Criminal hackers will try almost anything to get inside a profitable enterprise and secure a million-dollar payday from a ransomware infection. Apparently now that includes emailing employees directly and asking them to unleash the malware inside their employer’s network in exchange for a percentage of any ransom amount paid by the victim company.
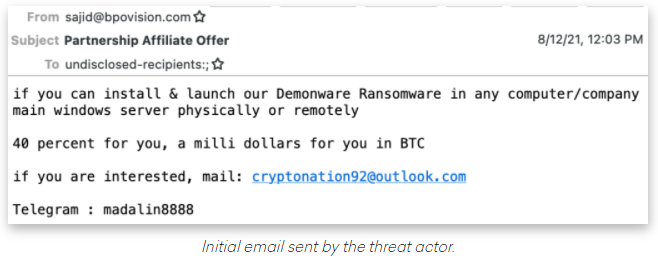
Image: Abnormal Security.
Crane Hassold, director of threat intelligence at Abnormal Security, described what happened after he adopted a fake persona and responded to the proposal in the screenshot above. It offered to pay him 40 percent of a million-dollar ransom demand if he agreed to launch their malware inside his employer’s network.
This particular scammer was fairly chatty, and over the course of five days it emerged that Hassold’s correspondent was forced to change up his initial approach in planning to deploy the DemonWare ransomware strain, which is freely available on GitHub.
“According to this actor, he had originally intended to send his targets—all senior-level executives—phishing emails to compromise their accounts, but after that was unsuccessful, he pivoted to this ransomware pretext,” Hassold wrote.
Abnormal Security documented how it tied the email back to a young man in Nigeria who acknowledged he was trying to save up money to help fund a new social network he is building called Sociogram.
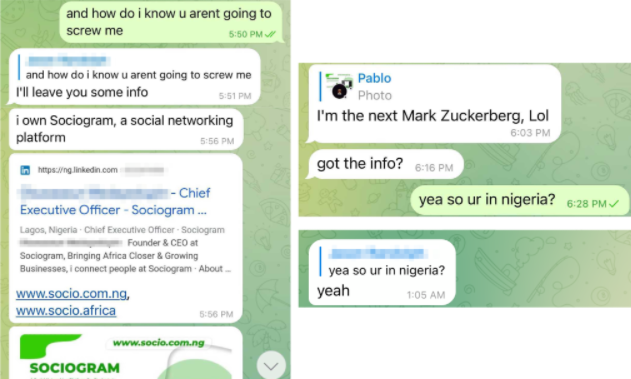
Image: Abnormal Security.
Reached via LinkedIn, Sociogram founder Oluwaseun Medayedupin asked to have his startup’s name removed from the story, although he did not respond to questions about whether there were any inaccuracies in Hassold’s report.
“Please don’t harm Sociogram’s reputation,” Medayedupin pleaded. “I beg you as a promising young man.”
This attacker’s approach may seem fairly amateur, but it would be a mistake to dismiss the threat from West African cybercriminals dabbling in ransomware. While multi-million dollar ransomware payments are hogging the headlines, by far the biggest financial losses tied to cybercrime each year stem from so-called Business Email Compromise (BEC) or CEO Scams, in which crooks mainly based in Africa and Southeast Asia will spoof communications from executives at the target firm in a bid to initiate unauthorized international wire transfers.
According to the latest figures (PDF) released by the FBI Internet Crime Complaint Center (IC3), the reported losses from BEC scams continue to dwarf other cybercrime loss categories, increasing to $1.86 billion in 2020.
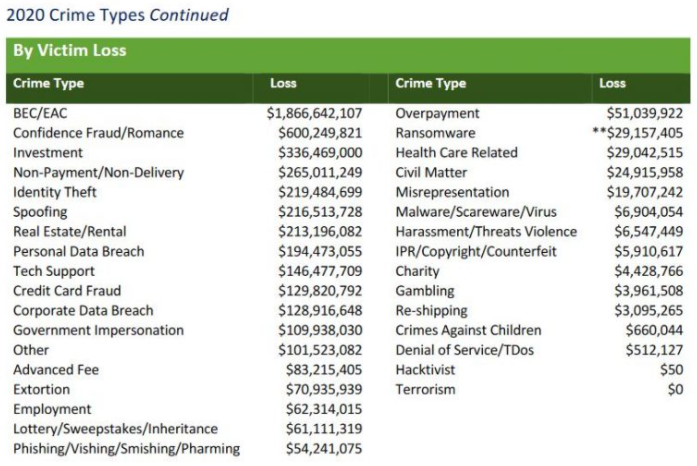
Image: FBI
“Knowing the actor is Nigerian really brings the entire story full circle and provides some notable context to the tactics used in the initial email we identified,” Hassold wrote. “For decades, West African scammers, primarily located in Nigeria, have perfected the use of social engineering in cybercrime activity.”
