Google this week made it easier for Android users to enable strong 2-factor authentication (2FA) when logging into Google’s various services. The company announced that all phones running Android 7.0 and higher can now be used as Security Keys, an additional authentication layer that helps thwart phishing sites and password theft.
As first disclosed by KrebsOnSecurity last summer, Google maintains it has not had any of its 85,000+ employees successfully phished on their work-related accounts since early 2017, when it began requiring all employees to use physical Security Keys in place of passwords and one-time codes.
The most commonly used Security Keys are inexpensive USB-based devices that offer an alternative approach to 2FA, which requires the user to log in to a Web site using something they know (the password) and something they have (e.g. a one-time token, key fob or mobile device).
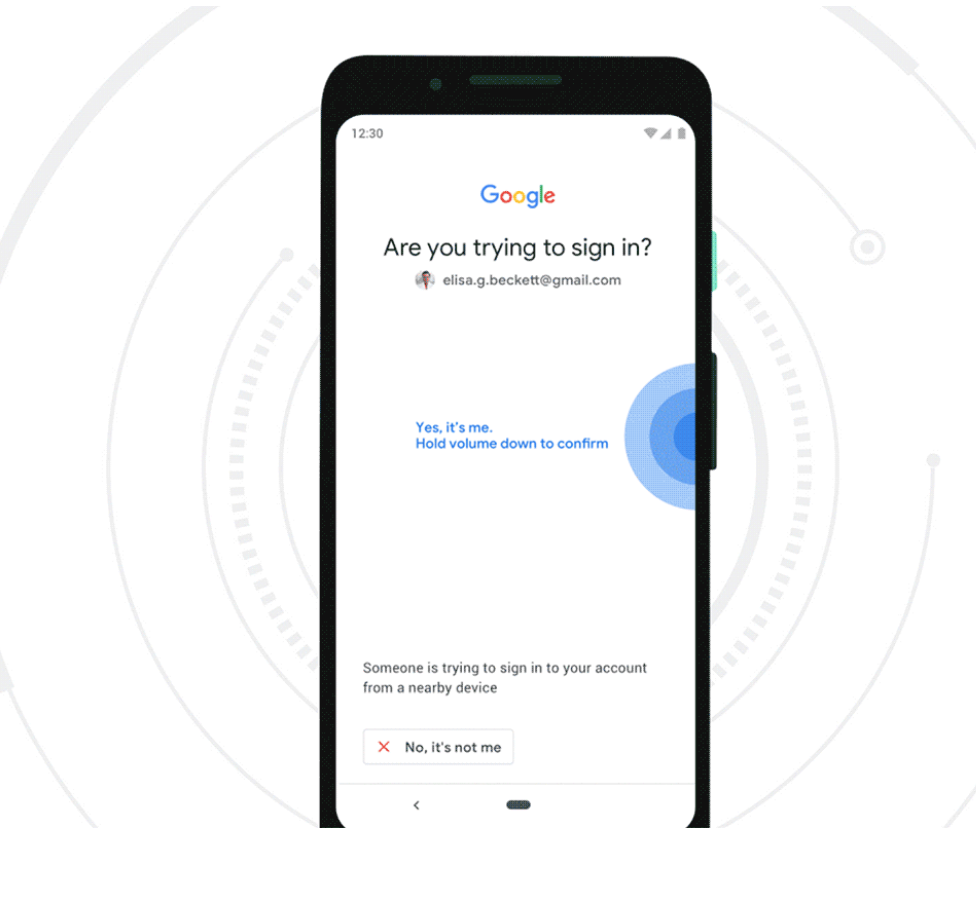
But Google said starting this week, any mobile phone running Android 7.0+ (Nougat) can serve the same function as a USB-based security key. Once a user has enrolled their Android phone as a Security Key, the user will need to approve logins via a prompt sent to their phone after submitting their username and password at a Google login page.
Many readers have expressed confusion or skepticism about how Security Keys can prevent users from getting hooked by phishing sites or clever man-in-the-middle attacks. This capability was described in far greater visual detail in this video last year by Christiaan Brand, product manager at Google Cloud.
