Federal prosecutors this week charged a Seattle woman with stealing data from more than 100 million credit applications made with Capital One Financial Corp. Incredibly, much of this breach played out publicly over several months on social media and other open online platforms. What follows is a closer look at the accused, and what this incident may mean for consumers and businesses.

Paige “erratic” Thompson, in an undated photo posted to her Slack channel.
On July 29, FBI agents arrested Paige A. Thompson on suspicion of downloading nearly 30 GB of Capital One credit application data from a rented cloud data server. Capital One said the incident affected approximately 100 million people in the United States and six million in Canada.
That data included approximately 140,000 Social Security numbers and approximately 80,000 bank account numbers on U.S. consumers, and roughly 1 million Social Insurance Numbers (SINs) for Canadian credit card customers.
“Importantly, no credit card account numbers or log-in credentials were compromised and over 99 percent of Social Security numbers were not compromised,” Capital One said in a statement posted to its site.
“The largest category of information accessed was information on consumers and small businesses as of the time they applied for one of our credit card products from 2005 through early 2019,” the statement continues. “This information included personal information Capital One routinely collects at the time it receives credit card applications, including names, addresses, zip codes/postal codes, phone numbers, email addresses, dates of birth, and self-reported income.”
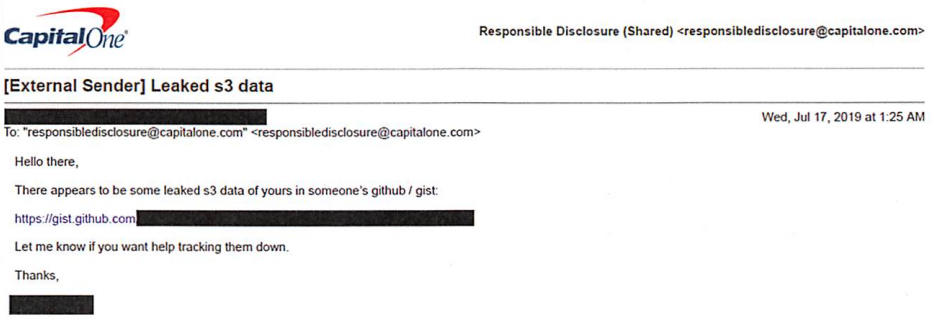
The FBI says Capital One learned about the theft from a tip sent via email on July 17, which alerted the company that some of its leaked data was being stored out in the open on the software development platform Github. That Github account was for a user named “Netcrave,” which includes the resume and name of one Paige A. Thompson.
The complaint doesn’t explicitly name the cloud hosting provider from which the Capital One credit data was taken, but it does say the accused’s resume states that she worked as a systems engineer at the provider between 2015 and 2016. That resume, available on Gitlab here, reveals Thompson’s most recent employer was Amazon Inc.
Further investigation revealed that Thompson used the nickname “erratic” on Twitter, where she spoke openly over several months about finding huge stores of data intended to be secured on various Amazon instances.
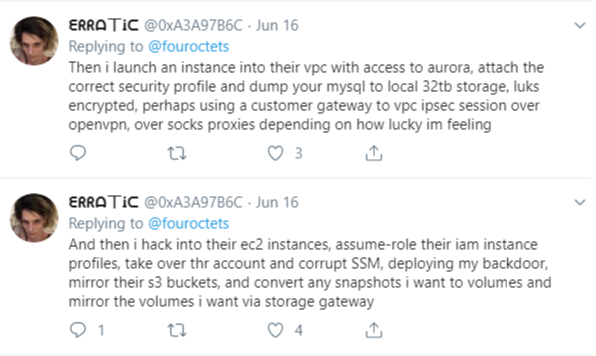
The Twitter user “erratic” posting about tools and processes used to access various Amazon cloud instances.
According to the FBI, Thompson also used a public Meetup group under the same alias, where she invited others to join a Slack channel named “Netcrave Communications.”
KrebsOnSecurity was able to join this open Slack channel Monday evening and review many months of postings apparently made by Erratic about her personal life, interests and online explorations. One of the more interesting posts by Erratic on the Slack channel is a June 27 comment listing various databases she found by hacking into improperly secured Amazon cloud instances.
