Communications at the U.S. Treasury and Commerce Departments were reportedly compromised by a supply chain attack on SolarWinds, a security vendor that helps the federal government and a range of Fortune 500 companies monitor the health of their IT networks. Given the breadth of the company’s customer base, experts say the incident may be just the first of many such disclosures.
Some of SolarWinds’ customers. Source: solarwinds.com
According to a Reuters story, hackers believed to be working for Russia have been monitoring internal email traffic at the U.S. Treasury and Commerce departments. Reuters reports the attackers were able to surreptitiously tamper with updates released by SolarWinds for its Orion platform, a suite of network management tools.
In a security advisory, Austin, Texas based SolarWinds acknowledged its systems “experienced a highly sophisticated, manual supply chain attack on SolarWinds Orion Platform software builds for versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020.”
In response to the intrusions at Treasury and Commerce, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) took the unusual step of issuing an emergency directive ordering all federal agencies to immediately disconnect the affected Orion products from their networks.
“Treat all hosts monitored by the SolarWinds Orion monitoring software as compromised by threat actors and assume that further persistence mechanisms have been deployed,” CISA advised.
A blog post by Microsoft says the attackers were able to add malicious code to software updates provided by SolarWinds for Orion users. “This results in the attacker gaining a foothold in the network, which the attacker can use to gain elevated credentials,” Microsoft wrote.
From there, the attackers would be able to forge single sign-on tokens that impersonate any of the organization’s existing users and accounts, including highly privileged accounts on the network.
“Using highly privileged accounts acquired through the technique above or other means, attackers may add their own credentials to existing application service principals, enabling them to call APIs with the permission assigned to that application,” Microsoft explained.
Malicious code added to an Orion software update may have gone undetected by antivirus software and other security tools on host systems thanks in part to guidance from SolarWinds itself. In this support advisory, SolarWinds says its products may not work properly unless their file directories are exempted from antivirus scans and group policy object restrictions.
The Reuters story quotes several anonymous sources saying the intrusions at the Commerce and Treasury departments could be just the tip of the iceberg. That seems like a fair bet.
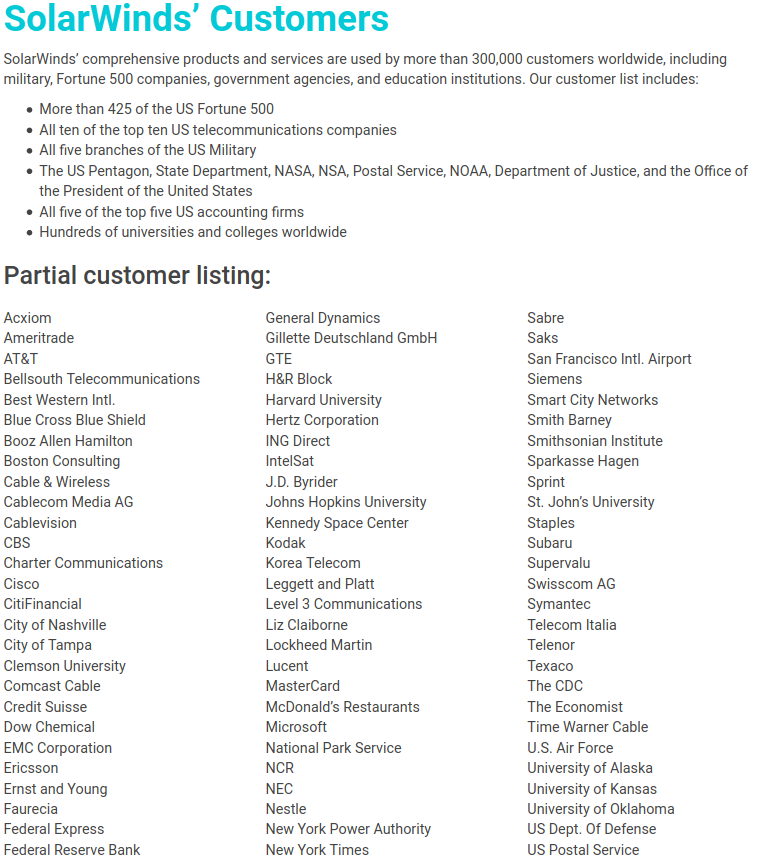
SolarWinds says it has over 300,000 customers including:
-more than 425 of the U.S. Fortune 500
-all ten of the top ten US telecommunications companies
-all five branches of the U.S. military
-all five of the top five U.S. accounting firms
-the Pentagon
-the State Department
-the National Security Agency
-the Department of Justice
-The White House.
