Twitter was thrown into chaos on Wednesday after accounts for some of the world’s most recognizable public figures, executives and celebrities starting tweeting out links to bitcoin scams. Twitter says the attack happened because someone tricked or coerced an employee into providing access to internal Twitter administrative tools. This post is an attempt to lay out some of the timeline of the attack, and point to clues about who may have been behind it.
The first public signs of the intrusion came around 3 PM EDT, when the Twitter account for the cryptocurrency exchange Binance tweeted a message saying it had partnered with “CryptoForHealth” to give back 5000 bitcoin to the community, with a link where people could donate or send money.
Minutes after that, similar tweets went out from the accounts of other cryptocurrency exchanges, and from the Twitter accounts for democratic presidential candidate Joe Biden, Amazon CEO Jeff Bezos, President Barack Obama, Tesla CEO Elon Musk, former New York Mayor Michael Bloomberg and investment mogul Warren Buffett.
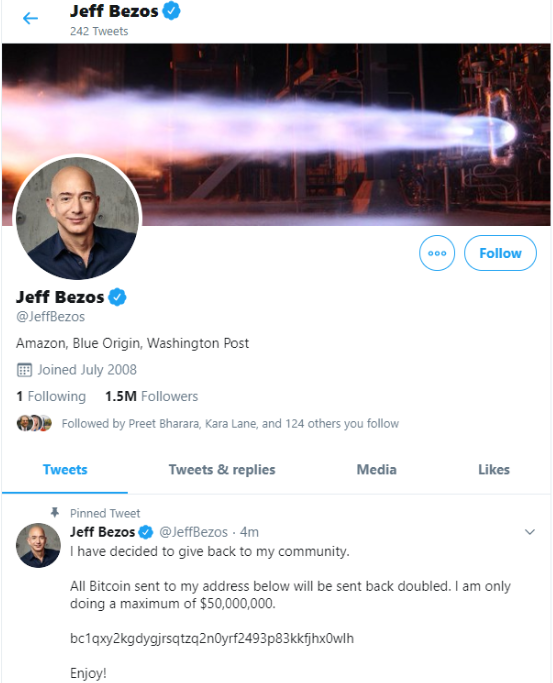
While it may sound ridiculous that anyone would be fooled into sending bitcoin in response to these tweets, an analysis of the BTC wallet promoted by many of the hacked Twitter profiles shows that over the past 24 hours the account has processed 383 transactions and received almost 13 bitcoin — or approximately USD $117,000.
Twitter issued a statement saying it detected “a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools. We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.”
There are strong indications that this attack was perpetrated by individuals who’ve traditionally specialized in hijacking social media accounts via “SIM swapping,” an increasingly rampant form of crime that involves bribing, hacking or coercing employees at mobile phone and social media companies into providing access to a target’s account.
People within the SIM swapping community are obsessed with hijacking so-called “OG” social media accounts. Short for “original gangster,” OG accounts typically are those with short profile names (such as @B or @joe). Possession of these OG accounts confers a measure of status and perceived influence and wealth in SIM swapping circles, as such accounts can often fetch thousands of dollars when resold in the underground.
In the days leading up to Wednesday’s attack on Twitter, there were signs that some actors in the SIM swapping community were selling the ability to change an email address tied to any Twitter account. In a post on OGusers — a forum dedicated to account hijacking — a user named “Chaewon” advertised they could change email address tied to any Twitter account for $250, and provide direct access to accounts for between $2,000 and $3,000 apiece.
