One of the oldest scams around — the fake job interview that seeks only to harvest your personal and financial data — is on the rise, the FBI warns. Here’s the story of a recent LinkedIn impersonation scam that led to more than 100 people getting duped, and one almost-victim who decided the job offer was too-good-to-be-true.
Last week, someone began posting classified notices on LinkedIn for different design consulting jobs at Geosyntec Consultants, an environmental engineering firm based in the Washington, D.C. area. Those who responded were told their application for employment was being reviewed and that they should email Troy Gwin — Geosyntec’s senior recruiter — immediately to arrange a screening interview.
Gwin contacted KrebsOnSecurity after hearing from job seekers trying to verify the ad, which urged respondents to email Gwin at a Gmail address that was not his. Gwin said LinkedIn told him roughly 100 people applied before the phony ads were removed for abusing the company’s terms of service.
“The endgame was to offer a job based on successful completion of background check which obviously requires entering personal information,” Gwin said. “Almost 100 people applied. I feel horrible about this. These people were really excited about this ‘opportunity’.”
Erica Siegel was particularly excited about the possibility of working in a creative director role she interviewed for at the fake Geosyntec. Siegel said her specialty — “consulting with start ups and small businesses to create sustainable fashion, home and accessories brands” — has been in low demand throughout the pandemic, so she’s applied to dozens of jobs and freelance gigs over the past few months.
On Monday, someone claiming to work with Gwin contacted Siegel and asked her to set up an online interview with Geosyntec. Siegel said the “recruiter” sent her a list of screening questions that all seemed relevant to the position being advertised.
Siegel said that within about an hour of submitting her answers, she received a reply saying the company’s board had unanimously approved her as a new hire, with an incredibly generous salary considering she had to do next to no work to get a job she could do from home.
Worried that her potential new dream job might be too-good-to-be-true, she sent the recruiter a list of her own questions that she had about the role and its position within the company.
But the recruiter completely ignored Siegel’s follow-up questions, instead sending a reply that urged her to get in touch with a contact in human resources to immediately begin the process of formalizing her employment. Which of course involves handing over one’s personal (driver’s license info) and financial details for direct deposit.
Multiple things about this job offer didn’t smell right to Siegel.
“I usually have six or seven interviews before getting a job,” Siegel said. “Hardly ever in my lifetime have I seen a role that flexible, completely remote and paid the kind of money I would ask for. You never get all three of those things.”
So she called her dad, an environmental attorney who happens to know and have worked with people at the real Geosyntec Consultants. Then she got in touch with the real Troy Gwin, who confirmed her suspicions that the whole thing was a scam.
“Even after the real Troy said they’d gotten these [LinkedIn] ads shut down, this guy was still emailing me asking for my HR information,” Siegel said. “So my dad said, ‘Troll him back, and tell him you want a signing bonus via money order.’ I was like, okay, what’s the worst that could happen? I never heard from him again.”
HOW TO SPOT A JOB SCAM
In late April, the FBI warned that technology is making these scams easier and more lucrative for fraudsters, who are particularly fond of impersonating recruiters.
“Fake Job or Employment Scams occur when criminal actors deceive victims into believing they have a job or a potential job,” the FBI warned. “Criminals leverage their position as “employers” to persuade victims to provide them with personally identifiable information (PII), become unwitting money mules, or to send them money.”
Last year, some 16,012 people reported being victims of employment scams with losses totaling more than $59 million, according to the FBI’s Internet Crime Complaint Center (IC3). But the real losses each year from employment scams are likely far higher; as the Justice Department often points out, relatively few victims of these crimes report the matter to the IC3.
LinkedIn said its platform uses automated and manual defenses to detect and address fake accounts or fraudulent payments.
“Any accounts or job posts that violate our policies are blocked from the site,” LinkedIn said in response to a request for comment. “The majority of fake job postings are stopped before going live on our site, and for those job postings that aren’t, whenever we find fake posts, we work to remove it quickly.”
