Antivirus and security giant Avast and virtual private networking (VPN) software provider NordVPN each today disclosed months-long network intrusions that — while otherwise unrelated — shared a common cause: Forgotten or unknown user accounts that granted remote access to internal systems with little more than a password.
 Based in the Czech Republic, Avast bills itself as the most popular antivirus vendor on the market, with over 435 million users. In a blog post today, Avast said it detected and addressed a breach lasting between May and October 2019 that appeared to target users of its CCleaner application, a popular Microsoft Windows cleanup and repair utility.
Based in the Czech Republic, Avast bills itself as the most popular antivirus vendor on the market, with over 435 million users. In a blog post today, Avast said it detected and addressed a breach lasting between May and October 2019 that appeared to target users of its CCleaner application, a popular Microsoft Windows cleanup and repair utility.
Avast said it took CCleaner downloads offline in September to check the integrity of the code and ensure it hadn’t been injected with malware. The company also said it invalidated the certificates used to sign previous versions of the software and pushed out a re-signed clean update of the product via automatic update on October 15. It then disabled and reset all internal user credentials.
“Having taken all these precautions, we are confident to say that our CCleaner users are protected and unaffected,” Avast’s Jaya Baloo wrote.
This is not the first so-called “supply chain” attack on Avast: In September 2018, researchers at Cisco Talos and Morphisec disclosed that hackers had compromised the computer cleanup tool for more than a month, leading to some 2.27 million downloads of the corrupt CCleaner version.
Avast said the intrusion began when attackers used stolen credentials for a VPN service that was configured to connect to its internal network, and that the attackers were not challenged with any sort of multi-factor authentication — such as a one-time code generated by a mobile app.
“We found that the internal network was successfully accessed with compromised credentials through a temporary VPN profile that had erroneously been kept enabled and did not require 2FA,” Baloo wrote.
THE NORDVPN BREACH
Separately, NordVPN, a virtual private networking services that promises to “protect your privacy online,” confirmed reports that it had been hacked. Today’s acknowledgment and blog post mortem from Nord comes just hours after it emerged that NordVPN had an expired internal private key exposed, potentially allowing anyone to spin out their own servers imitating NordVPN,” writes Zack Whittaker at TechCrunch.

VPN software creates an encrypted tunnel between your computer and the VPN provider, effectively blocking your ISP or anyone else on the network (aside from you and the VPN provider) from being able to tell which sites you are visiting or viewing the contents of your communications. This can offer a measure of anonymity, but the user also is placing a great deal of trust in that VPN service not to get hacked and expose this sensitive browsing data.
NordVPN’s account seems to downplay the intrusion, saying while the attackers could have used the private keys to intercept and view traffic for some of its customers’ traffic, the attackers would have been limited to eavesdropping on communications routing through just one of the company’s more than 3,000 servers.
“The server itself did not contain any user activity logs; none of our applications send user-created credentials for authentication, so usernames and passwords couldn’t have been intercepted either,” reads the NordVPN blog post. “On the same note, the only possible way to abuse the website traffic was by performing a personalized and complicated man-in-the-middle attack to intercept a single connection that tried to access NordVPN.”
NordVPN said the intrusion happened in March 2018 at one of its datacenters in Finland, noting that “the attacker gained access to the server by exploiting an insecure remote management system left by the datacenter provider while we were unaware that such a system existed.” NordVPN declined to name the datacenter provider, but said the provider removed the remote management account without notifying them on March 20, 2018.
“When we learned about the vulnerability the datacenter had a few months back, we immediately terminated the contract with the server provider and shredded all the servers we had been renting from them,” the company said. “We did not disclose the exploit immediately because we had to make sure that none of our infrastructure could be prone to similar issues. This couldn’t be done quickly due to the huge amount of servers and the complexity of our infrastructure.”
This page might need to be updated.
TechCrunch took NordVPN to task on the somewhat dismissive tone of its breach disclosure, noting that the company suffered a significant breach that went undetected for more than a year.
Kenneth White, director of the Open Crypto Audit Project, said on Twitter that based on the dumped Pastebin logs detailing the extent of the intrusion, “the attacker had full remote admin on their Finland node containers.”
“That’s God Mode folks,” White wrote. “And they didn’t log and didn’t detect it. I’d treat all their claims with great skepticism.”