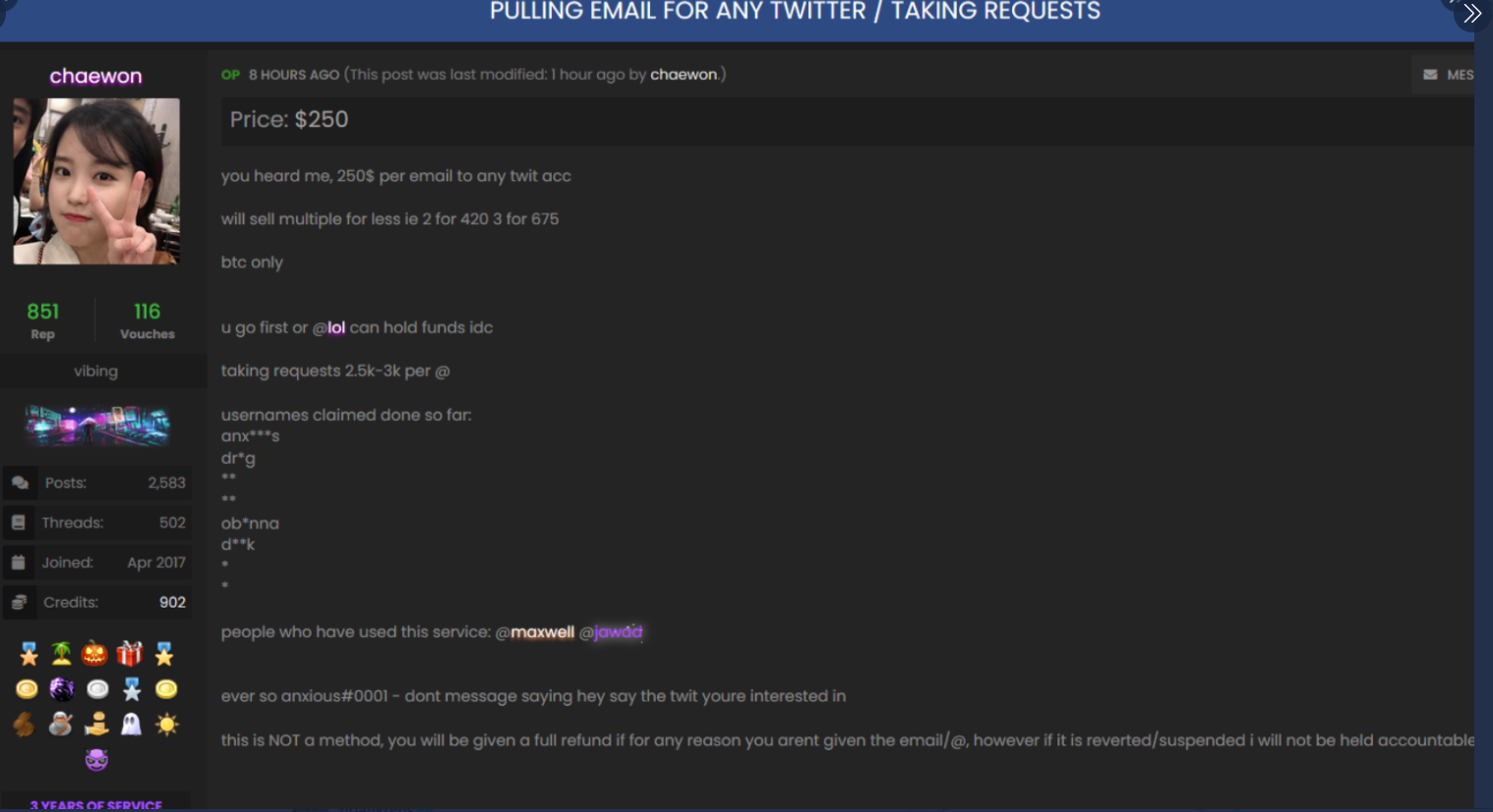
The OGUsers forum user “Chaewon” taking requests to modify the email address tied to any twitter account.
“This is NOT a method, you will be given a full refund if for any reason you aren’t given the email/@, however if it is revered/suspended I will not be held accountable,” Chaewon wrote in their sales thread, which was titled “Pulling email for any Twitter/Taking Requests.”
Hours before any of the Twitter accounts for cryptocurrency platforms or public figures began blasting out bitcoin scams on Wednesday, the attackers appear to have focused their attention on hijacking a handful of OG accounts, including “@6.”