That posting suggests Erratic may also have located tens of gigabytes of data belonging to other major corporations:
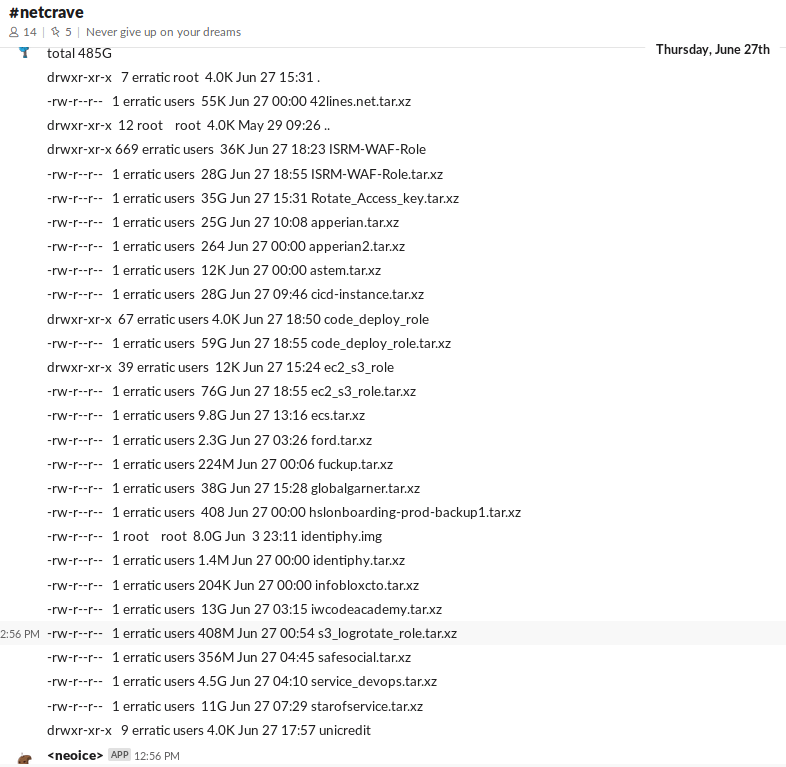
According to Erratic’s posts on Slack, the two items in the list above beginning with “ISRM-WAF” belong to Capital One.
Erratic also posted frequently to Slack about her struggles with gender identity, lack of employment, and persistent suicidal thoughts. In several conversations, Erratic makes references to running a botnet of sorts, although it is unclear how serious those claims were. Specifically, Erratic mentions one botnet involved in cryptojacking, which uses snippets of code installed on Web sites — often surreptitiously — designed to mine cryptocurrencies.
None of Erratic’s postings suggest Thompson sought to profit from selling the data taken from various Amazon cloud instances she was able to access. But it seems likely that at least some of that data could have been obtained by others who may have followed her activities on different social media platforms.
Ray Watson, a cybersecurity researcher at cloud security firm Masergy, said the Capital One incident contains the hallmarks of many other modern data breaches.
“The attacker was a former employee of the web hosting company involved, which is what is often referred to as insider threats,” Watson said. “She allegedly used web application firewall credentials to obtain privilege escalation. Also the use of Tor and an offshore VPN for obfuscation are commonly seen in similar data breaches.”
“The good news, however, is that Capital One Incidence Response was able to move quickly once they were informed of a possible breach via their Responsible Disclosure program, which is something a lot of other companies struggle with,” he continued.
In Capital One’s statement about the breach, company chairman and CEO Richard D. Fairbank said the financial institution fixed the configuration vulnerability that led to the data theft and promptly began working with federal law enforcement.
“Based on our analysis to date, we believe it is unlikely that the information was used for fraud or disseminated by this individual,” Fairbank said. “While I am grateful that the perpetrator has been caught, I am deeply sorry for what has happened. I sincerely apologize for the understandable worry this incident must be causing those affected and I am committed to making it right.”
Capital One says it will notify affected individuals via a variety of channels, and make free credit monitoring and identity protection available to everyone affected.
Bloomberg reports that in court on Monday, Thompson broke down and laid her head on the defense table during the hearing. She is charged with a single count of computer fraud and faces a maximum penalty of five years in prison and a $250,000 fine. Thompson will be held in custody until her bail hearing, which is set for August 1.
