Microsoft on Tuesday issued an emergency software update to quash a security bug that’s been dubbed “PrintNightmare,” a critical vulnerability in all supported versions of Windows that is actively being exploited. The fix comes a week ahead of Microsoft’s normal monthly Patch Tuesday release, and follows the publishing of exploit code showing would-be attackers how to leverage the flaw to break into Windows computers.

At issue is CVE-2021-34527, which involves a flaw in the Windows Print Spooler service that could be exploited by attackers to run code of their choice on a target’s system. Microsoft says it has already detected active exploitation of the vulnerability.
Satnam Narang, staff research engineer at Tenable, said Microsoft’s patch warrants urgent attention because of the vulnerability’s ubiquity across organizations and the prospect that attackers could exploit this flaw in order to take over a Windows domain controller.
“We expect it will only be a matter of time before it is more broadly incorporated into attacker toolkits,” Narang said. “PrintNightmare will remain a valuable exploit for cybercriminals as long as there are unpatched systems out there, and as we know, unpatched vulnerabilities have a long shelf life for attackers.”
In a blog post, Microsoft’s Security Response Center said it was delayed in developing fixes for the vulnerability in Windows Server 2016, Windows 10 version 1607, and Windows Server 2012. The fix also apparently includes a new feature that allows Windows administrators to implement stronger restrictions on the installation of printer software.
“Prior to installing the July 6, 2021, and newer Windows Updates containing protections for CVE-2021-34527, the printer operators’ security group could install both signed and unsigned printer drivers on a printer server,” reads Microsoft’s support advisory. “After installing such updates, delegated admin groups like printer operators can only install signed printer drivers. Administrator credentials will be required to install unsigned printer drivers on a printer server going forward.”
Windows 10 users can check for the patch by opening Windows Update. Chances are, it will show what’s pictured in the screenshot below — that KB5004945 is available for download and install. A reboot will be required after installation.
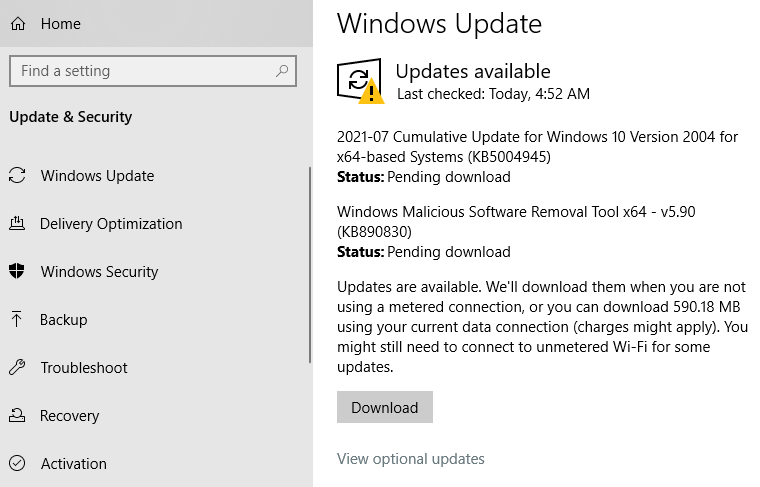
Friendly reminder: It’s always a good idea to backup your data before applying security updates. Windows 10 has some built-in tools to help you do that, either on a per-file/folder basis or by making a complete and bootable copy of your hard drive all at once.
Microsoft’s out-of-band update may not completely fix the PrinterNightmare vulnerability. Security researcher Benjamin Delpy posted on Twitter that the exploit still works on a fully patched Windows server if the server also has Point & Print enabled — a Windows feature that automatically downloads and installs available printer drivers.
Delpy said it’s common for organizations to enable Point & Print using group policies because it allows users to install printer updates without getting approval first from IT.
This post will be updated if Windows users start reporting any issues in applying the patch.




Quick correction: change “Server 2015” to “Server 2016” in the fourth paragraph.
I heard about this from work last week, great work on getting this out quick (Server 2015 typo)!
Quick release from MS might mean it’s buggy. Small sample size, but one out of three of our PC’s now crashes with BSOD with the patch installed.
I’m seeing BSOD on 2 out of 10 so far.
Just when printing, or on boot? If on boot, this is SCARY for updating servers…
When printing. Interesting because as the page starts physically printing the PC reboots. After the reboot the page prints again.
Same here.
PC’s with Brother printers connected via USB are getting BSOD too.
I am seeing the BSOD issue when printing to a Brother printer connected via USB.
Same here. Brother printer MFC-J491DW, connected through USB. Installed new patch, BSOD fairly quickly and several times. Uninstalled, paused updates, computer has been holding for 24 hours.
