Sources tell KrebsOnSecurity that Microsoft Corp. is slated to release a software update on Tuesday to fix an extraordinarily serious security vulnerability in a core cryptographic component present in all versions of Windows. Those sources say Microsoft has quietly shipped a patch for the bug to branches of the U.S. military and to other high-value customers/targets that manage key Internet infrastructure, and that those organizations have been asked to sign agreements preventing them from disclosing details of the flaw prior to Jan. 14, the first Patch Tuesday of 2020.
According to sources, the vulnerability in question resides in a Windows component known as crypt32.dll, a Windows module that Microsoft says handles “certificate and cryptographic messaging functions in the CryptoAPI.” The Microsoft CryptoAPI provides services that enable developers to secure Windows-based applications using cryptography, and includes functionality for encrypting and decrypting data using digital certificates.
A critical vulnerability in this Windows component could have wide-ranging security implications for a number of important Windows functions, including authentication on Windows desktops and servers, the protection of sensitive data handled by Microsoft’s Internet Explorer/Edge browsers, as well as a number of third-party applications and tools.
Equally concerning, a flaw in crypt32.dll might also be abused to spoof the digital signature tied to a specific piece of software. Such a weakness could be exploited by attackers to make malware appear to be a benign program that was produced and signed by a legitimate software company.
This component was introduced into Windows more than 20 years ago — back in Windows NT 4.0. Consequently, all versions of Windows are likely affected (including Windows XP, which is no longer being supported with patches from Microsoft).
Microsoft has not yet responded to requests for comment. However, KrebsOnSecurity has heard rumblings from several sources over the past 48 hours that this Patch Tuesday (tomorrow) will include a doozy of an update that will need to be addressed immediately by all organizations running Windows.
Update 7:49 p.m. ET: Microsoft responded, saying that it does not discuss the details of reported vulnerabilities before an update is available. The company also said it does “not release production-ready updates ahead of regular Update Tuesday schedule. “Through our Security Update Validation Program (SUVP), we release advance versions of our updates for the purpose of validation and interoperability testing in lab environments,” Microsoft said in a written statement. “Participants in this program are contractually disallowed from applying the fix to any system outside of this purpose and may not apply it to production infrastructure.”
Original story:
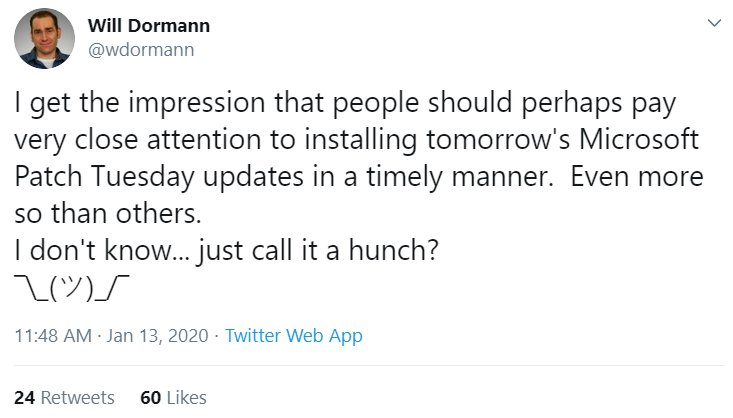
Will Dormann, a security researcher who authors many of the vulnerability reports for the CERT Coordination Center (CERT-CC), tweeted today that “people should perhaps pay very close attention to installing tomorrow’s Microsoft Patch Tuesday updates in a timely manner. Even more so than others. I don’t know…just call it a hunch?” Dormann declined to elaborate on that teaser.
It could be that the timing and topic here (cryptography) is nothing more than a coincidence, but KrebsOnSecurity today received a heads up from the U.S. National Security Agency (NSA) stating that NSA’s Director of Cybersecurity Anne Neuberger is slated to host a call on Jan. 14 with the news media that “will provide advanced notification of a current NSA cybersecurity issue.”
The NSA’s public affairs folks did not respond to requests for more information on the nature or purpose of the discussion. The invitation from the agency said only that the call “reflects NSA’s efforts to enhance dialogue with industry partners regarding its work in the cybersecurity domain.”
Stay tuned for tomorrow’s coverage of Patch Tuesday and possibly more information on this particular vulnerability.