“While the most common cyber attack we see from Nigerian actors (and most damaging attack globally) is business email compromise (BEC), it makes sense that a Nigerian actor would fall back on using similar social engineering techniques, even when attempting to successfully deploy a more technically sophisticated attack like ransomware,” Hassold concluded.
DON’T QUIT YOUR DAY JOB
Cybercriminals trolling for disgruntled employees is hardly a new development. Big companies have long been worried about the very real threat of disgruntled employees creating identities on darknet sites and then offering to trash their employer’s network for a fee (for more on that, see my 2016 story, Rise of the Darknet Stokes Fear of the Insider).
Indeed, perhaps this enterprising Nigerian scammer is just keeping up with current trends. Several established ransomware affiliate gangs that have recently rebranded under new banners seem to have done away with the affiliate model in favor of just buying illicit access to corporate networks.
For example, the Lockbit 2.0 ransomware-as-a-service gang actually includes a solicitation for insiders in the desktop wallpaper left behind on systems encrypted with the malware.
“Would you like to earn millions of dollars? Our company acquires access to networks of various companies, as well as insider information that can help you steal the most valuable data of any company,” LockBit’s unusual ad reads. “You can provide us accounting data for the access to any company, for example, login and password to RDP, VPN, corporate email, etc. Open our letter at your email. Launch the provided virus on any computer in your company. Companies pay us the foreclosure for the decryption of files and prevention of data leak.”
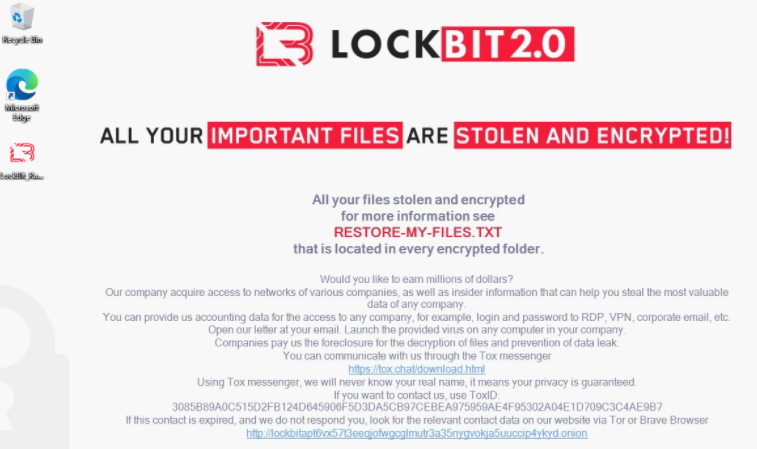
Image: Sophos.
Likewise, the newly formed BlackMatter ransomware gang kicked off its presence on the cybercrime forums with the unassuming thread, “Buying/monetizing your access to corporate networks.” The rest of the post reads:
We are looking for access to corporate networks in the following countries:
– the USA
– Canada
– Australia
– the UKAll lines of business except for:
– Healthcare
– Government entities.Requirements:
– Revenue according to ZoomInfo: over 100 million.
– Number of hosts: 500 to 15,000.
– We do not accept networks that anybody else has already tried to work on.Two options of cooperation:
– We buy networks: 3 to 100k.
– We monetize them (subject to negotiation on a case-by-case basis).How we work:
You select an option of cooperation. -> You provide access to the network. -> We check it. -> We take it or not (depending on whether it meets the requirements).




Nigeria, now their is a real backwards country, with a highly corrupt government
Necessity might be the mother of innovation, but Desperation is the cruel stepmother!
Holy Smokes. Proof of the inventiveness and brashness of people.
Though I have to say a fairly effective counter to this approach is to send such emails as a red herring to identify ‘at risk’ employees. That does open a potential can of worms in terms of terminations, but it’s better than having to pay ransomware.