That Twitter account was formerly owned by Adrian Lamo — the now-deceased “homeless hacker” perhaps best known for breaking into the New York Times’s network and for reporting Chelsea Manning‘s theft of classified documents. @6 is now controlled by Lamo’s longtime friend, a security researcher and phone phreaker who asked to be identified in this story only by his Twitter nickname, “Lucky225.”
Lucky225 said that just before 2 p.m. EDT on Wednesday, he received a password reset confirmation code via Google Voice for the @6 Twitter account. Lucky said he’d previously disabled SMS notifications as a means of receiving multi-factor codes from Twitter, opting instead to have one-time codes generated by a mobile authentication app.
But because the attackers were able to change the email address tied to the @6 account and disable multi-factor authentication, the one-time authentication code was sent to both his Google Voice account and to the new email address added by the attackers.
“The way the attack worked was that within Twitter’s admin tools, apparently you can update the email address of any Twitter user, and it does this without sending any kind of notification to the user,” Lucky told KrebsOnSecurity. “So [the attackers] could avoid detection by updating the email address on the account first, and then turning off 2FA.”
Lucky said he hasn’t been able to review whether any tweets were sent from his account during the time it was hijacked because he still doesn’t have access to it (he has put together a breakdown of the entire episode at this Medium post).
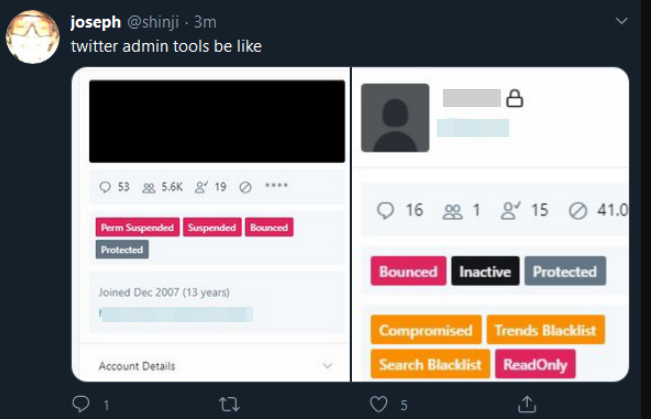
But around the same time @6 was hijacked, another OG account – @B — was swiped. Someone then began tweeting out pictures of Twitter’s internal tools panel showing the @B account.
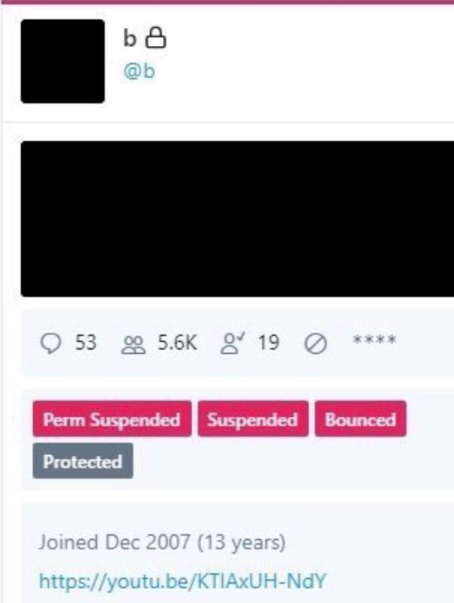
A screenshot of the hijacked OG Twitter account “@B,” shows the hijackers logged in to Twitter’s internal account tools interface.
Twitter responded by removing any tweets across its platform that included screenshots of its internal tools, and in some cases temporarily suspended the ability of those accounts to tweet further.
Another Twitter account — @shinji — also was tweeting out screenshots of Twitter’s internal tools. Minutes before Twitter terminated the @shinji account, it was seen publishing a tweet saying “follow @6,” referring to the account hijacked from Lucky225.
Cached copies of @Shinji’s tweets prior to Wednesday’s attack on Twitter are available here and here. Those caches show Shinji claims ownership of two OG accounts on Instagram — “j0e” and “dead.”
