Three individuals have been charged for their alleged roles in the July 15 hack on Twitter, an incident that resulted in Twitter profiles for some of the world’s most recognizable celebrities, executives and public figures sending out tweets advertising a bitcoin scam.
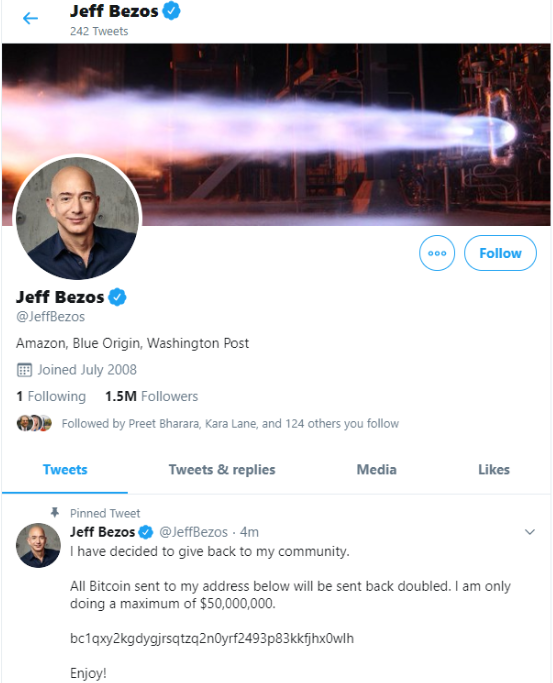
Amazon CEO Jeff Bezos’s Twitter account on the afternoon of July 15.
Nima “Rolex” Fazeli, a 22-year-old from Orlando, Fla., was charged in a criminal complaint in Northern California with aiding and abetting intentional access to a protected computer.
Mason “Chaewon” Sheppard, a 19-year-old from Bognor Regis, U.K., also was charged in California with conspiracy to commit wire fraud, money laundering and unauthorized access to a computer.
A U.S. Justice Department statement on the matter does not name the third defendant charged in the case, saying juvenile proceedings in federal court are sealed to protect the identity of the youth. But an NBC News affiliate in Tampa reported today that authorities had arrested 17-year-old Graham Clark as the alleged mastermind of the hack.

17-year-old Graham Clark of Tampa, Fla. was among those charged in the July 15 Twitter hack. Image: Hillsborough County Sheriff’s Office.
Wfla.com said Clark was hit with 30 felony charges, including organized fraud, communications fraud, one count of fraudulent use of personal information with over $100,000 or 30 or more victims, 10 counts of fraudulent use of personal information and one count of access to a computer or electronic device without authority. Clark’s arrest report is available here (PDF). A statement from prosecutors in Florida says Clark will be charged as an adult.
On Thursday, Twitter released more details about how the hack went down, saying the intruders “targeted a small number of employees through a phone spear phishing attack,” that “relies on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities to gain access to our internal systems.”
By targeting specific Twitter employees, the perpetrators were able to gain access to internal Twitter tools. From there, Twitter said, the attackers targeted 130 Twitter accounts, tweeting from 45 of them, accessing the direct messages of 36 accounts, and downloading the Twitter data of seven.
Among the accounts compromised were democratic presidential candidate Joe Biden, Amazon CEO Jeff Bezos, President Barack Obama, Tesla CEO Elon Musk, former New York Mayor Michael Bloomberg and investment mogul Warren Buffett.
The hacked Twitter accounts were made to send tweets suggesting they were giving away bitcoin, and that anyone who sent bitcoin to a specified account would be sent back double the amount they gave. All told, the bitcoin accounts associated with the scam received more than 400 transfers totaling more than $100,000.
Sheppard’s alleged alias Chaewon was mentioned twice in stories here since the July 15 incident. On July 16, KrebsOnSecurity wrote that just before the Twitter hack took place, a member of the social media account hacking forum OGUsers named Chaewon advertised they could change email address tied to any Twitter account for $250, and provide direct access to accounts for between $2,000 and $3,000 apiece.