This seems like a really brash/stupid approach, but the risk/reward calculation is different for this person than for you or I. It seems unlikely to succeed, but the risk is probably almost 0 for this person, I doubt they will be prosecuted in their country for attempting this. If they do it to enough people they might get a hit. It seems absurd because it’s not worth the risk for you because you are likely to get caught, but if there is an easy profitable crime where you won’t get caught in your country, a lot of people would do it (not that this is particularly easy, just that it could be the legal risk equivalent of burning a cd or downloading music in their country).
Those vigillantis might train employees how to deploy safely .
. invitations might be sent to personal emails or just links .
.and employees just open or execute back doors and simple wipe out codes .
.
.companies pay back times .??
.
——-
What a holLies..
.
. disgruntled emploYES now happy payback time .. employees love companies and companies hate them with vice versa .
. everyone tremble..??..
.
.join em nor beat em..
.
.
.
Interesting article. Makes me wonder whether vaccine mandates and other current challenges have increased the likelihood of this occurring… Curious how others are thinking about this…
Safe vaccine mandates don’t actually make people crazy, it merely gives existing crazies another excuse.
Wow, if anything was ever ripe for a high profile FBI sting operation this would be near the top of the list.
Hacker Facebook:
https://m.facebook.com/medayedupin.oluwaseun.5
“DemonWare ransomware strain, which is freely available on GitHub”. Does GitHub have no policy against criminal operations?
GitHub is a place to share code. Cyber security experts use the ransomware code to learn how to defend against it and Implement measures to stop it. Plus you can’t just run it like that they clearly add other stuff to make it get past antivirus signatures
Not really. Malicious code is still just a tool. I may use it for red team ops. And others for crime. The tool itself is just a tool.
In a lot of cases, the source code is leaked to Github in order to devalue any effort to sell the software.. This doesn’t change the SAAS approach much, but it does bring the issue to light.
There is no reason to ban something like this, it’s effectively the same as publishing vulnerabilities
How exactly you publish matters.
Not much we can do about crooks in Nigeria, but anyone state-side we catch, I hope at least a few years’ jail time!
Nigeria is next on the list as Afghanistan once was: all of the sudden ISIL BOKO HARAM appears and Mohammed Buhari would fly to London or meet his death in Abuja . US intel must look into Putin’security services GRU KGB and their Chinese cronies colluded with Mossad Netanyagu Bennett first, and not waste their operatives time on poor scammers and fraudsters like they did in my sensitive operations time in Colombia , arresting druglords fighting communist guerrillas and Soviet-Russian military Intelligence machine, instead of Masonry with its Zionist Presidents like Santos, Duque, Mickelsoen and you name it. Trump Kushner Pompeo Guillianni Flynn are more dangerous now than any poverty-stricken Nigerian scammer on line.
How ironic. This criminal begs you not to harm his fledgling company’s reputation. We can easily guess how he’d respond if a compromised business begged him for the decryption key following his successful insertion of a ransomware infection. Though it appears he wasn’t successful in pulling Mr. Hassold into the crime, it’s doubtful Medayedupin went from choir boy to ransomware distributor in one step.
This person’s actions need to be a permanent part of his online reputation so that any bank, customer, vendor, or other business can see in advance that Oluwaseun Medayedupin has a serious character flaw, and that he and his companies are not to be trusted.
Here’s a student profile and photo of Nigerian Oluwaseun Medayedupin: https://www.bangor.ac.uk/profiles/students/oluwaseun-medayedupin
That ransom statistic seems really skewed to the downside…29 millions? There were certain ransoms paid that were over 29m themselves in 1 pay….I think ransomware takes the cake. Its bad to correlate it like this but its kind of like rape. The corporation gets raped and is afraid to report it due to repercussions, embarrassment , legal ramifications and of course the backlash it will have on their stocks and or business in general. I think ransom payments far exceed any other crime because so many go unreported.
It’s very misleading to show the statistics and chart, but omit the HUGE CAVEAT right below.
Brian, can you PLEASE add:
“Regarding ransomware adjusted losses, this number does not include estimates of lost business, time, wages, files, or equipment, or any third-party remediation services acquired by a victim. In some cases, victims do not report any loss amount to the FBI, thereby creating an artificially low overall ransomware loss rate. Lastly, the number only represents what victims report to the FBI via the IC3 and does not account for victim direct reporting to FBI field offices/agents. “
“misleading” if you don’t consider those things completely obvious yet also unknowable.