A copy of the complaint against Thompson is available here.
Update, 3:38 p.m. ET: I’ve reached out to several companies that appear to be listed in the last screenshot above. Infoblox [an advertiser on this site] responded with the following statement:
“Infoblox is aware of the pending investigation of the Capital One hacking attack, and that Infoblox is among the companies referenced in the suspected hacker’s alleged online communications. Infoblox is continuing to investigate the matter, but at this time there is no indication that Infoblox was in any way involved with the reported Capital One breach. Additionally, there is no indication of an intrusion or data breach involving Infoblox causing any customer data to be exposed.”




Why was PII data at rest stored unencrypted?
Shame on Capital One. Basic info security is to encrypt PII data at rest. I think it’s well proven that almost all corporations are incapable of securing data, especially in a cloud system. There are a million ways of losing data and it only takes one. Having the data encrypted at least gives a chance that the data loss will be minimized if the encryption holds.
They aren’t unable to secure information. They’re not dedicating the resources. We need legislation in place to force basic secure practices.
Legislation alone won’t get the job done. Enforcement is a massive undertaking the results bound to create a new and very corrupt ecosystem.
Think about PCI compliance. When it first came out every Tom, Dick and Harry started calling small businesses saying their audit was mandatory for PCI compliance. Most of them took the businesses money, did not do a thorough audit and did not fix any PCI problems. Did these audits even make a dent in cc compromise? I don’t think so.
Actually, Capital One has more than sufficient Cyber Security Resources. Annual Cyber Security budget well in excess of $140 million per year, and close to 600 highly skilled Cyber Engineers and Developers. But the CIO’s intense focus is being first bank to be 100% in the cloud. Security is not top priority. That may be the external message, but internally, it’s widely known, even from the CISO, that Security is not a top priority.
It most likely was. She gained access to keys that allowed her to extract the encrypted data from S3. Basically, she gained access to decrypt the S3 data and then re-encrypted it on her storage with her own keys.
Sounds like she was able to exploit an office firewall hole that allowed her to log in to some instances with poor key management, thus gaining the castle’s skeleton key.
The data was likely encrypted at rest. The attacker was able to gain access to credentials associated with an IAM role that likely had access to the S3 bucket encryption key. This is by design. How else would applications be able to read/write data from encrypted S3 buckets? Encryption at rest is primarily designed to protect you if the physical storage device is stolen.
Data-at-rest encryption in general is not designed to just protect in case your physical device gets stolen. That is only one case it protects. Getting a key to decrypt data should involve credentials that are hard to fake or assume. And data-at-rest keys should be stored separately from the data it encrypts. But if AWS identity management allows an attacker access to all keys an account then no type of encryption will help.
The problem is misconfigured Identity Access Management. The encryption service in AWS is Key Management Service (KMS) and allows for you to assign separate roles. Ideally, everyone should be able to encrypt data, but decryption should be granted on a by-key basis to roles, users, etc based on the data they actually need to access. I work for a cloud security consultant firm and this is how we recommend (and audit) the environments we support.
The problem is that over 70% of the time, when we first look at an environment, everyone just grants “Admin” to every role because “we needed to get this done” but then never go back and remediate it. AWS even makes it easy by telling you exactly what permissions (of their >10,000 actions) have been used by a role within the last 90 days on a single screen.
Based on the limited Tweets I have seen of her method, I would say Capital One fell into this same trap. There’s absolutely no reason a web app should ever be able to spin up new instances and assign roles that let her perform the other steps.
Unfortunately, I think it comes down to convenience vs. security. And, developers and other business users go with the “let’s open and allow everything for ease” rather than take an elevated approach of least privileged access for users/apps etc..
Dear Readers: Please refrain from making any more comments about this person’s gender or gender identity. It adds nothing to the discussion about the important matters related to this breach. The only reason I mentioned it at all is that it is likely to come up in Thompson’s trial and/or sentencing.
Anyone who wants to see what an intelligent discussion about the actual breach itself looks like should spend some time over at Hacker News, which as usual has some pretty thoughtful comments on the matter of the “how” of this breach. https://news.ycombinator.com/item?id=20565014
Any further comments about gender identity politics will be removed, and the commenter will be placed on a permanent moderation queue. Thank you for your cooperation.