KrebsOnSecurity heard from a source who works in security at one of the largest U.S.-based mobile carriers, who said the “j0e” and “dead” Instagram accounts are tied to a notorious SIM swapper who goes by the nickname “PlugWalkJoe.” Investigators have been tracking PlugWalkJoe because he is thought to have been involved in multiple SIM swapping attacks over the years that preceded high-dollar bitcoin heists.
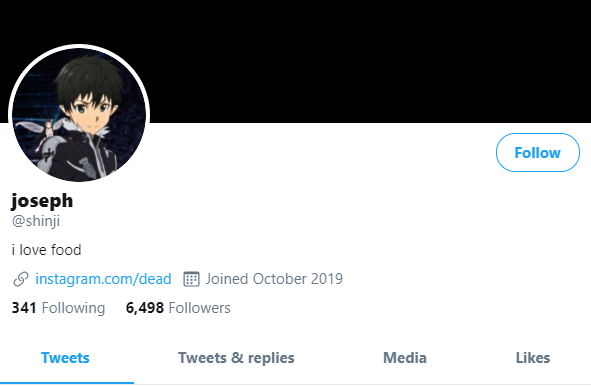
Archived copies of the @Shinji account on twitter shows one of Joe’s OG Instagram accounts, “Dead.”
Now look at the profile image in the other Archive.org index of the @shinji Twitter account (pictured below). It is the same image as the one included in the @Shinji screenshot above from Wednesday in which Joseph/@Shinji was tweeting out pictures of Twitter’s internal tools.
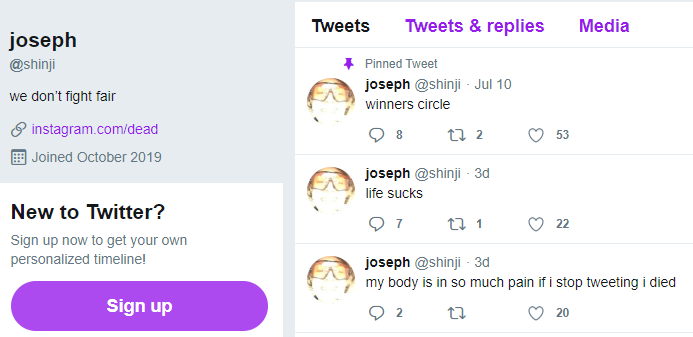
Image: Archive.org
This individual, the source said, was a key participant in a group of SIM swappers that adopted the nickname “ChucklingSquad,” and was thought to be behind the hijacking of Twitter CEO Jack Dorsey‘s Twitter account last year. As Wired.com recounted, @jack was hijacked after the attackers conducted a SIM swap attack against AT&T, the mobile provider for the phone number tied to Dorsey’s Twitter account.
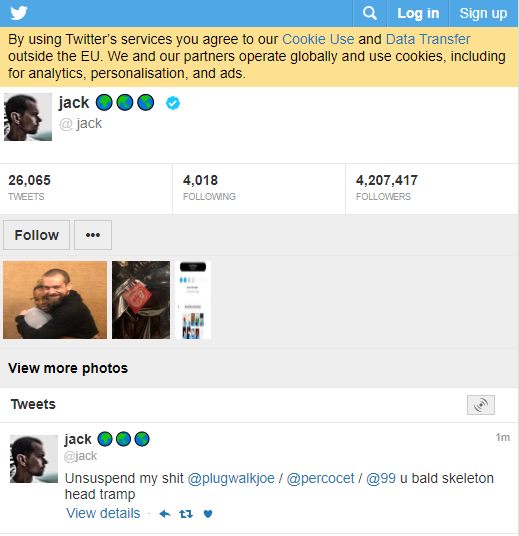
A tweet sent out from Twitter CEO Jack Dorsey’s account while it was hijacked shouted out to PlugWalkJoe and other Chuckling Squad members.