It’s unclear how many of the customers listed on SolarWinds’ website are users of the affected Orion products. But Reuters reports the supply chain attack on SolarWinds is connected to a broad campaign that also involved the recently disclosed hack at FireEye, wherein hackers gained access to a slew of proprietary tools the company uses to help customers find security weaknesses in their computers and networks.
The compromises at the U.S. federal agencies are thought to date back to earlier this summer, and are being blamed on hackers working for the Russian government.
In its own advisory, FireEye said multiple updates poisoned with a malicious backdoor program were digitally signed with a SolarWinds certificate from March through May 2020, and posted to the SolarWindws update website.
FireEye posits the impact of the hack on SolarWinds is widespread, affecting public and private organizations around the world.
“The victims have included government, consulting, technology, telecom and extractive entities in North America, Europe, Asia and the Middle East,” the company’s analysts wrote. “We anticipate there are additional victims in other countries and verticals.”
Update, 8:30 p.m. ET: An earlier version of this story incorrectly stated that FireEye attributed the SolarWinds attack to APT29. That information has been removed from the story.




https://www.solarwinds[.]com/company/customers
Doesn’t work anymore. Hmm. Do you have a full list somewhere?
https://web.archive.org/web/20201214065921/https://www.solarwinds.com/company/customers
Version 2020.2.1 was released in August 2020. How is that “in scope” if the vulnerable releases were between March and June 2020?
Any evidence for the hacker identification?
I’d guess it all will come out in due time, but do you know too many nation-states capable of pulling off such a sophisticated and coordinated attack?
Any of the 5-eyes, Germany, France, India, Israel to name 8 off-hand.
Okay, but those are allies, not adversaries. It it fathomable an “inside operation” could happen? Sure. Is it probable? Likely not. Russia has great skill, plus reason to use it, probably only more so with the changing of administrations.
Of course it could have been an “allie”, American government has been doing it to “allies” since before end of WW2, why shouldn’t “allies” return the favour ?
Plenty with the skills to commit at this kind of level also have the skills and wish to obscure themselves.
This has always been my argument against any form of centralised security, from basic password sites up to this kind of level, target has to be good and lucky 100% of the time, attackers just nerd luck on their side once, and it’s game over.
“Chaos and confusion reign”
Could’ve been the NSA for all we know. Good points, there’s too much racist russia-hate out there.
I don’t want to sound like a “Q” conspiracy theorist, but, Dominion (The election ballot processing company), is a SolarWinds customer. Certainly the Three Letter Agency (TLA’s) of the US Government have the ability to pull this off and while I hope that’s not the case, they can’t be ruled out at this time.
The other three letter agencies were also customers and potentially victims.
Dominion is a company that has many systems. Whether or not their stand alone voting systems had SolarWinds has not even been claimed. The voting machines may run Windows, but are owned and operated by individual states and counties… so don’t assume they run the full suite of whatever Dominion runs on their corporate network.
Dominion voting machines required a centralized windows server install that very could have utilized Orion. Regardless I never trust a system that doesn’t generate a voting receipt with a hash number and a corresponding public list.
Yes, most voting machines (not just Dominion but Hart, ES&S and Deibolds) use Windows. But there is no indication of SolarWinds Orion.
Think about it… these systems/networks are purchased from the Voting Systems manufacturer… but they are owned and operated by State and County governments with limited budgets. They don’t run IT operations centers to remotely monitor these systems. Perhaps they should but its a double edged sword. They get more visibility into all the endpoints for security and reliability, but then more connectivity over the internet which is necessary for real-time remote monitoring.