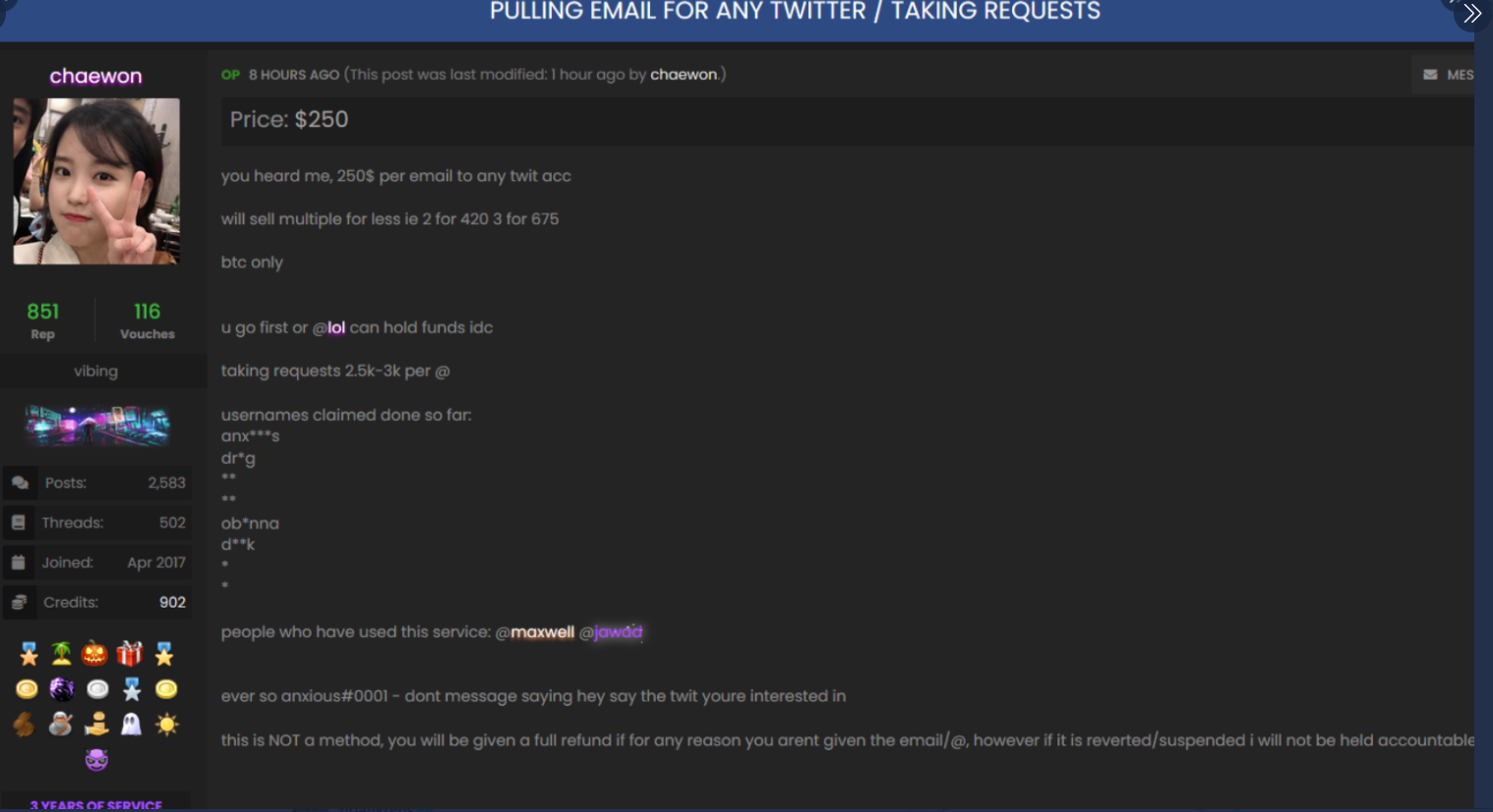
The OGUsers forum user “Chaewon” taking requests to modify the email address tied to any twitter account.
On July 17, The New York Times ran a story that featured interviews with several people involved in the attack. The young men told The Times they weren’t responsible for the Twitter bitcoin scam and had only brokered the purchase of accounts from the Twitter hacker — who they referred to only as “Kirk.”
One of those interviewed by The Times used the alias “Ever So Anxious,” and said he was a 19-year from the U.K. In my follow-up story on July 22, it emerged that Ever So Anxious was in fact Chaewon.
The person who shared that information was the principal subject of my July 16 post, which followed clues from tweets sent by one of the accounts claimed during the Twitter compromise back to a 21-year-old from the U.K. who uses the nickname PlugWalkJoe.
