Microsoft today released updates to plug security holes in its software, including patches to fix at least 74 weaknesses in various flavors of Windows and programs that run on top of it. The November updates include patches for a zero-day flaw in Internet Explorer that is currently being exploited in the wild, as well as a sneaky bug in certain versions of Office for Mac that bypasses security protections and was detailed publicly prior to today’s patches.
 More than a dozen of the flaws tackled in this month’s release are rated “critical,” meaning they involve weaknesses that could be exploited to install malware without any action on the part of the user, except for perhaps browsing to a hacked or malicious Web site or opening a booby-trapped file attachment.
More than a dozen of the flaws tackled in this month’s release are rated “critical,” meaning they involve weaknesses that could be exploited to install malware without any action on the part of the user, except for perhaps browsing to a hacked or malicious Web site or opening a booby-trapped file attachment.
Perhaps the most concerning of those critical holes is a zero-day flaw in Internet Exploder Explorer (CVE-2019-1429) that has already seen active exploitation. Today’s updates also address two other critical vulnerabilities in the same Windows component that handles various scripting languages.
Microsoft also fixed a flaw in Microsoft Office for Mac (CVE-2019-1457) that could allow attackers to bypass security protections in some versions of the program.
Macros are bits of computer code that can be embedded into Office files, and malicious macros are frequently used by malware purveyors to compromise Windows systems. Usually, this takes the form of a prompt urging the user to “enable macros” once they’ve opened a booby-trapped Office document delivered via email. Thus, Office has a feature called “disable all macros without notification.”
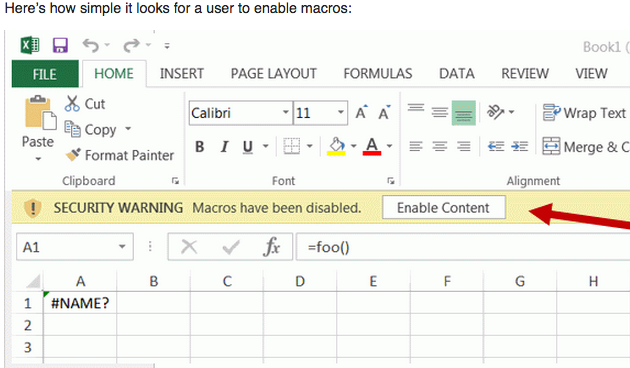
But Microsoft says all versions of Office still support an older type of macros that do not respect this setting, and can be used as a vector for pushing malware. Will Dormann of the CERT/CC has reported that Office 2016 and 2019 for Mac will fail to prompt the user before executing these older macro types if the “Disable all macros without notification” setting is used.
Other Windows applications or components receiving patches for critical flaws today include Microsoft Exchange and Windows Media Player. In addition, Microsoft also patched nine vulnerabilities — five of them critical — in the Windows Hyper-V, an add-on to the Windows Server OS (and Windows 10 Pro) that allows users to create and run virtual machines (other “guest” operating systems) from within Windows.
Although Adobe typically issues patches for its Flash Player browser component on Patch Tuesday, this is the second month in a row that Adobe has not released any security updates for Flash. However, Adobe today did push security fixes for a variety of its creative software suites, including Animate, Illustrator, Media Encoder and Bridge. Also, I neglected to note last month that Adobe released a critical update for Acrobat/Reader that addressed at least 67 bugs, so if you’ve got either of these products installed, please be sure they’re patched and up to date.
Finally, Google recently fixed a zero-day flaw in its Chrome Web browser (CVE-2019-13720). If you use Chrome and see an upward-facing arrow to the right of the address bar, you have an update pending; fully closing and restarting the browser should install any available updates.
Now seems like a good time to remind all you Windows 7 end users that Microsoft will cease shipping security updates after January 2020 (this end-of-life also affects Windows Server 2008 and 2008 R2). While businesses and other volume-license purchasers will have the option to pay for further fixes after that point, all other Windows 7 users who want to stick with Windows will need to consider migrating to Windows 10 soon.