Update, Jan. 14, 9:20 a.m. ET: The NSA’s Neuberger said in a media call this morning that the agency did indeed report this vulnerability to Microsoft, and that this was the first time Microsoft will have credited NSA for reporting a security flaw. Neuberger said NSA researchers discovered the bug in their own research, and that Microsoft’s advisory later today will state that Microsoft has seen no active exploitation of it yet.
According to the NSA, the problem exists in Windows 10 and Windows Server 2016. Asked why the NSA was focusing on this particular vulnerability, Neuberger said the concern was that it “makes trust vulnerable.” The agency declined to say when it discovered the flaw, and that it would wait until Microsoft releases a patch for it later today before discussing further details of the vulnerability.
Update, 1:47 p.m. ET: Microsoft has released updates for this flaw (CVE-2020-0601). Their advisory is here. The NSA’s writeup (PDF) includes quite a bit more detail, as does the advisory from CERT.




Maybe more people should using Linux instead of dealing with Windows 10 A lot of users are getting fed up with all the patching and twice a year featured updates
Linux isn’t always the answer to a Windows problem. To say that everyone should just use Linux for X, is not a responsible advocate for any piece of software.
I’m kinda glad I have MacBook. Ever since I started using using it, I haven’t had a single, not one, security headache.
Not a single security flaw. Except maybe things like… https://www.zdnet.com/article/stupid-stupid-macos-security-flaw/
Remember that time when you could login as root by pressing the “login”-button often enough on macos? That was late 2017. So idk when you got your mac, but nah.
Writing this from an mbp, I just can’t respect this ‘my vendor is safe’-crap. Every large company suffers from these issues, because that’s what increasing complexity does to your products unless you have a rigorous, *uncompromised* engineering-culture, up to every member of the controlling board. Which is a delusional expectation with respect to management culture in public companies.
Yeah, apple is doing a good job, but claiming that they have zero security concerns is much, much wronger than what anyone should nod off.
+100
In this age of fake news and rumors gathering momentum that may appear to give validation to nothing more than a fact-less comment, it’s best to take such comments as BS – or even better run a quick Google/Safari search on “MacOS security flaws” to become informed users, rather than scared ‘sheeple’.
If MacOS/Linux had nearly close to the global user base, of course you would see as many flaws causing serious problems, but the reality is that Macs are essentially a ‘niche’ product if you base the sheer volume of global Windows installations, which simply dwarfs apple based machines.
And there’s only so many hackers so where would you spend your time?
Of course on the larger target!
I’ve used Mac, Linux, and Windows for years and have only had one issue where malware impacted me. It was on windows but one of my daughters uses a macbook and I’m constantly having to clean it up. While I will not argue that windows is the easiest of the 3 to exploit it’s not so much the OS as it is the user and their activities.
It isn’t the malware/hacks you know about that should concern you
Hahahaha oh you ignorant people… macOS has had tons of security vulnerabilities recently. I even have and love my macbook, but to say you are safe is so wrong.
I suspect Mac Users are not aware of it so much because Apple just manages updates in such a way it’s mostly transparent – they just push out a mix of silent updates and major updates that are pretty easy to deploy.
Whereas MS has a complex update infrastructure and numerous layers of stuff going on.
Same as I’ve had countless people tell me they think Google Chrome is more secure than Internet Explorer or Edge etc as they never have to update Chrome. Of course Chrome constantly updates silently in the background…
Perception buys Apple a lot of fans.
What you mean to say is, you haven’t read about them because people make less of a big deal about them since less people, and businesses especially, use Macs. But they definitely do exist and anyone “saying I have a Mac or I have Linux, thus I don’t have these issues” is kidding themselves. People always go where the greatest reach is. Windows is installed more than any other OS, so exploiting it has the greatest impact. That really the *only* motivation. Let’s not kid ourselves into thinking MacOS or Linux are the most secure OSes in the world. Just wait until Windows starts using a Linux kernel. Fun will ensue.
You’re right. Qubes OS is the most secure OS in the world.
https://www.appleworld.today/blog/2019/3/1/netmarketshare-macos-ios-market-share-down-down-in-february
With a 9% market share, obscurity is not security
The obvious caveat: “That you know of.”