ANALYSIS
Many readers are curious about whether they should enshroud all of their online communications by using a VPN. However, it’s important to understand the limitations of this technology, and to take the time to research providers before entrusting them with virtually all your browsing data — and possibly even compounding your privacy woes in the process. For a breakdown on what you should keep in mind when considering a VPN service, see this post.
Forgotten user accounts that provide remote access to internal systems — such as VPN and Remote Desktop services (RDP) — have been a persistent source of data breaches for years. Thousands of small to mid-sized brick-and-mortar businesses have been relieved of millions of customer payment card records over the years when their hacked IT contractors used the same remote access credentials at each client location.
Almost all of these breaches could have been stopped by requiring a second form of authentication in addition to a password, which can easily be stolen or phished.
The persistent supply chain attack against Avast brings to mind something I was considering the other day about the wisdom of allowing certain software to auto-update itself whenever it pleases. I’d heard from a reader who was lamenting the demise of programs like Secunia’s Personal Software Inspector and FileHippo, which allowed users to automatically download and install available updates for a broad range of third-party Windows programs.
These days, I find myself seeking out and turning off any auto-update functions in software that I install. I’d rather be alerted to new updates when I launch the program and have the ability to review what’s changing and whether anyone has experienced issues with the new version. I guess you could say years of dealing with unexpected surprises on Microsoft Patch Tuesdays has cured me of any sort of affinity I may have once had for auto-update features.




This entry is very helpful, especially your analysis on it. I use this as part of my day job as a public librarian who gives monthly presentations on security (and cite KoS as a resource “to learn more”) to older patrons. While I haven’t discussed VPNs with attendees so far, that old 2017 entry may prove useful for discussing pros, cons, limitations, etc.
Secondly, I’m a bit puzzled as to the reference from a reader lamenting the demise of FileHippo. I checked the link as well as the FH website and the news section still has a recent article from Aug. 16th article (“Report: Your phone number reveals more personal info than your name”) and the list of software updates on the site is still current. I have not tried their App Manager in a little while and, last time I did, it wasn’t reliably working for me.
Thanks for the post!
As a former, longtime user who relied upon the Filehippo app to keep me aware of updates for non-OS software I use, your comment caught my attention. The FH site appears to be presenting old update information but simply posted with a current date in its own listing — the original release dates are presented accurately in the “Technical” tab of an individual app update listing. One example: SuperAntiSpyware is indicated on the FH “latest” page with an October 22nd date; the detail in its “technical” tab identifies it as v8.0.1044 dated June 26th.
When I discovered earlier this year that FH had stopped providing notice of updates on my systems, my subsequent investigation identified that the owner’s own domain name was no longer valid and the file updates were really stale, it seemed to be a zombie site.
So, I decided to abandon and completely remove its app from my systems as I no longer trusted what it might be doing in the background when scanning a system for update matches. While there are alternatives available for automated identification, I now just manually check the latest software downloads available at the MajorGeeks.com and Afterdawn.com sites every few days in order to keep my systems’ different apps up-to-date.
I suggest using Chocolatey.. https://chocolatey.org/why-chocolatey much more trustworthy
Thanks — am not familiar with it, but will check it out.
Try patchmypc as well. I moved to that after FH.
Good for you, Brian! I do not care to update most software automatically either–except for antivirus.
Since NordVPN is from Finland, I wonder if F Secure’s VPN is involved.
Regards,
Actually, NordVPN are based in Panama.
NordVPN is not from Finland. They simply had servers in Finlamd that were breached. Their servers were rented from another company.
Insidently, VPNs rent servers to get around no logs claims. If a VPNs rented server is being monitored by someone other than the VPN provider, the VPN provider can be legally in the clear for claims they make.
And since most large VPNs rent servers all over the world, it is easy for someone to target a server in an out of the way place to monitor or breach. Someone being state sponsored actors..
NordVPN is from Lithuania(company behind NordVPN is Tesonet), they only have shell company in Panama
Once again , multi-factor authentication with a USB token (Like Thetis) would have stopped and prevented both of these breaches
Actually, this is due to the lack of some positive culture being present in almost every corporation! The entire management level in most IT security companies has no clue about IT security and the common culture, that management is always at right does not allow constructive criticism of the nerds anymore! When it is more important, what words are used, than the message itself, every system is screwed and doomed already!
You hit the nail on the head. If Nord was actually committed to security at a corporate level then this type of breach would never have happened.