But the short version is that even if a user who has enrolled a Security Key for authentication tries to log in at a site pretending to be Google, the company’s systems simply refuse to request the Security Key if the user isn’t on an official Google site, and the login attempt fails.
“It puts you in this mode….[in] which is there is no other way to log in apart from the Security Key,” Brand said. “No one can trick you into a downgrade attack, no one can trick you into anything different. You need to provide a security key or you don’t get into your account.”
Google says built-in security keys are available on phones running Android 7.0+ (Nougat) with Google Play Services, enabling existing phones to act as users’ primary 2FA method for work (G Suite, Cloud Identity, and GCP) and personal Google accounts to sign in on a Bluetooth-enabled Chrome OS, macOS X, or Windows 10 device with a Chrome browser.
The basic idea behind two-factor authentication (Google calls it “two step verification” or 2SV) is that even if thieves manage to phish or steal your password, they still cannot log in to your account unless they also hack or possess that second factor.
The most common forms of 2FA require the user to supplement a password with a one-time code sent to their mobile device via an app (like Authy or Google Authenticator), text message, or an automated phone call. But all of these methods are susceptible to interception by various attacks.
For example, thieves can intercept that one-time code by tricking your mobile provider into either swapping your mobile device’s SIM card or “porting” your mobile number to a different device.
A Security Key implements a form of multi-factor authentication known as Universal 2nd Factor (U2F), which allows the user to complete the login process simply by inserting the USB device and pressing a button on the device. The key works without the need for any special software drivers.
Probably the most popular maker of Security Keys is Yubico, which sells a basic U2F key for $20 (it offers regular USB versions as well as those made for devices that require USB-C connections, such as Apple’s newer Mac OS systems). Yubikey also sells more expensive U2F keys designed to work with mobile devices.
A number of high-profile sites now allow users to enroll their accounts with USB- or Bluetooth-based Security Keys, including Dropbox, Facebook, Github and Twitter. If you decide to use Security Keys with your account, it’s a good idea to register a backup key and keep it in a safe place, so you can still get into your account if you loose your initial key (or phone, in Google’s case).
To be sure you’re using the most robust forms of authentication at sites you entrust with sensitive data, spend a few minutes reviewing the options at 2fa.directory, which maintains probably the most comprehensive list of which sites support 2FA, indexing each by type of site (email, gaming, finance, etc) and the type of 2FA offered (SMS, phone call, software token, etc.).
Please bear in mind that if the only 2FA options offered by a site you frequent are SMS and/or phone calls, this is still better than simply relying on a password to secure your account.
I should also note that Google says Android 7.0+ phones also can be used as the Security Key for people who have adopted the company’s super-paranoid Advanced Protection option. This is a far more stringent authentication process for Google properties designed specifically for users who are most likely to be targeted by sophisticated attacks, such as journalists, activists, business leaders and political campaigns.
I’ve had Advanced Protection turned on since shortly after Google made it available. It wasn’t terribly difficult to set up, but it’s probably not for your casual user. For one thing, it requires users to enroll two security keys, and in the event the user loses both of those keys, Google may take days to validate your request and grant you access to your account.




Let’s be honest, a Security Key is cool and all, but I have two words for Apple: Headphone. Jack.
No thanks, I stick with using “Authy” with my accounts.
I have seen two articles on this, both discuss how the tech works and what it is supposed to combat, but neither discuss how to actually set it up in the phone. A little more detail please.
Google it 🙂 But yeah, would be nice not to have to. Meanwhile, see:
https://support.google.com/accounts/answer/6103523?co=GENIE.Platform%3DAndroid&hl=en
There’s a link in the article to the “how” part
https://www.blog.google/technology/safety-security/your-android-phone-is-a-security-key/
Got it, thanks
@brian @ArnarBirgisson (if you are reading this) and others who dare to try:
I just set this up on an Android 7.1.1 phone and the experience was a *(near) disaster.*
Following the simple instructions on Birgisson’s post mMaking the phone a security key is easy, however:
1) The setup DOES NOT VERIFY that using the phone as a security key *actually works* before committing this factor to the account.
