Ne’er-do-wells leaked personal data — including phone numbers — for some 553 million Facebook users this week. Facebook says the data was collected before 2020 when it changed things to prevent such information from being scraped from profiles. To my mind, this just reinforces the need to remove mobile phone numbers from all of your online accounts wherever feasible. Meanwhile, if you’re a Facebook product user and want to learn if your data was leaked, there are easy ways to find out.
The HaveIBeenPwned project, which collects and analyzes hundreds of database dumps containing information about billions of leaked accounts, has incorporated the data into his service. Facebook users can enter the mobile number (in international format) associated with their account and see if those digits were exposed in the new data dump (HIBP doesn’t show you any data, just gives you a yes/no on whether your data shows up). 
The phone number associated with my late Facebook account (which I deleted in Jan. 2020) was not in HaveIBeenPwned, but then again Facebook claims to have more than 2.7 billion active monthly users.
It appears much of this database has been kicking around the cybercrime underground in one form or another since last summer at least. According to a Jan. 14, 2021 Twitter post from Under the Breach’s Alon Gal, the 533 million Facebook accounts database was first put up for sale back in June 2020, offering Facebook profile data from 100 countries, including name, mobile number, gender, occupation, city, country, and marital status.
Under The Breach also said back in January that someone had created a Telegram bot allowing users to query the database for a low fee, and enabling people to find the phone numbers linked to a large number of Facebook accounts.
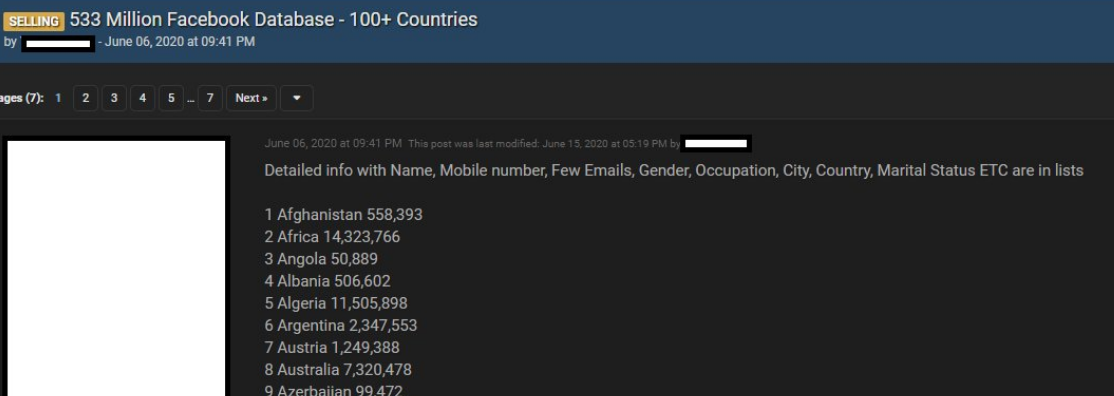
A cybercrime forum ad from June 2020 selling a database of 533 Million Facebook users. Image: @UnderTheBreach
Many people may not consider their mobile phone number to be private information, but there is a world of misery that bad guys, stalkers and creeps can visit on your life just by knowing your mobile number. Sure they could call you and harass you that way, but more likely they will see how many of your other accounts — at major email providers and social networking sites like Facebook, Twitter, Instagram, e.g. — rely on that number for password resets.
From there, the target is primed for a SIM-swapping attack, where thieves trick or bribe employees at mobile phone stores into transferring ownership of the target’s phone number to a mobile device controlled by the attackers. From there, the bad guys can reset the password of any account to which that mobile number is tied, and of course intercept any one-time tokens sent to that number for the purposes of multi-factor authentication.