MacOS is not invulnerable to targeted attacks, and Linux certainly isn’t. It’s no longer true that Unix and its variants are somehow inherently “more secure” and “more stable” than Windows. You can argue they may be more *usable* for whatever personal or technical reason, but it literally only takes one breach to prove any system is not secure. MacOS would not fare any better, probably even worse, if it got the same attention for attacks Linux (on servers) and Windows (as clients and back office servers) do. Suffice it to say, MacOS is just as vulnerable to traditional attack vectors as any other operating system written with traditional legacy computing languages and techniques. That doesn’t even get into the can of worms that it’s usually the *user* at fault in most data breaches, and not the software, when they’ve been tricked into installing malicious programs.
well, let me think – crypto & linux – ah well openssl right…
so this has nothing to do with windows rather then that crypto is hard also for the foreseeable future that means: whenever a central crypto-lib gets unpleasant news a lot of people will have a lot of extra work
so stop this os-war non-sense please, thanks
Hear hear! My OS is soooo much better than your OS…blah blah blah. I’ll keep my OS, thanks…
This perfectly expresses the eternal answer to the OS wars…
https://youtu.be/d85p7JZXNy8
Maybe, you’re in idiot.
snap!
You’re an* idiot.
Ain’t we all idiots?
I thought it was 1d10t around here.
No, YOU’RE a towel.
Having worked in the industry for over 20 years, my experience has shown that windows systems are patched much more frequently whereas I’ve worked lots of places that are running jboss from 10 years ago or a kernel from 2 years ago. Generally the windows teams at places I’ve worked have patched regularly and consistently, in contrast to the linux teams.
This is not true. Linux is patched constantly. You don’t wait for monthly patches.
Like the 10 year long open openssl bug?
He’s not talking about when the patches come out, he’s talking about actually patching the damn thing. No good releasing 5 patches a month when the patches aren’t being applied.
right – I just mean – this is just one step in the game writing patches – and yes there might be topics where patches are faster available but this holds true only for a number of projects / components too
And let us not forget about the patches that never get written, because few actually bother auditing the source code, they just use it. If a full scale audit were done on most major open source products I think people would be in horror at what was unearthed. You know who is auditing those major open source projects? Sophisticated hackers looking for their next zero-day to hit their high profile targets with! 😀
take your iot device of choice and say that again ;)…
I’m not so sure if that’s a reliable metric, to simply go by how recently an effort goes into developing patches for any of the hundreds of Linux variants that are out there
Isn’t it more likely that the lack of highly vulnerable backdoors being found inside Linux’s has something to do with how ‘unconcerned’ the Linux community usually is about joining the patch-culture?
I would expect that the only real effort going towards hacking Linux & developing malware for that, is being done by state level organizations who do not wish to let their bag of tricks get loose out on the net
As for myself, I’m planning on migrating from Win7 to Ubuntu. I just need to decide on what motherboard I would like to get and in typical fashion, being very slack about it all…
Your post is so retarded it makes my heart bleed
I get that reference… nothing like a vulnerability that simply ships big hunks of memory back to the requester. https://xkcd.com/1354/ And yeah, all the talk of Linux has no bugs and Mac has no bugs… nonsense. They all have bugs.
Love the mouseover text on that one …
You are using Windows 7 – hmmm…
The Linux community has maintainers for programs and libraries. As these programs are patched, the individual distributions then update their repositories. You have the option of using repositories that are more current than the distribution. For example someone doing multimedia would have packman in their selected repository. Programs like VLC are extremely finicky regarding libraries.
Kernel updates are another story. I don’t really know much about how the sausage is made.
I have used Debian based distributions on R Pi and similar embedded systems. Not my choice, but on arm it seems to be the distribution of choice. I use Centos on servers. On notebooks and PCs I use Opensuse.
I have switched back to AMD/Radeon from Intel/Radeon. The AMD processors have much less problems concerning speculative execution hacks. AMD provides two paths for graphics. One is to use the open-source drivers. The other is to use the proprietary blob. With Nvidia, you just get the blob.
When you build a system is the perfect time to evaluate a number of distributions. I do this every time I have what is basically a clean slate of a system. I always have ended up with opensuse running KDE. I access my centos servers 100% via ssh so graphics is of no concern.
If you are going to use ECC ram, you probably want to go with Supermicro boards. If you go with a software RAiD, you should have ECC. I highly suggest avoiding RAiD boards or even FRAID. If RAiD board or mobo fail, it is sometimes hard to rebuild the array. Software RAiD may be slower, but it is more universal. I use RAID5.
Hmm Windows 7 🙁
then you need to read this.
https://thehackernews.com/2020/01/windows-7-support-ends.html
Actually, as in all commerce, it’s who has the money. Is banking, sales, or retail on Linux? It’s mostly on win. So where are the attacks? On Mac? Linux? No. Most businesses run on ….! Therefore, you have wrong arguments. Now, win has too many variants that mean most programers don’t know the latest up to yesterday recent updates and punch holes in all needed secure updated programs.
