If you bank online and choose weak or re-used passwords, there’s a decent chance your account could be pilfered by cyberthieves — even if your bank offers multi-factor authentication as part of its login process. This story is about how crooks increasingly are abusing third-party financial aggregation services like Mint, Plaid, Yodlee, YNAB and others to surveil and drain consumer accounts online.
Crooks are constantly probing bank Web sites for customer accounts protected by weak or recycled passwords. Most often, the attacker will use lists of email addresses and passwords stolen en masse from hacked sites and then try those same credentials to see if they permit online access to accounts at a range of banks.
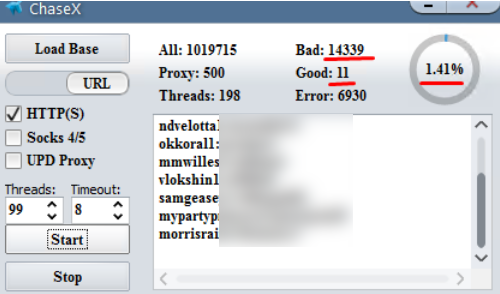
A screenshot of a password-checking tool being used to target Chase Bank customers who re-use passwords from other sites. Image: Hold Security.
From there, thieves can take the list of successful logins and feed them into apps that rely on application programming interfaces (API)s from one of several personal financial data aggregators which help users track their balances, budgets and spending across multiple banks.
A number of banks that do offer customers multi-factor authentication — such as a one-time code sent via text message or an app — have chosen to allow these aggregators the ability to view balances and recent transactions without requiring that the aggregator service supply that second factor. That’s according to Brian Costello, vice president of data strategy at Yodlee, one of the largest financial aggregator platforms.
Costello said while some banks have implemented processes which pass through multi-factor authentication (MFA) prompts when consumers wish to link aggregation services, many have not.
“Because we have become something of a known quantity with the banks, we’ve set up turning off MFA with many of them,” Costello said. “Many of them are substituting coming from a Yodlee IP or agent as a factor because banks have historically been relying on our security posture to help them out.”
Such reconnaissance helps lay the groundwork for further attacks: If the thieves are able to access a bank account via an aggregator service or API, they can view the customer’s balance(s) and decide which customers are worthy of further targeting.
This targeting can occur in at least one of two ways. The first involves spear phishing attacks to gain access to that second authentication factor, which can be made much more convincing once the attackers have access to specific details about the customer’s account — such as recent transactions or account numbers (even partial account numbers).
The second is through an unauthorized SIM swap, a form of fraud in which scammers bribe or trick employees at mobile phone stores into seizing control of the target’s phone number and diverting all texts and phone calls to the attacker’s mobile device.
But beyond targeting customers for outright account takeovers, the data available via financial aggregators enables a far more insidious type of fraud: The ability to link the target’s bank account(s) to other accounts that the attackers control.
That’s because PayPal, Zelle, and a number of other pure-play online financial institutions allow customers to link accounts by verifying the value of microdeposits. For example, if you wish to be able to transfer funds between PayPal and a bank account, the company will first send a couple of tiny deposits — a few cents, usually — to the account you wish to link. Only after verifying those exact amounts will the account-linking request be granted.
Alex Holden is founder and chief technology officer of Hold Security, a Milwaukee-based security consultancy. Holden and his team closely monitor the cybercrime forums, and he said the company has seen a number of cybercriminals discussing how the financial aggregators are useful for targeting potential victims.
Holden said it’s not uncommon for thieves in these communities to resell access to bank account balance and transaction information to other crooks who specialize in cashing out such information.
“The price for these details is often very cheap, just a fraction of the monetary value in the account, because they’re not selling ‘final’ access to the account,” Holden said. “If the account is active, hackers then can go to the next stage for 2FA phishing or social engineering, or linking the accounts with another.”
Currently, the major aggregators and/or applications that use those platforms store bank logins and interactively log in to consumer accounts to periodically sync transaction data. But most of the financial aggregator platforms are slowly shifting toward using the OAuth standard for logins, which can give banks a greater ability to enforce their own fraud detection and transaction scoring systems when aggregator systems and apps are initially linked to a bank account.