Thousands of separate municipalities all conducting their own elections, is simultaneously a weakness and a strength. A compromise of a central management system like Solarwinds Orion, is not likely to be used for such a decentralized patchwork of election voting systems.
I too share distrust of Direct Recording Electronic Systems (DREs) that do not produce a paper receipt for the voter to verify. But those machines are nearly extinct with the vast majority either using Ballot Marking Devices (BMDs) that actually just mark paper ballots for the voter to verify and submit, or just simply use paper ballots from the start. That is why hand or machine recounts and audits in all the disputed areas are looking at paper.
https://verifiedvoting.org/verifier
Not sure what you mean by hash and public list. Any examples in the US you can point to?
Remember, the principle of secret ballots are critical… for good reason, you don’t want governments going back to know which individuals voted for which candidate. Recipe for tyranny.
So hopefully that’s not the public list you are talking about.
Then you should trust Dominion because their systems do always generate a paper ballots for recounts. In fact, because of that, it doesn’t matter if they were hacked or not.
I’m not an expert, and I would like to think there was no foul play, but the fact that the voting machine generates a paper ballot for recount doesn’t seem to rule anything out, since the ballot is generated by the machine itself. In that scenario, wouldn’t a compromised machine be able to print out a compromised ballot?
No.
Most machines in question have the original paper ballots marked with ink from the voter’s own hands. The fast tabulators scan them. Then the audits and recounts confirm using the original paper.
Other machines just mark a paper ballot in front of the voter. Yes, the voter uses a touchscreen, but gets an Instant paper copy they can verify and can be used for audits.
Very few places use electronic voting machines without Voter Verified Paper Audit Trail (VVPAT) printers that allow the voter to confirm their selections on an independent paper record.
Texas and other red states have these machines though.
Look at this map that shows all the machines used, for each county, over several elections. 2020 was indeed the most secured, because more places are using more paper than ever before.
https://verifiedvoting.org/verifier/#mode/navigate/map/ppEquip/mapType/normal/year/2020
The United Nations said Monday that it will contact the United States about reports that the National Security Agency hacked its internal communications, and the world body emphasized that international treaties protect its offices and all diplomatic missions from interference, spying and eavesdropping.
U.N. spokesman Farhan Haq said Monday that the United Nations will “reach out” to U.S. officials about the reports of eavesdropping, as it has in the past when such allegations have been raised.
Haq added that “the inviolability of diplomatic missions, including the United Nations and other international organizations, whose functions are protected by the relevant international conventions like the Vienna Convention, has been well-established international law.”
The German magazine Der Spiegel reported Sunday that documents it obtained from American leaker Edward Snowden show the NSA secretly monitored the U.N.’s internal video conferencing system by decrypting it last year.
Allies???
https://www.usatoday.com/story/news/world/2013/08/26/united-nations-nsa-hacking/2703835/
Der Spiegel also reported that the NSA installed bugs in the European Union’s office building in Washington and infiltrated the EU’s computer network.
The 1961 Vienna Convention regulates diplomatic issues and status among nations and international organizations. Among other things, it says a host country cannot search diplomatic premises or seize its documents or property. It also says the host government must permit and protect free communication between the diplomats of the mission and their home country.
Lol, I’m German and believe me Germany clidnt even hack an ATM, hacking isn’t a stronghold of Germans intelligence services
“Im German and believe me” – welp, I’m sold.
Why do they hire reverse engineers then?
I’m gonna go with someone wants to make sure that we keep on hating Russia as the new administration takes over.
It is simple it is part of the Russia and Trump agenda. Why do you think they invited Trump to move to Russia? Doesn’t Trump always strike back 10 times as hard and now he hates all of America from top to bottom and trying to provoke war.
I blame Trump. He is the number one suspect with motive!
I blame the “big guy”. He clearly isn’t getting the ten percent cut and why else would they pay a crackhead billions of dollars?
Biden is clearly the one with the motive provided he can remember what day it happens to be.
I was insane once too, but I got better. See? Good luck.
-Mitt
That has to be one of the most ridiculous comments I’ve seen. Wow, bringing US politics into cybersecurity…really?