LinkedIn’s most recent transparency report says these automated defenses block or automatically remove 98.4% of the fake accounts. But the scam that ensnared Gwin and Siegel is more of a hybrid, in that the majority of it operates outside of LinkedIn’s control via email services like Gmail and Yahoo.
This, by the way, should be a major red flag for anyone searching for a job, says the FBI: “Potential employers contact victims through non-company email domains and teleconference applications.”
Here are some other telltale signs of a job scam, as per the FBI:
-Interviews are not conducted in-person or through a secure video call.
-Potential employers contact victims through non-company email domains and teleconference applications.
-Potential employers require employees to purchase start-up equipment from the company.
-Potential employers require employees to pay upfront for background investigations or screenings.
-Potential employers request credit card information.
-Potential employers send an employment contract to physically sign asking for PII.
-Job postings appear on job boards, but not on the companies’ websites.
-Recruiters or managers do not have profiles on the job board, or the profiles do not seem to fit their roles.



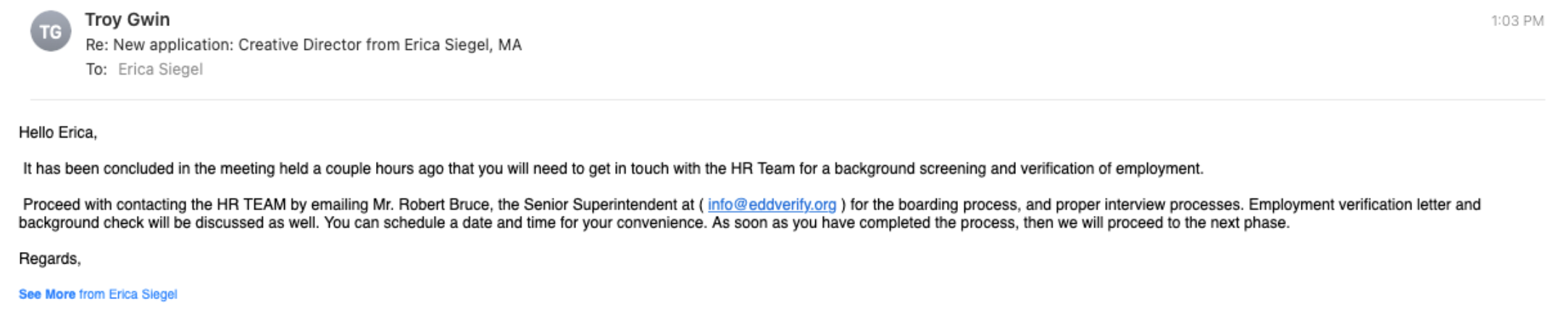

Had I received this letter, would my suspicions be aroused by the awful writing? It doesn’t look like something a native English speaker would compose. But in our world of multinational corporations and employees from diverse backgrounds – and frankly, I’ve known native English speakers who can’t write even that well (though none of them have ascended to the level of Senior Recruiter, not yet at least) – how confident could I be? These days, everything requires verification.
From one Stephen to another, yeah, I am with you.
To quote a famous president: “Doveryai, no proveryai.”
I copied/pasted that quote into Bing Translate and it ‘auto detected’ as Spanish, failing to translate!
…roughly “trust, but verify” – in Russian…
First thing I would have done was to look at the headers. I always do that with any weird email to see if I can get any clues on where it’s coming from
They were from gmail accounts, so the headers would have told you nothing. The people who got duped were naive enough to think a large corporation wouldn’t use their own domain name.
Scammers are buying domains and hosting services. They send email from their registered domains.
something you cannot do w/Outlook 365
I think what John Clark is referring to is setting up legitimate domains such as xyzcorp.com to give their emails an air of legitimacy. Not “spoofing” existing domains.
Yes you can. You have to tap the email header to pull down the email. I get fake email from so call Amazon for delivery that I never ordered in the first place and I do look who actually send it.
I have seen such kind of thing from an email address that does not correspond to the actual company in question unless you initiate the job search. If they do, then you must do an actual search of the company based on its location. My motto, the more you search things, the more Qs you have.