Or the attackers take advantage of some other privacy and security wrinkle in the way SMS text messages are handled. Last month, a security researcher showed how easy it was to abuse services aimed at helping celebrities manage their social media profiles to intercept SMS messages for any mobile user. That weakness has supposedly been patched for all the major wireless carriers now, but it really makes you question the ongoing sanity of relying on the Internet equivalent of postcards (SMS) to securely handle quite sensitive information.
My advice has long been to remove phone numbers from your online accounts wherever you can, and avoid selecting SMS or phone calls for second factor or one-time codes. Phone numbers were never designed to be identity documents, but that’s effectively what they’ve become. It’s time we stopped letting everyone treat them that way.
Any online accounts that you value should be secured with a unique and strong password, as well as the most robust form of multi-factor authentication available. Usually, this is a mobile app like Authy or Google Authenticator that generates a one-time code. Some sites like Twitter and Facebook now support even more robust options — such as physical security keys.
Removing your phone number may be even more important for any email accounts you may have. Sign up with any service online, and it will almost certainly require you to supply an email address. In nearly all cases, the person who is in control of that address can reset the password of any associated services or accounts– merely by requesting a password reset email.
Unfortunately, many email providers still let users reset their account passwords by having a link sent via text to the phone number on file for the account. So remove the phone number as a backup for your email account, and ensure a more robust second factor is selected for all available account recovery options.
Here’s the thing: Most online services require users to supply a mobile phone number when setting up the account, but do not require the number to remain associated with the account after it is established. I advise readers to remove their phone numbers from accounts wherever possible, and to take advantage of a mobile app to generate any one-time codes for multifactor authentication.
Why did KrebsOnSecurity delete its Facebook account early last year? Sure, it might have had something to do with the incessant stream of breaches, leaks and privacy betrayals by Facebook over the years. But what really bothered me were the number of people who felt comfortable sharing extraordinarily sensitive information with me on things like Facebook Messenger, all the while expecting that I can vouch for the privacy and security of that message just by virtue of my presence on the platform.
In case readers want to get in touch for any reason, my email here is krebsonsecurity at gmail dot com, or krebsonsecurity at protonmail.com. I also respond at Krebswickr on the encrypted messaging platform Wickr.




I wonder if I published a google voice number that was forwarded to my cell. The hackers would not know my cell. But anyone who wanted to call me still could. What do you think of that Brian?
I use a Google voice account for SMS 2FA and accounts that need a phone number; the Google account has a Titan USB key to secure access.
I use a GV account protected with their authenticator but had a curious experience recently that I thought I’d share. I called up a financial institution to request a wire out and, after asking me a bunch of additional authentication questions, they confirmed the instructions. Since the wire did not go out at the time they promised, I called back and they said it had gone to their research department and i would have to await their findings. I escalated and eventually learned it had triggered a fraud alert.
I found out later that they can tell when a number is a GV (or other VoIP) number and they do further verification by calling a number that they pull from a database that gives them confidence belongs to the account holder. In my case, it was my cell phone which is configured to only ring when the call is from a number in the Contacts list, so I was not able to answer the call. This mobile number is not on their account records and I did see a missed call from the number their Fraud department uses for outgoing calls.
Long story short, after the matter was eventually sorted out, they advised me to call from a landline or a mobile number when moving money!
It isn’t surprising that yours wasn’t in there. Only 32 million accounts from the USA were in this dump out of roughly 190 million total. Looking at accounts as proportion of country populations, it looks like whoever stole this data is probably Egyptian.
I think Brian used to advise doing exactly that.
Thanks for laying out the approach to removing phone numbers from online accounts.
Now I have the problem of picking an authenticator. That task has been beyond me for over a year. I gotta buckle down, think it through, write a plan, and carry it out, step by step.
Not easy for a codger working on qualifying to become a geezer.
Use the authy app, or if you’re really serious, a yubikey.
Yes. Yubikey is preferred. It’s an external physical device. And Yubico Authenticator actually stores the secrets on the Yubikey rather than the phone.
