Unsettling new claims have emerged about Nicholas Truglia, a 21-year-old Manhattan resident accused of hijacking cell phone accounts to steal tens of millions of dollars in cryptocurrencies from victims. The lurid details, made public in a civil lawsuit filed this week by one of his alleged victims, paints a chilling picture of a man addicted to thievery and all its trappings. The documents suggest that Truglia stole from his father and even a dead man — all the while lamenting that his fabulous new wealth brought him nothing but misery.

The unflattering profile was laid out in a series of documents tied to a lawsuit lodged by Michael Terpin, a cryptocurrency investor who co-founded the first angel investor group for bitcoin enthusiasts in 2013. Terpin alleges that crooks stole almost $24 million worth of cryptocurrency after fraudulently executing a “SIM swap” on his mobile phone account at AT&T in early 2018. Terpin also is pursuing a $200 million civil lawsuit against AT&T in connection with the theft.
Authorities arrested Truglia on November 14, 2018 on suspicion of using SIM swaps to steal approximately $1 million worth of cryptocurrencies from a different Silicon Valley executive. But Terpin’s civil lawsuit (PDF) maintains that evidence was revealed at Truglia’s bail hearing that he had texted his father and multiple friends to brag about the $24 million hack on the day of Terpin’s theft, allegedly offering to take friends to the Super Bowl with “porn star escorts.”
Terpin’s lawsuit includes a large number of supporting documents, including an affidavit filed by Chris David, a 25-year-old New York City resident who claims to have been an acquaintance of Truglia’s until he began to unravel the source of his new friend’s overnight riches.
In his affidavit (PDF), David describes himself as a self-employed private jet broker who met Truglia in a fitness center attached to Truglia’s luxury apartment building. Truglia allegedly struck up a conversation about booking private jets with his cryptocurrency. When the two met again a few days later, David says Truglia showed him accounts on his mobile phone and computer indicating he had over $7 million in cash in a JP Morgan account and more than $12 million in various cryptocurrencies.
“At the same time, Nick showed me two thumb drives (Trezors),” David recounted. “One had over $40 million in cash value of various cryptos, and the other one had over $20 million cash value of various cryptos.”
David said Truglia initially explained his wealth by saying he’d made the money by mining cryptocurrencies, but that Truglia later would admit he stole the funds.
“Over the next few months, Nick and I socialized at nightclubs, local bars, the gym, and in his apartment playing video games,” David recounted. “Gradually, I got to know Nick. He does not have a job or visible means of support. His typical day is to get up late, go to the gym, eat at the deli across the street, play video games late into the night and he had no friends. Nick was an egotistical braggart about his life and wealth. For example, once at a crowded lounge, he said: ‘Chris, I have more money than all of the people here tonight.'”
David started documenting Truglia’s activities after he and several of his friends were arrested for allegedly stealing Truglia’s laptop, mobile phone and Trezor drive. That incident, recounted in this New York Post story and in David’s own testimony, indicates that Truglia later recanted the accusation and chalked it up to confusion resulting from a heavy night of drinking.
According to David, when Truglia wasn’t bragging about his wealth he was displaying it openly: He lived in a $6,000 per month apartment, wore a Rolex watch which he claimed cost $100,000, and boasted he was going to purchase a $250,000 McLaren sports car. David also said he recorded conversations with Truglia in which the latter admitted to stealing $24 million from Terpin.
David said he even witnessed Truglia attempting a SIM swap at a Times Square AT&T store in August 2018. Here’s David’s account of that hijack effort, which allegedly failed when Truglia declined to pay the target’s overdue phone bill:
The affidavit states that later in the month David took screen shots of a now-defunct Twitter account that Truglia allegedly used (@erupts), which included six different messages about what the theft of $24 million had wrought.