And in my case it DID NOT work and would not prompt my phone when attempting to reenter my account. This was the case tested on two separate devices (Win10 and ChromeOS), both with bluetooth on and my phone BT paired to the devices.
2) WORSE, having previously set my phone as a security key, when the prompt did not happen the ONLY option was to login with a physical security key. There was no presented option to login via Google Authenticator or manual security codes.
Restarts, re-pairing, toggling BT on and off while attempting PC-based logins failed to change the fact that I could not authenticate.
Making the phone a security key is not “an additional authentication layer” it REPLACES everything else.
Rereading Birgisson’s blog post it not clear that having a physical/USB security key is either required or should be done before making the phone a security key. Furthermore, the Google account security 2FA configuration itself doesn’t prompt/warn/or require this. Nor does it warn that TOTP/Google Authenticator/manual recovery codes will no longer work.
At this point panic was begining to settle in!
Luckily my phone was still logged in to my account, even after my restart. From there I was able to get into my account security settings (duly tested to enter the TOTP) and thankfully remove the phone as a security key.
Google, this dangerous feature needs to be fixed!
Before using my Titan security keys, on my Pixel 2 XL, I was using the phone as my primary authentication device for all things Google.
I’m not sure where you went wrong in the process, but Bluetooth has absolutely *NOTHING* to do with this setup – it uses your Google account, and push notifications, to your phone – no matter if you are right next to the device that you are attempting to authenticate to or 9000 miles from (which I can verify, as one of my Google accounts is continually attempted to be reset by users in India (yes, I’m Indian, and the attempted account PW resets come to my phone showing me where the attempt was made from), and it does not matter if I am beside my computer, or traveling in California 3000 miles from my computer.
The need for the security keys is only mandatory if you are enable the Advanced Protection program, and if you go to their web page on that program, https://landing.google.com/advancedprotection/ it *clearly* states that you need a pair of security keys.
“The strongest defense against phishing with a Security Key
Even the most security-conscious users can be tricked by a sophisticated phishing attack. To protect you from this threat, Advanced Protection goes further than traditional 2-Step Verification, requiring you to use a physical Security Key in addition to your password to sign in to your Google Account.”
Again, I’ve been using my phone as my primary method of authentication for my Google accounts (not Google Authenticator, not Authy, no 3rd party apps – straight from my Google account) since it was made available for any and all of my Google accounts (including multiple G-Suite accounts, whose domains I administer, so multiple accounts across 4 different domains) for a long time – not sure when, exactly it started, but if I am honest, I’m pretty sure I was using it on the device previous to this Pixel 2 XL, which I purchased in Oct 2017, so, there is that. However, the image showing in Brian’s blog is not anywhere near what I am seeing, I’ve always had a “yes” and “no” button, which were enhanced last year (with the release of Pie, maybe?) to show “Yes, it was me” and “No” that show side by side, and that also show the location that the attempted login occurred.
I’ve only recently (last week, to be exact) enabled the Advanced protection Program across all my (non G-Suite) Google accounts, and enforced physical security key verification across all the G-Suite accounts (with the option to save credentials removed, forcing all users to always use a key for verification).
Thanks for your reply @johnl.galt
I’ve also been using Google Authenticator on all of my G accounts (and more) since it first launched.
Few people in the US don’t seem to realize that Google Titan Secuity Keys are not sold or available in most (all?) countries outside of the US. Some grey market resellers exist but I only want to buy from Google and don’t have a US address.
Same with Google’s Advanced Protection Program, not sold outside US, it requires the Titan keys. Maybe if I got Titan Keys Google will allow APP on my non US account and maybe a 3rd party FIDO can be used with APP.
I understand the strength of security keys, including specifically for phishing protection, and have been following FIDO since the start of its process.
The point of the announcement in this article is that it suggests, and Google’s account security configuration allows, making the phone a secuity key via bluetooth without a physical security key.