The server side emergency patch to fix printer problems with KB5004945 not working at least for me. Still receiving BSOD when attaching Brother printer via USB. Page fault in non-paged area is the error message. Followed path in Registry Editor to check if server side patch installed. Again, if I unplug USB, computer holds.
After installing the update- I get a notice “windows encountered a problem and must reboot”. I have to delete the patch. Is there a known bug that MS is repairing? Thanks!
Same here on a machine connected to network. So far haven’t heard of other Win10 machines with same issue. I’ve delayed update reboot as far as I could in hopes of finding solution.
I have the same problem – there are four computers in our household, all different makes and models, and all are having the same issue. A bit of a catch-22 – we need the fix to stop a serious security issue, but can’t install teh fix because it renders the computers unusable. Hoping MS do something about this quickly!
I did one of the recommended work arounds (Disable inbound remote printing through Group Policy), which seems to not have caused any problems, i.e., I can still print to my printer via wifi at home. Given the nature of this – and concerns about potential bugs in the patch – I may wait 24-48 hours before updating with it…
Installed with no problems here. The update did not show up automatically – I had to click the “Check For Updates” button which did bring up the update in about 20 seconds. Downloaded, installed and restarted all with no problems.
after the update , all my customer’s zebra TLP2844 stop working KB5004945
ours too – any way to fix the problem ?
All of ours too. Our ZT410’s as well.
Reinstall the driver
Uninstall the update and reinstall the printer and set it up again like new. Took me a couple of hours of trying every fix I could think of and had to ask my wife for help and she fixed it ( uninstall update ) in 30 minutes. I have the LP 2844 also. Good luck
All of my Zebra ZT220’s stopped printing. We are a fish processing company and this has caused thousands of dollars in downtime.
Same here, tested 2 home workstations before attempting test deployment. Both systems got BSODs.
Did this happen only when printing, or on boot?
Tried to install the OOB update onto two separate 2008R2 servers. Update completes successfully, but after the required reboot, I get the message “failure configuring Windows updates, reverting changes.” Be merciful, these are not my servers.
Tried to install the OOB update onto two separate 2008R2 servers. Update completes successfully, but after the required reboot, I get the message “failure configuring Windows updates, reverting changes.” Be merciful, these are not my servers.
Can someone make this easier for tech-challenged people? My sister is in her 70’s and still has Windows 7. Can you just post a link “to download Windows 7 patch click here”?
Wi ndows 7 is no longer supported = there are no publicly available patches
“The PrintNightmare exploit is so scary, even Windows 7 just got an emergency fix.” M.S. has an emergency fix to download for windows 7. Even though they no longer support windows 7. That’s how bad the security breach is.
This morning’s CNN report on this said the below. So, doesn’t this mean that it does cover Windows7?
“ Despite announcing that it would no longer issue updates for Windows 7, Microsoft issued a patch for its 12-year old operating system, underscoring the severity of the PrintNightmare flaw. “
Security Patches are still common for Windows that is no longer “supported”
https://www.catalog.update.microsoft.com/Search.aspx?q=KB5004951
2021-07 Security Only Quality Update for Windows 7 for x64-based Systems (KB5004951) Windows 7 Security Updates 7/6/2021 n/a 34.6 MB
2021-07 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB5004953) Windows 7 Security Updates 7/6/2021 n/a 358.0 MB
ann after downloading this patch you find out that you need to install another patch first, when clicking on that one, that patch is not available anymore
You can get past that hurdle via several other patches as outlined here:
https://support.microsoft.com/en-us/topic/july-6-2021-kb5004951-security-only-update-out-of-band-e05a81cd-9b45-4622-b715-ddb2367bca47
However, that ultimately won’t do you any good if you have Windows 7. After spending half a day trying to install the patches I discovered the truth. Microsoft finally figured out how to screw us out of security updates. Yes, the security update is still created, but you won’t be able to install it unless you have an “ESU MAK key”. You get this ESU (extended security updates) MAK key ONLY IF YOU PURCHASE EXTENDED SUPPORT FROM MICROSOFT!!!
They proudly state, “After installing this update and restarting your device, you might receive the error, “Failure to configure Windows updates. Reverting Changes. Do not turn off your computer,” and the update might show as Failed in Update History.
THIS IS EXPECTED in the following circumstances:
If you do not have an ESU MAK add-on key installed and activated.
They have a link where you find out more about ESUs and you find out:
“How can I purchase ESUs? Extended Security Updates are available through specific volume licensing programs. ”
So yes, they have been planning to screw us over all along. I would not be surprised at all if they purposely built these critical vulnerabilities into their software and then leaked the information when they finally want to force anyone with an old OS to upgrade or be pretty much guaranteed to get hacked sooner or later. It’s a reprehensible way of doing business, but it is beginning to be a pattern, and not a coincidence.