The same thing the person in the article did and saved her from the trouble.
Here’s another one: I received a call from a head hunter firm that I have applied to (it is familiar and known) which he hung up before it went to VM. Based on my search I was able to locate the name of the person who called. So I called back using the exact # , he denied that he called and I mentioned that I was able identify his name and I used his own # to return the call. He then said “yes I did called.” I ended up talking to him in person.
Great article Brian, thank you! LinkedIn must have their hands full dealing with this type of scam and fake profiles. I am sure the proliferation of cute animal pictures, political posts and my family member did this… diverts their attention from what really needs to be addressed. Over the last couple of years LinkedIn has become more of a Social Media site than a professional networking site. Unfortunate, I always had a great respect for the site and what it offered.
What amazes me is that Internet user are not aware that just like LinkedIn , Facebook is a huge cesspool of scammers from Western Africa
I’m curious what the companies whose names are being spoofed for these scams can do, if anything. These fake jobs posts are not just on LinkedIn but on every gig-work site there is around the globe.
In the case of Geosyntec (the real corp), if they are made aware of the scams and their intellectual property is used via clone sites or typosquatted sites and whatnot, they can issue take down notices through legal avenues to hosting providers and name registrars and such, but that can often take weeks/months unless you have good connections to people working at said hosting providers or registrars.
Other options are using a service that does this for you – i.e. recorded future or zerofox and the like. They have agreements with the big players that give them auto takedown capability or nearly instant ability to take action.
Lots of large orgs do this for brand and identity protection – they don’t want people getting conned and their brand/name being associated to a bad experience.
Unfortunately, I think you’ll find that the approach you suggest rapidly becomes whack-a-mole. For every fake the company takes down, two more will spring up in their place.
I wonder if it might be possible to get a sting operation going… Screen shot the interviewer, capture and trace their IP address. Have the FBI set up a national program with a call-tree, find the nearest field office to the perpetrator and see if it isn’t possible to keep the interview on the line long enough to get someone there. Still whack-a-mole, of course, since the tactics will change, but if you could catch and enough of them…
Uh, Brian, you used an abbreviation without defining it. 🙁 What’s PII?
Personally identifiable information
PII=Personal Identifiable Information
…Personally Identifiable Information…
…IIHI = Individually Identifiable Health Information…
It’s described in the story. And it’s me quoting the FBI, not me saying it
“Fake Job or Employment Scams occur when criminal actors deceive victims into believing they have a job or a potential job,” the FBI warned. “Criminals leverage their position as “employers” to persuade victims to provide them with personally identifiable information (PII), become unwitting money mules, or to send them money.”
> One of the oldest scams around — the fake job interview that seeks only to harvest your personal and financial data
Yeah, I hear that one was really common around the savannah.
Brian Krebs, you are a brilliant researcher and writer. This entry is enlightening, to say the least HOW TO TELL A JOB OFFER FROM AN IDENTITY THEFT TRAP. I have seen job applications and even offers of money grants running these scams. Thank you for all you do,
If they are using an email account that is not directly connected to their domain that is a Black flag. If they want you to pay for anything that is a Black flag, Always do research on the company and ask questions about the company and questions very specific about the job. Expect to talk with a real person.
Simpler Method: If it comes from an Indian firm, heave it.
What is really nasty is legit staffing companies have been outsourcing their recruiting and first layer recurring to Indian companies. It is no longer possible to tell the difference between legit scummy staffing companies and scammers. They all use India and rent-by-the-hour offices in major US cities.
I know. This has been going on since the 90’s, and it’s only gotten worse. The losers in this game are US Citizen IT pros as well as the Indians who get here on a H1B, only to find they’ve become indentured servants living 5 to a 1 br. apartment. There are several of these apartment “little India’s” in San Diego, Silicon Gulch, and any tech-heavy city.
The only winners are the H1B body shops and Big US Tech.