They lack the appropriate level of paranoia to be considered serious at this point.
Uninstalled, account cancelled.
C‘est la Vie.
Sounds like projecting. You cannot assume a corporate culture problem by the scant details of this breach.
“Corporate culture” has become a scapegoat used by people who don’t have any actual details, so just blame management. It could just as likely be a single contractor to blame.
What I’m wondering about is why people install all this crap software and then get puzzled over why their system gets breached? Do you really need a CCleaner app? It won’t make your system faster. Remove all those crap apps will.
Also the VPN is provided for free in Firefox as a “Firefox private network” add-on from Mozilla. Then Firefox as well provides a feee secure DNS service. Why pay to some company for VPN?
Dennis, you mentioned why people install crap software and then cite to use a browser add-on. Malicious add-ons are just as bad, if not worse, than most software. Add-ons update automatically which means if you have a legitimate add-on that later is updated with malicious software or gets hacked, that is automatically updated in your browser. Any add-ons that you add into your browser is only increasing the attack surface (much like any piece of software, really).
It’s hard to find a trusted add-on. I remember a while back I was searching for “AdBlock”. Well, I found “AdBlock” and just about every combination of Ad+Block you can think of. Sure, you can go by ratings and reviews to narrow the search, but it shows how many crap add-ons there are as well.
I trust DuckDuckGo more that any other ad blocker I’ve used in quite a while. It has more granular control as well – but then I don’t block KOS or other ad dependent sites that I want to survive on the web.
It also sets chrome so Google can’t look down your shorts anymore. It actually speeds up the chrome browser in the process! YMMV..
I like startpage.
Okay, thanks! I’ll check that out.
Actually at an enterprise level an application such as CCleaner Cloud is very useful for removing buildup of system trash and unnecessary log files, for cleaning out registry errors, for monitoring system health, for controlling startup applications and for many more reasons. When you have 50+ computers, it is an indispensable tool to maintain uptime. Think of it as flossing your teeth on a regular basis…
As far as I know, the only thing CCleaner does that your operating system file cleaner doesn’t is remove LSO’s and zombie files. If I could find a reputable cleaner that did the same thing faster I’d go for it, because CCleaner is getting slower and slower. Plus it was bought by Alwil (AVAST), and pops up ads often.
I’ve know for quite a while that it cleans the file structure enough to get rid of attack packages left behind in various HTML files and downloads. I’ve tested it for that, and if you operate as a restricted user, it is almost just as good as an anti-virus.
I do still have to be aware of any desktop behavior that indicates a drive by adware attack though. Even legitimate sites can get to you. Make sure the UAC is still fully functional, and don’t give anything permission that you are sure you didn’t originate yourself, and CCleaner can take care of business.
However even I get fooled once, and thought Skype was updating when I opened it after I knew I’d been compromised by a drive by ad attack. I got lazy and didn’t run the cleaner, and then fell asleep at the wheel when the UAC prompt went off upon opening Skype. No Skype was not updating – the malware is getting more and more sophisticated now, and waited until I tried to open an app before attacking. That’s what happens when you get arrogant and complacent. I’ll admit it – shameful but I’ll admit it!
I have been reviewing updates prior to installing them for as long as I remember. It was part of my job for a while. I did recommend auto-updates for friends and relatives, but like you I am changing my stance. Too bad Microsoft has made that option so hard to exercise.
I cannot understand how these two security oriented organizations do not have a handle on their infrastructure. There are a lot of tools available to inventory your networks and the device configurations. Periodic audits of devices, configurations, and accounts is a fairly basic security item for organizations of their type and size. I managed to do it on a limited manpower group. You cannot manage what you don’t know.
From Tom’s Guide:
“NordVPN, TorGuard Admit Being Hacked, But That’s Just the Beginning”
https://www.tomsguide.com/news/nordvpn-torguard-admit-being-hacked-but-thats-just-the-beginning
And from ARS Technica:
“Hackers steal secret crypto keys for NordVPN. Here’s what we know so far”
https://arstechnica.com/information-technology/2019/10/hackers-steal-secret-crypto-keys-for-nordvpn-heres-what-we-know-so-far/
That pastebin contains a DHCP server which belongs to Hetzner, who have a datacenter in Finland. So if we trust NordVPN claims then Hetzner servers have a backdoor.
bloomberg claims the hosting provider in question is creanova (they probably just lease dc space from hetzner)
No, Creanova does not lease DC space from Hetzner – Creanova existed way before Hetzner did – they run their DC out of Espoo
A utility for updating third-party Windows programs that some might find useful is Patch My PC:
https://www.lifewire.com/patch-my-pc-review-2625194
1. Re the above about VPN on Firefox: — VPN is also available in Opera.
2. Re updating third party programs: – the above-mentioned Patch My PC patches 300 programs (or as many of them as you have on your pc) in silent mode which makes it very easy to use. It includes Flash updates. I have used it for at least a year and find it excellent.
