Law enforcement agencies in the United States and Europe today unsealed charges against 11 alleged members of the GozNym malware network, an international cybercriminal syndicate suspected of stealing $100 million from more than 41,000 victims with the help of a stealthy banking trojan by the same name.
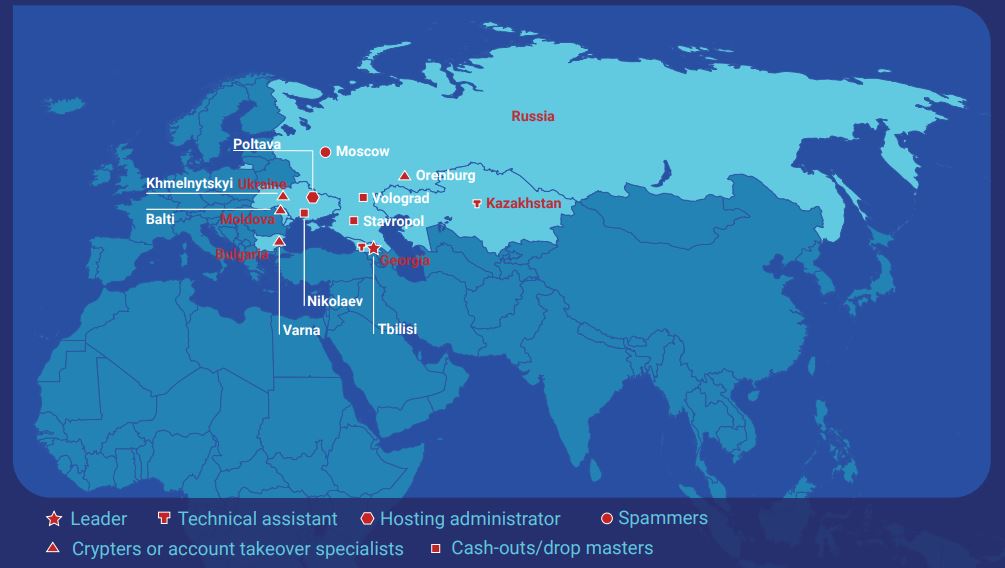
The locations of alleged GozNym cybercrime group members. Source: DOJ
The indictments unsealed in a Pennsylvania court this week stem from a slew of cyber heists carried out between October 2015 and December 2016. They’re also related to the 2016 arrest of Krasimir Nikolov, a 47-year-old Bulgarian man who was extradited to the United States to face charges for allegedly cashing out bank accounts that were compromised by the GozNym malware.
Prosecutors say Nikolov, a.k.a. “pablopicasso,” “salvadordali,” and “karlo,” was key player in the GozNym crime group who used stolen online banking credentials captured by GozNym malware to access victims’ online bank accounts and attempt to steal their money through electronic funds transfers into bank accounts controlled by fellow conspirators.
According to the indictment, the GozNym network exemplified the concept of ‘cybercrime as a service,’ in that the defendants advertised their specialized technical skills and services on underground, Russian-language, online criminal forums. The malware was dubbed GozNym because it combines the stealth of a previous malware strain called Nymaim with the capabilities of the powerful Gozi banking trojan.
The feds say the ringleader of the group was Alexander Konovolov, 35, of Tbilisi, Georgia, who controlled more than 41,000 victim computers infected with GozNym and recruited various other members of the cybercrime team.
Vladimir Gorin, a.k.a “Voland,” “mrv,” and “riddler,” of Orenburg, Russia allegedly was a malware developer who oversaw the creation, development, management, and leasing of GozNym.
The indictment alleges 32-year-old Eduard Malancini, a.k.a. “JekaProf” and “procryptgroup” from Moldova, specialized in “crypting” or obfuscating the GozNym malware to evade detection by antivirus software.
Four other men named in the indictment were accused of recruiting and managing “money mules,” willing or unwitting people who can be used to receive stolen funds on behalf of the criminal syndicate. One of those alleged mule managers — Farkhad Rauf Ogly Manokhim (a.k.a. “frusa”) of Volograd, Russia was arrested in 2017 in Sri Lanka on an international warrant from the United States, but escaped and fled back to Russia while on bail awaiting extradition.
Also charged was 28-year-old Muscovite Konstantin Volchkov, a.k.a. “elvi,” who allegedly provided the spamming service used to disseminate malicious links that tried to foist GozNym on recipients who clicked.
The malicious links referenced in those spam emails were served via the Avalanche bulletproof hosting service, a distributed, cloud-hosting network that for seven years was rented out to hundreds of fraudsters for use in launching malware and phishing attacks. Avalanche was dismantled in Dec. 2016 by a similar international law enforcement action.
The alleged administrator of the Avalanche bulletproof network — 36-year-old Gennady Kapkanov from Poltova, Ukraine — has eluded justice in prior scrapes with the law: During the Avalanche takedown in Dec. 2016, Kapkanov fired an assault rifle at Ukrainian police who were trying to raid his apartment.
After that incident, Ukrainian police arrested Kapkanov and booked him on cybercrime charges. But a judge later ordered him to be released, saying the prosecution had failed to file the proper charges. The Justice Department says Kapkanov is now facing prosecution in Ukraine for his role in providing bulletproof hosting services to the GozNym criminal network.
The five Russian nationals charged in the case remain at large. The FBI has released a “wanted” poster with photos and more details about them. The Justice Department says it is working with authorities in Georgia, Ukraine and Moldova to build prosecutions against the defendants in those countries.
