In January 2019, dozens of media outlets raised the alarm about a new “megabreach” involving the release of some 773 million stolen usernames and passwords that was breathlessly labeled “the largest collection of stolen data in history.” A subsequent review by KrebsOnSecurity quickly determined the data was years old and merely a compilation of credentials pilfered from mostly public data breaches. Earlier today, authorities in Ukraine said they’d apprehended a suspect in the case.
The Security Service of Ukraine (SBU) on Tuesday announced the detention of a hacker known as Sanix (a.k.a. “Sanixer“) from the Ivano-Frankivsk region of the country. The SBU said they found on Sanix’s computer records showing he sold databases with “logins and passwords to e-mail boxes, PIN codes for bank cards, e-wallets of cryptocurrencies, PayPal accounts, and information about computers hacked for further use in botnets and for organizing distributed denial-of-service (DDoS) attacks.”

Items SBU authorities seized after raiding Sanix’s residence. Image: SBU.
Sanix became famous last year for posting to hacker forums that he was selling the 87GB password dump, labeled “Collection #1.” Shortly after his sale was first detailed by Troy Hunt, who operates the HaveIBeenPwned breach notification service, KrebsOnSecurity contacted Sanix to find out what all the fuss was about. From that story:
“Sanixer said Collection#1 consists of data pulled from a huge number of hacked sites, and was not exactly his ‘freshest’ offering. Rather, he sort of steered me away from that archive, suggesting that — unlike most of his other wares — Collection #1 was at least 2-3 years old. His other password packages, which he said are not all pictured in the above screen shot and total more than 4 terabytes in size, are less than a year old, Sanixer explained.”
Alex Holden, chief technology officer and founder of Milwaukee-based Hold Security, said Sanixer’s claim to infamy was simply for disclosing the Collection #1 data, which was just one of many credential dumps amalgamated by other cyber criminals.
“Today, it is even a more common occurrence to see mixing new and old breached credentials,” Holden said. “In fact, large aggregations of stolen credentials have been around since 2013-2014. Even the original attempt to sell the Yahoo breach data was a large mix of several previous unrelated breaches. Collection #1 was one of many credentials collections output by various cyber criminals gangs.”
Sanix was far from a criminal mastermind, and left a long trail of clues that made it almost child’s play to trace his hacker aliases to the real-life identity of a young man in Burshtyn, a city located in Ivano-Frankivsk Oblast in western Ukraine.
Still, perhaps Ukraine’s SBU detained Sanix for other reasons in addition to his peddling of Collection 1. According to cyber intelligence firm Intel 471, Sanix has stayed fairly busy selling credentials that would allow customers to remotely access hacked resources at several large organizations. For example, as recently as earlier this month, Intel 471 spotted Sanix selling access to nearly four dozen universities worldwide, and to a compromised VPN account for the government of San Bernardino, Calif.
KrebsOnSecurity is covering Sanix’s detention mainly to close the loop on an incident that received an incredible amount of international attention. But it’s also another excuse to remind readers about the importance of good password hygiene. A core reason so many accounts get compromised is that far too many people have the nasty habit(s) of choosing poor passwords, re-using passwords and email addresses across multiple sites, and not taking advantage of multi-factor authentication options when available.
By far the most important passwords are those protecting our email inbox(es). That’s because in nearly all cases, the person who is in control of that email address can reset the password of any services or accounts tied to that email address – merely by requesting a password reset link via email. For more on this dynamic, please see The Value of a Hacked Email Account.
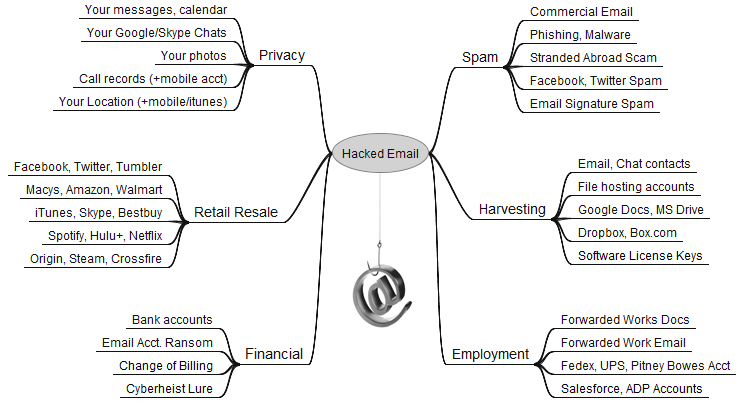
Your email account may be worth far more than you imagine.