If you don’t want to carry a separate device, using another app like Authy is basically having OTP codes in another app’s storage, but on the same device. With KeePass, you get the same segregation if you just have a separate database file on the same device.
There is nothing proprietary or special about Google Authenticator.
For Desktop, I recommend KeePass. In addition to the common storage, management and generation of strong static passwords…. an entry can also store a TOTP seed/secret, and produce the same One-time Pad (OTP) code that you would get from Google Authenticator.
Yubikey would be best, but many sites/services online don’t do FIDO2/U2F authentication. If you’re lucky, they’ll do TOTP.
Of course, for good layered security… you can use Yubikey as a 2nd factor to encrypt your KeePass database on both desktop and mobile. Yubico Authenticator app on Android can store TOTP codes too.
I don’t love keeping 2FA codes in the same location as passwords, for obvious reasons. Better to run a separate app like authy or use a yubikey.
Concerns about security on Android, lol? How cute.
None of them are perfect.
Google Authenticator favors paranoia, which makes certain things hard. (These lead to Usability/Availability issues)
LastPass Authenticator is probably fine. But, it appears to be a bit below Google Authenticator and falls mostly into the paranoid bucket.
Cisco Duo is probably fine, but, basically Authy or Google Authenticator end up looking like better choices depending on requirements.
Twilio Authy favors accessibility which means an increased attack surface. (Also, they have a number of UX bugs.)
Microsoft Authenticator has to deal w/ the split personality between their two services and some custom stuff. Roughly, it suffers from embrace-extend. I actively avoid this product.
If you’re Paranoid and trust Google, then that’s probably the right choice. If you’re paranoid and don’t trust Google, LastPass may be the right choice. If you want to use multiple devices, Authy is probably the right choice.
No matter what you use, make sure that the account name you use is distinct and not reliant on the icon. Sometimes an icon won’t persist, and if you have 3+ things, you’re going to be in real trouble when you try to use your device to authenticate. Don’t assume you will only ever have one Google account, or one Twitter account. And certainly don’t assume you’ll only have one Microsoft account (and keep in mind that M365 and Live account spaces are different, and that each company might run their own Microsoft directory which is keyed to your email address but which would default to the Microsoft icon…).
If you can get Hardware keys, Google/Yubikey are probably the way to go. Beware, your keys will eventually die. I’ve had both RSA Keys (old fashioned, they were also voided [3]) and Google keys die [4]. Make sure you have provisions for this. And make sure those provisions are secure (and tested). As with everything else, the reset cases often end up being the easier attack vector for attackers, and since you probably aren’t testing them, and only need them in a crunch, you’re likely to be in trouble.
And of course, be *very* careful about enabling 2FA. I suggest using a second session to enable. And then a third independent session to validate that you can log in with 2FA. Because if you’re not careful, the act of turning on 2FA can easily lock you out. And, ideally it’s hard for anyone (especially an attacker, but also you) to regain access to an account w/ 2FA enabled.
[1] https://www.pcworld.com/article/3225913/what-is-two-factor-authentication-and-which-2fa-apps-are-best.html
[2] https://www.nytimes.com/wirecutter/reviews/best-two-factor-authentication-app/
[3] https://krebsonsecurity.com/2011/03/domains-used-in-rsa-attack-taunted-u-s/
[4] https://www.engadget.com/2019-05-15-google-recalls-some-titan-bluetooth-security-keys.html
@Brian: I like the UI refresh. It feels modern and appears to be mobile friendly.
n.b. I failed to actually include placements for the [1] and [2] citations, people can imagine that they belong at the end of the first sentence.
Also, I’m not certain, but I think the blog is adding a `-` between `[x]` and the url — I don’t believe I included that myself.
Have I been Pawned website has been around for a long time. It deserves a better recognition that it currently gets (which is none, I think).
Thanks to you @Brian and team (and HaveIbeenpwnd.com)for keeping the community informed and advised.