…and I’m NOT anti Indian. Love the people, the corporations and current government I can do without.
any company that outsources to third world centers for cheap labor… i would not apply to period. it’s indicative of their culture.. something i choose not to be part of. even if it’s a recruiter hired by a primary company… i still would not apply.. maybe that’s why i retired at 54…. was sick of zero personal human interaction, i was never big on applying to a blind p o box… or some generic email address. if you can’t talk and interact with a real human being… then i didn’t apply.
So very true. They’ve managed to destroy the recruiting process.
“Potential employers contact victims through non-company email domains and teleconference applications.”
This describes exactly the experience with some real jobs these days; a small or medium company does not perform the initial screening with their own HR department, but all contact is via a recruiting company or FaceTime / Zoom. Hopefully the recruiting company itself can be checked out to verify.
The kind of scam is also typical in real estate scenarios when people try to find an appartement.
A similar version has been going on for decades. Real small companies troll for your resumes and will include them as part of their bid packages for contract work for larger companies or the government. Their excuse is they’ll offer you a job if they win the contract. You generally never hear from the small company again, unless multiple companies bid your resume for the same contract.
Really big “defense contractors” do this too. Decent medium sized companies often find they are bidding against their own staff because a big competitor managed to get a copy of their last big proposal in a similar area.
That happened before with my company. They were not please when they found out but were grateful they found out before sending out a proposal. When you blackball yourself with one firm, word gets around fast. This was a fews years back but I know we never used them again.
I’ve always wondered if/ how LinkedIn validates that a person’s stated employer really is their employer. I suspect I could claim to work for, say, Goldman Sachs, and no one would call me on it. If I were then to pose as a hiring manager, or an HR staffer….
‘Troll him back, and tell him you want a signing bonus via money order.’
Dad rocks.
You just have to be smarter than the scammers. I e-mailed someone that actually works in HR for a company that was trying to “recruit” me through an App that they asked me to download on my phone (major red flag, but I wanted to play along to see what they said so that I could get what I wanted, which was to curse them out). I asked if they knew the HR lady that I’d just e-mailed. They stopped communicating immediately.
Ah ha…
My question is, did she get the money order ;’>?
Several years ago i was contacted by an individual claiming to be a recruiter for a staffing company. The individual wrote that he had a contract position for my skill set and job title and in my geographic area. The email was sent from a company email address and had a link to the company’s web site and detailed job description. I like to know more about who i am going to be talking to and did a LinkedIn search and saw the individual had just a handful of connections on his profile.
Doing a little further digging and i saw that there were five other web sites that were identical with the exception of the recruiters’ name and the company name. I also found a number of entries on 800notes dot com saying it was a scam to get targets’ DOB and SSN. Annoyingly legit staffing companies claim that big companies in my region need partial DOB and SSN in order to submit a candidate.
I shared this experience with Krebs at the time, but he choose to not do a report at the time. I also reported to IC3 and never got a response.
I built a Blogger site to try to spread the news about this scammer (I used a fake name to protect myself). For a while i was getting regular replies from other individuals that had been targeted by the scammer and were smart enough to search before replying.
https://fakestaffing.blogspot.com/
For over three years i tracked the scammer and saw that he built 53 different fake staffing companies and paid for separate domains just so it looked real and he could send emails with matching company addresses. Some of the hosting companies are based in the United States. I sent emails warning them and several of the hosting companies took down the domains. One hosting company in Bria, California responded they did not care and continued to host the scammer.
That hosting company’s IP range might quickly find its way into the “Drop all traffic from source” rule on my firewall…
I know someone who got a signing bonus after providing a company with direct deposit info for a new remote job. Then the recruiter said that the deposit was too much and he wanted some of it returned, to him personally, via Western Union. Of course the direct deposit bounced and the whole thing was a scam. Cost my friend a couple thousand dollars. I have a rule: money only flows one way. I don’t send any money, for any reason, related to employment.