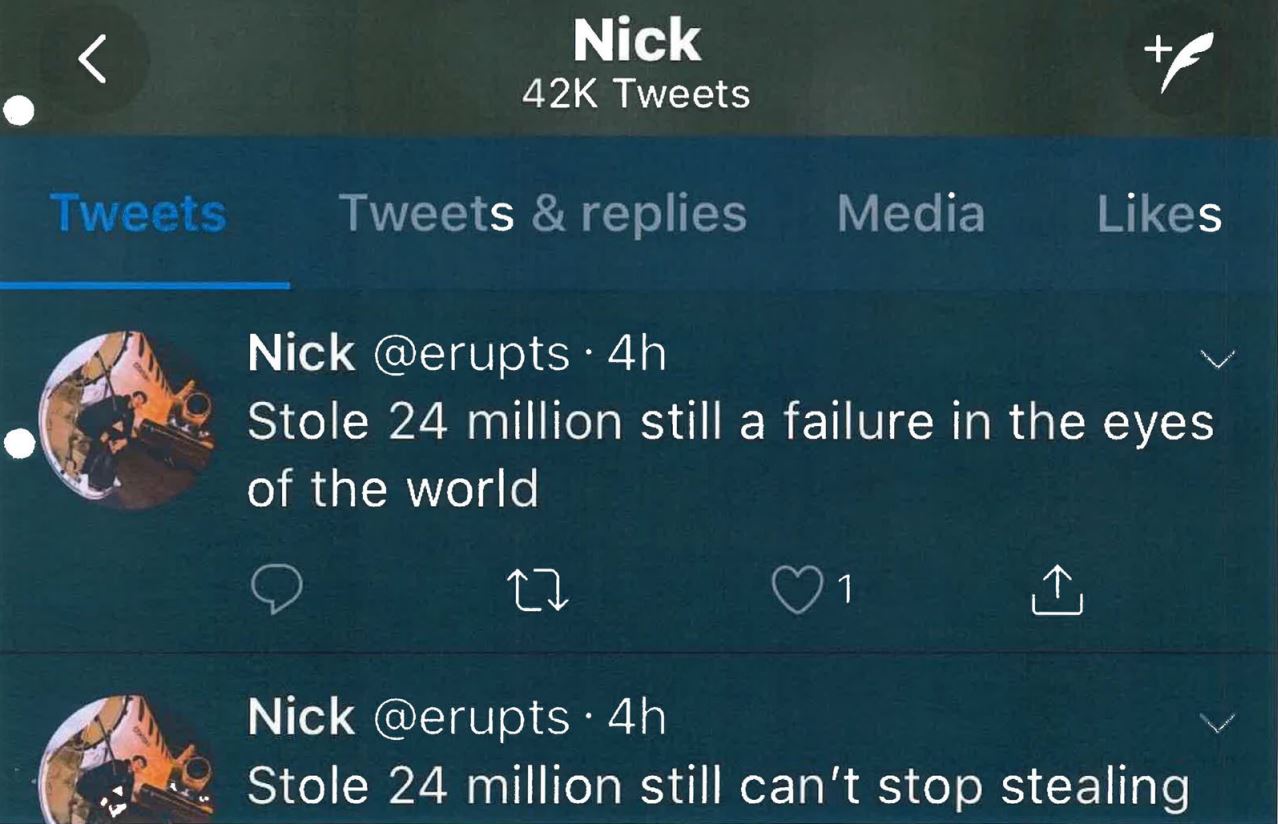
Tweets from the account @erupts, allegedly penned by Nicholas Truglia.