That’s according to Don Cardinal, managing director of the Financial Data Exchange (FDX), which is seeking to unite the financial industry around a common, interoperable, and royalty-free standard for secure consumer and business access to their financial data.
“This is where we’re going,” Cardinal said. “The way it works today, you the aggregator or app stores the credentials encrypted and presents them to the bank. What we’re moving to is [an account linking process] that interactively loads the bank’s Web site, you login there, and the site gives the aggregator an OAuth token. In that token granting process, all the bank’s fraud controls are then direct to the consumer.”
Alissa Knight, a senior analyst with the Aite Group, a financial and technology analyst firm, said such attacks highlight the need to get rid of passwords altogether. But until such time, she said, more consumers should take full advantage of the strongest multi-factor authentication option offered by their bank(s), and consider using a password manager, which helps users pick and remember strong and unique passwords for each Web site.
“This is just more empirical data around the fact that passwords just need to go away,” Knight said. “For now, all the standard precautions we’ve been giving consumers for years still stand: Pick strong passwords, avoid re-using passwords, and get a password manager.”
Some of the most popular password managers include 1Password, Dashlane, LastPass and Keepass. Wired.com recently published a worthwhile writeup which breaks down each of these based on price, features and usability.




So, as far as (standardized) Password Managers go – isn’t that just another single-point failure location for the bad guys, or am I missing something? RAT’s have gone after simpler credential sets on all sorts of private individual’s platforms iStuff/Win/Android – they just have to make exploits for the PM software and then you’re protection is gone. It’s a little like WWII submarines dragging along a surface flag, relying on being underwater to be safe… (well, almost…)
Password length, complexity and reuse is a bigger problem, and much easier to exploit. Previous breaches, dictionary, hybrid, brute force, etc…. are WAY more of threat than RATs.
So, if you could memorize 100+ long random passwords… then maybe you’re safer without a password manager. Or you could write them down, unless you fear physical intruders.
Rules for password construction to modify one complex password are easier to remember than complex passwords.
For $12/year you can pay for Google to host an email domain with forwarding for you, then set up your own complex authentication – an email address per signin and a password that varies using a scheme based on the site’s domain name.
Yes, I’ve used similar schemes before.
It is much better of course, but still only thwarts automation and adds a few steps for attackers. At best, it might require 2-3 or more breaches to figure out the correlation.
Using GMail’s username+uniquestring email scheme is good, but goes only so far.
It is good to have completely different unique email addresses too.
Variable passwords derived from a common memorable base, then modified for the domain is a good trick that I use too. For things not accessible with password manager. But I do worry, that if attackers brute force more than 1, they’ll figure out the commonality.
Especially if the base is memorable, as that part would be subject to dictionary hybrid attacks and clever mangling.
> “…a password that varies using a scheme based on the site’s domain name”
But wouldn’t that make it very unsecure? Unless I’m understanding it incorrectly, it seems as though that scheme is part of some algorithm on the back-end to come up with the password per account. That’s hardly increasing the security at that point as the algorithm can be easily guessable.
LOL your kidding. Googles databases are hacked so often that they dont even report it anymore.
I know this is controversial – is Yubikey really the best? I know the DoD uses that…
I exchanged email with the Bank of America VP in charge of account security. I asked her why they weren’t using U2F yet, especially since BofA was part of the group which developed it.
I got an answer back that they were “looking at all options”, which is likely “Form Letter B”.
Since they _do_ offer SMS codes, you’d think switching that to a TOTP (Google Auth-sytle) system would be a small change to their systems.
And I also bought their $20 One-Time Password card, only to find that “we’ll only ask for this for certain transactions”. None of which, apparently, have happened to my account. But this means that BofA currently _has_ infrastructure to deal with OTP codes, but for some reason refuses to make it available as part of the login process.
Yubikey? I’ve got several generations; I like them a lot. My advice is to buy one, use it where you can, use an Authenticator app where that works, and (unless you’re a high-value target) use SMS for the others.
I believe the DoD usage is limited to their PIV (“smart card”) capability, rather than U2F.
We should all push the financial institutions to adopt the SQRL way of logging in:
Instead of using a username, email and a password, SQRL uses an app to login to SQRL-aware websites.
When SQRL logs you into a website, your identity is a long code that looks like this: E6Qs2gX7W-Pwi9Y3KAmbkuYjLSWXCtKyBcymWloHAuo.