Standard heads-up: Windows 10 likes to install patches all in one go and reboot your computer on its own schedule. Microsoft doesn’t make it easy for Windows 10 users to change this setting, but it is possible. For all other Windows OS users, if you’d rather be alerted to new updates when they’re available so you can choose when to install them, there’s a setting for that in Windows Update. To get there, click the Windows key on your keyboard and type “windows update” into the box that pops up.
Keep in mind that while staying up-to-date on Windows patches is a good idea, it’s important to make sure you’re updating only after you’ve backed up your important data and files. A reliable backup means you’re probably not freaking out when the odd buggy patch causes problems booting the system. So do yourself a favor and backup your files before installing any patches.
As ever, if you experience glitches or problems installing any of these patches this month, please feel free to leave a comment about it below; there’s a decent chance other readers have experienced the same and may even chime in here with some helpful tips.
Update, Nov. 13, 11:34 a.m.: An earlier version of this story misstated some of the findings from CERT/CC, and misspelled the name of the researcher. The above post has been corrected.




Thanks for the reminder to update, but I haven’t been successful updating two desktop and one laptop since early summer of 2019. They all run Windows 7 and most important updates fail and cause the computers to lock up and eventually run the windows repair utility. Have spent alot of time searching for a good solution to no avail. Since update support for Win 7 ends in a couple of months, I have disabled MS Updates in order to not be inordinately irritated each month by a company that can’t even supply users with good, reliable updates. Microsoft has become a major disappointment.
Hi John,
I had the same problem a while back. Head over to the forums at sysnative.com and post your problem there. They have Windows experts and sorted my problem in a couple of hours.
Amen, brother, and cursed be KB4519976! Attempts to install this “essential” October “security” update on my W-7 laptop has left the latter dead in the water, circling a drain eddy of unrelenting system restores, computer “repairs” etc. Having jumped through as many hoops and more as you have, I am still trying to get out from under this “update attack.” To make things worse, it’s my sole, un-networked work computer.
Like you, I disabled automatic updates years ago. Probably also like you, I have waited a week past Patch Tuesday every month to be reasonably assured there were no problems with the latest update. Somehow I slept through the alarm clock this time.
Why worry about malicious actors and their malware when you have MS to cut you off at the knees?
Haha. Agree. My old Dell Windows 7 kept updating the same 5 updates for weeks 18+ months ago. I did every repair until reinstalling Windows was the final “solution” . It stopped even trying to update. I use Firefox and do only very specific browsing to a short list of secure sites. No question many have more problems with Windows updates than with malware.
You probably are used to hearing this, but that’s not normal. Instead of opening yourself up to ethical & security issues, a better idea would be to take your system to someone and have them investigate what’s wrong with it. Because there is something wrong with it. That’s not normal. That’s not necessarily the fault of the updates.
Given that it’s been ongoing for that long it’s got to be the fault of something that’s been installed to the system. Better to get it fixed rather than end up the victim of identity theft, ransomware, etc.
I can’t tell you the number of people who’ve brought their systems to me with free antivirus programs installed with all kinds of weird issues. To the last the reason they were having weird issues is because they were infected up the wazoo.
That is what I was thinking. If I were him, I’d have someone with a clean machine, burn the latest rescue disc from Kaspersky and nuke the drive from space.
I totally agree. Time to move on to another provider.
99% of the time for failed updates are for two reasons: firewall/AV is blocking the downloand and 2. The download folder where MSFT places the patches prior to execution is full or corrupted. Both are easy fixes, disable your firewall/AV then re-run windows updates (manually). delete the contents of the patch repository, they’re good for roll-back purposes but I’ve seen where for some reason new updates don’t like it.
@ JohnNicholson: I heartily endorse your comments.
MS has become a disgrace and has not shown ANY remorse for the havoc and uncertainty it has created.
My problems are identical to yours but I use Win8.1Pro
which I do not have the courage to install the Updates since the September Updates and subsequent roll-ups.
The usual barrel of laughs… And no, my Mac does not run anything out of Redmond…
Thanks, Brian.
And you are not using the last macOS, because of its many bugs? And you did not mention last autumn update problems with Safari? Do you REALLY think you are using a very complete product?
Internet users need to stop using Adobe Flash Player !