That individual shared a series of screenshots showing he had been in communications with Chaewon/Ever So Anxious just prior to the Twitter hack, and had asked him to secure several desirable Twitter usernames from the Twitter hacker. He added that Chaewon/Ever So Anxious also was known as “Mason.”
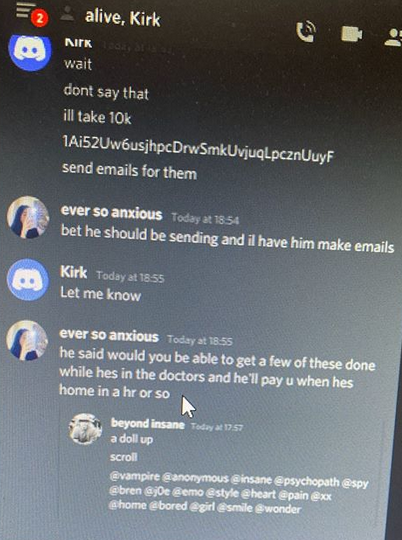
The negotiations over highly-prized Twitter usernames took place just prior to the hijacked celebrity accounts tweeting out bitcoin scams. PlugWalkJoe is pictured here chatting with Ever So Anxious/Chaewon/Mason using his Discord username “Beyond Insane.”
On July 22, KrebsOnSecurity interviewed Mason/Chaewon/Ever So Anxious, who confirmed that PlugWalkJoe had indeed asked him to ask Kirk to change the profile picture and display name for a specific Twitter account on July 15. Mason/Chaewon/Ever So Anxious acknowledged that while he did act as a “middleman” between Kirk and others seeking to claim desirable Twitter usernames, he had nothing to do with the hijacking of the VIP Twitter accounts for the bitcoin scam that same day.
“Encountering Kirk was the worst mistake I’ve ever made due to the fact it has put me in issues I had nothing to do with,” he said. “If I knew Kirk was going to do what he did, or if even from the start if I knew he was a hacker posing as a rep I would not have wanted to be a middleman.”
Another individual who told The Times he worked with Ever So Anxious/Chaewon/Mason in communicating with Kirk said he went by the nickname “lol.” On July 22, KrebsOnSecurity identified lol as a young man who went to high school in Danville, Calif.
Federal investigators did not mention lol by his nickname or his real name, but the charging document against Sheppard says that on July 21 federal agents executed a search warrant at a residence in Northern California to question a juvenile who assisted Kirk and Chaewon in selling access to Twitter accounts. According to that document, the juvenile and Chaewon had discussed turning themselves in to authorities after the Twitter hack became publicly known.




Lets hope for some good prison tweets from these punks
Digital crime must result in the death penalty, as a universal phonomena of our times.
Hospital, essential servies hit.
Crimimal justice has not evolved sufficiently;
20 year olds can endure 2 years in jail; our hospital just blew 1.4 million to digital thugs.
Stop with the fascists draconian measures to criminal justice.
If the government can justify the death penalty for cyber crime, look out… those same laws will hang you too.
Now that was quick ! LOL
Yeah, when the rich elite are affected law enforcement seems to catch the miscreants very quickly. For the rest of us subject to fraud less diligence in apprehending the criminals is seen.
Wow. I wish they would have captured the hackers from other breaches as fast as they did for the Twitter jack attacks. I guess the investigators are getting better and faster. Good sign and good work.
It probably didn’t take much investigating on the fed’s part, they just had to read Krebs 10 minutes after this happened. Or the yahoos giving interviews to NYT the next day.
The owls are not what they seem Grady.
This only scratches the surface as to who was involved. Kirk was also in contact with many other prominent figures who pulled other high level SEing scams which will probably become public soon after his interview with FBI.
So is. Kirk a twitter employee or a hacker that managed to get internal tools?
And Kirk got away while this poor kid got 45 years??? . UN REAL !!!!
From the website arstechnica.(dot) com today,
The attackers then called the employees and used the information obtained from LinkedIn and other public sources to convince them they were authorized Twitter personnel. Work-at-home arrangements caused by the COVID-19 pandemic also prevented the employees from using normal procedures such as face-to-face contact to verify the identities of the callers.
With the confidence of the targeted employees, the attackers directed them to a phishing page that mimicked an internal Twitter VPN. The attackers then obtained credentials as the targeted employees entered them. To bypass two-factor authentication protections Twitter has in place, the attackers entered the credentials into the real Twitter VPN portal within seconds of the employees entering their info into the fake one. Once the employee entered the one-time password, the attackers were in.