You’re too pessimistic. Have I Been Pwned has a huge recognition. In fact, it has agreements with a lot of governments all over the world, whose cybersecurity authorities officially recommend it. Troy Hunt’s efforts have really come to fruition.
I really love that the site is mobile-friendpy now. So much easier to read 🙂
Oddly enough, I got my SIM card disabled a few days ago when trying to set up a SIM PIN and then, at a Verizon store, an employee insisted that they didn’t advise doing that due to frequent issues like that and that it wasn’t even needed since they required an ID to swap out a SIM card. Great.
SIM Swap protections are still only as good as the compliance mechanism internal to the carrier’s systems.
Many places “require” a PIN or a photo ID… but of course, a supervisor can bypass this. So, instead of the security protecting your phone number from a SIM Swap relying on the teenager behind the counter, now it relies on the 23 year old in the back room.
Bribing an employee has gotten a bit harder, but still an easy path for a SIM Swapper.
Thanks Brian for all you do!! I have looked into removing my cell number from online accounts, based on your emails, however it appears many banks etc. don’t provide an option for 2-factor auth. other than sending an SMS message to one’s cell. Am I missing something? Is there another way to get 2-factor auth. on an account, such as a bank website, if the provider doesn’t note any particular auth. apps being available but just prompts for cell number when you are setting up 2-factor? thx
I have looked into removing my cell number from online accounts, based on your emails, however it appears many banks etc. don’t provide an option for 2-factor auth. other than sending an SMS message to one’s cell. Am I missing something? Is there another way to get 2-factor auth. on an account, such as a bank website, if the provider doesn’t note any particular auth. apps being available but just prompts for cell number when you are setting up 2-factor? thx
Nope, nothing you can do but complain to them.
Thx – that’s what I thought!
Look to see if they’re here then send complain to them about it.
https://2fa.directory/#banking
My bank does 2FA two ways; you’re asked which you’d like.
1) send 2nd factor to your cell phone
2) send 2nd factor to your email
I don’t have a cell phone, so I always specify the email option.
And someone trying to steal your account… Will choose whatever’s easiest for them.
My bank ignored my suggestion to use security keys. Can I use the Google Authenticator on my desktop without the bank needing to install any s/w?
There is nothing proprietary or special about Google Authenticator.
For Desktop, I recommend KeePass. In addition to the common storage, management and generation of strong static passwords…. an entry can also store a TOTP seed/secret, and produce the same One-time Pad (OTP) code that you would get from Google Authenticator.
I think you mean One-Time Password (OTP). Google Authenticator doesn’t use One-Time Pad.
We read your recommendation the first time dawg. Then the second. Now the 3rd. One is plenty.
These are replies to specific questions.
The new format is easier to read on mobile, but harder to follow individual comment reply threads.
Actually either way you’re saying the same thing multiple times. Try to take advice FWIW.
Since you’re so vociferous about repeating your own. It’s good once, maybe twice, sure.
Are you suggesting most people reading the comments, read ALL the comments?
That’s not how comments here are structured.
People are free to ask questions by starting a new thread, and without having to read everything first. And since everyone has a different experience, they ask different questions. Sometimes different problems can have common solutions.
And since we’re all free to comment or not comment… and free to read or not read… you are don’t have to read anything you deem to be repetitive.
“That’s not how comments here are structured.” – Uh, yeah they are.
I read the comments one after another, I don’t do anything special to do so.
Someone offers you a light suggestion of not repeating your own suggestion 4 times in a row verbatim in the same thread, but you’re running an advice-diode.
One way, apparently. Oh well, blather on about yubikey and keepass 10x serially.
#muhrights!
The comments are structured with reply indentation, so people can read individual threads. But even if they weren’t (new mobile view), people would still not read all comments.
Again, “most” people do not and will not read several dozen comments in an attempt to find an answer to a similar question they may have.
Comment section trolls often don’t give advice. They just tell people to “look it up for yourself”, “go read this entire thread”, “its been answered before”, or “Google is your friend”.