Internet users will have no choice but to stop using Adobe Flash Player next year when Adobe ceases providing support at the end of 2020. With the caveat, however, that you can’t fix stupid.
Sometimes it’s not up to the user. For instance, Xfinity Stream uses Adobe Flash on both Windows and OS X running in a browser. Works just fine without Flash on iOS, tho. So Internet developers will have to stop using it as well. I’m sure for cost reasons many of them will wait until the last possible moment to migrate their content.
Friends don’t let friends use Comcast, no matter what they rename themselves.
That Comcast is this far behind the times and still using Flash is precisely why nobody should ever have anything to do with them. That kind of neglect and incompetence is the norm for them.
I would generally like to get my users away from flash, unfortunately our vendors use flash.
No, no I don’t think I’ll be participating in this one. Thanks Ubuntu. Switched last month, haven’t looked back.
Same here except I switched to a Chromebook in 2012. Not that I trust Google all that much! Had I got into IT like I thought I might(realized at 57 I’m far too old!) I would be forced to keep up with all this Windoze stuff.
Larry never to old I got into IT when I was 57 and I am now 70 and still doing it. Go for it.
IJAC
Brian, the article you cited on managing Windows 10 updates is from January 2018. Microsoft introduced some new controls in more recent versions of Windows 10 (1803, 1809, and 1903 builds) that make this a little more user friendly. The 1909 build rolls out this week. Looks like there is room for improvement.
See:
https://www.windowscentral.com/how-stop-updates-installing-automatically-windows-10.
https://www.ghacks.net/2019/09/06/surprise-microsoft-changed-windows-update-behavior-for-the-better-in-windows-10-1903/
I’ve delayed WU on my Win10 1903 machine for a few days until there was some feedback on this month’s round, but since that deferral option isn’t available I went ahead with them on my 1809 machine — all processed without trouble. The Win7Ult machine processed everything except MSRT, which consistently fails with the error 800B0109 — a number of people have reported the same issue on a ghacks blog Woody references, and the thread on the AskWoody forum covering the updates seems to indicate that it’s a sequencing problem. Someone there has provided links to the relevant manual downloads and installation sequencing protocol, so I’ll try that tomorrow and see if the gremlin is banished or remains present.
There was a servicing stack update that was required that WU downloaded and installed this morning which took care of the MSRT issue on that W7U desktop. All seems good with it at this point, and I’ve re-enabled the W10H 1903 laptop so the cumulative update is now being downloaded and installed on it (though it doesn’t reference 1909).
Hi JimV,
Thank you so much for your comment. I have been trying to resolve this issue for hours and getting nowhere. In the future I should probably wait a few days before patching up.
Thanks again,
Win7
If WU is still not installing the MSRT patch properly and delivering that same error, download the tool and run it manually — you can select whether to do a quick scan or deep/thorough scan, but recognize the deep scan will take awhile to run through to completion. The following link is for the 64-bit version; if you need the 32-bit version, just search the Microsoft download page on “MSRT” and it should bring up all the different options.
https://download.microsoft.com/download/2/C/5/2C563B99-54D9-4D85-A82B-45D3CD2F53CE/Windows-KB890830-x64-V5.77.exe
More on this issue over at AskWoody:
https://www.askwoody.com/2019/born-microsoft-incorrectly-signed-the-msrt-update-thats-been-bouncing-around-its-fixed-now/
Windows Update for November 2019 did a terrible job on my laptop. I can’t use my keyboard and other controls. It’s good as I can’t use my laptop at all. Do you guys have any I idea to fix this?
Apparently Microsoft still gives free support for Windows 10 as long as it is an update issue. My sister called MS and they RDP’d into her computer and worked on it for two hours and finally had to give up. She ended up buying a new computer! Maybe your luck will be better. It is very difficult to find the 1-800 number but it is out there somewhere on Google. Once you get hold of them, they will try to obfuscate whether you are eligible for support, but all you have to do is firmly tell them it is an update issue only, and they have to give you support.
I had the same issues with November Update for Windows 10 1903, a few days ago.
I got another update KB4524570, this time it fixed the problems with my keyboard, cut & paste, File Explorer bugs, etc.. but now Oracle VirtualBox isn’t working anymore.