I went through the same process and had the same outcome on my Windows 7 Sp1 x86 machine. No luck
Have you found a way to fix this problem if you’re not on ESU and need to print from your machine?
FWIW this page claims “Windows 7 – not affected”: https://blog.0patch.com/2021/07/free-micropatches-for-printnightmare.html
Any comments?
My experience precisely when trying to protect my Windows 7 SP1 x86 machine without having ESU.
Do you know of any workaround if you still want to print as usual?
FWIW https://blog.0patch.com/2021/07/free-micropatches-for-printnightmare.html claims ”Windows 7 – not affected” by PrintNightmare.
I had the same outcome on my Win 7 SP1 machine.
Do you know of any workaround if you want to use your machine to print normally?
FWIW https://blog.0patch.com/2021/07/free-micropatches-for-printnightmare.html claims Windows 7 not affected by PrintNightmare.
Isn’t that a paid service?
There are hundreds of good sources for information, The Slovenian owned 0 patch isn’t one.
As someone who has to deal with Win7 issues still in the work environment I hear you. Let’s keep in mind at some point, everything gets beyond the ‘repair/fix’ stage. Its also still possible to upgrade a Win7 machine to Win10 for free, so its not like M$ is forcing people to spend money, just move on to a system that is (supposedly) better designed to handle today’s issues & needs.
Maybe you can protest in another Windows Refund Day.
https://www.youtube.com/watch?v=1j9j-Ywjmbk
In 1999, groups of open source software users staged an international protest against Microsoft. They demanded a refund for something they didn’t want, but were forced to pay for: Microsoft Windows 98. Today’s video examines one of these protests, which occurred in California’s Silicon Valley, and the battle that these users fought to get their money back.
I have a confirmed workaround for this. First, I agree with everything you said regarding MS and also wasted hours of time trying to get this installed, not realizing they had this stupid licensing program.
The fix is to use BypassECU (exactly what the name implies) You can find the latest version here (version 11):
https://gitlab.com/stdout12/adns/uploads/b5ad06702413b6bf6b1d5a1db8b086d4/BypassESU-v11.7z
Note, the ZIP password is 2020. After installing, reboot, then Windows Update will be patched to allow ECU updates to come through. Props to the developers of this software.
My apologies for the typo, I meant ESU, not ECU.
Run Windows Update
Wupdate didn’t suggest any of these on my 7 box.
Assuming I don’t do any printing on a machine and have no plans to, would disabling the Print Spooler service protect me from possible future vulnerabilities of this nature? Or are there any other Printing services I can disable that would achieve the desired effect?
I’d imagine turning the spool service to disabled + stopped will keep you safe since the flaw is in the service itself, according to the MS blurb. But we don’t know how accurate the blurb is on that point. Probably good enough. You can then use a separate 3rd party screen capture to PDF instead of printing regularly. That should work. In a month when they re-issue a patch that doesn’t hose printers and BSOD and whatnot, maybe then go ahead.
It appears Microsoft is 0 for 2 on an actual fix for this one, as researches are still able to bypass today’s out of band patch. Microsoft only fixed the remote code execution component. Local escalation is still possible with SYSTEM privileges on some systems. Details on BleepingComputer.
https://www.bleepingcomputer.com/news/microsoft/microsofts-incomplete-printnightmare-patch-fails-to-fix-vulnerability/
This was already circumvented.
The author of mimikatz: https://github.com/gentilkiwi/mimikatz/releases/tag/2.2.0-20210707
As many readers already pointed out, exploitation workarounds have already been discovered in this patch (https://www.bleepingcomputer.com/news/microsoft/microsofts-incomplete-printnightmare-patch-fails-to-fix-vulnerability/). Does not seem to be a valid solution. Additionally, the patch totally breaks the functionality of all Zebra printers.
Does this workaround work or a waste of time in this case?
===
1. Press WIN+R keys together to launch RUN dialog box. Now type regedit and press Enter. It’ll open Registry Editor.
2. Now go to following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT
3. Select Windows NT key and right-click on it and select New -> Key option. Set the new key name as Printers
4. Now select Windows Printers key and in right-side pane, right-click on empty area and select New -> DWORD (32-bit) Value option.
5. Set the new DWORD name as RegisterSpoolerRemoteRpcEndPoint and set its value to 2 to disable inbound remote printing operations
6. Reboot
===
For those of you with Windows networks under your belt, I stayed up late writing a PowerShell script to tackle the install with some reporting capabilities.
As of writing the darn hotfix isn’t available from standard Windows Update app, and the out-of-band files are unique depending on Windows release, so this factors that in.
https://github.com/djcabrera/printNightmareUtility/blob/main/checker-deployer.ps1
Hope it helps.