The mobile industry security source told KrebsOnSecurity that PlugWalkJoe in real life is a 21-year-old from Liverpool, U.K. named Joseph James O’Connor. The source said PlugWalkJoe is in Spain where he was attending a university until earlier this year. He added that PlugWalkJoe has been unable to return home on account of travel restrictions due to the COVID-19 pandemic.
The mobile industry source said PlugWalkJoe was the subject of an investigation in which a female investigator was hired to strike up a conversation with PlugWalkJoe and convince him to agree to a video chat. The source further explained that a video which they recorded of that chat showed a distinctive swimming pool in the background.
According to that same source, the pool pictured on PlugWalkJoe’s Instagram account (instagram.com/j0e) is the same one they saw in their video chat with him.
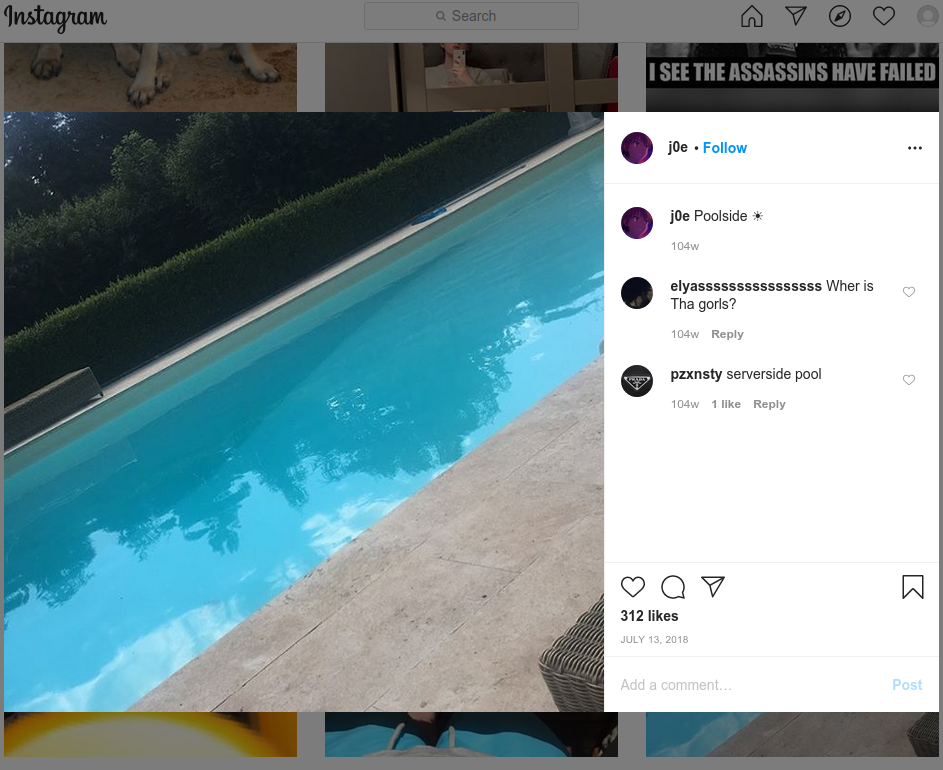
If PlugWalkJoe was in fact pivotal to this Twitter compromise, it’s perhaps fitting that he was identified in part via social engineering. Maybe we should all be grateful the perpetrators of this attack on Twitter did not set their sights on more ambitious aims, such as disrupting an election or the stock market, or attempting to start a war by issuing false, inflammatory tweets from world leaders.
Also, it seems clear that this Twitter hack could have let the attackers view the direct messages of anyone on Twitter, information that is difficult to put a price on but which nevertheless would be of great interest to a variety of parties, from nation states to corporate spies and blackmailers.
This is a fast-moving story. There were multiple people involved in the Twitter heist. Please stay tuned for further updates. KrebsOnSecurity would like to thank Unit 221B for their assistance in connecting some of the dots in this story.