…what a wicked web we weave…
I suggest you look into PlugWalkJoe, he has done things far worse then these guys. He has accumulated (in his words) around 9 million dollars in bitcoin from Sim Swapping and Extorting
Plugwalkjoe is more of a celeb guy, and those were shoutouts he didnt hack. He flexed a pic wasnt his, krebs reported good stuff but pwj is no rich guy hes a fake flexer. brian proved that
Nah he has money. Maybe not 9m but ask around.
It’s hard for me to comprehend how someone like Graham Clark could make such an obvious mistake of verifying his own coinbase account with his own driver’s license then receive the stolen bitcoin there.
I guess they put so much thought and energy into navigating rogue paths to other people’s data that they forget to protect paths to their own.
Like that Silk Road guy arrested in a San Francisco library years ago: his laptop wasn’t even encrypted.
That guy’s laptop wasn’t encrypted because the FBI set up an elaborate operation to seize the computer out of his hands before he even knew they were there.
I don’t remember if he actually had an encrypt hot key, but it wouldn’t have been useful in that situation anyway.
Silk Road guy laptop was encrypted. They made sure to arrest him while he was using it and logged in. They coordinated this, so he could not even close the laptop and someone took it immediately out of his hands keeping the system running to avoid the system from locking itself.
No way he actually did that. Do you have source? That’s hilarious.
There’s a Wired article that describes the takedown in detail and i remember that part sticking out. They only had a small window of time to make sure he couldn’t shutdown before they seized the laptop. If its true that is. Who really knows. Could be someone else altogether.
I remember the library sting operation.
They got a female agent to cause a distraction, and other agents grabbed his open laptop while he was working on it.
It was previously known that DPR uses encryption on his laptop. And agents usually seize computers with mouse jigglers.
There was a whole book written about the Silk Road takedown. It describes this incident in detail, but that’s the gist of it.
If memory serves, two agent posed as a couple and started a loud argument nearby, and then they swarmed.
I still don’t understand how the spearphish worked. I know they sent a clever email to a select group of Twitter employees. What happened next? A link to a fake login page for credential grabbing? An MS Office attachment with a macro hack?
I assume they had to remote into the Twitter network, then get to the admin tool. Otherwise, even with Twitter admin credentials, is the Twitter Admin tool really on the open internet?
scrim aka graham clark also stole millions of dollars via sim swapping and needs to be further investigated
Silk Road. I’d forgotten all about that one. Wasn’t much to be found on it while it was current news.
One or more (local) restaurants went by that name at a time current arrestees were just starting to get bolder with their crimes. I’ve always wondered what networking, if any, a good investigator with the right databases might turn up.
Nice. Hope Twitter gets hit harder next time.
I know this is crazy talk, but if all these VIPs had a RSS feed, they could say what they wanted to say from a website they control. Also they wouldn’t get trolled.
I think using a service you can’t control is a bad idea if your named and reputation are concerned. No government entity should be using social media.
I’ll eat my hat if you can find one legit celebrity on Twitter that knows what RSS is. They’re not the most tech-savvy lot.
Maybe not the celebs… but the initial attack on twitter, was on the accounts owned by cryptocurrency companies.
eah, when the rich elite are affected law enforcement seems to catch the miscreants very quickly.
It was a good scam effort anyway. Haha
I’m beginning to believe some of these actors were not concerned with getting caught – they probably liked the attention it would get almost as much as the money – if all of them knew money was going to be involved, that is. They are not completely stupid, so should be totally aware of what is coming to pass.
Given the ages, 17, 19, and 22…
I would not assume any forethought about consequences.
Anyone know where the court document PDF is posted?
(The accusatory instrument)
There are links in this article: https://www.zdnet.com/article/how-the-fbi-tracked-down-the-twitter-hackers/
Did you share your finding with John Szydlik or were they already on to these kids?
Hard to say which is worse, the attackers opsec, or Twitters’ security posture? Luckily for Twitter, the damaged they caused was relatively minor compared to the level of access they had.
Dorsey will probably hire him for cyber security!
what a shame that internal critical major production servers are open from the outside for attackers . this is big shame for twitter as i see the was not got any VPN connection or similar just strong credentials and thats it . poor security and big shame again.
If you or your systems are not smarter than a 17 year old, step away from your keyboard.