And instead of thinking about passwords, consider using unique, lengthy passphrases — collections of words in an order you can remember — when a site allows it. In general, a long, unique passphrase takes far more effort to crack than a short, complex one. Unfortunately, many sites do not let users choose passwords or passphrases that exceed a small number of characters, or they will otherwise allow long passphrases but ignore anything entered after the character limit is reached.
If you are the type of person who likes to re-use passwords, then you definitely need to be using a password manager, which helps you pick and remember strong and unique passwords/passphrases and essentially lets you use the same strong master password/passphrase across all Web sites.
Finally, if you haven’t done so lately, mosey on over to 2fa,directory and see if you are taking full advantage of the strongest available multi-factor authentication option at sites you trust with your data. The beauty of multi-factor is that even if thieves manage to guess or steal your password just because they hacked some Web site, that password will be useless to them unless they can also compromise that second factor — be it your mobile device, phone number, or security key. Not saying these additional security methods aren’t also vulnerable to compromise (they absolutely are), but they’re definitely better than just using a password.




The only crime is that blanket pattern
If a password database is stolen does it really matter how complex your password is? The only option is to change the password frequently.
I have been thinking to regularly cease using an email address, creating a new one, forward the old one to the new one for a while and then deleting it.
2FA is problematic and unreliable for international travelers.
@Sam ; Yeah, I think it matters how complex your password is as the way I understand it as long as the stolen database passwords are not in plain text (i.e. so they are in hashed form) and your using a really secure password (like random/long passwords generated by a password manager) it’s unlikely they will be able to recover your password from that stolen database file, at least not in the near future as it’s not like it will be cracked easily and I suspect they will probably give up because the amount of time/resources to figure out the password will likely exceed the amount of time/resoruces they are willing to put into it. so while they might end up cracking some peoples passwords, who use weak passwords, since your using a long random password, I would say it’s unlikely they can crack your without quite a bit of time/resources put into it.
but in general changing ones password often is a waste of time as the only time that should generally be done is if you think a website was compromised or know it was compromised and your changing the password as a precaution.
I think your constant email changing is basically a waste of time. just make sure you got a really secure password on your email. if your using Gmail and want even more security, use a YubiKey.
don’t let paranoia make you overthink security because from what I have heard the shady people are usually after the ‘low hanging fruit’ as they say and if your using a password manager your already way more secure than the common person who uses the same crappy passwords over multiple websites. plus, assuming ones computer is secure and that person is worried about being Phished out of their password… as a general rule never give away login info (username/password) from a email link etc and ALWAYS go to the actual site by manually entering the site into your browser before entering the log in information. this should keep your chances of being Phished at a bare minimum.
ThaCrip: Whenever I see an article on stolen pw databases it will usually include a blurred out image listing of user names & passwords in plain text giving the impression that the info is plainly accessible by whoever stole it.
I have a feeling a lot of people look at it that way also.
Here’s an example of what I mean:
https://www.bleepingcomputer.com/news/security/home-chef-announces-data-breach-after-hacker-sells-8m-user-records/
Look at it again Sam
The field names are visible, and it clearly says, “encrypted_password”.
The article you linked even says it…
“This information includes a user’s email, encrypted password…”
Another clue is they all seem to be very long, and the same length.
These are NOT plaintext passwords.
Read it again Sam.
The field names are shown and it says explicitly, “encrypted_password”.
Another clue is that the redacted strings are very long, and the same length. You can even still see some encrypted text that wasn’t quite redacted.
Definitely not plaintext.
The article you linked even explains it. “This information includes a user’s email, encrypted password, last four…”
Just because its redacted, doesn’t mean it’s plaintext. It’s a good idea for security folks to redact hashes so nobody even tries or gets lucky with a weak password.