“Stole 24 million but still can’t keep a friend,” reads another tweet allegedly tied to Truglia’s account:
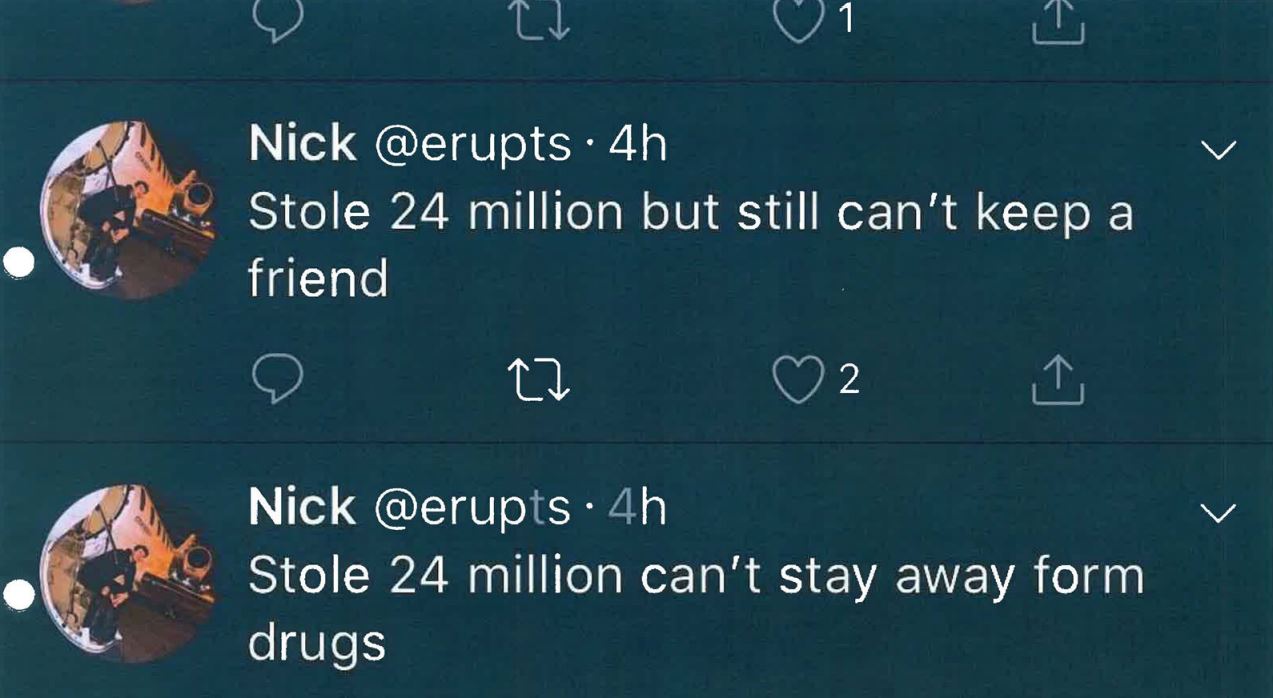
David says Truglia even acknowledged stealing $15,000 after hacking into his own father’s accounts. According to David, Truglia’s dad asked to be repaid, and that his son agreed to return the money — but in bitcoin. In the image below — which David claims was a screenshot he took of a mobile phone chat conversation between Truglia and his father — the elder expresses mystification and frustration about how to complete the transaction.
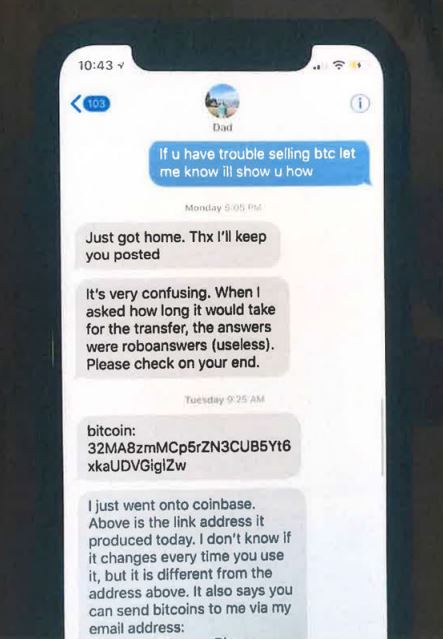
A screen shot David says he took of an alleged chat conversation between Truglia and his father regarding repayment of $15,000.
In the affidavit, David also testifies that he saw Truglia in possession of a fake New York State driver’s license which had the name and identifying information of a deceased man named Quentin Capobianco, but with Truglia’s photo on the license.
A copy of this phony drivers’ license was documented by investigators with the Regional Enforcement Allied Computer Team, or REACT — a task force in Santa Clara, Calif. that is almost singularly focused on tracking down criminals who use unauthorized SIM swaps to steal virtual currencies (for a deep dive into the workings of the REACT Task Force, see my November 2018 story, Busting SIM Swappers and SIM Swap Myths).