The point of my post is to warn that no one should try this UNLESS they already have a physical security for that account.
“The point of my post is to warn that no one should try this UNLESS they already have a physical security for that account.”
This is key (for lack of an unavoidable pun). Would be nice if Google made this clear in their announcement, as at the moment it looks altogether omitted. I’ve already gotten multiple emails from clients wondering if this is the end all / be all for authentication. Given the risk/ruin ratio of NOT having a Yubikey (ie https://privacycanada.net/dangerous-cyber-security-risks/) or similar physical security), it would be asinine to rely solely on your phone as a security authentication device.
Google does a lot of interesting things with security. People interested in security should read their BeyondCorp papers (usually less than 10 pages) that are available to down load online.
Who does your graphics for these? They always look so nice.
Can’t take credit for that one, which comes from Google.
Hah, that’s comical. When I reverse searched it with google it guessed it was an iPhone.
Where do you get your graphics? They always look so nice.
I wonder if Apple Pay uses the same thing, done essentially the same way.
This approach may well keep our secure from all but Lord Google himself!
He’s the smartest of the internet behemoths, the best we can hope for.
I don’t use chrome extensions or android apps from any other. The danger with apps from small companies is that they may be HQ’ed in BVI, and one day sold to a front co. of the Russian mafia. And you would never know.
SO, Jockular’s Law is: only ever use an extension or an app from a company whose reputational risk is greater than any revenue gain they might enjoy. This means: stick to behemoths for extensions and apps.
If use Google Security Keys on gmail account, and also have Thunderbird setup to get email, do you need to authenticate everytime you get mail, or is it just 1st time you setup mail?
In short, you issue thunderbird an app password and use that instead of your normal password+2fa.
https://support.google.com/mail/answer/185833?hl=en&visit_id=636908085401063243-1864899479&rd=1
Google logs the access separately, and if at any point you discover that Thunderbird/its computer was compromised, you can revoke that credential w/o impacting your normal password.
Note: generally speaking app passwords are not full tokens, such things can be restricted to a given function. At the very least, one can’t use an app password to log into Google w/ a web browser and one can’t use it to change one’s password / security settings.
So………. if you loose your device you are locked out of your account?
Google provides you a set of alternate methods to ensure you do not get locked out like SMS, backup codes, etc.
But you cant receive SMS or input codes if you don’t have the device.
That is why you need to register at least two devices so you have a backup. Of course, buying two smart phones is going to be more expensive than a couple of YubiKeys. . .
Two devices that’s expensive but sounds like a plan if the user has only registered one! What happens when device doesn’t have a usb drive?
This is why Google uses the BT as a mean to log in so you don’t need a USB.
That’s why you print out your backup codes and store them in two safe locations, one preferably being a safe.
I have had this enabled for months. Was it previously only available to Pixel and Nexus products or is the only difference now that phones can be used for their Advanced Protection?
Curious, given that a large number of Android phones are manufactured and have their OS loaded by Chinese manufacturers, does Google ensure that the “Security Key” capability is protected against malicious OS vendors?
Personally I’d rather use a dedicated device, or iOS device. If I lived in the Android universe, I’d go first-party or ensure that I loaded the OS (which usually results in much of the phone’s capability being unavailable due to the need for specialized hardware support.)
Good point – there is good reason for suspicion – at least with USB keys, you pretty much know the vendor path, and if you trust the company to check the hardware, not much can go wrong.
It is all about risk management and level of confidence you need and price you want to pay. THere are different methods that all rely on the same protocol. YOu can use Google Titan Key/ Yubico (I like their form factors). Android phone as a key is way better than only using password for regular authentication as it deters cybercriminals who exploit vulnerabilities of passwords and SMS.
To exploit Android security keys even on cheaper Android devices, takes a determined actor (nation state or persistent threat actor) to exploit that. Cybercriminals will prefer to move to softer targets….which there are plenty!
Google Titan (their version of a physical security key) is made in China and Google is a partner of China’s military and communist leadership.
Google is also known to comply with the demands of oppressive governments around the world, seeking information about their citizens and in blocking speech undesirable to those governments — including China, the US, and Canada.