VMware Workstation Pro 15.5 x64 though is working perfectly again.
Microsoft has been doing some funky stuff the past 2.5 months or so. Most of their patch updates seem to break something, then they rush a fix out that fixes what they broke, but then makes another problem somewhere else.
A couple patches ago (2-3 weeks) VMware Workstation stopped working, VMware updated fast to fix problem. Windows updated again and broke copy paste click and drag to guest os etc.
and broke it in the host win10 os too.
I hope they will figure out what they’re doing. I’m giving up Microsoft Windows 10 for my New Year’s Resolution.
Only Linux & macOS for me from now on.
@Brian These posts and the accompanying comments are always gloom and doom. Yes, Microsoft is trying to get people to voluntarily update 1 billion PCs, every single month.
The world has changed and all software makers are doing their best to change with it but people like our friend john nicholson insist on running dying OSes. We no longer live in a world where you can use your museum piece computer securely.
Yes, as long as people write code, there will be vulnerabilites. Microsoft in particular is trying to improve on 30+ years of code while trying to be as backwards compatible as possible.
So Brian, let’s not tar Windows or MacOS or Chrome with the same brush as we do Adobe or Equifax. It’s important to recognize how much the OS and browser makers are working to make their products more secure each day.
And if you keep up your end of the bargain and update as soon as possible, then everyone wins.
Bottom line: Every patch released is not a failure, it’s a success.
Are you on M.S.’s payroll?
Hahaha – well said Larry
Touche’ As I read his comments, that exact thought kept bouncing around in my thick skull:-)
Carl, thanks for your message. I care less about hurting Microsoft’s feelings that about giving people useful information about how to avoid major problems. It certainly seems to me (unscientifically and anecdotally at least) that MS has been having more issues than usual with its updates lately. Yes, you can say well there are a billion PCs and lots of variety, but that’s hardly the user’s concern.
Like you quipped – “Windows Exploder” – very accurate statement as far as I’m concerned; even if it was redacted. 🙂
@Brian, I have seen major problems with Microsoft Updates for Windows 10 1903 versions for the past 3-4 months especially.
Microsoft updates “broke” functionality of:
my built in web camera
my built in WiFi adapter
created graphics errors and non responsive windows file explorer issues when cutting and pasting or moving files around in File Explorer
VMware Workstation Pro 15 (actually corrupted my vm and I lost data)
Oracle VirtualBox
and a lot of other weird quirky things like:
.NET error messages
Visual C++ error messages
I have VLSC account and can download an ISO from last year from Microsoft, but I was hoping that they would just get their act together and get with the program.
I have lost about 40 hours of productivity every patch that fails.
I am gonna switch back to Apple macOS as my primary computer platform & Linux, of course for my lab setups and servers.
I enjoy your site man. Thanks.
Keep it up Brian please.
You are a very well respected voice in this mire of a wilderness and there’s just a glimmer of hope that INTRANSIGENT MS will get the message
BECAUSE it ain’t them left holding the baby and paying for our losses – and leaving us with problems that the ordinary computer technician just cannot undertand or deal with.
The funniest comment of late was on this Forum I think ran something like this – “Why bother about ransomware when we have MS to contend with?
(wish it had been my comment hahaha)
Today Google News saw fit to have a separate category for Windoze Updates–and KrebsonSecurity was the lead entry. Congrats!
fyi
Lots of people having problems with
win 7 64
wont install
Windows Malicious Software Removal Tool x64 – November 2019 (KB890830)
I can probably solve it with work around
bu…. various times in the day the site to download manually returned with
( Microsoft message) page encountered errors
later in the day it started showing site part English and part another language
including the servicing stack for Nov as explained below.