If encrypted passwords are dumped, and the database uses reversible encryption… then the hackers may have also obtained the decryption key. Cracking/exfiltrating the encryption key for one password, could compromise the whole database of passwords.
99% of the time the passwords are hashed (which cannot be “reversed”, only brute forced), but sometimes wrongly called “encrypted” by the database.
So not sure if the Chef database was using both hashing and encryption (best), just encryption (bad), or just hashing mislabeled as encryption (fine).
I have seen both used together. Passwords are hashed, salted with a unique value (to prevent using common lookup tables), and then encrypted with another key located on a separate system.
This way, it’ll take a full breach (the database with salts and the encryption key), and even then, will take a long time to crack the hashes depending on the strength of each password.
In case you don’t know why passwords are typically hashed instead of being plaintext…
There is no reason why a server should know a user’s plaintext password. They only need to know that the user knows the same exact same string of characters. So there is no reason to store plaintext passwords. Just hash the password in the user’s browser (client), send that hash to the server (TLS encrypted), and the server stores/checks only the hash. Only hashes get compared, because it is a mathematical improbability that two different strings (of real keyboard characters) could result in the same hash.
Yes, it matters.
99% of password database dumps are HASHED passwords, not plaintext. Even MD5 would offer some protection, as it forces the attacker to spend time cracking it.
If you don’t use a random password generator, and use words, phrases, and numbers… so the password is “memorable”, then cracking a weak hash like MD5 will be trivially easy. But if you generate completely random strings, use the maximum allowable characters… even a weak hashing algorithm will protect your password for a while.
If 2FA is unreliable for you, because you travel… you’re doing it wrong.
SMS (text message) codes have not been considered good 2FA for several years. Use an app like Google Authenticator, Authy, etc…. to store rotating codes for 2FA. If the service you using only has SMS, then you should look for another company.
Yes, password complexity still matters in such case. Passwords in DB are rarely stored in plain text, instead they are secured with cryptographic function (hash). Given the value of a hash function one can only recover the original password via brute force or dictionary attacks. Your passphrase needs to be at least 20 chars long (to resist brute force) and complex (to make sure it is not in any kind of dictionary). Note that I wrote passPHRASE not password, you will need several words to satisfy length and complexity requirements.
You should look into a YUBIKEY if you are an international traveler. So you can still believe in 2FA!
“And instead of thinking about passwords, consider using unique, lengthy passphrases — collections of words in an order you can remember — when a site allows it.”
I suggest Diceware since it’s truly random with at least a six word passphrase. just search ‘diceware eff’ to find the wordlist (i.e. eff_large_wordlist.txt ) and one can combine that with a bit of padding which should make for a extra secure password. it would also be a good idea to use at least one capital letter, a number and symbol to further boost your passphrase security. like for example…
woRd.word.word_222_word.word@word (so in this example you got six words combined with some padding and there is at least one upper case/number/symbol in there. because I figure just guessing the six word passphrase is slim but with the padding someone is unlikely to guess the padding you used along with the six words you randomly selected with Diceware. I would avoid using the spacebar in your passwords as a general rule which is why I gave my example like I did above)
but seriously, everyone should be using a password manager since it gives a person a unique password for each website they use. so if one is compromised, you don’t have to worry about someone using those credentials to compromise your other accounts. but Diceware can be good for a master password to your password manager or just use it on accounts where higher security is needed like email/banking.
Diceware is easy to use. if you got five dice you simply roll the dice a total of six times (each dice roll is a 5 digit number which you simply read from left to right, or right to left, as the dice fall in front of you and using that Diceware word list you look up the number you rolled with the dice in that txt file (use CTRL+F on your basic text program since it will find your number much faster than manually going through it) and that’s the first word to your passphrase) to create a six word (or longer) passphrase. if you got only one dice you will have to roll that single dice 30 times to come up with six words. so it’s a bit more time consuming vs if you got five dice and roll them all at once since each roll of five dice gives you one word.
With 5 dice, why not call it some variant of Yahtzee?