On the gender issue, in question. If you don’t want to draw comments, don’t add that into your main report. That is an irrelevant comment to add in regards to the breach.
I disagree there. I read the gender part, but ignored it because the matter at hand is about a breach. Brian doesn’t write about gossip, he writes about cyber security and breaches. My 1st thought was this is a breach article, not a gossip blog post.
Motivation is an important aspect of any alleged crime. Especially of interest here, because someone was actually caught, unlike so many other data breaches.
Before dropping a ban-hammer, look at it from the perspective of executives who, today, might be looking at the transgender former Pvt. Manning and Paige Thompson as representative of a new kind of IT security risk. (And perhaps wondering if gender and psychological struggles might indicate an employee who should be removed from sensitive data projects).
Be glad you don’t have the same audience as Ycombinator. “How” is not nearly as interesting as “why” and “who.” Their discussions are so boring.
Any executive trying to look closer at gender identity as a new risk… will no longer be an executive.
Human Resources often outrank even the CISO. They would, and rightly should, squash any attempt at the discrimination you are advocating.
And if they don’t… the lawsuits will flow. And rightly so.
Just because the media makes mention, and the mob can’t stop talking about… transgender people are no more likely to commit crime. There are plenty of them in IT, and often it isn’t even noted until something happens.
It is observation bias…. nothing more!
Even if the data was encrypted in an S3 bucket, the EC2 instance compromised could have rights in its policy to decrypt the data from the bucket.
Interestingly enough, on almost all the records the SSN and other regulated data were tokenized, they left the basic PII like name, address, income level alone because there is no current US Federal legislation protecting that information. However, Massachusetts has a robust privacy law about it’s citizens, and California just passed a very strict one for it’s citizens, so I expect the lawyers are gearing up already for this profitable class action suits.
Can’t tell ya the time I’ve written findings for no policy in place to rotate system/service accounts or API keys for AWS instances during SCA’s.
Brian,
I’m interested to see what other companies have been compromised… I see InfoBlox in there, Apperian, Code Academy, Ford, Safe Social, Unicredit (Eu bank I believe)…. any word from those organizations yet?
Looking forward to learning more.
So who do you think the FU tarball refers to? Capital One? 😀
As stated in the story, Erratic said the Capital One data corresponds to the two entries in that screenshot beginning with ISRM.
I’ve been in a dispute with CitiCards (Master Card) for 4 months. They said my information was breached and that I needed to close my account and let them open a new one. I refused because I knew I was done with them. This happened a little over two years ago and the real problem was that they didn’t call me. Out of state purchases for Tracfone minutes, new cell phone and the insurance to cover it along with an airline ticket from Atlanta to Florida!! I live in Illinois. I got the statement and almost stroked out. This latest was for 5 duplicate charges in Singapore which they approved. Really – SINGAPORE?? I froze the account instead of allowing them to close and open a new one. 5 weeks later, they allowed somebody to UNFREEZE my account and purchase something from ClarksUSA.com for $260.88. They did not honor the dispute even though they knew I wasn’t in Singapore and have never placed an online order from Singapore. This card had just been reissued with a new security code so I knew it was CitiCards. The shoes order proved it.
I used to work for Citibank. 90% of the fraud there is done by EMPLOYEES. You have no idea how often this happens at EVERY financial institution. Either it’s someone you know,or a family member,and most likely a bank employee.WHO else would have access to all your info?
At this point? Just about anyone. After Equifax, Experian, Marriott, and the other massive breaches with PII included in them; it’s not hard to see how a lot of people could easily have all of the information about you required to open up a credit card (or get a duplicate card, etc.) in your name. Or mine. Or anyone’s.
Working at aws three years ago does not constitute an insider threat. Improperly secured s3 buckets and misconfigured firewalls are the root cause of this issue, which is essentially an error by capitol one that lead to the breach.
Bingo!
@vb: It very well could have *been* encrypted: many organizations achieve “encryption at rest” by using AWS KMS-encrypted stores (e.g., by turning on the “encrypted” flag for MySQL or Aurora). Thompson’s access path (get the right access keys and do a mysql dump) has the hosting provider do the decryption for them.