(explaining error)
https://social.technet.microsoft.com/Forums/en-US/41557079-7c15-4847-88e6-9b2f25942ffb/latest-windows-7-quotmalicious-software-removal-toolquot-installation-failure?forum=w7itprogeneral
Thought it had to do with
new service stack signing for Nov
looked there for answer
googled
Servicing stack update for Windows 7 SP1 and Server 2008 R2 SP1: November 12, 2019
top result
https://support.microsoft.com/be-by/help/4523206/servicing-stack-update-for-windows-7-sp1-and-server-2008-r2-sp1
sidebars in another language
didn’t trust that
searched
Microsoft catalog update pick win 7 64
clicked on
Windows Malicious Software Removal Tool x64 – November 2019 (KB890830)
not the download link but the description.
normal information
but if you click more information
https://support.microsoft.com/be-by/help/890830/remove-specific-prevalent-malware-with-windows-malicious-software-remo
you get English with sidebar in another language.
maybe this is normal?????
sorry long day hope it makes since
Tom, I get the same strange page with what looks to be a Russian sidebar. I don’t know what to make of it – except mistrust.
I read on ZDNet, that Technet and other services were going to be dumped together with other tools and the name changed. Maybe they’ve done that already. I would have thought there would be a page redirect though.
If you’ll look at the URL in your post and change the \be-by\ to \en-us\ the sidebar language changes accordingly. A quick search reveals that the be-BY is language code for Belarusian.
English version URL below.
https://support.microsoft.com/en-us/help/890830/remove-specific-prevalent-malware-with-windows-malicious-software-remo
Hello Brian,
Are you familiar with “0Patch” for Windows 7 and Server 2008 (and if so, what is your take)? Here are a few articles:
“Windows 7 and Server 2008 Get 0patch Security Fixes After EoS”
https://www.bleepingcomputer.com/news/security/windows-7-and-server-2008-get-0patch-security-fixes-after-eos/
“0Patch to support Windows 7 and Server 2008 R2 with security patches after official support end”
https://www.ghacks.net/2019/09/21/0patch-to-support-windows-7-and-server-2008-r2-with-security-patches-after-official-support-end/
“0patch Promises Support for Windows 7 Beyond January 2020”
https://www.securityweek.com/0patch-promises-support-windows-7-beyond-january-2020
And a company post from September:
“Micropatching Keeps Windows 7 and Windows Server 2008 Secure After Their End-Of-Support”
https://blog.0patch.com/2019/09/keeping-windows-7-and-windows-server.html
Looking at the links and comments on those links, their setup and service seems a little odd. Like once they figure out a patch, they use a loader to re-rewrite the module in memory leaving original file intact. And it also significantly slows down the computer as reported by a user of the service.
And how in the world will they have the resources to do the patches the way they talk about? Like testing a POC for the exploit, figuring out the code and testing, etc.
Re the malicious software removal tool error. I simply downloaded it manually from the Microsoft Update Catalog and ran it manually.
I download all the Updates and Rollups manually anyway to save for future problems where I have to rollback my system using a saved image and then reinstall updates. Often it is faster to install them manually than to run MSUpdate which can bog down when the servers are busy I guess?
I really do not want to ‘upgrade’ to Win 10, after the Oct 2018 update mess, I rolled my PCs back to Win 7. I may have to dedicate a PC to dual boot 7&10 just for a time when programs like TurboTax will no longer provide Win 7 versions.
Last time I checked, about 26% of PC still are running Win 7 (Oct 2019), and that’s twice the number of computers running Apple OS (Macs, Macbooks, etc., not including phones). There’s a reason many are sticking with Win 7.
If MS gives out Win 10 for free, there is a reason, and it isn’t because they’re a charity. I assume they are monetizing all the usage info they collect from Win 10 users – just imagine how that information could be used for nefarious purposes, eh?
Alas…to err is human, to really screw up, you need a computer.
These fixes still do not address the date/time problems I have experienced when booting into Linux on my dual boot system. For some odd reason, even though Linux Mint stays current, when I boot into Windows 10 the time changes to 6 hours later.
It’s a strange bug that should not be a problem as both operating systems are separate.
Makeawish that is not a M$ update problem that is because Linux and Windows use different times.M$ uses local time and Linux doesn’t. Try this site.
https://www.howtogeek.com/323390/how-to-fix-windows-and-linux-showing-different-times-when-dual-booting/
Recent WU for Windows Malicious Software Removal Tool x64 – November 2019 (KB890830) was frustrating to say the least. For the first time, it was the only thing that didn’t update successfully. As such, spent a lot of time trying to find a solution for error code:0x800B0109 (which had little to no information). Cleaning files, virus and malware scans, etc. Ended up trying to back up my SystemDistribution and Catroot2 which was mostly offered as a solution but still to no avail. Then all of a sudden, Servicing Stack Update KB4523206 appears and updated normally.