It stands to reason that Google would not care about the security interests of individuals or in keeping secrets from the Chinese, or anyone else.
Assume there are back doors in all Google products, physical or not.
https://techcrunch.com/2019/01/08/yubico-launches-a-new-nfc-security-key-and-preps-iphone-support/
I was under the impression that Google Authenticator/Authy generate codes internally every minute and that the apps are time-synced with whatever sites you registered the apps with, so that both the app and site have synced codes so nothing is transmitted. However, the article states that “…common forms of 2FA require the user to supplement a password with a one-time code sent to their mobile device via an app (like Authy or Google Authenticator).” How are codes “sent” to these authenticator apps, especially when the apps continue to generate codes that are accepted by the sites registered to the apps when cell phone, wifi, and bluetooth functionality are all disabled.
You’re correct, TOTP [1] involves a secret that the app generator uses to calculate the correct answer w/o requiring a live connection to the server (because they’re in time-sync).
But, from an English perspective, one could say that the app calculates the code and then “sends” it from the phone’s CPU to the phone’s display. It’s a bit stilted, but not technically incorrect :-).
[1] https://en.wikipedia.org/wiki/Time-based_One-time_Password_algorithm
Yes and no. Goggle Authenticator is strictly TOTP but Authy has multiple methods including SMS transmitted OTP and Push Authentication in addition to TOTP. They should not have been lumped together in the article.
so apologies if I am being a little dense on this but am I correct in thinking that the mobile device(s) you register as a security key cannot be used to log into a service using that device?
If a criminal stole your android phone (registered device), got through onto the phone (either no biometric or passcode enabled or hacked through it), opened Chrome and tried to log in to your gmail account, automatically they would access your email as the hardware device is present. This seems daft to me.
Generally w/ an Android phone, Chrome and Gmail are already logged in, so upon stealing such a phone, once it’s unlocked, you’re done anyway.
Now, historically Google tends to ask for a password if one tries to change Google security settings (and potentially the 2fa as well). But it’s true that generally one can ask Chrome for Android about stored passwords and get them w/ just the device’s unlock code.
The basic assumption when using any hardware security device is that you’ll notice when it’s missing, whether it’s a phone or a key fob. If you don’t pay attention to your keys, then you’re at risk.
2FA is always better than 1FA. But yes, you need to not lose/have your 2nd factor stolen.
As Brian mentions, Google allows one to set up Advanced Protection which lets you register two 2nd factors. Historically, that could be two hardware tokens, now it could be a phone and a hardware token. One could lock that second token into a physical bank vault.
What should be noticed that you can remove the security key if you lose the means to log in using the U2F. It is best to have several backup if needed.
“The most commonly used Security Keys are inexpensive USB-based devices…”
Inexpensive is quite a relative term.
The average North American cannot comfortably manage the absence of more than one paycheck or a major home repair, without resorting to the use of credit cards, a loan, or an insurance claim. Most don’t even fully own their own homes or mobile phones; they rent or owe payments.
For many people, spending $40 for a pair of USB keys is a big deal. I submit that it is not inexpensive to them.
There are some for $8 on Amazon, and with the phone acting as one key you would only need one physical key for the second key. Having two keys is only required for Google’s Advanced Protection Program, which is mainly meant for journalists, politicians, and other high-profile targets.
Most people will be fine using TOTP keys with software like Authy or the Google Authenticator. If you save the seed someplace safe you can add it to another phone if needed. The point of the Advanced Protection Program is to prevent people from clicking on phishing links and putting their credentials into shady websites. That can be avoided entirely (assuming your device is not compromised) by only signing in through google.com
“your account if you loose your initial key”
I think you mean “lose” 🙂
*bzzzt* I sense nitpicking *beep boop*
*bzzzzzzzzzt* You knew what they meant, who cares? *bzzt*
*beep* Quit nitpicking over tiny grammar mistakes that no one cares about *beeeeeeeeep*
I routinely apply maximum torque when securing my keys to ensure that they do not become loose.