It’s counter productive, and pretty rude. So instead of offering real advice or suggestions to sincere questions, you want to troll by suggesting I not give answers to legitimately sincere questions.
It is common courtesy to answer questions regarding cyber security/privacy. And just because someone didn’t read previous comments or previous articles here on KrebsOnSecurity, and asked a redundant question… does NOT mean they don’t deserve a response.
You are free to provide your own suggestions on cyber security matters, but a reply of “shut up, you said that already in another thread” is not a sincere suggestion.
How does this address Bart’s question, re using a OTP code with his bank (Generated by Google Autheticator or Keepass or Authy or whatever)?
Seems to me that generating a OTP is useless if the bank can’t validate it. And even more useless if they *will* let an attacker in via their own OTP sent by SMS.
The question about using an OTP app on a desktop.
It’s the same secret and protocol used on Google authenticator, Authy, etc. It’s not proprietary, and the bank does not need to know what kind of app you’re using. They have no idea what software you’re using.
It’s confusing because they will recommend you install a specific app as if it mattered.
Why would a bank offer time-based OTP, when the transaction that is supposed to be authenticated is in no way included in the generated code?
PSD2 SCA requirements in Europe contain a dynamic linking requirement (sign what you see) which requires the authentication code to be dynamically linked to the transaction. As long as you and an attacker both can authorize different payments within the same 60 seciond time window that the OTP is valid, what use is it?
TOTP secrets are preshared. We aren’t talking about digital signature or individual transaction step up 2FA. Rather account login 2FA.
My advice is people should stop using Facebook completely , because Mark Zuckerburg does not care about it’s user base.
@ChrisSuperPogi Here it is:
Have I Been Pwned (correct spelling) was created by Troy Hunt troyhunt.com and is from Australia.
As for Fakebook – I left it about 2012 with no regrets because they wouldn’t let me use my pseudonym.
Besides, I had heard that they were using my data for monetary gain and I wanted a cut, but I knew that
would be impossible.
Fast forward to present day and numerous data breaches later (8 by one count) – still no regrets. Not a fan of Instagram either.
Big Thank You to Brian…I bookmarked your website a long time ago. Keep up your excellent work.
Oddly enough the phone number I’ve had since June 2019 showed up in haveibeenpwned, but I never entered my phone number on Facebook.com. It is however associated with my WhatsApp account, so they must be using the same security practices as the parent company
They are linked – article is from 02/19/21
https://www.msn.com/en-us/news/technology/facebook-tries-to-explain-the-whatsapp-privacy-changes-one-more-time/ar-BB1dPDhd
An email I haven’t used in well over 7 years, was snagged from bitly, discus and ticketfly. The one after that and the one I’m using now came up clear
Weird thing is I never used ticketfly, so I wouldn’t know how that got a positive on the HIBP
But both of the previous two were used on Facebook. I made use of the FB account kill feature in 2016, so maybe that data was actually deleted? But I had used the data kill years before that, only to find the account was still waiting for me when I tested it out in 2015, so I was never sure about that
As a non-tech person, I have learned a lot from Brian’s posts and readers’ comments. But I continue to be baffled by what I can use for two factor authentication other than my mobile phone or email address. I just looked at Authy and read some about it. I searched for my bank and Vanguard. Neither were on there. What is the average user to do?
https://2fa.directory/
Here’s a good start.
Thank you. Vanguard is interesting. You can purchase a YubiKey, but you must have text or phone as a back-up.
Best way I have found to lock down Vanguard for me is to restrict access to only my desktop PC.
See if you can change your phone number to a landline, maybe a VOIP at work. Vanguard seems to allow ‘phone call’ 2FA codes. Although still possible… hacking the VOIP call manager is exponentially more difficult than SIM swapping and other methods of SMS interception.
“restrict access to only my desktop PC”
Not really a “lock down”. But rather they use a web browser cookie to determine if 2FA is required.