“Bringing US politics into cyber security.”
When a foreign nation attacks, politics are always involved.
When a foreign nations doesn’t attack, politics are always involved.
So far, I’ve seen 2 articles tying UNC2452 (FireEye’s tracking designation) to Cozy Bear, but no one is giving the reference to that information. I’ve looked through the FireEye releases, and haven’t found any written indication of that attribution or connection. Could you provide a source please? Thanks!
https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
Thank you for the reporting
Oof. I’ve had the pleasure (?) of working with the Orion product to get logs into Splunk.
This is going to be a cluster across the Federal Govt. They all use it. Whichever group got in over the last few months likely has some very sensitive data
I guess placing blind trust in software used in the organization isn’t such a good idea?
Managed Service Provider.
Saves you money until this crap happens.
That statement has nothing to do with the topic at-hand. Orion is used by many internal IT departments; I wouldn’t even consider it an MSP focused tool.
Sounds like someone is sore about being replaced by an MSP better than they were. Were you saying the same things about Kaspersky or EVERY other system out there experiencing vulnerabilities?
The best antivirus is between your ears. So yeah, I’m not a fan of Kaspersky. Ask the NSA how they like it.
The only outside service I allow is RBLs. I live in the real world and email would be unmanageable without them.
I am curious about the verdict on Kaspersky?
PCMag says “Kaspersky Anti-Virus takes perfect or near-perfect scores from all the independent testing labs, and it aced our hands-on ransomware protection test. It remains an antivirus Editors’ Choice…Editors’ Note: We are aware of the allegations of Kaspersky Labs’ inappropriate ties to the Russian government. Until we see some actual proof of these allegations, we will treat them as unproven, and continue to recommend Kaspersky’s security products as long as their performance continues to merit our endorsement.” I noticed Kaspersky seemed to alert on geopolitical penetrations leading American AV products did not detect.
Rumors flying about Dominion voting systems use of SolarWinds. Any comments? SolarWinds advertised on the bottom of their log-in screen.
https://dvsfileshare.dominionvoting.com/Web%20Client/Mobile/MLogin.htm
Oh my goodness. Still another loony tune person who is looking for a way to say Trump won the election. Please check yourself into a facility.
This is a legitimate and bad hack. It was by the Russians. Why would the Russians want trump to lose?
Becuase the Russians have more ties to the Bidens than the Trumps. Ask Hunter about it.
That’s 3/4 to 5/6 horsecrap. Ukraine != Russia.
Donald Trump literally hung out with and traded real estate with Russian oligarchs in furtherance of his money laundering / frauds, and did everything Putin asked him in order to secure the good graces of autocracy. Whatever Hunter Biden did or didn’t do, DJTJ met with Russian spies IN THE OVAL OFFICE, and Donald Trump had the 3 top intel chiefs OF RUSSIA in the Oval also – one of them even leaking photographs that Trump tried to keep secret from the US public – to Russian state media, as a demonstration of control.
Trump is bought and in fact 1/2 Billion + in hock to Russia/Middle East non-Democracies.
Trump will die in prison for multiple frauds and conspiracies.
He’s already unable to run a charity legally due to fraud.
Hunter, like him or hate him, is not nearly anywhere close to as dirty or friendly with Russian autocrats as the Trump traitors.
Try again someday, after you’ve read the first thing about it.
Ahh do some research. He did win. Forensic audits prove the machines were fixed.. they had a 68% error rate. .0008% is the allowed limit. Get informed
Link to empirical evidence pls.
I believe this is the leaked report he’s referring to:
Allied Security Operations Group
Antrim Michigan Forensics Report REVISED PRELIMINARY SUMMARY, v2
Report Date 12/13/2020
https://www.scribd.com/document/488107901/Antrim-Michigan-Forensics-Report-121320-v2-REDACTED
This forensics report was done by ASOC which is run by a hyperpartisan former Republican Candidate, who has submitted previous signed affidavits full of mistakes such as Minnesota Counties he claimed were in Michigan.
We have to wait for “independent” forensics investigators to examine the machines.