I hope people will start use more the federated social media platforms, like Mastodon, Pixelfed, PeerTube, etc..:
https://en.wikipedia.org/wiki/Fediverse
That way you can have your own instance and protect it however you want, and have whatever accounts (@6, @B, etc) you want. Or you can choose create your account on an existing instance – there are many to choose from.
And you can move your account easily from one instance to another.
Take the step. It’s time.
…And their security is better than Twitter’s or Facebook’s?
I’d say such solutions are a bit more untested in that front so from a security standpoint I would not count those as a “benefit” to using such services.
I’m pretty sure that never will be able a kid to sell access to every account on Mastodon (for example).
I have been using the federated social media platforms for a while now. There actually really amazing and don’t have to worry about your accounts being hacked all the time. No bots are a huge plus
Is that because nobody is using it? If the only users are beta testers, then why would hackers even target this system? There is nothing to gain.
Has anyone done a real security assessment?
They have full access to the most powerful twitter accounts in the world and they scam bitcoin? What a bunch if amateurs.
Have they heard of a thing called stock market?
Dude, they’re 21 and broke, they don’t have access to a stock broker. I’d have gone for elon musk’s account, easy easy TSLA money!
The clowns that bribed the Twitter emp don’t even have 7 figs worth of coin let alone a stock broker. Kids are on low 6 figs, quite small numbers for this com.
Why would ‘a bunch of kids,’ even ‘poor kids,’ waste one of the world’s most potentially powerful hacks on a Bitcoin scam worth a little more than 100,000 dollars?
Especially when they could download the DMs of all of those users, that are worth a s***load more than a mere hundred thou?
If all this was, was a Bitcoin play, the same hack could have gotten them the accounts of numerous major media stars with huge followings who are if anything, less suspicious of foul play than the followings of political and business leaders.
So why would they pick their targets based on the current USA political and business landscape for a mere Bitcoin scam?
What do you think FSB or GRU would pay for the DMs of former President Obama, and his former Vice President Biden who stands for election this year?
Prediction: we will see ‘DM dumps’ as the USA elections come closer. Probably shortly after Labour Day, when the American political season hots-up. Some of the dumped material will be real, some will be faked but crafted to interfere with American politics.
It’s 2016 all over again.
To perform a stock market attack you need a lot of money and you can’t participate in the stock market anonymously. The SEC has all sorts of monitoring in place to catch more common forms of insider trading and fraud and you can guarantee that they would conduct a long, thorough investigation into a hypothetical hack-based market fraud. Unlike Bitcoin transactions, wire transfers and stock purchases can be reversed after the fact, and the exposure and risk go way up when you’re actually working with US dollars.
Do they? Because there sure are a lot of criminals on Wall Street and within the halls of government and corporate America, who seem to get away with it! It would seem that they are using the very powerful security tools selectively at best.
In addition to all the Know Your Customer stuff and SEC oversight, another factor that makes cryptocurrencies more attractive to thieves than trading is that trades take 3 days to clear. That’s ample time for an exchange to reverse a trade or for any party to annul a trade if fraud is suspected.
They obviously are poor criminals, plus bitcoin is more anonymous
New conspiracy theory: Maybe there was no hack, and they only agreed to publish a campaign against bitcoin. I understand that Elon and Bill do not support BTC, Kanye is their friend (but not sure about Jeff and Kanye)… I don’t know Rick, looks fake to me.
Why is this against bitcoin? If they asked for cash or gold, would it have been against those currencies?
This dude is a drainer. Look at his profile picture; its bladee. DG for life man !
blade still owes me 68usd
Krebs, great report, but it would be good if you could not name the alleged individual until they are indicted
How can one be an alleged individual?
@Dan: Sometimes the “alleged” perpetrators only get indicted because they were names and outed by Krebs!!