So it’s a downgrade to single factor for convenience. If you can, you should disable this feature so 2FA is ALWAYS required, even from the same PC.
If you do want the convenience of disabling 2FA (or “remember my device”)… things to remember:
Cookies are frequently stolen. Many initial points of compromise, is the browser itself. The web browser is your front line (vanguard pun) to the Internet. It is the first piece of software that is going to process/parse potentially malicious code. Modern browsers are better at segregating each tab and plugin/extension into their own separate memory space, but if a vulnerability exists, it’s very possible that malware can read everything going on with other tabs.
That is why patching your browser must be done “immediately”.
For banks and other highly sensitive logins… I recommend using an entirely different browser from your day to day web browser. So malware would at least have to infect your entire system and look for cookies. Portable browsers (not ‘installed’, so profile data is wherever you put it) are nice, because most automated malware won’t know where to look for it’s data. Downside is the need to manually update, but upside is that even an unpatched browser that is only every used for one website is low risk.
For the technically inclined and slightly paranoid, running a separate virtual machine spun up just for financial institutions can provide robust security against host attacks. Qubes if you are bold.
Thank you, Jammin. I’m going to implement your suggestions.
“That is why patching your browser must be done”
“I’m going to implement your suggestions.”
“Also, breathe air.”
“I’m writing that down. This is great stuff, thank you.”
Patching the browser wasn’t a suggestion.
And you removed the context, where I wrote “immediately”. Not every patch is done immediately. Non perimeter, offline, kernel stuff isn’t patched immediately.
Browser are different, hence the urgency.
As far as my suggestion that she will try to implement, that probably has to do with setting up 2FA using a landline.
Actually you suggested an “unpatched” browser wasn’t a big security risk.
“That is why patching your browser must be done “immediately”.”
-me
I suggested the absolute opposite.
If you got a different impression, then you should actually read the entire comment before replying.
Facebook doesn’t allow the phone number associated with it to be removed. It gives such a dire warning (you will get locked out of account if you forget your password etc) when you try to remove your phone number that you just abandon the process and let the phone number remain
Facebook certainly does allow the deletion of phone numbers as long as you have an e-mail address in your contact info. I keep a trash e-mail address for just such purposes.
Yes it does allow phone number deletion provided they have an e-mail address to reach you.
Yeah, as if I would fall for another scam that wants my telephone number! This service will get hacked next week and even if my number isn’t available from the facebook hack, it will be available through this scam. This service doesn’t save your telephone number? Ha, I have a bridge for sale!
I use YubiKey or Google integrated authentication (which allows me to use YubiKey) wherever possible. I see the latter as the lesser of many evils right now, although I’m not happy about it. But there are a huge host of companies, particularly financial and medical related ones, who are stuck on using mobile texts as their strongest 2nd factor. For me, all of these are companies who couldn’t care less what a small customer like me wants and who I’m convinced won’t change their practices unless required to my government regulation or a major revolt among customers. Of course just getting them to offer MFA at all was a long struggle, as is getting other customers (including family members) to use it.
Facebook appears to have plugged this particular leak back in April 2018. See https://about.fb.com/news/2018/04/restricting-data-access.
The original vulnerability was published by Suriya Prakash back in 2012. See, for example, https://www.pcworld.com/article/2011396/facebooks-phone-search-can-be-abused-to-find-peoples-numbers-researchers-say.html. It is my understanding that all 533M records were collected by attackers choosing phone numbers at random, and then using FB to look up the account.
But this leak already flooded a lot of people.
Yeah, phone numbers aren’t a huge keyspace to just bruteforce through the entire set. The only thing that stops that, is slowing down the API responses. But of course, FB wants 3rd parties to do lookups fast and easy.
Vice has an article that really rips FB and Zuck.
https://www.vice.com/en/article/88awzp/facebook-says-its-your-fault-that-hackers-got-half-a-billion-user-phone-numbers
They got to be at the top of terrible tech companies and there is a lot of competition for the top spot.