The speculation that Solarwinds is being used by Dominion ‘voting machines’ is premature, and there is a history of wild speculation based on bad analytical methodology. For instance, finding a logo on some random website that says dominion. This is similar to previous speculation from ASOC that Edison Research has a server in Iran, because of a similar subdomain/hostname in an open source search for DNS records.
You must be citing Foxnews forensic audits. lol. A real forensic audit on a random sample of Dominion machines in Georgia found no signs of cyber attacks or election hacking. They also don’t support “fractional” or weighted voting, and it is technologically impossible to see votes being counted in real-time and/or to ‘flip’ them.
That’s Serv-U, not Orion.
Excellent; thank you Chris. Appreciate your contribution versus simply dismissing the topic with hate speech.
That’s exactly why I asked the question. I made no statement that potential use had any impact on the election, much less a specific outcome.
I merely noted it was in use and rumors are flying.
It would behoove us, and appropriate parties, to get ahead of the rumors however, before they take on a life of their own.
We shouldn’t summarily dismiss this connection. Surely any rational person can recognize how valuable a target they would be?
Dominion Voting Systems does appear to be using a different product from SolarWinds called Serv-U. We have no idea if they were also using other products. And, SolarWinds was obviously compromised, so all of their software should be suspect.
I’m not saying we jump to the same conclusions as right wing conspiracy groups, but for all our sake, I hope it’s being exhaustively investigated.
Agreed. And like any other sensitive forensic investigation, we should only accept evidence that was properly handled and done by an “independent” cybersecurity firm.
As it stands now, ASOC is not independent and is generating politically motivated reports because ASOC is run by Russell James Ramsland Jr., a cybersecurity analyst and former congressional candidate from Dallas, Texas.
Like most things in our field, independence from politics is crucial.
https://www.solarwinds.com/securityadvisory
SolarWinds products believed to be NOT AFFECTED by this security vulnerability:
…
Serv-U FTP Server
Serv-U Gateway
Serv-U MFT Server
…
I appreciate healthy skepticism until the dust settles… but jumping to assumptions can be just as bad.
This was an attack on confidentiality, not integrity.
I’ve made the connection. I’m sincerely hoping it’s a coincidence, because if it’s not, the national security implications are enormous.
The removed the footer from their production website… Luckily the internet is recorded.
https://web.archive.org/web/20201214093452/http://dvsfileshare.dominionvoting.com/Web%20Client/Mobile/MLogin.htm
Wait.. the link worked yesterday and I saw the Dominion Voting logo. Now the CEO is testifying today and its no longer there..
Conspiracy theory
Bitcoin is open 24/7 and never hacked buy bitcoin 300k is cheap for bitcoin its cheap 20k is nothing for btc
I guess if you shill it enough to get mainstream fintech onboard then perhaps it can gain wings.
“The theft of $69 million worth of bitcoins from a Hong Kong-based exchange highlights the continuing challenges around keeping large quantities of digital currency out of the reach of hackers.”
https://www.bankinfosecurity.(com)/bitcoin-hack-highlights-cryptocurrency-challenges-a-9305
Hackers are now proving that nothing in the digital world is safe.
A service was hacked, not Bitcoin protocol.
Who cares, if they can steal the money… it doesn’t matter.
That’s like saying there is an unpickable lock on a plastic safe.
Another Sandworm exploit? Read the book of that title, by Andy Greenberg.
Reuters is indicating the Russians: “but three of the people familiar with the investigation said Russia is currently believed to be responsible for the attack” -https://www.reuters.com/article/BigStory12/idUSKBN28N0PG
Current Brian: “According to Reuters…”, “In a Microsoft blog…”
Previous Brian: “This reporter found the culprits to be from the country of _____ and not from Russia.” Their names are listed below, along with their address, pet names, and passwords to their adult sites.”
I miss Previous Brian. I wonder what changed.
Patience, grasshopper. Patience.
I hardly ever pay much attention to initial breach notifications, but I think this one is going to be really bad just based on how many organizations EVERYWHERE uses SolorWinds.
SolarWinds CEO Kevin Thompson just unloaded 700K shares of SWI on 16 November. Coincidence?