J Donald
Anyone can add any company name to their profile on LinkedIn and link that to the LinkedIn company page. That “person” will appear as an “employee” of that company. I’ve seen this on our company page and could do nothing except block that “person’s” profile. but this only stops me from seeing the person on our LinkedIn company page (I am the administrator of the company page). Visitors of the company page will still think that this “person” is an “employee” of our company (if they click on employees of the company profile on LinkedIn.
I have seen job scams often target college students as well. Unfortunately I have seen some college students not only send personal information but money for “remote” positions. It also appeared they were targeting foreign college students who were in the U.S. for school.
Reminder to tell warn your kids too.
Unfortunately the last couple of times I’ve been in the labor market, I have gotten things that appeared to be scam emails but turned out to be legitimate. So be very careful in both directions. I’ve also had HR employees ask me to scan and email forms containing highly sensitive information without providing a PGP key or anything. I’ve had to upload it to my personal webserver and send them an https link to it. I have no idea how other people do that, but it makes me very nervous. It makes the whole job search just that extra little bit stressful.
LinkedIn is filled with scam job announcements that just hand your info over to recruiters and perhaps criminals too. But when you need a job, what are you to do?
Don’t do that. Being in a position of ‘need’ is not a valid justification for making poor security decisions with P.info.
Great article! Cyber criminals are getting ever more sophisticated with their methods, whilst attacks are getting ever more frequent – particularly within the last year with the rise in job hunters. When it comes to social engineering tactics, it only takes one human error for the attack to be a success, which is why user education is so critical for businesses to protect themselves from a data breach. There’s some great information on cyber security user training here if anyone’s interested – https://stripeolt.com/cyber-security/cyber-security-education/
Anyone with two brain cells to rub together would know that email was a fake. People in those positions don’t write like English is their second language.
“Believe none of what you hear and believe half of what you see” is considerably older than 40 years. It has been attributed to Benjamin Franklin (1700s), Edgar Allan Poe (1800s), and others as well.
I’ve already received several contacts from easily-determined scam offers for security analyst & engineer positions. I thought to myself, “surely there must be lower hanging fruit.” I suppose this answers my question.
It’s very easy to find the Public Relations’ Executive from a particular company’s email on their website. From there you can easily confirm if the job offer is genuine by sending a polite email to that person, asking if the email of the executive in the job offer is the correct one. If “NO” — then you know nothing’s legitimate about the offer. There are other ways but this is the simplest. Public Relations’ role involves dealing with the public and mitigating any potential scandal or bad publicity. They’re always eager to help.
Linkedin is criminal. Try googling “full loadz cvv” and see what the number one result is? Also try searching for “travel companion” using the linkedin search option.
Instagram.com/btc.exe
Why not address the larger version of this problem on LinkedIn? Resume info skimming and reselling your info by the fake companies pretending to be small consulting/staffing firms. A standard resume has your name, phone number/email address, etc. They just post some job and stating they are consulting/staffing for a bigger company. Then ghost you after you submit. LinkedIn cannot confirm how many cases but acknowledge this “might” be happening. With no way to prove when an actual client is ghosting you vs a fake company made to skim for resume info to sell. It may seem like paranoia. I’ve seen a staffing agency reuse linkedIn job posts IDs under a different title, so when I try to apply linkedIn says I already applied.
Any fishy email that I get, I put it in ‘Forward’ mode whereby the actual domain of the sender becomes visible. Most of the newbie and low IQ phishers fall into this category. But some are a bit smarter and able to hide the domain from showing up in Forward mode. For them, there is a little more leg work. Right-click on the message at the In-Box > View Source.
There’ll be a LOT of jibberish there, but the ‘From” line which is usually about the center of the displayed code shows the origination point, including the IP address.
Thanks to my email being in the list of multiple breaches, I’m getting a LOT of these scam emails, lately from .Info and .Press and similar domain extensions. Some of the domain registrars have their barns wide open, and appear to be doing nothing to stop the criminals from setting up untold number of scam accounts at their domains and from unleashing their crap on the hundreds of millions of email addresses that have been, and are continuing to be, harvested in breaches from incompetent holders of PII.