The encryption lesson in that case needs to be more along the lines of “bring your own dragons”: don’t trust your hosting provider to maintain your keys. OTOH, it is *very* difficult to use many cloud services (think Kinesis, for example) in an encrypted way *without* giving AWS control of your keys. Then the convenience of the tools themselves (the tool looks up your access rights using AWS IAM, and then gives you access to the keys those rights offer) opens up the data.
It’s hard to be sympathetic for anyone on the customer or Bank side of the equation. Just open Capital One’s main page https://www.capitalone.com/ and check the option: “See if you’re prequalified”, wherein they boldly ask for Social Security and other identity info. Who would deal with a company so obviously exposing of its customers?
And, its Capital One who sends me more junk mail than any other source, monthly postal solicitations, telling me I am pre-qualified for a credit card, year after year. For fun, I sent in the invitation reply form for a credit card after dozens of letters telling me I was; and guess what: I am not pre-qualified; it was marketing misdirection. Frankly, the company acts like a phishing operation. Sorry for any innocent’s being harmed, but good riddance to Capital One, they are Spam.
SSN’s would be identifying information, yes. But how else could a person be prequalified for credit?
“And, its Capital One who sends me more junk mail than any other source”
This is why I always ask for the privacy policy at each business I start doing business with and sign off for them to “not” contact me with solicitations, mailings, phone calls, or sharing my information with other companies, even within their own realm.
I get zero solicitations in the mail and no phone calls. They don’t like this but it protects me, I don’t care about their profits. The only people who try to contact me by phone or mailings are scammers. I haven’t gotten a pre-approved CC offer in decades.
Jennifer Garner and Samuel L. Jackson must be turning over in their graves.
Wow, July 19, you really had this article in draft since then 🙂
Brian uses a different (European?) date format – the larger-font “30” is the day, while July 19 refers to July, 2019.
The big number is the day.
This is certainly the top comment on the site. Do you ever get the urge to change the format?
as a daily reader, I agree. Even if it went long format.
On this 31st day in the month of July and the year 2019 AD.
“The complaint doesn’t explicitly name the cloud hosting provider”
Yes, it does, right there in the message: “There appears to be some leaked s3 data of yours.” S3 is Amazon’s Simple Storage Service: https://aws.amazon.com/s3/
I’m thinking the operative word is ‘explicitly’. if i ask my wife or neighbors what an S3 bucket is, they won’t know.
Also, when this story initially came across my phone screen last night, the only clue Amazon might be involved was the court jurisdiction cited at Bloomberg.
How can CapOne say the sensitive data was “99% not compromised” when the largest component of the compromised data is collected PII? How can their CEO come out and say, “not used for fraud or dissemination” when the file permissions are WORLD Readable (I see 644 permissions on the listing….)?
I hope there’s an access log proving it wasn’t copied somewhere between March and when they removed the files/changed permissions.
“over 99 percent of Social Security numbers were not compromised”
The SSN part is important and shouldn’t be omitted.
Remember, they collect SSNs from a LOT of places.. even from non-customers. I am willing to bet that people who have filled out credit applications, still make up less than 1% of their total number of SSNs collected.
Wow, at first I wanted to say that it was the first one in my memory when a woman does this kinda thing. But then reading further, it turns out, nope. It’s a dude.
Female name, female pronouns, she calls herself a female… seems like a female to me… No idea where you’re getting a dude from.
If I call myself a dragon, I’m a dragon? What an imbecilic way to think.
The imbecilic thought would be that dragons exist. And if they were… that they are human with the same DNA.
Women exist. And during fetal development… men and women are essentially the same. One chromosome difference.
Open a book, and see how self identity is actually formed, biologically and chemically…. before you sound foolish with ridiculous metaphor.
How did they know when to ac
Junk mail from from capital one has delivered countless dead trees to my mailbox. Got pre-qualified info yesterday. Almost fell for capital One since rate finally looked reasonable. Since I’m new to all of this over the net, web, etc. I feel blessed to have stumbled across this info. Time to drag out the shredder.
I am getting tired of hearing about these breaches at major corporations. Breach fatigue is kicking in. And of course, they all take the security of your information “very seriously.”
