Three individuals have been charged for their alleged roles in the July 15 hack on Twitter, an incident that resulted in Twitter profiles for some of the world’s most recognizable celebrities, executives and public figures sending out tweets advertising a bitcoin scam.
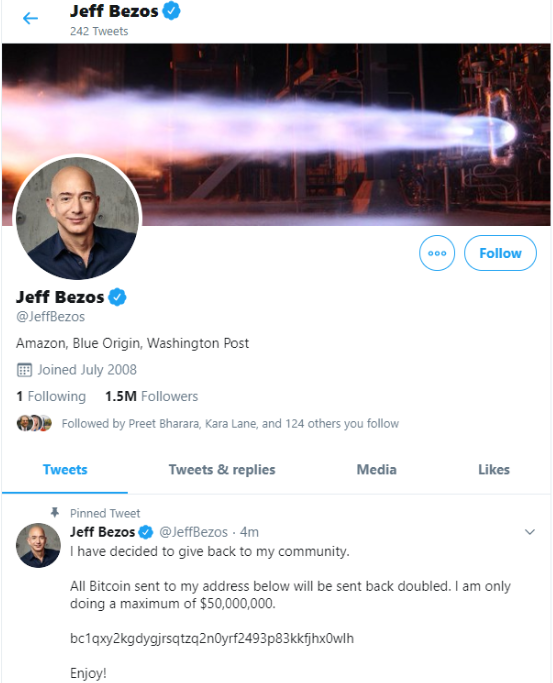
Amazon CEO Jeff Bezos’s Twitter account on the afternoon of July 15.
Nima “Rolex” Fazeli, a 22-year-old from Orlando, Fla., was charged in a criminal complaint in Northern California with aiding and abetting intentional access to a protected computer.
Mason “Chaewon” Sheppard, a 19-year-old from Bognor Regis, U.K., also was charged in California with conspiracy to commit wire fraud, money laundering and unauthorized access to a computer.
A U.S. Justice Department statement on the matter does not name the third defendant charged in the case, saying juvenile proceedings in federal court are sealed to protect the identity of the youth. But an NBC News affiliate in Tampa reported today that authorities had arrested 17-year-old Graham Clark as the alleged mastermind of the hack.

17-year-old Graham Clark of Tampa, Fla. was among those charged in the July 15 Twitter hack. Image: Hillsborough County Sheriff’s Office.
Wfla.com said Clark was hit with 30 felony charges, including organized fraud, communications fraud, one count of fraudulent use of personal information with over $100,000 or 30 or more victims, 10 counts of fraudulent use of personal information and one count of access to a computer or electronic device without authority. Clark’s arrest report is available here (PDF). A statement from prosecutors in Florida says Clark will be charged as an adult.
On Thursday, Twitter released more details about how the hack went down, saying the intruders “targeted a small number of employees through a phone spear phishing attack,” that “relies on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities to gain access to our internal systems.”
By targeting specific Twitter employees, the perpetrators were able to gain access to internal Twitter tools. From there, Twitter said, the attackers targeted 130 Twitter accounts, tweeting from 45 of them, accessing the direct messages of 36 accounts, and downloading the Twitter data of seven.
Among the accounts compromised were democratic presidential candidate Joe Biden, Amazon CEO Jeff Bezos, President Barack Obama, Tesla CEO Elon Musk, former New York Mayor Michael Bloomberg and investment mogul Warren Buffett.
The hacked Twitter accounts were made to send tweets suggesting they were giving away bitcoin, and that anyone who sent bitcoin to a specified account would be sent back double the amount they gave. All told, the bitcoin accounts associated with the scam received more than 400 transfers totaling more than $100,000.
Sheppard’s alleged alias Chaewon was mentioned twice in stories here since the July 15 incident. On July 16, KrebsOnSecurity wrote that just before the Twitter hack took place, a member of the social media account hacking forum OGUsers named Chaewon advertised they could change email address tied to any Twitter account for $250, and provide direct access to accounts for between $2,000 and $3,000 apiece.