Maybe for the more detail oriented (not to say, anal retentive, yes, that’s my reflection I’m looking at in the mirror…) of us here, turning off (or at least setting a delay) on automatic updates might be a positive security trade-off.
However, for the great majority of users, the risk they run of not updating at all/ forgetting for quite a long time and being vulnerable, is far greater than the risk from hacked automatic update mechanisms.
We must be careful about to which audience we suggest what set of balanced compensating security controls, always remembering that manual/administrative controls are the weakest, and most users are weak at those.
This is very much the case. For all but a few individual PC power users it is auto update or no updates. Even in corporate environments…well how many breaches have a failure to update some piece of software as (at least part of) their root cause? Going back to at least 2003’s SQL Slammer, where a patch was available months before the incident but not widely deployed, we’ve seen the need for auto-update. So unless you are almost pedantic about having processes to evaluate and apply patches in a timely manor without using auto update, use auto update.
NordVPN playing the blaming game with the data center provider:
https://www.bloomberg.com/news/articles/2019-10-21/after-twitter-allegations-nord-vpn-discloses-2018-breach
The problem isn’t 2fA absent from remote access accounts; the problem is remote access accounts with the ability to enact changes and view company secrets. Everything should need to be done on-site by credentialed employees.
If that’s too hard, your business is overextended and asking for trouble.
I agree. There are ways that an attacker worth their salt can bypass MFA. I was pleasantly surprised to find out the sheer amount of ways that MFA can be bypassed. Of course, this all depends on the setup and the other factor(s) in use, but it’s most certainly a misconception to believe, “If I add MFA, I’ll be protected from everything.” It’s terrible practice to have remote access accounts exposed to the internet, but then think MFA will cure your misconfigurations, rather than assessing the accounts and determining if they are truly needed or not and using MFA in tandem–not in place of–other controls. On the same hand, can’t a jump server / bastion host be used for needs such as that?
“using MFA in tandem–not in place of–other controls.”
I fully agree. Most reputable MFA providers will say this too. That you should “add” MFA, and as a requirement, not an option. The attackers who “bypass MFA” are actually just exploiting yet another “misconfiguration”. Setting up MFA to be bypassed is often accidental, but sometimes directed by management looking for convenience and doesn’t understand.
“It’s terrible practice to have remote access accounts exposed to the internet”
Well, that is what makes them “remote”, right?
Do you suggest putting them behind a VPN ;)?
“can’t a jump server / bastion host be used for needs such as that?”
Yes, this is what I often recommend for critical servers that need remote access. It can be considered another factor, a trusted source.
“Everything should need to be done on-site by credentialed employees.”
Well, that is not how the world works. Lots of companies cannot have on-site credentialed employees. It is way to expensive to staff employees at, or traveling to hundreds of datacenters around the world. It would be folly for a company to do that, charge $50/mo for VPN, just because they don’t trust remote management.
That is not “overextended”, that is called a global business model.
Version 463 of Ccleaner installed two trojans on my computer. Fortunately, Kaspersky removed them very fast. Ccleaner will no longer be used here along with any other Avast products. Some of the tech sites I visit regularly are no longer recommending Avast products either.
Let this be a reminder that Cloud is just outsourcing your data center, and anyone that has physical access to the servers you run on has admin access to your system.
Though you point out that the main issues were phantom accounts, one of the biggest issues I saw with the NordVPN breach was that they had no idea what was connected to their network.
“[…]the attacker gained access to the server by exploiting an insecure remote management system left by the datacenter provider while we were unaware that such a system existed.”
You can’t secure or maintain what you don’t know about. Sloppy inventory management.
I wasn’t Nord’s own infrastructure or data center but a rental, that’s the problem.
thanks for this info… I agree. There are ways that an attacker worth their salt can bypass MFA.