Google is the Worst at security of any big company.
Millions of people have unwittingly download malware infested apps from their play store, which goog later removes. And although you have to have an active Email account to get the files they NEVER send notices to people that they should remove the malware – making google the biggest and most persistent malware distributor in the world. Zero notifications. But they’re so big, they can do what they want. Make no mistake, Google is evil.
…and nobody held a gun to your head telling you to use Google if you are that paranoid about them…
If you don’t want to be part of the surveillance economy, do not casually use the internet, end of story.
The whole idea of using a smart phone at all, whether with software (Google Authenticator, etc…) or as a hardware token, is a PITA when it comes time to upgrade your phone. You have to go into every 2FA site you and reset them up. I have about a dozen. I might switch to a USB Token on my next phone upgrade.
Wanted to add, I like to leave BlueTooth turned off on all of my devices, partly for security, partly for interference with other BT devices in the vicinity/home. I don’t like the idea of having to leave it turned on for this to work. If I turn it off until needed, it is the same hassle as Google Authenticator and other TOTP based apps, having to turn BT back on for two devices.
Does this provide any advantage or disadvantage compared to authenticator apps on your phone? Looks the same, as pressing “Yes its me loggin into google” window presented by google existing MFA.
So do you have to have your phone with you while you’re at the screen logging in? Where I sit at work I generally can’t get a signal on my phone, so when I do SMS authentication, I have to walk outside, write down the number, then come back to the screen and enter it. Is it the same way with this method? The website sends something to the phone and I authenticate, but I have some time to get to my phone, or does the interaction with the phone have to be immediate? If so, then I don’t think I can use this method.
Why would you need to write it down? Once you receive the SMS it stays on the phone. Just walk inside and open the message again. No need to write anything down.
Generally this method (or SMS to Google Voice) would require some form of Internet access, whether that’s Cellular or WiFi…
TOTP [1] otoh doesn’t…
[1] https://en.wikipedia.org/wiki/Time-based_One-time_Password_algorithm
I’ll stick with the YubiKey. Google knows to much as it is.
The problem is this requires Bluetooth, which is notoriously unreliable. I can’t for the life of me get my phone and work computer to recognize each other via Bluetooth. Plus, I don’t see the advantage over using the regular Google prompt on my phone (for Gmail) until lots of sites are using it.
I had no problem in setting mine relative quickly. You have to make sure the codes are the same on both devices and accept it to pair it.
I hate Google. They almost destroyed the Internet to create the Googlenet. Shame on them…
So the question comes to mind: What if the phone breaks. Can any of these two factor authentications be transferred to a new phone without the old phone operational and in hand?
It is a pet concern of mine since I have several hosting accounts, websites, Amazon, etc., on Google Authenticator, and I have this paranoid fear of having my phone fly out of it’s holster as I ride my motorcycle and have it squished by the car tailgating me…
Any suggestions?
@catwhisperer
I’ve done it a few times and it would be nice if it was easier but I’m not sure how this would be without incremental risk (eg if the backup code printout also included a QR code to transfer the pseudorandom seed to the new GA instance).
Here are the steps to moving GA Google Accounts to a new phone:
https://support.google.com/accounts/troubleshooter/4430955?hl=en#ts=4430956
You will need (and should already have printed and safely kept) your backup codes for every GA Google account.
Your should also have backup codes for your other accounts and each service may have their own migration steps.
Amazon help is less than helpful.
In order to set up GA on your Amazon account, they required you to register a backup phone number. If you suddenly lost your phone, using either that or your backup codes will allow you to log in, disable your old GA-phone and set up your replacement.
https://www.amazon.com/gp/help/customer/display.html search “Two-Step Verification” “google authenticator”
I’ve always wanted to setup 2FA but I’ve had bad luck with the Blizzard Authenticator on my PC where I happened to lose the config from hardware failure.
Does any of these options (Authy/Google Auth/Yubi Key/etc) have a backup way to fix things in case your primary option dies/gets compromised/gets lost?
I’ll stick with the YubiKey. Google knows to much as it is.