David said he took this photograph of a license Truglia had in his possession; the license includes Truglia’s photograph but the information of a dead man that Truglia allegedly SIM swapped.
That REACT Task Force investigation report (PDF) was included in Terpin’s lawsuit, and it lays out how detectives tied Truglia to SIM swaps that allegedly gave him access to Capobianco’s accounts at Coinbase, a virtual currency trading and purchasing platform.
David testified that despite Truglia’s ill-gotten riches, he was constantly borrowing small amounts of cash and was otherwise tight with his money. Much like David’s testimony, a related memo (PDF) filed by REACT Detective Caleb Tuttle suggests that Truglia was in the process of being evicted from his pricey Manhattan apartment because he refused to pay his rent.

A snippet from a memo filed about Truglia by REACT Task Force Detective Caleb Tuttle.
Truglia is currently being held by Santa Clara authorities on a $1.4 million bond. His next court date is April 10. Neither Truglia nor his attorney could be immediately reached for comment. Members of the REACT Task Force declined to comment for this story.
A SIM card is the tiny, removable chip in a mobile device that allows it to connect to the provider’s network. Customers can legitimately request a SIM swap when their existing SIM card has been damaged, or when they are switching to a different phone that requires a SIM card of another size.
But SIM swaps are frequently abused by scam artists who trick mobile providers into tying a target’s service to a new SIM card and mobile phone that the attackers control. Unauthorized SIM swaps often are perpetrated by fraudsters who have already stolen or phished a target’s password, as many banks and online services rely on text messages to send users a one-time code that needs to be entered in addition to a password for online authentication. However, many online services let customers reset their password merely by using their mobile phones.
All four major wireless carriers — AT&T, Sprint, T-Mobile and Verizon — let customers add security against SIM swaps and related schemes by setting a PIN that needs to be provided over the phone or in person at a store before account changes should be made. But these security features can be bypassed by incompetent or corrupt mobile store employees.
For more on ways to minimize your chances of becoming the next SIM swapping victim, check out the “What Can You Do?” section at the conclusion of this story.





“Money doesn’t buy class.”
Money does make one more of what they already are.
Why does none of this surprise me….
Another miscreant who deserves every bit of hard time handed down, but who should also have the key to his cell’s door thrown away (or irrevocably deleted if it’s a modern electronic version) for his criminal assholiness.
Well Said my friend well said
Well said
He will have plenty of friends in jail now.
In before someone says we should be hiring this guy to help us secure our SIM cards or some other such nonsense.
The problem here isn’t a lack of security policies by the mobile operators. The problem is that employees of those operators routinely ignore those policies. Either they’re incompetent, stupid, or corrupt. I don’t know which and I really don’t care.
In this case, the guy convinced an AT&T employee to perform a SIM swap based entirely on a phone number and a phished PIN. The employee asked to see the account owner’s ID, but somehow decided that the ID for somebody else was sufficient.
This is no different from a bank teller closing your account and giving the money to a total stranger simply because he knew your account number.
The difference is that there are laws preventing bank employees from doing this, but there are (apparently) no such laws preventing mobile operator employees from the same thing.
This problem with SIM swapping won’t end until mobile operator employees start going to prison for “mistakes” like this.
I very much doubt sending the smallest fry to jail will be all that’s required. The carrier needs to be held accountable too. They’re the ones responsible for training the field tech and putting sufficient road blocks in place. There are any number of ways having a third party (meaning someone not in the store) implement the change after the customer service rep provides sufficient documentation and information. Socially engineer the rep all you want, the person on the phone isn’t going to budge until they’re given the correct amount of information because that’s their job, and good luck trying to slip them $20 through the phone.
You are such an entitled asshole. You realize that the people working these stores are paid next to nothing right? Now you want to send them to prison? Why the fuck should they care about some rich assholes SIM card?
So being paid “next to nothing” makes it OK to break the law & help someone steal from someone else?
Yes he is entitled to have employees follow the policies and procedures put in place to safe guard against these types of takeovers.