No trace of the previous KB890830 WMSRT even after several update checks. At the moment, I have my rig completely (and successfully) updated. Jeez louise papa cheese… smh
same problem with KB890830 (and who names this sh-t by the way) and every online forum seem to think you have malware, never had before but have had (month here) roll outs and tools repeatedly fail then the next one updates fine.
Can’t count the number of ‘hanging update’ screens i get these days stuck on either preparing to configure your computer… or starting windows 45 minutes later i can go back to what i was doing when you suddenly restarted it in the middle of the youtube news vid i was watching!, hard shutdown same screen or some sh-t about failure to start no just taking a year yo do it!!!
and i don’t have $50 diagnostic fee for my local PC center they get to keep even if it took them 5 minutes to fix it
as i tell them i own a PC not have a degree in IT, i don’t develop software
Same problem. Same result. Servicing Stack Update KB4523206 appears and updated normally. No further problems so far, (fingers crossed).
The Adobe Flash Player has been updated to version 32.0.0.293; as of this writing, their Security Bulletins and Advisories site has not been updated, so it not yet known whether this is security related.
For now, November release of KB890830 is no more offered on Win7 machines. Seems that the update was recently withdrawn from detection.
As stated in KB4472027, starting August 2019, updates for Windows 7 are signed with SHA-2 only, which is true for MSU packages and there were no such problems observed. KB890830 is distributed as an EXE (PE image) and first release signed with SHA-2 only was the yesterday’s one. Although both formats (CAB-MSU and PE-EXE) support embedded Authenticode signatures, each format needs its own parsing code. It seems that changes introduced in KB4474419 and KB4490628 are not sufficient for successful validation of PE images signed with SHA-2 only. Hope that Servicing stack update fixing this issue will be released soon.
So far have 2 instances where critical update that ran Nov 13 at 3am removed all cached passwords; email, network connections etc. I am running a restore to the time just before this update to fix …
My Windows 7 PC installed the important updates on 11/13/2019 (today) but one failed. It is the Windows Malicious Software Removal Tool x64 November 2019 (KB 890830). Earlier versions of this in August and October installed with out any problem. I’ve restarted my PC and tried to do the install again, but it failed again. Any thoughts on this? Anyone else seeing this? Should I just wait a few days and check again? Or pursue a solution more aggressively?
I have obviously led a charmed life over the recent years of Windows 7 and Windows 10 updates. Apart from an AMD processor equipped Windows 7 PC being bricked in early 2018 (or was it early 2017? I had a week-old system backup to save me.), all the tribulations seem to have passed me by. I am now using Windows 10 Pro Feature Update 1909 for all my security critical tasks. That OS seems only to get better and better.
After working on the problem off and on for weeks (see my previous comment of Nov. 12), only today was I able to restore my system to working order, sans KB4519976 (the October “security” update). Somehow, my trial/error/trial/ad nauseam process that eventually succeeded also managed to uninstall my Kaspersky security suite. Luckily, I was able to re-install it to working order.
At this writing, I am on a break. I still have to get my Firefox browser back into working order, possibly reinstalling that, too. Shouldn’t be too hard.
This day–one day after the November 2019 Patch Tuesday–I have sworn off any further patching from MS for my Windows 7 Pro laptop. Because I use it for a government job, I am now faced with these choices: 1) buy a new Windows 10 laptop (not possible in my budget), 2) buy an additional year of W-7 “protection” for my small-government usage if available (won’t know till 12-01), 3) Attempt to install W-10 on my 6-yr.-old machine (high-risk, no matter what MS says) or 4) Continue indefinitely unpatched, depending on “safe-computing” and job-limited usage to maintain some measure of security.
Did anyone see a good option in that list? I didn’t think so, either.
Marcus,
I think the best approach for you is to upgrade your PC to Windows 10. As Brian points out at the bottom on this & every Patch Tuesday article: Back up your computer before making any big changes to your system.