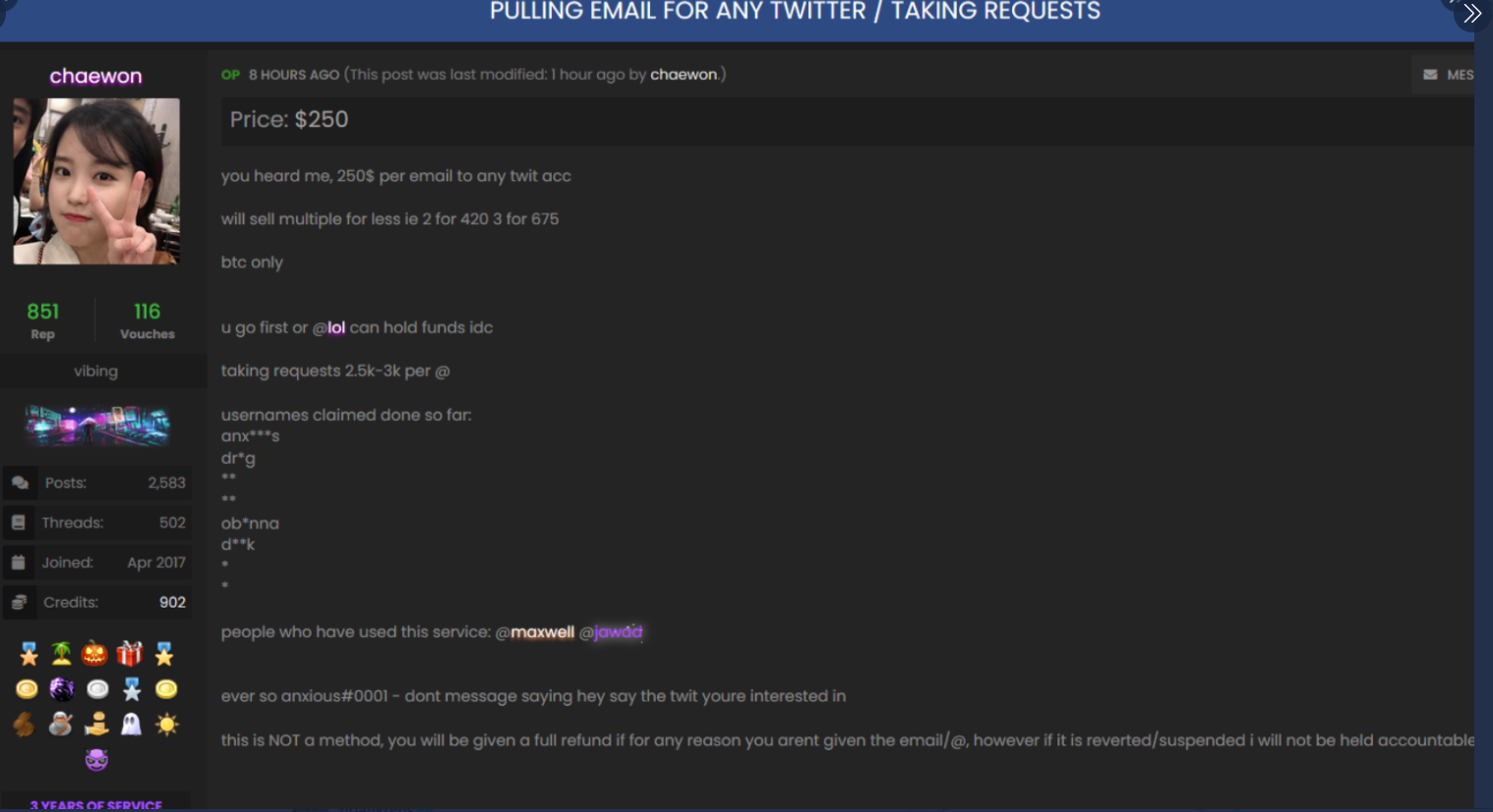
The OGUsers forum user “Chaewon” taking requests to modify the email address tied to any twitter account.
On July 17, The New York Times ran a story that featured interviews with several people involved in the attack. The young men told The Times they weren’t responsible for the Twitter bitcoin scam and had only brokered the purchase of accounts from the Twitter hacker — who they referred to only as “Kirk.”
One of those interviewed by The Times used the alias “Ever So Anxious,” and said he was a 19-year from the U.K. In my follow-up story on July 22, it emerged that Ever So Anxious was in fact Chaewon.
The person who shared that information was the principal subject of my July 16 post, which followed clues from tweets sent by one of the accounts claimed during the Twitter compromise back to a 21-year-old from the U.K. who uses the nickname PlugWalkJoe.
That individual shared a series of screenshots showing he had been in communications with Chaewon/Ever So Anxious just prior to the Twitter hack, and had asked him to secure several desirable Twitter usernames from the Twitter hacker. He added that Chaewon/Ever So Anxious also was known as “Mason.”