Your SQRL identity is a different long code for every website you login to, but it is always the same code when you return to a site you visited before. This means that websites never know who you are, but they do know when you return.
You may choose to remain anonymous to a website, such as when you post a response to someone’s blog. SQRL never identifies you by anything other than that long code.
In other cases you will want to be known, like when you use SQRL to login as you at Amazon, Facebook, Netflix, or your bank. In those cases, you would inform Amazon that that particular code is actually you. SQRL lets you do that.
The problem here isn’t that users want anonymity from the website they’re visiting. Tor would be MUCH better. SQRL only obfuscates the username, who cares?
Nobody uses SQRL, and nobody wants to. It is a GRC pet project that has no real world application.
Or simply don’t link your online banking to anything…
It sounds like some banks have taken that choice out of your hands by giving the aggregator sites read-only access based on just the user and password (entered into an aggregator account by the attacker). Sure, lack of a linked PayPal will keep them from attacking *that* to siphon the funds, but not from getting enough transaction information to either phis the customer or trick the bank.
+10
I wish banks had an option to provide 2 passwords, one for full access and one for read-only access. The 2nd could be used for Mint and Yodlee, etc. This way worst case, crooks could just see how little money I have and not take any 🙂
You missed the point. With read-only access I can still syphon money from your account. I just need to link your account to my account. When I set it up, my bank will send micro deposits to your account. I then just use my read-only access to your account to verify the micro-deposits. Then I move money from your account to my account, then wire the money to Russia. True story.
That is insane that they are now using the dollar amounts as a form of initial authentication.
They are so desperate not to disturb the customer for proper authentication, they they are essentially going backward toward knowledge based questions.
Read only access to my account would not allow you to move money from my account. If my account is A and your account is B and you link B to A, then you have to login into A with full access to move money from A to B. You can’t use B to pull money from A. It has to originate with A
You’ve never used a transfer site/app like Paypal, have you?
You can pay others from your bank account once you’ve “Verified” it’s yours by validating transaction amounts.
In Europe, most of, if not all banks and similar are providing a small “calculator” which computes pinS for various operations, login, pay, money transfer…
some also send you instant notification on SMS/email…
Problem: several banks, several calculator…
When I saw that in USA, they just implement pin for credit cards, no doubt that banks are more taking care of their profits than their clients! Just a signature on a piece of paper… nuts
Like for GDPR, clients should sue them for not being enough secure and they know it.
Problem: several banks, several calculator…
No Problem: The ‘calculators’ are usually the same with simply different branding so they work across banks and accounts.
Good to see passwords in the news and industry discussions, we use a Zero Knowledge Password Proof application that uses a one-time pad.
I’ve asked this question before and never really got an answer; perhaps some of the security experts on here with more knowledge than me can help. I set up 2FA using an authentication app since it is more secure than SMS. However, some sites, Amazon for example, allow you to choose what type of 2FA to use when you are logging in. Doesn’t that give a blackhat a way to circumvent the authentication app? What good is it to have an OTP app when it can be bypassed by SMS? Amazon requires a phone number with the account, so there is no way to unlink the phone from the login process. ???????
You can choose a different phone number for the 2SV (2 step verification). Just use a land line instead.
It is significantly more difficult to hijack a land line phone. Involves hacking telecom switches Mitnick style or hacking into VOIP systems. Use your office line maybe.
With SMS, yeah, there is a problem because those lines are made to be rapidly transportable with teenagers at thousands of local carrier stores across the country. So easy to bribe to Swap a SIM.
Land lines, much more involved.
When using a land line for 2SV on Amazon, you can select voice instead of SMS, and choose not to verify, so you can give a wrong number, and essentially disable this 2SV option (make sure you have Authenticator App OTP set up and working first).
Joe, thanks for the reply. It seemed to me, some years ago, that it was an easy thing to have a landline routed through a Google VOIP number; perhaps I am wrong on that. But, that it why I was avoiding the Voice over landline option; I didn’t think it was anymore secure than SMS. It is something I would look into, but I just discontinued my landline a couple of days ago. I didn’t use it and it was nothing but a pest with robocallers and non-profit telemarketers and illegal telemarketing calls. I’ll look over the 2SV options for a cell phone and see if I missed something. I wish Amazon would simply give me an option to not use a phone number at all for 2SV. I have the backup codes, encrypted, for the Authentication app in a safe place if I ever needed them. Again, thanks for the reply.