Banking? Most banking software I know runs UNIX.
You will see windows desktops, and a pretty web developed user interface, but the core applications run on UNIX/AS400.
Maybe most is Unix… but a bit over a year ago I walked up to use an ATM that said in its lower-right corner “Windows 7 / Build 7601 / This copy of Windows is not genuine”. Sent a photo of that to the bank’s CIO.
The machines inside the ATMs could very well be windows, but they connect back to a Unix/Linux “core”.
I’d say Windows is the predominant _desktop_, no question, and Windows has a place in the server-side but has long been playing catch-up to *nix (and before that, mainframes). Remember, the Internet was built on Oracle + Sun. So definitely, patching Linux matters, and folks with a vested interest, i.e. any of the big shops out there running Linux servers take it very seriously and you will be patching Linux just like Windows. No one escapes.
JBOSS has critical vulnerabilities released about every two weeks.
Fed up if it was 2005 maybe. This is 2020, patching is a fact of life for anyone, regardless of OS. The Linux kernel had 170 published CVEs for it last year, so inferring that Linux would have no ongoing maintenance / security considerations is factually incorrect.
Linux patches are, for the most part, safe. Also quite small. Replace a little bit of code and done.
Unless it’s a kernel patch, no need to reboot and wait and wait. Plus update at your own timing and not be forced to update at any random time a Windows 10 machine wants.
With Windows 10, patch at your own risk, because Microsoft don’t care. Microsoft fired most of the quality control staff, and passed that task onto end users. Such a failure it is.
I get a new kernel update at least one a month on Mint, not to mention the desktop environment updates on top.
Ah yes, the classic security through obscurity. I suppose you think Apple OS devices don’t get hacked too.
There is no “Apple OS”. There is “Darwin” (a *nix OS closely related to BSD) and ios (also unix-like and closely related to BSD).
And both, like all other systems, have vulnerabilities.
That’s just silly. I have two MRP databases that run on Redhat and Centos. I can’t even keep up with patches because Redhat releases so many of them and they have to be validated by QA, so I am way behind. I have about 20 Windows Server 2016 server’s, I am never more than 2 weeks behind on patches. Same with my windows 10 laptops (140 of them), between testing and patching the team has them patched in 2 weeks
You can whinge about Linux all day long, but Heartbleed wasn’t a Windows flaw and neither was Spectre.
What a joke, a comment from a person who does not live in reality…
Face the facts, windows is far from the most used os and will for sure continue to be, for a reason… Linux is not in a position to replace windows in any way.
And btw. It’s more or less as diverse and as confusing as the explosion of programming languages during the past 10yrs, just a fxxxing mess where developers try to follow some kind of “hype” curve when choosing what to use…
Linux? Really, please go find Linux software for HR, payroll, finance, accounting, reception stations, and building security. Then train the users.
Most good HR, payroll, finance, accounting programs are web based these days. But there will always be windows only apps, especially things like office security stuff.
There are ways around using windows, you absolutely don’t have to. There are additional costs to going non-windows, but there are also costs for staying on windows. Everyone’s calculation will be different.
Heartbleed? *koff koff*
I’m glad Florida man has schooled us in the ways of using Linux so we don’t have to patch anymore …
This actually made me LOL… You haven’t used Linux much in the true Enterprise space have you. It is a mess to manage securely at scale (thousands, tens of thousands, hundreds of thousands of machines) without some expensive third party tools and even those can often end up looking like DOS attacks on the primary Identity system used in most on-premises environments in the Fortune 100 space for the last couple of decades.
The best microsoft patch is the Linux install ISO.
Because Linux Desktop is now far less secure than windows 10, as are nacs….and Linux also has monthly updates just like windows, oh and its not usable to everyone…windows barely is.
2020 is the year of Linux on the Desktop! lolz
I love how Linux fanboys jump on the chance to haze Windows every time the simplest issue comes up. I would say its getting old but its been old for 15 years. The best part is, its usually a Linux Newbie as the older salty Linux guys don’t bother with it anymore. Let it go already.
If you think once or twice monthly updates are bad then you haven’t tried Linux. Ubuntu get a few updates a week.
This may be the day we have all been waiting for: those who (smartly) delay receiving updates may need to manually install this update right away.