* named
Hi Joe, nice pool you have there. Be a shame if someone were to see it on a video call
Ok you’re guilty
Try University of Salamanca and swimming en la piscina cerca de the catedral Nueva cerca de la universidad. Enlist Walk Away Joe by Don Henley and Tricia Yearwood. Watch for flammable truck symbols. Watch meet joe Black with Brad Pitt on Amazon Prime if it is still there. You may need to enlist in Showtime. Watch John Conner in the Terminator series especially Terminator Salvation. Look at birds and flowers, sunglasses and eyes.
This was a coded comment to launch the DoS attack on Krebs.
Nice. Expecting more update
Whenever you Agree to Participate in Crypto Exchanges, Every Criminal in the World has Free Reign Over your Digital Domain, and while they PROMISE you Will Make Money, More Often than Not, the Opposite Occurs. It’s like a Giant Pyramid Scheme. Not Only That, Bitcoin Halving REQUIRES that Funds be Annually Withdrawn, So No Matter How Much Money you Invest, you can NEVER Turn a Profit
Lovely to see people talking about things they know nothing about. If what you say is true, why have millions of the originally mined bitcoin NEVER been moved/withdrawn? These are easily inspected on the public blockchain. Can you monitor other people’s bank accounts? No. Blockchain addresses? Yes. Which one do you think provides more accountability?
The bitcoin halving is an event that happens approximately every 4 years (every 210000 mined blocks to be exact) which reduces the miner’s reward in half. Due to the economic effects of supply and demand this eventually creates scarcity in the market, thus driving the price up. Research the stock to flow model for one theory on the eventuality of this feature.
Also, Coinbase, a US based crypto exchange is FDIC insured just like a bank for funds you keep on the exchange. The days of “crypto is for criminals” are long behind us. The majority of people still buy drugs and pay for other illicit activities in cash.
Lastly, no one promises anything about the speculative nature of cryptocurrencies, just like no one guarantees your 401K will increase in value, or that your house will be worth more in the future. Investments are risky, some more than other. Crypto is driven by speculation, thus is inherently more risky than other investments. Nothing about being risky means it is a scam.
Coinbase users’ funds ARE NOT directly insured by the FDIC. Coinbase is not a bank. Users are actually, at best, secondary beneficiaries of FDIC coverage. Why? Because Coinbase supposedly holds users’ dollar deposits in bank accounts COINBASE controls.
Bottom line: if Coinbase becomes insolvent or otherwise “loses” users’ funds (see: Wirecard), users will not receive any payments from the FDIC.
your name makes perfect sense if your comments here.
Nice
If they’d yanked DMs en masse instead of this stunt hacking we’d all be waking up to a different world.
Also, wow DM sure isn’t private.
As I read Krebs’ article, they didn’t necessarily have access to accounts en masse — and who’s to say they didn’t yank all the targeted accounts’ DMs?
That could very well have been their main target, with the bitcoin acting either as obfuscation or a way to get some extra money. This sure seems like a lot of work for just US$117,000. If the perpetration purchased services from chaewon at the prices in the screenshot, it looks like they might have not even made a net profit.
Not sure if DM’s would be all that important. These celebrity twitter accounts are used for mass broadcast communications… and generally the owner doesn’t engage in private conversation with DM’s. And if they do, its probably uninteresting banter.
I’m a novice, but saw this through a link on another page…
Do the internal tools ‘search blacklist’ and ‘trend blacklist’ mean what I think it means—if they don’t want people to see you they put you on that list?
Those tools sure make them look like a publisher, which means they shouldn’t be protected by section 230….
And your statement clearly shows you do not understand Section 230.
Traditional editorial functions such as allowing content to be seen or not are still allowed under Section 230 and does not constitute you as a publisher.
“If you passively host third-party content you will be fully protected under Section 230.
If you passively host third-party content, you will be fully protected under Section 230.
If you exercise traditional editorial functions over user submitted content, such as deciding whether to publish, remove, or edit material, you will not lose your immunity unless your edits materially alter the meaning of the content.
If you pre-screen objectionable content or correct, edit, or remove content, you will not lose your immunity.
If you encourage or pay third-parties to create or submit content, you will not lose your immunity.