Performing anti-virus scans on servers as I write and removing stale Dial-In permissions from AD accounts due to this breach by Avast. It’s better to be proactive than to be sorry.
That being said, I would recommend that VPN’s for the private sector are only useful when used in places with public WIFI. I would not recommend a VPN for commercial use unless I controlled the server endpoint., and it had the latest encryption technology. If your business takes credit card payments on premessis, you will fail PCI compliance if you are using legacy encryption (3DES/Diffie-Hellman Groups 1 to 5) such as you have in Windows Server 2012 with L2TP/IPsec…
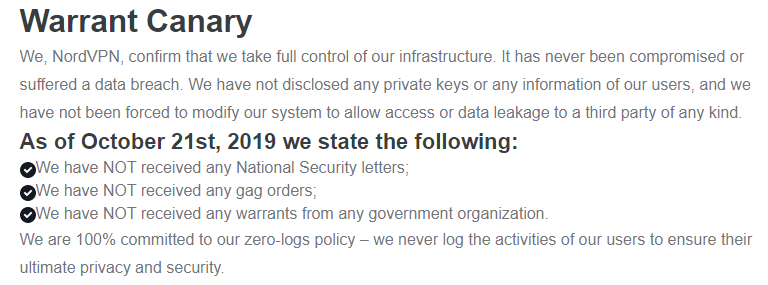
It’s a little twisted for them to state “We have not received any National Security letters, gag orders, or warrants .” when they outsource their infrastructure. The letters, orders, and warrants can be served on their providers. Plus, the providers probably have full logging.
Any company that uses cloud services is in the same position. Why would the government subpoena the data owner, who would fight the subpoena, when the cloud provider will hand over whatever is subpoenaed.
Well, the datacenter as a provider of hardware, doesn’t have the same access as the data owner, the VPN provider.
It isn’t the same level of access.
If law enforcement in any country were to coerce the logs from the datacenter, they would be able to see IPs, access time, bandwidth used… all the stuff visible from OUTSIDE the tunnel. Pretty much the same that your local ISP would have.
But even with the servers being located in the data center, that doesn’t directly give them access inside the encrypted tunnels. That is why this breach was serious, because the remote admin access got ‘inside’ by exposing the private keys to the VPN tunnel.
So no, the subpoena would not give them access to the kind of logs that a VPN user might be worried about. Pretty much, no more than the ISP knows (you connected to VPN at this time, for this long, and used this many bytes).
The real risk would be to subpoena the hosting provider to then compromise all future VPN traffic for all users. But that isn’t the same as “keeping logs”.
I on the side that tries to never auto update anything, even the apps on my phone I go through one by one when I want them updated.
And I’m not a fan of “cleaner” programs. I see people using them on Macs as well and don’t understand why. Often they are advertised as making your computer run faster which is usually untrue.
I’d agree with the comment about using VPNs in a public space. I don’t use public wifi very often. I will try to use cellular first. On hotel stays, especially longer trips it is often unavoidable.
I’ve never been a big fan of always on AV tools either. In some cases they may be unavoidable but for home use I don’t do much downloading and would prefer to run something on my time frame.
There’s an implied assumption that your cell provider is relatively secure. I would assume that all large US-based ISPs (including cellphone providers, cable cos, and telcos) are routinely monitoring traffic for their own use (and for sale), and are providing a copy to the Utah Data Center of the NSA.
A VPN provider like NordVPN at least PRETENDS to be more secure.
I would like to chime in on the autoupdate on phones. What change logs are you reading to see what is patched in App SW updates? I never see any. Being an Android user, most updates generically say “Bug fixes and user experience improvements”. Looking at my last Walmart app update, “Our engineers work diligently behind the scenes, providing Walmart Customers with the best app experience. …” They mention generic improvement to pharmacy and store features. Basically, how would you make a go/no-go call on this information? Why not just autoupdate on phones with such meaningless update information?
I owned a brick-n-mortar computer repair shop for 17 years. Several years ago I was chasing down an infection and found that an HP update was used to infect the computer. I notified HP and they said they would look into it but….
Now, as a matter of course, I removed any and all automatic updates to applications and drivers.
I’ve had Avast Security on my Mac for years. Today, the same day that I learned of this hack, Avast has for the first time ever prompted me to enable ‘full disk access’. Being a suspicious type, I’ve not done so. Any thoughts on whether this is coincidental timing, or something to be concerned about?