Don’t expect IT to answer their phones… Their hands will be full with the company servers.
What are the chances Microsoft’s update servers will crash tomorrow? Their response? Probably: “May you live in interesting times.”
Because Linux doesn’t get updates either right?
I’ve been running Mint Mate on my secondary machines, and I’m really getting fed up with how often I have to babysit the darned update process! That OS doesn’t seem to have any easy method to automate the updates, and there’s been lots of them, all the time. But not a single one in the last 3 or 4 years has been ‘critical’ or ‘urgent’
However, I do like the backend support that Ubuntu has built up. I’m switching over to that one, when I get motivated enough to spend an hour on it
And just recently noticed Ubuntu Core
I suggest that the author of this note read the following web page about automated security updates from 2013!
https://community.linuxmint.com/tutorial/view/1217
How to enable unattended software updates on Linux Mint
I am sure that there are many other web pages on the subject — try LOOKING for them!
I did set up a Linux Mint for an old lady. And her system does automatic updates. I will explain how it works.
1. start update manager
2. go edit/Preferences/Automation
3. activate automatic updates
This process will run once a day at a given time. So worst case, your system will be 23h and 59 minutes behind.
I’m doing this for all the old Win 7 laptops families have given me! Seems to work quite well
The fact that a ‘source’ leaked this critical proprietary information again speaks to the futility of any entity’s ability to safeguard Anything due to the human factor. If the bad guys aren’t already concluding their skulduggery, this leak gives them time conclude it. I recall a while back Apple discovered some critical flaw in their OS and pushed out a patch simultaneously with the press release. Yay Apple!
Pushing a press release is not bad. Imagine you found a flaw, which is actively abused already. In such a case, you have to warn your customers. And even if your patch is not ready, you have to warn them as well. It might be bad for business though.
Maybe this is related?
https://usn.ubuntu.com/4236-1/
I am going to say that this is not related, a timing attack is normally unique to the implementation.
That and the MS bug seems to be more than a side channel bug.
Libgcrypt is riddled with side-channels. Not at all related to Windows.
That doesn’t sound dangerous enough. A timing attack on a single/new algorithm.
I’d imagine it’s something on the levels of RCE with SYSTEM permission without user participation.
…or maybe someone broke NDA the day before the patch was supposed to be released which prevented that simultaneous disclosure?
Timing of this (see crypt32.dll mention in the link) report is about right, but severity isn’t that high, unless combined with another vulnerability..
https://safebreach.com/Post/NVIDIA-GPU-Display-Drivers-for-Windows-and-GFE-Software-DLL-Preloading-and-Potential-Abuses-CVE-2019-5694-CVE-2019-5695
Combining that code-signing exploit with this shellcode injection could be it:
https://github.com/dotnet/aspnetcore/issues/13706
Given .NET Core updates aren’t generally handled as part of Patch Tuesday, that seems pretty unlikely IMO.
Worth remembering that Oracle is also releasing. And more.
https://www.riskbasedsecurity.com/2020/01/08/2020-the-vulnerability-fujiwhara-effect-oracle-and-microsoft-collide/
It’s going to be a busy day.
Thanks again, Brian, for a timely heads up!
Having watched the software fiascos that have occurred since, what, win386, it seems to be the same issue always. Rushing out product for sale before it is fully vetted, i.e. marketing overrides the dictates of good engineering practices. Good thing airplane manufacturers don’t do this. Oops, oh wait, they do this same thing also don’t they…
Saying Linux is better than Windows is like saying iPhone OS is better than Android OS. To some you are right & to others you are wrong. Its only ever going to be biased opinion.
Unless your a cyclist….then you are always wrong……..
The facts here do not offer any relevant information.
so does the wording of “timely manner” and the ‘tease’ mean the patch should be installed asap or we should hold off??
Seems equally open to either interpretation…
@ch
“timely manner” means quickly.
https://www.vocabulary.com/dictionary/timely
“tease” has nothing to do with whether it should be quick or slow. It just means that people are currently giving partial information, but aren’t giving the full information (thus they are teasing us).
how can we tell if crypt32.dll has been updated?
Do a search on that filename in the Windows folder (allow hidden files to be revealed if need be) — the active top directory should have a version which is dated 14 January 2020.
So BK learns something is so serious it involved a news embargo until 14 January, but felt the urgency to release that on 13 January? And he learns that the patch won’t be available generally until the day after he gushes the story out?
That’s not responsible, man.