They contacted me about an app security job because they were ramping up a team of people in various locations across the country. The phone screening went well and the POC said they would send me more info and set up a tech interview. Heard zip, zero, nothing from them, even on a follow up email. My interest was pretty low considering it is FB but I think they went back to my resume and figured out I wasn’t in the age profile they were looking for.
Earlier they contacted me so I set up a phone interview time, went home only to find out they canceled the interview with the reason to the effect that the applicant canceled it. Uh, no. I rarely cancel stuff, instead they did and tried to blame me.
I’ve had contact with other top tech companies and none behaved as poorly as FB.
This is what I have observed in my short life span. Kind of techy companies like MCI started having problems with offering really bad customer service, and the next thing we all knew, they were flushed down the toilet. I just wonder if Facebook is nearing that flushing down the toilet point? I don’t hate Facebook but I don’t even have the app installed on my phone anymore and I am reluctant to so much as leave a comment on someone else’s post. Why? Because they started becoming insane a few years ago with their policies on blocking accounts for 30 days. All I did was comment LOL in response to a Facebook-only friend’s post that he put up about himself. His profile (as is mine) was private and only friends could see what he posted. So he took a selfie of himself with a cowboy hat covering his u knows and he captioned the picture “Hey Facebook! Block this!” Now I can understand them maybe blocking him for 30 days but also blocking every single one of us for 30 days, including me, who merely typed LOL in response to his post? I lost most of my interest in Facebook after that.
wtf is international number format? obviously country code – but is it numerics only or do you add the plus in front of the country code? what about spacing? what about hyphens or parens?
…the plus sign, spaces, dashes, etc., are just for the human…
…the basic format is country code and the number you’d use to dial in that country…
…so for the USA the country code is 1 so the full number is, for example, 19995551212 where 1 is country code, 999 is the area code, and 5551212 is the number…
…for the UK, for example, it’s 4412345678 where 44 is country code for the UK, and the number is 12345678…
…etc…
…btw – you can also use the international code as though your calling USA from another country…
…so 01019995551212 also works as though your calling the US from the UK…
Top quality perfume available in lowest price
I prefer the delicate perfume that is spam.
And today we received news about 500.000.000 linkIN mail-addresses being leaked – it seems scrapers had nothing better to do. Am i happy to have taken the harsh viewpoint of filtering all social media out. Me=associal=healthy.
Learn Linux. Learn Docker. Learn Caddy. Learn Cloudflare. Deploy a Bitwarden server. Use it.
Remarkable that FB has managed to get the popular press to repeat the phrase “years old data.”
Another way of saying it and arguably more informative: “data copied barely more than a year ago.”
Fresh data.
Old and busted:
NextNewThing: Same question to the 500M who got Linkedined?
We had been used to such kind of leaks, aren’t we?
Any suggestions how LI and FB cases were actually happened? My guess is another API leak, devs still are not used to think about IDORs and overall API authorisation even if OWASP stated it 2 years ago in API TOP 10
re: Facebook and LinkedIn
If builders built houses the way programmers write software, the first woodpecker that came along would have destroyed civilization.
So would it better to just use a strong password and no second factor when possible? Some sites that are potential targets, like banks and credit cards, only have the option of using your phone number for the second factor. Of course some of them also demand a phone number of some sort. Watch out for Google Voice numbers as the second factor. Sometimes a GV number just won’t work to receive codes as I found out recently while helping my father file his taxes.
Even a strong password can be compromised easily. A clever phishing page, accidentally typing into the username field, stored in the browser, etc.
Even using a phone number for 2FA, as problematic as it is, will be more secure than single factor.
Thank you for posting that it could be just the thing to give inspiration to someone who needs it! Keep up the great work!
Thank you for posting that it could be just the thing to give inspiration to someone who needs it! Keep up the great work!