SO – regarding those Files and Directory Exclusions.
uhhhh.
I know of a group who updated following the CISA alert and was told they were not at risk – over the weekend.
This would make me wonder about that…
Doesn’t seem too sophisticated to me https://savebreach.com/solarwinds-credentials-exposure-led-to-us-government-fireye-breach/
Why blame russia ?russia is not old country the oldest leaders are behind new countries usa neither russia old.
Switzerland city of london germany old
And russia there is nothing only vodka russians been plundered stolen the natural reseources so clearly russia is not running nothing but just proxy
Sorry, but if this is certain to be Russia or Russian-based actors, this is an act of war and should be treated as such and responded to as such.
Indeed, this is serious enough to warrant a heavy response but I wouldn’t start a war with an economically poor nation that has 10,000 nukes over a breach like this.
What I would do is finally invest in cyber security as much as, if not more than, I do in building dumb bombs and fighter jets that just sit around in hangers.
It’s minor, but: Smithsonian Institute? It’s *Institution*, SolarWinds.
how do we know only those versions were compromised?
We dont know. I persistent APT would have infected as many as they could without triggering suspicion. Thats why SANS has stated to assume any installation has been compromised.
It depends on the source code repositories and management.
If the breach could only affect versions in current development, but not archives which may have additional integrity checks if someone were to attempt to alter it.
It may be the way certain signing certificates were compromised, but not others.
It would be a very different attack to go back and retroactively compromise previous versions.
So its totally possible to have reasonable certainty of specific versions to be affected only.
Well it’s bad when companies entrust companies like this to assume a over watch position for their networks thinking they must be good because they have a ton of well known clients. Then you find out they are not so good at the one thing you entrust them to do.
Volunteer to examine and review the code. Clearly you can find the flaws and issues before hackers do, yes?
Sometimes that is the only real benefit of buying a product used by many other high visibility clients…. that when a major breach happens, they will be more likely to spot it.
If this was a minor company, would you be safer? Or only “feel” safer? You may not know about the breach until 2024.
It is not clear why only the newer versions are effected? Is this a watering hole attack on vulnerable update servers in the cloud? So if someone has older. So if anyone has older version of Orion then they don’t have to do anything? Solarwind is not clear about it.
What was the channel the malware on infected Orion hosts used? Presumably https and maybe not inspected by network AMD?
They emulated a proprietary and utterly useless (and most likely wildly insecure) protocol developed by SolarWinds.
…assume that if you use any version of solar winds you’re compromised…
my question is, how did they get hold of the signing keys? which moron at solar winds had the signing keys readily accessible on the network?
and for a patch to get pushed up to release, how many other systems were compromised? in lots of places, you can’t even submit a request to merge code into the main trunk until layers & layers of compliance requirements have been met. so many safeguards had to be bypassed in order for this to happen. it’s mind-boggling.
These attacks are indeed complex involving many steps of compromise. This is what APTs do. This is why we can be somewhat certain of a nation-state attacker.
How does a hack in monitoring software lead to the ability to impersonate SSO tokens? surely there must be an another exploit thats not be discussed in the identity layer?
Maybe referring to Kerberoasting using a privileged account running the SolarWinds agent.
Auto-update is, on balance, Evil.
Every time you update software, you create the possibility of introducing new bugs and/or malware. Meaning you fully trust every actor & every potential attack vector involved in the entire tool chain (iffy & constantly changing personnel & potentially compromised systems) at every step upstream. Generally all of which is invisible to the downstream consumer.
Isn’t the devil you know better than the devil of opaque software you just installed and don’t know?
Basically sovereignty is abdicated via lazy ‘pass the responsibility thinking’ (authority != responsibility). I.e. your highly paid CIO is just passing the buck to their software providers while collecting gigantic paychecks for basically nothing. Skimming changelogs is laughably inadequate.
The only solutions are 100% closed, encrypted, trusted black boxes or 100% open & auditable & peer-review validated systems. I prefer the latter.
Sadly, I’ve never been listened to even once.
There is an old saying: If nothing every changes, there is no reason to make changes.