There is no person or device that I cannot catch anywhere on Earth doing criminal activity. You cannot hide or transfer your identity or location from me and if you are curious enough then try it, the prisons are full of older guys who believed they couldn’t be caught, please don’t cry about people who were not charged due to public relations that I don’t control.
Have a nice honest day!
If I were a Twitter user I’d be most concerned that just about any yahoo working at Twitter has access to that tool, which means anyone can read everything to post, including private IM’s.
It’s only a matter of time, if it hasn’t happened already, that a 19 year-old intern that just read Atlas Shrugged starts selling/leaking private info OTC.
This sounds like slick confidence game. But, this con-game seems a bit too slick and a little unbelievable without a degree of insider help. I am confused by the reporting of this scam. The site Vice-Motherboard site held to the notion that an inside “rep” of Twitter or outside consultant gave a bit of help to con-men. Who knows. What’s confusing is ZDnet report a teen from Florida who may have been in northern California (close to Twitter) started in May of this year probing Twitter. This scammer got very lucky and found Twitter’s slack channel with sensitive data. It a bit murky from May to July 15 but withthe help of other con-men the group setup a fake “Twitter Admin” page to get a Twitter employee to type in his user name and password for the Twitter Admin tool in the core of Twitter network and somehow scrape or grabbed the “reps” user name and password – which are generally a cryptogram or encrypted tokenized and the con-man just typed said “credentials” into the actual Twitter Tool and waited for the pawnd “rep” to get one time password from an his/her email which was somehow also “typed” into the actual Twitter Admin Tool maybe by the con-artist or the Twitter “rep” cough, which seems odd. Why would an encrypted VPN into the Twitter network allow two individuals to type in user name-password also the one-time password from two locations? Maybe it was all a confidence act including the pawnd Twitter rep. Who is to say. How did the “one time password” actually get in the Admin Tool at the same time the credentials and password? That seems like very good timing.
I have been following the scam but not that closely. There needs to be some clarification on the actual mechanics of this scam. Last, I will say the IRS is getting better at tracing bitcoin transactions and clusters.
IRS wasn’t involved in the investigation.
Tracing bitcoin is rarely the thing that exposes these cyber criminals. Criminals need only a quick tutorial on tumblers and basic understanding to evade tracing their stolen bitcoin.
The old tricks still work the best. Communication of the conspiracy is not so organized as the financials. In organized crime, they have this down to a science, since they get instruction from the top on which comms to avoid, which to use, and how. Remember the pay phones back in the day?
With “un”organized criminals who are conspiring (working with) other criminals they may not trust and likely never met before… the comms are much less secure, because they never know who the feds are. And LE is often pretending to be your criminal co-conspirator.
So that is what cracked this case so fast, and so easily. The criminals conspired over insecure channels because they didn’t really trust each other nor have they worked closely before.
It’s so easy to find these people because they flex everything on twitter, insta, discord, etc. If the feds actually looked into discord/certain discord servers they’d see how easy it is to see these people flexing things and admitting to things. I mean some of these discord servers are filled to the brim with sim holders/swappers/callers. I mean you can easily encounter them by going into most OG discord vanity invite links
https://www.zdnet.com/article/how-the-fbi-tracked-down-the-twitter-hackers/
“Per court documents, the FBI used data shared on social media and by news outlets to get chat logs and user details from Discord. ”
“Correlating data from the three sources, the FBI was able to track hacker identities on the three sites, and link them to email and IP addresses. ”
“For example, authorities tracked Fazili down after he linked his Discord username from his OGUsers page, an obvious operational security (OpSec) mistake. “
Open-and-shut case: hackers with downright terrible OpSec get caught. Breaking news: water is wet and hackers with terrible opsec also get wet.
Good article as usual though Brian!
No way he actually did that. Do you have source?
so who was josh perry then?
From the story:
“Another individual who told The Times he worked with Ever So Anxious/Chaewon/Mason in communicating with Kirk said he went by the nickname “lol.” On July 22, KrebsOnSecurity identified lol as a young man who went to high school in Danville, Calif.
Federal investigators did not mention lol by his nickname or his real name, but the charging document against Sheppard says that on July 21 federal agents executed a search warrant at a residence in Northern California to question a juvenile who assisted Kirk and Chaewon in selling access to Twitter accounts. According to that document, the juvenile and Chaewon had discussed turning themselves in to authorities after the Twitter hack became publicly known.”