If you have a Google Voice (or Google Fi) number, they are marginally better as a recovery phone (or second factor), because they are tied to your GMail account, and hence more difficult to hijack or SIM swap. But yes, all sites that offer something more secure that SMS, and then still allow your phone to be used as a “recovery” mechanism have effectively neutered their more secure option!
>Many of them are substituting coming from a Yodlee IP or agent as a factor
So if you BGP hijack a Yodlee IP range or proxy through them, you can bypass 2FA and carry out spending actions too, presumably.
IP hijacking is trivial. You should NOT be using it for authentication.
It’s bad that some organizations don’t get this. They are being led by the nose with marketing from companies touting “network location” as an authentication factor.
Why don’t the banks offer Mint, etc read-only access?! So risky to give full access.
Sorry, didn’t see a link to ask you to consider reporting on the Urgent/11 vulnerabilities and the risks of any RTOS that is embedded and never updated.
https://armis.com/urgent11/
Thanks
My account balance is usually so pathetically low that no bad guys would consider it worthwhile to hack me.
Pretty sure I’m safe.
If someone controls your account, it doesn’t need a high balance. It can still be used as an intermediary for transferring funds among criminals.
How come they did not mention a finger print login? Is this not a safer method?
Biometrics are a terrible idea.
The biggest problem is that *when* biometric data is compromised [1], it can’t be replaced.
When a password is compromised, it can be replaced. When a username is compromised, it can be replaced. When a name is compromised, it can be replaced. When an SSN/SIN/… is compromised, it can be replaced.
Beyond that, what happens if your biometrics are permanently damaged (chemical burns: acid; metal: knife cuts…; biology: macular degeneration?)?
2FA (something you have, not something you are) is a much better thing.
[1] https://www.businessinsider.com/vulnerability-found-in-major-biometrics-system-2019-8
1. biometric authentication is perhaps the most idiotic security regime. It is permanently linked and does not ever change. There are proof of concept to spoof this in code. don’t ever let anyone tell you that fingerprint “security” is sound. It isnt! Think of it this way: you SSN is permanent and tied to you forever. Have that stolen and your toast! Same thing with facial recognition, voice and fingerprint. It is YOU, it never changes. And once (not IF) it is stolen, you are toast!
2. password managers (yes, even local only, non-cloud) are a disaster waiting to happen. Think about it from a comprehensive viewpoint: you are relying on YOUR computer and YOUR network and software to handle your password encryption. That zero day or speculative exploit that will be announced next year that shows your entire system was pwned for the last seven years (looking at you intel, spectre/meltdown!)…yeah, go ahead and “store your single point of hack failure on a demonstrably vulnerable machine and network..) yeah do do it! And about those router and modem exploits that still exist! yeah, your network is f/ed!
3. sms and auth apps running on your android phone? what could go wrong? about everything…first, the number of vuln/s in android is staggering..then the mobile network you navigate…pathetic! and you might have another bad app with access to root, unknown to you! or you have wifi discovery turned on and no secure vpn over a public pwned network! maybe even your own wifi router poorly configured or firmware corrupted!
take your pick…you are doomed…
security, is achieved when you physically control everything and remove as much as you can from the internet. period. period …period.
don’t be a sucker!
I always find it amazing how so many seem to be so willing to delegate the protection of their passwords to the cloud. A password manager that you fully control is OK; a password manager in the cloud is madness.
Unfortunately I’m going thru the process of attempting to recover my funds that were stolen aka transferred via PayPal to various accounts. My Wells Fargo account was wiped empty after a couple of small deposits were made. Not sure if directly related but it was around the same time I used Zelle for first time.
Recently, hacking of bank accounts of corrupt officials has been on the increase. I really dont blame people who ask hackers to help them do things like that cos they got the money in a very wrong way. that was why I didnt blame my brother when he said his new car and house was got from asking “eazihacker” on gmail to help him hack an account.
I appreciate kloviaclinks com tools form the $35,000 they sent me