Unfortunately, it isn’t possible to remain static forever. The universe changes whether you do anything or not. The threats change, the standards and protocols change, the requirements change, etc, etc. The standalone black box that cannot be updated will eventually become useless and be thrown in the trash, requiring you to start over validating a new box.
why? why would the ancient black box need the latest and greatest new ™ update? isn’t the tcp/ip still working?
what absolutely necessary ™ piece of software solarwinds provides anyway? network load gauge? come on…
so and so guy is right. it can be done right, but then it eliminates nepotism, or plain stupidism…..
(“you need so and so here because ” and then you sell it to the government…us (hi)story is full of such scams, you may remember one from 2007/2008)
Agreed, remaining static forever isn’t really a good long-term answer. I was just trying to point out that only two reasonable binary options are available, ‘walled-garden’ 100% vendor-trust with all that implies (lock-in, etc) or 100% open, which currently isn’t exactly perfect either. Any other mix is even less optimal and rapidly arrives at the very sub-optimal mess that we live in now.
Fundamentally currently security is all about reducing or ideally eliminating attack-surfaces & chains-of-trust. Personally, I don’t really trust any commercial business that puts their investors (profits) first.
Generally speaking, the only open system I’m aware of that’s proven itself as trustworthy is consensus (beyond just protocols) aka. peer-reviewed open-source. But most software vendors will never do that because they lose their proprietary advantage.
It’s a serous conundrum that left unresolved will just perpetuate the ever deepening mess that typifies what we call the current state of the art.
I think to solve the root cause of security problems will require solving the open-source development funding problem first. Example would be OSS bug-bounties, paid contribution systems, etc.
“only two reasonable binary options are available”
Not really something that happens in the real world.
When a major Supply-Chain compromise happens:
It is tempting to say automated processes for updating is bad, and organizations should manually assess each update for integrity or just don’t update.
When a Zero-Day compromise happens:
Update your system as soon as possible and set up automatic updates. Don’t wait until the attack makes the news.
Can’t have it both ways.
Solarwinds updated their security advisory. Now they’re saying version 2020.2.1 was NOT vulnerable.
https://www.solarwinds.com/securityadvisory
Time to make more popcorn #2020
Best comment ever.
Alot of InfoSec/Network Security is moving into DEVSECOPS. Penetration security is changing. Multi-entry from different direction.
Graphing out to the command and control avsvmcloud.c, domains listed in Snort; but more domains than listed in Snort.
http://www.virustotal.com/graph/embed/g6aedd13040ce49c9846613aede04437a9ad22b0133f6484dad28b5a6579657f1?hideButton=1#
In addition to the Snort rule domain names, the graph includes:
mx3. and mx1 .emailowl[.]com Communicating with trojan & backdoor.
Avaddon ransomware
217.8.117[.]63 malware-trojan-ransomware
123.45.67[.]89 backdoor & communicating with trojan
What’s kind of crazy is that we all think about the need to stay updated for security reasons. Here is a case where being up to date didn’t pay off in a bad way. We are approaching a point where large providers like SolarWinds will have to pass regular external audits of their policies and procedures before a contract can be signed. I really would like to know what their “supply chain” consists of and what controls were in place to prevent what happened. Either SolarWinds was penetrated or somebody they contracted out some critical part of the supply chain was.
When a major Supply-Chain compromise happens:
Don’t have automated processes for updating. Organizations should manually assess each update for integrity or just don’t update.
When a Zero-Day compromise happens:
Update your system as soon as possible and set up automatic updates. Don’t wait until the attack makes the news.
Can’t have it both ways.
Which do you think is more common? 0-days or supply-chain?
“pass regular external audits”
Yes, however, this is often annually.
APTs with supply chain infiltration can often sit quietly and still pass most external audits.
Lesson learned here banks can hacked digital money can be hacked i trust paper money and hard gold hard assets !
Its time to turn of the internet and pc.
Only fool will trust internet
Please shut down big media/ social media etc. 1st. Robin Hood. 2nd. correction 3rd. fair/just systems. ” All walls eventually fall “