He got his name added to the account.
The store clerk in that instance wouldn’t have done anything wrong. The failure is where-ever he managed to get his name added. Possibly by phone / online.
—-
Fwiw, additional names on accounts aren’t uncommon. Even barely related.
My first cell phone line was part of a distant relative’s account because I didn’t have enough of a credit record to get my own. Thus their name and my name were both initially on the account. After I built sufficient credit history w/ the provider (Cingular), I removed their name from the account.
It’s also common for families (see “family plans”). Or businesses w/ multiple authorized managers/users.
The whole phone account management system is actually pretty weak. It’s based almost entirely on trust.
—-
My favorite example was divorcing my account from an account w/ thousands of other users/lines at a basic kiosk like store. It was amusing watching the poor system struggle to merely open the account. I was authorized to take my line out of the system, but I don’t think there was much protecting the system from me or someone else removing a different account (possibly not their own).
Nice he went from a $6,000 per month apartment to a jail cell, what a fall from grace.
$24 million +
But he never used a gun to steal it…
In my state, he gets 3 months, tops, with 40 years to repay the money, at zero interest; (many prior cases).
In my state, use a gun to steal $3.19, it’s 20 years to start.
Electronic theft, a growth industry.
I wonder why…
No one has ever murdered someone or held up a liquor store with a SIM card or a Trezor. Or Ledger Nano S.
Phil, I know you and I must be in some level of agreement on this: cyber crime does real world physical harm.
One of the most important institutions that has allowed this nation to be successful is property rights–this behavior is a direct affront to that most important institution and it should be punished as such.
Consider horse thieves during the westward expansion. You may have sneaked off with the horse without any sort of threat or physical interaction with the victim… but you may have sentenced your victim to death by the elements nonetheless by depriving them of their property.
Now consider that you manage to cyber-swipe a portion of someone’s savings in crypto. What may that victim be deprived of now? It could be a trip to Barbados… or it could be the roof over their heads.
I do not advocate for capital punishment (as horse thieves were once dealt with), but I do believe that there is much room for improvement when it comes to proportional punishment for cyber-criminals. And I think that is similar to the point that Blanche is trying to make.
Hence why in the old West, they hung horse thieves…
You know this for a fact or is that just your opinion?
Leonardo Decaprio needs to make a dope movie about this.
Why would anyone want to watch a movie of a kid playing fortnite and being an arrogant asshole?
lmao
Guy(s) … there IS no “What Can You Do” section “at the conclusion of this story.” You CAN click on the words ” at the …” which is a hyperlink to another story apparently called “hanging up on mobile in the name of security” which is NOT the same thing as a “What Can You Do” section. May I suggest an edit for clarity here? Otherwise LOVE your work. Alley
Made perfect sense to me. It is talking about the “What Can You Do” section at the end of the story it is linking you to. Click on the link, then scroll down a few paragraphs.
I followed the advice of that article when it first came out and switched my 2FA from my phone to a new GV number tied to a new gmail account that is protected with a Yubikey.
The hard part was changing all of my accounts over. One bank locked me out for several days while they conducted manual verification. Another locked my account and opened a fraud investigation. The investigator called me but I didn’t answer because I didn’t recognize the number. However, I did get a voice mail and eventually connected with the fraud investigator to verify my identity and release the account. I also had a chance to school him on SIM swapping.
Now everything seems to be working except for one bank that won’t send 2FA to a GV number, but they allow email verification so I use that instead. The email account is protected with an authenticator app.
Other than that, it is important to use unique strong passwords using a password manager that is also protected with a Yubikey. I think it is a premium (paid) option only. Otherwise, you can use authenticator app.
In the end, it was a bit of a hassle and took about a week to move everything off of my cell phone, but I feel much safer now.
A PIN to prevent SIM swaps or account changes isn’t an option for many prepaid cellphone accounts.
Oh, and Mr. David sounds like a Grade A douchebag, recording and photographing his friend and snitching him out.
It sounds like Mr. Truglia was playing pretend. A con artist, for sure, and a lowlife. But no mastermind here.