I think you’d be better off with Malwarebytes Anti-Malware for Macs. It’s not free, but I’ve grown more trusting of it than Avast. Avast is okay for folks that just can’t afford an active anti-malware with real time protection.
Cc cleaner is no longer useful also we have no trust in so called “security software”
There is evidence that VPN’s are not secure as promoted buyer beware.
Previous compromise of Avast CCleaner was discovered in Sept 2017, not 2018 as this article states. Off by a year.
Just as most companies have a page with Terms and Conditions and a page with “Privacy”, they should be required to have a page with Security news.
Further, we need a law which states that all members of a companies board of directors can be legally held responsible for the accuracy of statements on the Security page.
In this case, some sites have reported that NordVPN tried to minimize the seriousness of the breach by stating that the certificate was expired. It was not expired when compromised, only when discovered. That is willful misrepresentation of the seriousness of the breach.
We need less laws, not more.
If a company lies or withholds information you want disclosed, hire a different company for the service you need or complain loudly.
Don’t have a choice, because of a monopoly? Take out a 30 second TV ad. Visit their offices. Protest them at trade shows. Appear on the earnings calls. Petition their boardrooms. Write an op-ed in the newspaper. Piss in their lobby.
But don’t make the mistake of believing that more government would help. It’s just as likely to take notice of you with deadly force.
This is an absurd opinion based on ignorance and fear. The criminal hackers would absolutely love this anarchy nonsense.
Hackers benefit and revel in places with little to no regulation.
“Complain loudly” only works when there is a legal basis for anyone to listen. Yeah, you could just take your business elsewhere… but that means companies can simply insure themselves against the minor loss of business by cheating even more. When companies are not compelled, they usually just write it off, and it pays to lie cheat and steal if the only consequence is losing a few customers.
Laws are meant to protect people who cannot afford to buy TV ads or op-ed columns, don’t have enough shares be allowed in boardrooms or to be noticed on an earnings call (only works for public companies anyway). BTW, you do realize that customers and shareholders aren’t the same people, right? They are usually at odds, where shareholders encourage pushing legal limits or cheating customers if it means more profits.
You could piss in their lobby… but again, you assume there is a lobby to piss in. This is the internet age, where many of the companies don’t have big corporate HQs but have a distributed model across the globe. Also, the law then works against you, for trespassing, etc.
Sensible laws that are updated for the Internet Age isn’t the same as “more government”. So go back into your bunker. Laws concerning fraud and consumer rights should be updated and include disclosures as Mike suggested. And opposing that on the basis of your “govment=bad” ideology doesn’t even make sense here.
Who ever wrote that analysis is way behind the times. You can no longer get Secunia PSI, and I think the whole company was sold out to somebody who ripped it up and claimed it for their own security solution. I wished I knew who, because I would have gladly paid money to get it back.
File Hippo’s “Application Manager” is dead in the water, and I need to uninstall it, because it doesn’t work anymore – and by the way Secunia’s auto-update never worked for me anyway. I never actually used it to update, but just to get notifications that applications were out of date, or no longer serviced by the originator. That alone was priceless information.
I quit using Avast when it came down to a decision as to whether I was going to keep my life long license to MBAM or drop Avast free. Since I already paid for MBAM, I decided to drop Avast, because they were no longer compatible. I was only using it so I could gain insight into any problems my indigent customers were having with the freebee anti-virus.
This whole accident/incident is something out of proportion. I till now, don’t want to say a lot about it, and encourage people to read as many different sources as they can, to have arguments from both sides, and then decide. The discussion here is fascinating btw, so guys, also read this one https://vpnpro.com/blog/nordvpn-security-breach-between-fact-and-fiction/ Just to have the other side of opinion 🙂
I like to make huge lists of servers owned by VPN providers for research and other stuff so, to blow the cover off, the provider was Packet Exchange Limited.
(ISP: Fiber Grid Inc.)
If needed, I can provide the server IP’s, DNS records and even screenshots of the IP’s being used.
Tech crunch played it well, creating such a crazy story with lots of maybes and doubts. For me everything seems clear – Nord is their competitor (as Tech crunch is owned by a company who has a Vpn service). I can’t really get another thing – why everyone believes in this so called “journalism” and no one cares to research and understand what actually happened ?? Restore privacy wrote an article about this situation: https://restoreprivacy.com/nordvpn-hack/