+1
Dicewear seriously reduces your space, to 1-6 for the majority of the characters. What is generates is particularly unmemorable. If you are going to have an automatically generated password, it has no advantages.
@ L Jean Camp
It does have advantages in the sense it’s much easier to type in and is secure if you have enough words as if you have to type in some long randomly generated bunch of random characters it’s going to be harder to do and will take more time since it’s easier/takes less time for us humans to type in words vs a bunch of random characters.
also, I don’t know the details but you have a guaranteed level of entropy with Diceware that you don’t have by selecting something in your own mind which won’t be truly random. from what I read on some sites it appears if you use a 10 word Diceware passphrase it’s pretty much uncrackable (at least not for the foreseeable future(hell, even a bit less words than that is not likely to be cracked either)) since it’s around 129bits and I suspect is a bit more if you use a bit of padding and use at least one lower/upper case letter, a symbol, and a number.
Diceware is good for making a master password to someones password manager and then having the password manager generate some long/random/complex password you don’t have to remember is optimal. but if one is generating a master password for their password manager I suspect a better compromise is to consider using some level of Diceware (say 4-6 words, which will probably be easier to remember) paired with padding as this way it might not be super secure but likely secure enough especially for the common person since it appears the hacker types tend to go after, as they say, ‘the low hanging fruit’.
Brian, I’m left wondering why the Mentos are in this picture. Is there a secret in that box besides mints?
I have this image in my head of the suspect being handcuffed in the car, then picks the lock and runs away. Turns back to the bewildered police officers, smiles… and holds up his Mentos. “The fresh maker!”
How can people even SEE these things? :^)
I haven’t been receiving your emails since the patch tuesday post. I only came here because this post was reported on on in the news
It is funny to watch people waste time trying to defend against dictionary attacks by placing odd characters in the password. Dictionary attacks are old school. A skilled hacker has automated the process and uses every character combination. The only way to slow down these folks is with a long pass phrase. But even that is like playing a slot machine. They could guess correctly on their first pull of the handle. In other words, a long password will not take a hundred years to crack. It could take UP TO 100 years to crack. It could crack on the first attempt. I hate to say it but I know that I am the first one to say it…. One thing that people and even the hackers have NOT considered is to use ASCII characters that are not on the keyboard. Duh.
Many, if not most, sites allow only certain special characters in their passwords. Characters not on the standard keyboard are rarely, if ever, allowed.
And of course there are the sites that don’t allow any special characters. Can someone tell me(being just a “wannabe” tech guy) why do websites have any limitations on passwords/phrases?
The reason why non-keyboard characters are not considered, is because they also don’t work for passwords. Nearly all password fields won’t accept them.
Increasing the character set does help. But its a linear increase in password strength… adding length, is exponential. Simplified, the password strength against brute force, is the set of possible characters to the power of the length of characters in the password.
Hackers have dictionaries in many languages, have masking patterns and cracking algorithms that will substitute 1337 (leet (elite) speak) characters, etc.
So rule of thumb, if it’s memorable, it’s weak. Someone has already thought your mnemonic device and wrote something to crack it.
Use a random password generator, and use the longest allowed password. If you absolutely have to make it memorable, then passphrases with mixed character sets are best, again make it as long as possible.
Very good stuff, and entertaining – maybe a few years out of date. https://www.coursera.org/learn/crypto
San Bernardino has two “R’s”
Hi Brian hope you are well, been a longtime reader of your blog and like the updates you share. I am looking to start a new website to curate information and news within the cyber security industry and was wondering if it would be ok to use your blog feed. I will only be publishing the title and a short snippet with an attribution link and button to read more which will go straight to your blog post.
There’s an interesting article on digital surveillance which has bee developed and adopted in China. The article outlines the APP WeChat.
WeChat became increasingly intertwined with modern life in China, it’s true purpose rapidly became apparent. The Chinese government use it as a surveillance tool. Tencent can access deleted messages, and has no end-to-end encryption.
The News article in question – titled ‘Cyber Generation Unknown’ is a very interesting read: https://www.vrone.co.uk/chris-world/articles/cyber-generation-unknown