Why didn’t they at least have anti-malware to prevent the installation of the backdoor used to exfiltrate the data? Isn’t this basic blocking and tackling for any server? Or is the assumption that it’s “secure” because it’s in amazon and has a WAF?
Anti-malware products don’t detect everything!
Nothing does! It’s called layers. Who knows, maybe they had it but 90+% of AWS customers don’t bother. I would hope a financial institution would have a few layers of protection.
You’d think they’d have some sort of anomaly detection looking at flows. How do you miss 32 GBs if data being exfiltrated?
If she worked there from 2015 to 2016, her login/access credentials should have been revoked when she left.
I don’t know if that falls on Cap One or Amazon, but either way, it points to a much more serious vulnerability, namely, that someone who has left should not be able to get back into the system.
It will be interesting to see what they turn up — and if they share it publicly.
I feel there is some under the table dealing happend between aws and capital one. I was hoping BRIAN KREBS will explore this angle. Last night I read the full complaint, I have no idea how can aws escape from this..
She used her knowledge from AWS to utilize the services but the exploit could have been done by anyone reportedly. They had a misconfigured “firewall” (WebACL) and a severely misconfigured Identity and Access Management (IAM) system.
Generally even AWS employees don’t get carte blanche access to customer accounts. By the reports of AWS employees I know, their access is severely limited and audited.
Can anyone tell me why aws is not at fault here?.She is employed by aws, insider threat, aws failed to detect one of their employees accessing the customer data. Which against the cloud user and cloud provider agreement.
No one detected the attack.
Even capital one where you have the TOR node IP accessing the s3 bucket, is it not an indication?. Where is all the ML and AI went??. Is that only for talk?
According to her esume she was only employed at AWS from 2015-2016. She wasn’t a current employee.
Not an insider threat. Just happened to work there in the past.
Also arrested at the same location during the arrest…
https://www.king5.com/article/news/seattle-man-arrested-on-firearms-charges-along-side-capital-one-hacking-suspect/281-9f92419f-e6ec-4c4a-a56a-c3ec7c409566
Check that link, I get “Access Denied”.
Thompson is, by the way, a man. He “self-identifies” as a transgender woman, but he is a man.
Why is that relevant?
Why is that relevant? Are you trying to imply that transgender people are mentally unstable?
That’s exactly what they are. Are you a moron?
Looks like a misconfigured principal in IAM role policy… [page.6] in this report.
https://www.justice.gov/usao-wdwa/press-release/file/1188626/download
Erratic just wanted to finally answer the question that has gone unanswered for years now…”What’s in your wallet?”.
It’s more like, “who’s in your wallet.” And what are they doing in there? Hmmm, CC numbers, bank acct card, driver’s license, let’s see what “we” can make use of – at your expense!
Glad I never applied for a Cap 1 card. So many other cards give better rewards. I pay everything on time, take the reward money and life is good.
My guess, since she has hacked other AWS instances/buckets before, is that she’ll cut a deal with the feds and become a confidential informant.
Checking on account been hacketts
Checking on my account been breached
I don’t know about the USA, but in Canada your Costco membership card is a Capital One credit card. I’m wondering if this breach affects that relationship.
Definite had some issues:
http://irclogger.arpnetworks.com/irclogger_log/arpnetworks/?date=2018-03-16,Fri
@Krebs When you said “Further investigation revealed that Thompson used the nickname “erratic” on Twitter,” – how did you find or associate the person’s twitter account? Can you elaborate?
Have you seen the complaint? It goes a bit in-depth under the investigation section about the attack methodology.
https://www.justice.gov/usao-wdwa/press-release/file/1188626/download
I called capital one today after my accounts were frozen. After someone used one of my cards. They are asking for three pieces of information that they want me to send them. A bill from of utilities to verify my “address”, “social security” and my “drivers license”… I thought they had this information. It makes me wonder why they need the information they already have. After being breached what makes them think I can trust them with more of my data… If they can’t secure the data I gave them…
And this is why you use Google Cloud … Encryption at rest and in transit BY DEFAULT!
I do love that about Google Cloud, but it doesn’t help when the company removes default security controls (SSH keys) on an instance and then grants it an Administrator role.
That’s good to know about google cloud. I keep telling people, you can have security in the cloud, but you need to pay for it and design around it.