the fact. It’s knowledge that gives you the best chance. You have to know what can happen to understand what to do if it does – and that includes the worst possible outcome.
It’s called:
2FA = two factor authentication
MFA = multi factor authentication
2FA can be for example something you know and something you have. That would be for example your password + some device to authenticate you (mobile phone with an app or hardware token).
Therefore, to answer your question, unless they have your password as well the device itself is not almighty.
Hope this helps.
I would like to see a comparison between TOTP and a finger print. My iPhone of course uses the later but some banks are also using finger prints. It is easier to get my thumb out of my pocket than a key and I’m less likely to loose it. Is it more or less secure?
The trouble with a thumb/finger print is that it cannot be changed.
If someone took a print of your finger (E.G. From a glass you had touched), they now have a way of defeating your 2fa, and you cannot revoke it.
On the other hand (see what I did there?), if someone stole your token, you could just revoke it and buy a new token.
Chris,
There is a development towards biometric tokenization. This is the creation of a token based on the digital representation of your fingerprint. This may be the answer to the challenge you presented.
Nevertheless, I agree with you that using a more secure combination of factors (tokens, biometrics, OTP, etc) add layers to your security posture.
Another Chris 🙂 wrote: “Nevertheless, I agree with you that using a more secure combination of factors (tokens, biometrics, OTP, etc) add layers to your security posture.”
Programming today is a race between software engineers striving to build bigger and better idiot-proof programs, and the Universe trying to produce bigger and better idiots. So far, the Universe is winning. (Quote found on the Net)
Fingerprints, retina scans, DNA perhaps, hackers will try to circumvent these. As long as there is a challenge, someone will take it on. Multiple factor ID can help stop some bad guys. It might help limit social engineering schemes. But I suspect/expect that someone will find a way to circumvent parts of the roadblock we set up, a toe hold is all that they need.
As an aside, today I got a bunch of scam calls, not dead air hangs up, but actual voice mail, very unusual for my phone number. One stood out. The old, calling about your “credit account”, scam was replaced with a new version.
“…because we have been monitoring your accounts and your on time payments, you are eligible for rates as low as…” Looks to be engineered for people with good credit, they pay on time. Of course anyone could press “1” to speak to a live rep but perhaps they want people with good credit (higher $$$ limit) to take the bait.
Ironically it is true, they “are” monitoring our accounts, all our info is out there. The X Files got it all wrong, it’s not the truth that’s out there, it’s our personal info 😉
All kidding aside, the ‘other hand’ *is* a way to get past a stolen ‘thumbprint’.
Of course, you’ll have to remember to use the proper ‘thumb’ (or whatever digit you choose), from that point forward.
> Reddit didn’t specify how the SMS code was stolen
Apps with SMS access could have stolen SMS codes. Hackers would only need to access a site where the apps were uploading a copy of SMS messages.
Thanks for sharing such an informative post! To know more about cyber security visit the link: https://www.marlabs.com/digital/engineering/cyber-security/
Another great article, Brian! It would be nice if eBay (and others) paid heed to this and re-instituted some type of app-based 2FA in lieu of their current SMS-only option.
When it comes to estimating the level of unauthorized access and impact, I rarely believe the organizations who state this information (they almost always underestimate it). If my information is on those systems, I always assume worst case.
Who cares? Usa economy will collapse soon anyways !
So smart guys take what is left on the table b4 they close this restoraunt
Interesting. Good article as usual, and even some better comments, most unusual.
“But” as usual. People mistaking security thru math algorithms. Anything based on math can be be replicated. Sooner or later, someone is going to add the right number up, divided by the right number and your cloud is not safe again. It may be a little more complicated then that. But some people make monies by that method.
Tfa, is another branch to add into that equation. ,Interesting concept on backup key, don’t use it.
Someone breaking into anothers account aught to be punishable by law. Apparently, only international law, and if you are someone special. Otherwise it’s not a crime or an legal offense. Momma Jones won’t get helped, but poppa moneybags who got thair riches by stealing from the public is. Oh well.
Maybe I’m missing something, but wouldn’t it make more sense to demand better account security from the mobile providers?
Not only are they the weak link in the two SMS circumventions, but paying customers would be the ones doing the demanding, unlike free websites where users are the product.
Am I the only one disturbed that Reddit used TL;DR incorrectly?
How’s that? Didn’t they essentially use it as a synonym for “Brief Summary?”
Tl;dr should be at the end, not the beginning. And it really should be a sentence, not a convoluted paragraph.
Written correctly, it would be: “We don’t know why or how, but someone stole the portion of our user database created before 2007.”
One action I have taken to mitigate Sim Card hijinks is to require my cell phone provider to only do transactions for me at a physical store with my ID. Pretty sure I did that after reading about it on this valuable blog. Thanks, Brian! I have followed your wisdom for years, even back to your WP days.
U2F U2F U2F – did I mention U2F? Apps are okay but they’re a poor solution. My U2F fob sits neatly on my keyring, is supported by every browser that matters – is far more secure – and I have a backup fob in my water/fire resistant lock box for worst-case scenarios. Apps, SMS and anything else simply should be a thing.
Is a push to my smartphone where I press “Yes/No” and it sends the token back to the requestor more secure than entering a TOTP read from an authenticator app?
Reminds me on AuthPoint that was just released by WatchGuard.