Nothing in this story indicated that the intangible millions were recovered or that there’s real evidence the magical crypto funds actually existed in the amounts claimed.
Just the word of a snitch and Mr. Terpin who’s sad his Ponzi scheme’s fake money went poof.
I’m always struck by those who call out “snitches” – you’re basically saying you’re in support of criminals remaining criminals. I applaud David and hope all criminals consume each other rather than victims.
Friendship requires acceptance and compassion for the imperfections of our friends, even if they’re criminals. Snitches pretend to be friends.
A good friend demands penance, restitution, honesty, and integrity. A good friend will offer, “Stop it now and I’ll stick with you, even if you’re caught and wind up in jail.” A good friend will keep your dirty secrets, even while trying to help you be better.
A snitch doesn’t want the crimes to stop. A snitch doesn’t care about you or victims. All they care about is the anticipated satisfaction of having authorities listen to their stories. And cash rewards.
Yes he messed with the Wrong People.
and also he Got greedy.
IF You steal from Rich That’s big mistake.
but IF You make like construction company and Don’t pay Even to your cheap Workers, then That’s Fine.
as longes You Don’t steal from Rich You Will be Good.
Definitely had some social issues. An extreme introvert. Didn’t fit in. These are the types that seem to run afoul of the law more often than not.
But can he be charged with theft of finance if it’s not a recognized currency? hacking yes, tax evasion yes, steeling money from his dad yes, fraud yes. Steeling millions of crypto currency – bah. If they do, they should bust everyone with it for tax evasion.
Where is thee CIA?!?! This is a threat to National Security. If these 21 year old kids can call phone carriers and get your personal cell phone number ported over to a device in their control so can Murders and Terrorist.
Someone can sim swap you, text your Parents or loved ones from your number and have them meet in some back alley and Assault them.
Terrorist can Sim Swap innocent civilians and Government Officials and do God knows what with those phone numbers.
THIS IS A THREAT TO NATIONAL SECURITY!!!
The FBI handles criminal investigations foreign and domestic. The CIA handles foreign intelligence operations. Not criminal investigations.
It’s not inconceivable for the government to maintain the belief that crypto currencies are real money in a property crimes case, while also ignoring crypto currencies for tax cases.
It wouldn’t be the first (or last) time government was inconsistent.
Example one:
Kill a pregnant woman in (most of) the US, get charged with double murder.
Punch a pregnant woman, she lives, baby dies, get charged with assault and manslaughter (at a minimum).
But if she underwent an abortion, she wouldn’t be charged with assault or murder, because of R vs. W privacy rule. (Really).
Example two:
Kill a cop in anger, get murdered by the state.
Kill your spouse in anger, only get 25 years.
(^As Animal Farm taught, “All animals are equal, but some animals are more equal than others.”)
Another example:
This month, a US magistrate ruled, “Biometrics and passcodes serve the same function,” so a warrant is required in order to force a defendant to open a smartphone.
But prior to this ruling, some judges didn’t require warrants for biometric locks, distinguishing them from passcodes, even though the goal was the same (getting access to phones).
Logical inconsistencies, all.
It might just be me, but the text on that photo of the iMessage convo looks fake/altered…
I’m also wondering how much of his story is legit and what parts have been embellished. I feel like that is the case with braggarts like him often when looking at their claims on social media. Boasters boast, or at least in my opinion the real threats walk quietly with their big sticks.
Brian:
> … which David claims was a screenshot he took …
Is that use of “screenshot” normative?
I’d have expected “snapshot” or “photo”.
Thanks for asking the world’s least important question.
It says “In the IMAGE below — which David claims was a screenshot”
A “screenshot” doesn’t use a camera, hence not a photo or snapshot. It is a digital image of the screen being used by the device (in this case a mobile phone) captured internally by the device itself—but not using a camera to take a picture.
2FA sort of works. Why not use a similar technique with the SIM swap scams? Require all account changes to be authorized by a second party on the account, preferably the main holder. Or maybe make a phone call at least, to the main account holder. It’s up to the cell phone companies to implement better security for these SIM swap scams.