I recommend you use an imaging backup program and an external hard drive. Macrium Reflect is free for personal or commercial use, this is my choice software for Windows machines.
Before upgrading to Windows 10 make an imaged copy of your computer to an external drive. If you use Macrium you should also create a recovery DVD or bootable USB drive to be used later in case your computer has issues booting in the future. You can boot the Macrium recovery image to either repair the Windows bootloader, run CMD, use File Explorer or restore the computer from a previously made imaged backup.
After you have your backup made, you can then go to https://www.microsoft.com/en-us/software-download/windows10 and create your Windows 10 installation media.
Play it safe & backup first before installing Windows updates or upgrading to Windows 10. It is not safe to abstain from updating your Windows system. You just have to do it. Sorry.
Good advice and practices, Nijel: just about all of which I observe and follow. It kind of goes back to that budget thing. If my only way to get a new laptop is to reach into my own pocket, it ain’t gonna happen. (Remember, I work for a local gub’mint.)
As for installing W-10 on a 6 yr. old machine, Seymour: that’s not likely to happen. Hardware has life expectancies and other limitations. I just don’t see the good sense in installing a V-6 in the rear of a VW bug.
If my Dell Latitude D420 Core Duo (a 32-bit ULV CPU) can run Windows 10, I think your system will be perfectly fine. I did upgrade it’s dinky 80GB 1.8″ PATA HD with a 128GB SSD, but aside from that it the same old 2.5GB laptop it was when it was made in 2006.
In the UK this has not been fixed, it has just been removed and not offered as an update.
Windows Malicious Software Removal Tool x64 – November 2019 (KB890830)
Installation date: 13/11/2019 18:44
Installation status: Failed
Error details: Code 800B0109
Update type: Important
The links to the manual download produced a 404 error and installing the
https://support.microsoft.com/be-by/help/4523206/servicing-stack-update-for-windows-7-sp1-and-server-2008-r2-sp1
did not do anything at all.
Downloaded from here
https://download.microsoft.com/download/2/C/5/2C563B99-54D9-4D85-A82B-45D3CD2F53CE/Windows-KB890830-x64-V5.77.exe
the November 2019 Malicious software tool and ran it, no problems.
As stated above the November KB890830 has been removed from being offered and checking on Windows update all is now updated.
More information:
http://support.microsoft.com/kb/890830
Typical Windows service, don’t they test these things before they let them out in the wild!!!!
🙂
Windows automatically updated last night. This morning, I have internet, but Chrome and other programs can’t access. Trying to roll back.
FYI…Office update, specifically affects Microsoft Access, pushed out wreaking havoc for one of my customers. The kicker – apparently MS knows, has a fix but isn’t going to push out until 2nd Tue of Dec!
https://support.office.com/en-us/article/access-error-query-is-corrupt-fad205a5-9fd4-49f1-be83-f21636caedec
we have 3 computers running here – 2 for business and a personal laptop – all run windows 10 – just this week (11/13/2019) the laptop and one of the business can’t view pdf files in chrome – viewing these is critical for the business – had to start using MS edge on that one – tried the settings route in chrome – uninstalled and reinstalled both chrome and adobe reader – extension is enabled – if we open incognito window..files open normally – anybody else have this issue
KB4524570 was a disaster on my desktop. USB would randomly go unresponsive, and I was experiencing multiple BSOD’s per day.
Finally gave up and rolled it back. I have things to do.
This was on Windows 10 Pro.
Brian,
“Microsoft says all versions of Office still support an older type of macros that do not respect this setting, and can be used as a vector for pushing malware…”
So it’s established that the macro itself controls security, not Excel…
Seriously, even for Microsoft that’s depressing… 🙁
Brian,
I have two computers that cannot be upgraded to Windows 10 from Windows 7.
I know Microsoft will be providing large corporations, and certain small businesses, with automatic update of Windows 7 for a fee (securitynow podcast).
Is there any way those of us in this situation can manually update the updates MS will have to have in the MS Update Catalog for those businesses anyway, or do you think MS will detect a non-paid fee.
If it can be done, can you provide a list of KBs for updates after January 14, 2020?