“So BK learns something is so serious it involved a news embargo until 14 January, but felt the urgency to release that on 13 January? And he learns that the patch won’t be available generally until the day after he gushes the story out?
That’s not responsible, man.”
Dude… There are no exploit details given, just a warning that this patch is a particularly critical one. That’s entirely responsible, man.
So not a single word of your comments even sound like English to me… Can someone PLEASE give (in layman’s terms preferably…) me an idea of what I’ve neglected to research before jumping on the internet band wagon some 20 years ago?… I’m intelligent enough to know that most things now days that are “security related” and have to do with a force update tend to not always be because Microsoft, Samsung, etc. aren’t really for my “safety and security”… I basically picture a fatter version of my nerdy self behind a computer using a radio dispatching (your cities name here)s FINEST, Pretectimg and serving…. Themselves…
Until three weeks ago I was still using Win XP and was very happy with it, especially after Windows “supported” it not anymore.
Only because some hardware on the mainboard broke down, I had to change to a new PC with Win 10.
Since I started with Win 3 decades ago, the (unsupported) XP was the best.
Sure it was. Until you plugged the Ethernet cable and ran the browser.
Lots of “could” and “might”. I guess we don’t have long to wait to find out more.
I currently support four different major OS platforms (not counting differences between Windows 10, server 2008/2012/2016/2019 etc.)
Windows
Linux
MacOS
ChromeOS
Every-SINGLE-system, person, user, everywhere is going to have security updates. Period. It is a way of life.
It is the duty of that user to know how to apply those updates, and not ignore them.
That said, Microsoft is 80% of the market, they are the biggest target and thus make the news most often. Once-a-month patching is a good balance, but MS has been known to release out-of-band patches when needed.
For my MAC users – updates are so far-between that some of my users ignore them, and could go months without addressing it.
For Linux, sometimes there are multiple updates daily – released when they are ready. It is very fortunate that applying them is far-less intrusive (usually no reboot required) that I don’t get involved unless there’s a broken package dependency, requiring intervention.
For ChromeOS – it’s more like a browser update (with a very small kernel to keep things connected) and an occasional reboot is necessary.
Software evolves. Keep up.
I could not agree more with you there Scott!
Conspiracy theorist believe,,,,, the patch doesn’t Fix Windows crypto, it makes it easy to read for the NSA.
Brought to you by the History Channel.
Though more rare, MS has released very critical updates out-of-band in the past. What’s that say about this one?
It is Trump’s fault. He and his g-damn Russian buddies.
yeah, how dare they abuse time travel by going back to 1990 and creating this bug/exploit. I hope they erase that annoying singer Randal Kufafison from time while they are there.
Thanks to MS. They are able to spot this.
https://www.zdnet.com/article/microsoft-spots-malicious-npm-package-stealing-data-from-unix-systems/
So, this update actually put my laptop into a boot loop. And if I change the boot mode.to Legacy away from UEFI, it tells me there’s no bootable device. This isn’t true, since on UEFO mode Windows attempts and fails to roll back changes because BOOM autoreboot. I can’t start in safe mode.
I’m going to have to remove the SSD and plug it into one of my ArchLinux boxes which will mount everything and anything and its grandmother, grab my data, and reinstall Windows on this laptop. YAY. >_>
What are you talking about? The updates aren’t out yet.
Your pc, no matter which brand of os you use, is only as safe as the user (you). Stop downloading all the useless crap. Stay safe.
This same argument has been going on for 20 + years. This is hilarious. 🙂
Thank you and looking forward to the next updates 😉
OMG, really grow the hell up and act like professionals. Patch and move on.
As usual!!!
A web story detailing the hidden horrors of a particular patch!
A Blog with 85 + comments detailing the pros/cons of Windows vs. Linux….
…Would anyone care to state the KB article and CVE for this particular patch?
CVE-2020-0601
MS: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0601
NSA: https://media.defense.gov/2020/Jan/14/2002234275/-1/-1/0/CSA-WINDOWS-10-CRYPT-LIB-20190114.PDF
US CERT: https://kb.cert.org/vuls/id/849224/
Brian… since we’re talking about the NSA here, that date stamp on the NSA file is probably not a typo.
That means that the NSA has been sitting on (and probably exploiting) this bug since 20190114 … i.e. january 2019
They could have just forgotten to update the year. It happens to be exactly one year ago today..
Or, are we being manipulated into installing a “fix” that is actually a new back door for the NSA?