I also recommend that two separate devices be used for 2FA. Don’t log into PayPal with your smart phone and then turn around and use that same smart phone for the 2FA whether it be SMS, email, Auth app, etc…
I am rather perplexed by this story. I have several accounts with crypto exchanges and all use Google Authenticator for 2FA with the exception of one that uses Authy. I’ve never been given the option for SMS 2FA. The theft referenced above apparently occurred in early 2018.
Can Brian (or anyone) please explain how it’s possible for Mr. Terpin to use SMS 2FA at a time when exchanges were using app-based 2FA?
As always a great read!
I commented on twitter but didn’t really get a response: https://twitter.com/4mroot/status/1087379584209678337.
I just want to note that switching to Google Voice for 2FA removes the “something they have” part of 2FA and only requires an attacker to obtain the “something they know”.
The “773M Password ‘Megabreach’ is Years Old” is a great example poor password choices and password reuse. If those accounts don’t use a physical device for 2FA then there is no need to attempt a SIM swap because the attacker already obtained the “something they know” piece.
I hope this helps some random reader out there. Thanks!
Except the biggest weakness with the mobile providers is their customer service people can and are being tricked or bought into assisting these fraudulent SIM swaps. That weakness simply doesn’t exist with Google Voice, which combined with strong 2FA (like a Security Key, which is something you do have) and a strong passphrase is pretty good and a damn sight better than just relying on the big mobile companies to give a darn.
mEsOsORRYyO my english a no go.
Dave that whom suggested there should be another form or 2FA to prevent SWAMPsim which HeLLoOOo wait i forget you guys are and just got your joke. good one
and wait the guy talking about a killer simswapping text a family member to kill them and the if the terrorist caught on to the this.
that was too right? sorry english humor gets lost in translation cause talk but talk
Either or you guys gunny AF.
2FA 2 stop SS LMAO so silly cause 2FA heck all of existence revolves was sim get to go raw dog on the celli.
But herea thought why not have these ATT gemps just follow the protocols and CHECK IDENTIFICATION as that mc lovin ID was super bad bin laden bad.
Just as bad as that rat/snitch of B*TCH DAVID lil HATER of a “Friend” that nikled and dimed n dropped the dime so hes scaming sim swapping could do 5 years tops hoping never to drop that soap.
noHAhomo which he kid more then likely be the theatrics attention seeking (IM ON TO TALK RIGHT?) drama queen emo rant on $40 mill no friends no cause sure he looking for boy like a boyfriend probally had a thing for DAVID but who doesnt? 😛
So anyways to Mr K or or the drama queens them over r.e.A.C.T.’er
them under paid AT&T rep was im om too or was paid to look the other way. Which is way Keyser Soze aka DAVID name droppped it and now that i think DAVID is THAT DOODer for sure…
Brovo Sir Bravo! Havent read the MEMO just going on BKk’s writing.
So David’ has a bigger role then clueless hatting snitch so he a master mind Kaeer Soze or hes as scandalous F’d up pedo actor Kevin Spacey
DAVID done had a lot a dirt on the dood. Documented Dirt like crustal key almost strategical “Kaiser Soze” evidence dirt so David can not be clean with all that dirt
So st. nick was desperate for a friend or had a broner for DAVID so NICHOLAS started working with DAVID amd started showing him the ropes.
Why DAVID didnt care for the guy but bared FLOM
lol why isnt there a charaacrter limit on the comments huh KB?
well im on one and lost one so ill go back to U+1F910
Your spelling, grammar, syntax, cadence, and slang betray you.
These aren’t the usual suspects.
Strangely this is also why you don’t use swipe technology especially creditcards that allow this. If you can tap and go imagine someone in a drive by with a scanner that can swipe your card and go.
More technology that gets introduced the more pains of preventing problems crop up. It is an endless cat and mouse game.
I’m sure some lawmaker is running this story to stifle crypto currencies at large. Underpinning it to the darkweb eyecandy and drugs.
Another interesting example you can now buy legal marijuana, which unfortunately used to be outlawed once. Funny times we live in.