Thanks Dan. I’ll check it out.
Out of Band, essentially means a manual and difficult update process.
For those of us with no printer, should this be a concern? How about print to PDF? I removed all default printer icons except for the PDF one.
I have print spooker service disabled and can still print to PDF, so that should be fine. Just turn it off in services.msc
It won’t help to remove icons/printers. The service that allows you to print using the built in Windows mechanism, is the vulnerable part.
Try disabling the print spooler service. And see if you can print. Even ‘print to PDF’ may be unavailable depending on how the app is configured.
Some PDF renderers might be self contained (perhaps Adobe Acrobat Distiller), and not rely on the Windows print spooler service.
He likes to repeat things, it’s his schtick.
I installed the patch this morning. I immediately had a problem printing to a printer that was USB connected and another that was ethernet connected. I uninstalled the patch and near the complete of that, I got the BSOD. I powered down and powered on, and machine worked ok again without the emergency patch
I installed the patch this morning. I immediately had a problem printing to a printer that was USB connected and another that was ethernet connected. I uninstalled the patch and near the complete of that, I got the BSOD. I powered down and powered on, and machine worked ok again without the emergency patch.
I think the issue is with the print spooler service program (C:\WINDOWS\System32\spoolsv.exe). Deleting printers etc will not help.
I have yet to find a Windows 7 patch that Microsoft said they have created. Where can I find that download? The CNN article stated that Microsoft felt the flaw was so severe that a fix for Windows 7 would be available.
Unless you have purchased and ESU (Extended Service Update) license from Microsoft you are not going to find any update as Windows 7 is end of life and has been out of mainstream (free) support for years.
If you’re a home user with a simple printer using a satellite connection and no WiFi, does this patch need to be installed?
You may want to read this:
Microsoft’s incomplete PrintNightmare patch fails to fix vulnerability
https://www.bleepingcomputer.com/news/microsoft/microsofts-incomplete-printnightmare-patch-fails-to-fix-vulnerability/
All of this is another example of why I abandoned windows a while back. Microsoft can’t seem to secure their software. So many monthly patches make me ponder if a bunch of their offshore programmers are also working for local governments purposely introducing vulnerabilities. Msft should spend a couple years focused on securing their software instead of introducing a new pile of defects with win11.
George,
Actually Windows 11 can help reduce the defects in Windows because it is Microsoft’s major step in iterating to replace components and the legacy code they are based on. Microsoft has been rewriting on the noncritical supporting applications to use UWP. They have been doing this since the beginning of Windows 10. Windows 11 does require very recent 64bit CPUs that itself can lead to better code maintenance because Microsoft can rewrite and optimize the code.
Windows 11 forces Secure Boot which requires kernel mode driver signing so that could have been a possible mitigation for this attack if print drivers are kernel mode. I don’t know enough about this attack and what mode print drivers operate in.
Download shows 100% but does not install update. What to do?
I have the same problem.
No problems with the update on my end.
My thoughts on “Microsoft Issues Emergency Patch for Windows Flaw
I have not seen any formal notification from MicroSoft to the use community about the scope of the flaw, resolution timeline and support plan.
Is MicroSoft planing to issue patch that will auto install and a novice user, which I am , does not have to worry about it?
As a novice end user, I am scared of using my computer and feel frustrated due to lack of information that I can trust.
I wish MicroSoft has a better process for the. release of patches.
There is a normal Windows update process. Google how to enable automatic updates.
Don’t be afraid of computers, this isn’t that bad of a vulnerability for workstation users. It got a lot of attention because of what it means for Servers, and especially Domain Controllers.
MS updated my system this morning and now I can’t access any of my apps nor any settings. Start menu has completely change and half the entries are non-responsive.
Since I can get to the apps or settings I can’t load any troubleshooters.
Is there a fix?
DO NOT INSTALL KB5004945 if you are using Zebra printers. It will cause BSOD on some PC and most will printers will stop printing and just spool endlessly. We have 14 Zebra ZT220 and all failed today causing a nightmare in our production lines. We process about 40,00 lbs of fish a day and this “patch” has caused us thousands in lost time today.
After installing KB5004945 I can’t print to my Canon TS302 color printer.— However, I can print to my Brother lazar printer. Hope Microsoft comes up with a fix
Same here with a TS205 (“printer spooler hangs”). Removing the patch made the printer work again.
I installed it on 4 systems so far, and zero problems, including printing.
Of course it makes sense that I’m not seeing issues, I have backups to roll back to, which (usually) keeps Murphy at bay.
TS205 print issues both with the June and July updates (KB5003690 and KB5004945), issues solved after rollback of the updates. Waiting for any news that this is being worked on.