If you use drop-down forms or multiple-choice questionnaires, you should be cautious of allowing users to submit information through these forms that might be deemed illegal.”
http://www.dmlp.org/legal-guide/immunity-online-publishers-under-communications-decency-act
Laughing right now so hard, imagine moving all the money to your hardware wallet with no tumble. Joe if you’re reading, which I know you are full of yourself and you probably are reading this, you’re still the same idiot I knew in 2018. Go back to minecraft where you belong. Your pedophilia behavior is disgusting and you honestly are a mockery to “hackers” in general. You leech and leech. You will never be like any of the greats before you, and you know who they are. Anyways, can’t wait for debug and aqua next 😉
If I decide to get rid of my cellphone altogether and instead, get a real landline (which I have confirmed is available where I live), would I still be vulnerable to this SIM swap attack? I am very close to doing this due to not so reliable cell service within my house.
In the U.S., at least, landline phone numbers are vulnerable to being ported out to a mobile phone account. That’s not the same as a SIM swap but the result is the same.
ik them they cool ppl
This startup Anchain.ai is linking the twitter hackers with cryptoForHealth scam group. They are tracking down the bitcoin flow. pretty interesting.
https://medium.com/@AnChain.AI/twitters-tax-day-disaster-the-beginning-and-end-of-mainstream-crypto-scams-6fbbfb520f1b
hmm interesting from the bitcoin side. wondering if anchain knows any intel on the actors. that would help SEC.
I find it amazing that Twitter lambs like to be slaughtered!
Regards,
Could all those childish actions be a false flag operation used to hide the real operation objectives?
Nah. Occam’s Razor.
Project Mau5trap
I was wondering if the Twitter’s admin tool can be accessed from public interface. If it is the case, it is a fundamentally design flaw.
The hacker reused a bitcoin address. That left some trace to track. We will see how it goes.
Screenshot of Jack being hacked will forever be legendary haha
Brian, you might want to read the below NY Times article. It shows someone else was responsible for the Twitter hack and PlugWalkJoe had only a minor, tangential role.
https://www.nytimes.com/2020/07/17/technology/twitter-hackers-interview.html
I have read it. As I said in my story, there are multiple people involved. Joe and his circle have a strong interest in playing down their involvement, and have been spinning different stories to anyone who will listen. But the fact remains that they had advance knowledge of the twitter tools access and were in direct communications with the “insider.” That doesn’t sound to me like a tangential role. Also, keep in mind you’re dealing with a group of people who claimed responsibility for hacking the CEO of twitter’s account just a few months back.
And unfortunately the US and UK legal systems will just give the kids involved a slap on the wrist when they actually should belong in prison.
Hopefully they will all get rolled up soon enough.
Ah, yes… he stole the CEO of twitters account… no big deal right?
This digital thrill seeking seems more addictive to some than any drug mankind has ever known. It must make them feel like mini-Gods or something, and darn be to any consequences and/or harm they may cause in getting that high.
You are all assuming the objective was the silly Bitcoin spam and sale of OG handles. We don’t know what we don’t know.
Twatter might not easily store logs of admin acct viewing DMs or copying / pasting or screenshotting
A few useful idiots allows a blackhat cover to do whatever they want. More important, it allows their handler to meet their own objectives which could be far worse and will take time to uncover. This ain’t over
A good hacker will find his way even with all the security used. Reach Stalkerben84 at G mail
The sim swapping stuff is idiocy. Obviously, the harvest came from a Twitter database. How that data was obtained we do not know. Either social engineering or bribery. Definitely no relation to sim swapping. That is a meme. Sorry, Brian.
I second that.
The com Joe is from are full of teenage sim swappers with 6 figures. I can feel one big indictment coming soon to wipe these idiots.
Twitter got hacked as soon as I tweeted that COVID is a biowar
These activities to an outsider (no twitter or bitcoin participation), are like watching children fight for the toy the others have and peer recognition, while missing out on the best things in life. I hope they figure it out before life passes them by.