I think it’s much safer, as they generate a fingerprint of your mobile device that carries the authentication app. In addition, you can configure it, that you can confirm ‘yes’ only by your fingerprint.
Also when something is going on, you are getting these push messages and can react on them, when it wasn’t you, who tried to log in.
I like it, because I don’t need to type the OTP….
Many many years ago when I had worked on the frontline team for one of the UK’s Mobile Service Providers. At the time or our training one of the group fraud team gave us a couple of hours of training in fraud and what to look for. We were actively encouraged to be paranoid.
At the time we used to aske for their password etc. and if we were not convinced we then performed a 3 or 4 point check. 4 point checks were requested when performing SIM swaps.
Unfortunately this level of paranoia as gone out of the window. Team leaders are no longer bothered as they do not measure this in their KPI’s
I lost my phone earlier this year. I used the Google authenticator app for Google, GoDaddy and LastPass. It was harder to remove the 2FA on GoDaddy than the other two. I would have thought LastPass would have made it very difficult.
Saw this on how to bypass 2FA. Not sure if this was used or not, but good to know how even 2FA can be bypassed if used improperly.
https://youtu.be/xaOX8DS-Cto
This is why I find quantum cryptography so fascinating. Once/if it takes hold, it will change the world of encryption and multifactor authentication. While there is no perfect solution for multifactor authentication – the quantum route has to be as close to perfect as possible. It’s a shame that bringing this technology into the mainstream is years away. It would be interesting to get Brian’s take on this.
The article doesn’t address another attack vector: Man-In-The-Middle.
Getting a key code by text message provides no protection from MITM attack. Here’s how the attack works:
1. You get an email from your bank instructing you to log in, a link embedded in a social media page.
2. Your browser is misdirected to the Bad Guy’s web server, where you are presented with an exact replica of your bank’s login page. The web address will appear very similar in your browser location window: something like mybank.co instead of mybank.com. If the Bad Guy uses good tradecraft, his site will even have a good SSL certificate and appear to be secure to your browser.
3. You type your user name and password. The Bad Guy passes both to your bank’s legitimate login page, and then changes his web page to an exact replica of your bank’s key challenge page.
4. Your bank sends you a text message with a 6 digit key. Since you are still on the Bad Guy’s key challenge page, you type in your 6 digit key there.
5. The Bad Guy sends your key to your bank. Now he is in, masquerading as you.
6. Meanwhile, he performs a “cut-through” proxy connection directly to your bank – which has authenticated your connection – and everything looks completely normal to you.
7. The Bad Guy hijacks the same session to empty your bank account.
8. Done.
Yes, it does:
Technically, 2FA via mobile apps and other TOTP-based methods are more accurately described as “two-step authentication” because the second factor is supplied via the same method as the first factor. For example, even though the second factor may be generated by a mobile-based app, that one-time code needs to be entered into the same login page on a Web site along with user’s password — meaning both the password and the one-time code can still be subverted by phishing, man-in-the-middle and credential replay attacks.
Here’s a far simpler exploit: How to crack Google SMS Auth with only a phone and a web browser.
Anyone can exploit the vulnerability. They can gain unauthorized access in the context of the victim to the full range of Google services. Spoofing Caller ID for unauthorized access to victim voice mail is a very old and well known exploit. Since Google will deliver SMS auth codes by voice, and Google does not detect delivery to voice mail, attackers can easily access those codes.
1) You will need the victim’s Google user name, Google password, and cellphone number.
2) Wait till 4 AM when you are sure the victim won’t answer their phone.
3) Log into Google using the victim’s user name and password. When the two step auth delivery screen appears, select other delivery options.
4) Select delivery by voice to the victim’s (already-stored-by-Google) cell number.
5) Call the victim’s cell number spoofing their own number in the caller-ID (there are multiple services, such as Spoof Card, to do that for you).
6) Their cell phone provider will respond as though you were calling from their own cell phone. The vast majority of cell users are too lazy to configure their voice mail to require a PIN to access their voice mail from their own phone.
7) Listen to Google read off their 6 digit pin.
You’re in!
User countermeasure: Configure your voice mail to require your PIN even when calling from your own phone. Don’t be lazy. (Alas, most people are lazy.)
Google countermeasure: devise a way to not disclose Google Auth PINS to robots (voice mail). Such as, make the person press a key before the delivery is accomplished: “Please press 1 to receive your key.”
I learnt NOT to use Google Authenticator the hard way, when I wanted to back up my codes prior to erasing my phone and rooting it.
The short version is: you can’t! You cannot sync the codes with your Google Account, you cannot export them and you cannot save them via the usual ADB backup procedure.
Your only hope is that you have a rooted phone or you printed backup copies of the QR codes. I now use Authy with encrypted backup and sync and it’s much better.
It is by design. Less convenient, more secure.
Yes, the onus is on you to backup a screenshot of those qr codes. etc in a secure location, like safe deposit box.
One thing Google should do is be more obvious and explicit to people that they may want to do this. It is indeed a pain to find out the hard way, as I also did, but going forward, I just modified the new add process by taking screen shots, printing those out, and storing them in my safe deposit box. Simple, fixed, the most secure TOTP solution is implemented by Google Authenticator vs. Authy.
Security is all about trade-offs… generally, the more secure something, the less convenient, no different here.
the authentication gives us the surety of the protection. the stuff is very much informative. keep sharing these type of ideas.