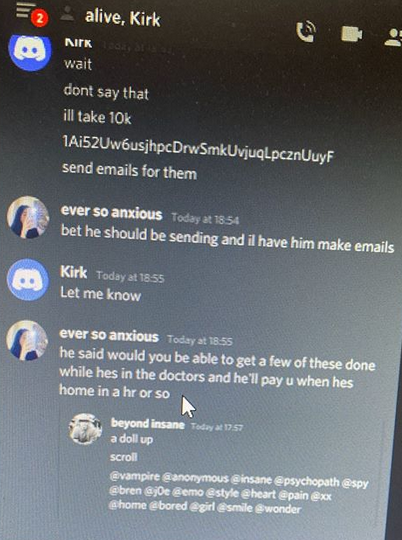
The negotiations over highly-prized Twitter usernames took place just prior to the hijacked celebrity accounts tweeting out bitcoin scams. PlugWalkJoe is pictured here chatting with Ever So Anxious/Chaewon/Mason using his Discord username “Beyond Insane.”
On July 22, KrebsOnSecurity interviewed Mason/Chaewon/Ever So Anxious, who confirmed that PlugWalkJoe had indeed asked him to ask Kirk to change the profile picture and display name for a specific Twitter account on July 15. Mason/Chaewon/Ever So Anxious acknowledged that while he did act as a “middleman” between Kirk and others seeking to claim desirable Twitter usernames, he had nothing to do with the hijacking of the VIP Twitter accounts for the bitcoin scam that same day.
“Encountering Kirk was the worst mistake I’ve ever made due to the fact it has put me in issues I had nothing to do with,” he said. “If I knew Kirk was going to do what he did, or if even from the start if I knew he was a hacker posing as a rep I would not have wanted to be a middleman.”
Another individual who told The Times he worked with Ever So Anxious/Chaewon/Mason in communicating with Kirk said he went by the nickname “lol.” On July 22, KrebsOnSecurity identified lol as a young man who went to high school in Danville, Calif.
Federal investigators did not mention lol by his nickname or his real name, but the charging document against Sheppard says that on July 21 federal agents executed a search warrant at a residence in Northern California to question a juvenile who assisted Kirk and Chaewon in selling access to Twitter accounts. According to that document, the juvenile and Chaewon had discussed turning themselves in to authorities after the Twitter hack became publicly known.




“IRS wasn’t involved in the investigation.” – JamminJ
Agent T. G. of the IRS did a lot of the Bitcoin tracings. I am sure you can find the court pdf: CRIMINAL COMPLAINT U.S. DISTRICT COURT NORTHERN DISTRICT OF CALIFORNIA SAN FRANCISCO. Affidavit, I am employed as a Special Agent with the Internal Revenue Service Criminal Investigation (“IRS-CI”) in Washington, D.C….
Now, as for the one-time password, I would like to hear from experts on how much information is held in cryptogram. From the cryptograms I have used used the OTP usually generates a number of data points when the person who gets via email including machine finger printing and other data and time to live. This is then send back to the secure server to ensure people who get the OTP are who they are and where they are and if the time of the OTP has expired. I am confused as to how it slipped into Twitters internal network.
Ack.
I misstated and was wrong about the IRS. The details in the affidavit are indeed interesting. Thanks for following up.
“Why would an encrypted VPN into the Twitter network allow two individuals to type in user name-password also the one-time password from two locations?”
-KoSReader600000
A common attack vector for this kind of credential theft social engineering combo, is a phishing page that isn’t the real login. Many VPNs do not use a thick client application, but rather a Web app client (SSL VPN).
So if the attackers know what the real VPN login page looks like, have a social engineering hook into some employees, it is easy to have the victim go to the attacker controlled spoofed web login page. They enter username, password, and OTP.
I am not sure if you were asking about 2FA used for the VPN, the Admin Tool, or both.
2FA is common to use for VPN, and with many working from home, it is a safe bet the victims had VPN access. And with VPN using 2FA, it is a safe bet that if the Admin Tool needed 2FA,… it’ll be the same token (phone, RSA hard token, Yubikey, whatever).
What isn’t clear about Twitter’s security posture, is whether the authentication into the Admin Tool required the client system to be on the network (already VPN’d), client certificates, or device/browser fingerprinting. If the Tool only required the right credentials and a client being on the network… then the security might only be as strong as the VPN access, since that requires the creds (with OTP) that could have been stolen in a single social engineering session.
If the OTP is just a TOTP (like most are), then the timing doesn’t have to be that quick. 30 seconds is trivial.
With the push for many companies to support a remote workforce, using BYOD for employees and put everything “in the cloud”. It is very feasible that Twitter has 2FA protections that do not include extras like device fingerprinting, client certificates, etc.
Mugshot looks remarkably like Norman Bates’. Just sayin’.
https://vignette.wikia.nocookie.net/psycho/images/6/63/NormanProfile.jpg