Nikolov entered a guilty plea in federal court in Pittsburgh on charges relating to his participation in the GozNym conspiracy on April 10, 2019. He is scheduled to be sentenced on Aug. 30, 2019.
It’s good to see this crime network being torn apart, even if many of its key members have yet to be apprehended. These guys caused painful losses for many companies — mostly small businesses — that got infected with their malware. Their activities and structure are remarkably similar to that of the “Jabberzeus” crime gang in Ukraine that siphoned $70 million – out of an attempted $220 million — from hundreds of U.S.-based small to mid-sized businesses several years ago.
The financial losses brought about by that gang’s string of cyberheists — or at least the few dozen heists documented in my series Target: Small Business — often caused victim companies to lay off employees, and in some cases go out of business entirely.
A copy of the GozNym indictment is here (PDF).




Receiving notifications again, great article !
Where is Hitler when we need him?
What up, fam?
No-one ever needed Hitler. The last time people thought they do he devastated their country, killed millions of innocent citicens of his own land, started a world war and ordered his army to commit senseless and cruel war crimes everywhere they arrived.
Yeah, noone needs something that acts like Hitler did.
The americans do all the bombing, robbing and killing the millions right now.
Loving these official court records, good stuff
The AUSA’s press release says they’re pursuing this because of “…a number of victims located in the Western District of Pennsylvania,” but the indictment lists just one business in Pennsylvania.
Simple ‘errors’ like that are why people don’t trust prosecutors.
Most of the alleged victims were located outside of Pennsylvania. The Pittsburgh region has no tech industry, few legal firms dedicated to cybercrime defense, and a jury pool that’s poorly educated. There’s really no excuse for the DOJ filing charges there, except to deliberately ignore the appearance of fairness.
Shame on them.
And if these guys are criminals, as alleged, shame on them, too.
I’m confused. They’re pursuing in the Pittsburgh region because some victims were there? That doesn’t make sense to me at all. This seemed like a mass-spam campaign according to:
“[criminal] who allegedly provided the spamming service used to disseminate malicious links that tried to foist GozNym on recipients who clicked.”
If that’s the case, how is this targeted to a few regions? I don’t understand the workings of law enforcement whatsoever, so I’m very ignorant on the subject. It just seems weird to me that they would indict in the region where the attack occurred. This just seems like some unlucky person clicked a link they shouldn’t have, not that one or more of the malware leaders are in that area.
“The Pittsburgh region has no tech industry, few legal firms dedicated to cybercrime defense, and a jury pool that’s poorly educated. There’s really no excuse for the DOJ filing charges there, except to deliberately ignore the appearance of fairness. ”
You must be joking. (Or from Cleveland). Pittsburgh is a tech hub and the home of Carnegie-Mellon University, one of the top 5 computer science schools in the country.
Extra points for the Cleveland reference in replying to perhaps the least-informed post I’ve ever seen on this site.
To say that Pittsburgh is not a tech city, despite the few babushkas that still roam wild in the streets, is to not have been there in the past 20 years and to know very little.
Other PA victims were named in the 2016 indictment: https://www.justice.gov/usao-wdpa/pr/bulgarian-charged-goznym-malware-attacks-us
OK so then that makes some sense to continue there. Thanks BK.
Seems the entry point is always an email or URL link on a website; people (especially untrained/uneducated) are always the weakest link. Click, click, click…….
We’re always talking about weak Cyber defenses within organizations’ networks, but maybe we should all take a closer look at security on ad servers and mail exchange servers. I for one would like to see all email with spoofed ‘From’ addresses or obfuscated URLs deleted immediately. Some mail servers don’t even mark them as SPAM/JUNK.
Kind of like these spoofed phone numbers from robo callers; just read today the FCC is trying to start legislation to have service providers block spoofed calls by default.
“the FCC is trying to start legislation to have service providers block spoofed calls by default.” About time.
The weakest link is MS Windows. Using a Chromebook for reading email, I can be fooled by malware clickbait, but I can’t be infected. I’m mostly safe while using OS X and Linux too.
MS Windows is so full of security holes that it will probably always be the weakest link.
It’s almost like comics, all the funky names of the criminals, and one (known) hero. Wish you had time to investigate Monsanto or a certain former politician (or all of them).
We need more hero types that do what you do. And less un-trustable governments/companies.
Perhaps the best thing for the modern age that could happen would have many parents teach their kids by updating an older personal mantra from “Don’t Be Stupid” to the modern “Don’t Be Clickbait”, and adhering to it themselves….
Why They waste their skills and talent?
Much Better way is just Invest in crypto currency and Wait When Federal reserve dump huge load of cash.
Dollar Go Down but You will be Rich Rich!
2nd point.
How the feds gona proof that They are guilty?
The Good lawer will fix.
And those guys have money to pay Good layewer.
But how They proof? If the guys Don’t own anything on their name no assets, nothing.. Then how to proof anything?
“the FCC is trying to start legislation to have service providers block spoofed calls by default.” About time.
When r they going to stiffen penalties for these cyber criminals? Minimum of 20 years to start per count, is a good start. It is a plague that is ongoing.
More Russians that can’t go on abroad anymore. When is the US of Agression going to stop to bully countries into extraditing people they hate?
Have you heard about one of the fastest- growing frauds in the UK that starts with a fake email allegedly from the UK TV Licensing Authority. I have a copy of it if you need it, Mr Krebs.