We desperately need secure digital services. Digital services are often the only way for people to use the economic system or stay connected with family. That means that all people need to be able to use them safely, not just people sophisticated enough to understand security. My mom is 86 years old and my brother and I try but there is no way we can make her computer literate enough to follow all the advice from security professionals. Expecting a population with an average reading level around 8th grade to develop the necessary skills to prevent highly motivated crooks who are experts in the technology from breaking into networks is absurd.
The insider threat is another problem. If people can’t be bought they can be blackmailed. A hacker who has obtained enough access to a person’s computer to download or encrypt files can also upload files. Uploading incriminating material and then threatening to contact law enforcement unless the person facilitates a network intrusion at their work is just a digital version of what spy agencies did to turn agents during the Cold War. For that matter encrypting the person’s hard drive and making the price of decryption clicking on a link in an email on their work computer is a simpler option.
Punishment is not going to work either. Going after these criminals is like going after drug dealers. Put one away and two more take his place. The financial rewards are too great. Many of them live in jurisdictions that protect them from legal consequences. And while it may sound good to some people to think about using missles, bombs, or special forces to take the crooks out, those also kill innocent people, put US servicemen at risk, and cost far more in the long run than just taking the losses to the criminals. We spent over $1,000,000,000,000 in Afghanistan and it would take about 500 years to lose that much money to crooks at the current rate.
We need to retool our whole way of thinking about digital information. For example, the ad-based revenue system relies on surveillance which leads to security holes. Perhaps if we spent less money invading other countries then we would be able to rebuild our physical and digital infrastructure with security as a foundation instead of as an add-on.
You, good sir, are a hopeless romantic!
Where can I vote for you?
LOL.. you are living in an ideal dream world that doesn’t exist and won’t.
The main reason why security is not implemented into software, hardware across the board is:
1. Profits before security.
2. CIA, NSA, CCP, Mossad any other nation state ABC, XYZ would not have it any other way.. its all built by design to be insecure.
Here is what you do for mom, mema, or any elderly that needs or wants internet access.
Buy them an ipad, configure the wifi setup and let them go bananas. If it gets hacked reimage and start again.
Who knows even their learning curve might up tick to realize how bad the wild internet really is.
P.s dont forget to disable credit card store feature. Have fun.
Agreed, we need secure digital services and as time goes by technology will only continue to improve and along with it, its security can be difficult to maintain because just as tech improves so does better programs and ways of attacking it.
Very fair points, but you ignored the main factor, why this cannot happen at all, our governments! All the money spend to ‘spy’ on everybody possible, even own citizens, but this isn’t good enough to protect those people, who pay for that?
This is by design and easy to reduce a lot, make software vendors liable for unsecure software! No matter if it is an operating system, some tool, as long as there is money made with it, hit them hard! Just the same as car companies, they had to be forced to make their products safe to use, why not doing just the same with the IT industry?
Go and call your congressmen for something useful for once and ask them, why this is not cemented into law already, the answers certainly are hilarious!
What a holLies..2.
.
. disgruntled emploYES now happy payback time .. employees love companies and companies hate them with vice versa .
. everyone tremble..??..
.
.join em nor beat em..
.
.
Interesting… And the likelihood of the disgruntled employee actually being caught and prosecuted or sued is significantly lower if they use a modicum of misdirection, negotiate the sharing agreement from non-corporate systems, and then simply click on an apparent phishing link to start the ball rolling.
History repeats himself.
If you read about spies during the cold war, most spies of both sides were both recruited because they were unhappy in their job. Some did it for ideological reasons, but the majority did it because they think they deserve better from their employer, either being not paid enough or thinking they deserve to do a better job.
Keep your employees happy or shackle them… :D.
Seems like the smart thing for corporate CyberSec teams to do is to let rumors slip out that they themselves are phishing people in the company with these messages, and anyone caught replying will be summarily fired. Let that rumor get out there, let it fester. Do it for real, and fire people for it. It sounds harsh, but it may be the only preventative medicine for this kind of ‘inside job’ temptation.
Also – Least Privileged Access, cordoning off valuable info inside the network, and monitoring for ransomeware activity will help slow these attacks once they do have a beachhead.
The problem is a natural opportunity for hackers that are looking people in the service industry. Technology is filled with service people. That would include code cutters down to retail sales persons selling the newest iPhone contracts with SIM numbers.
I was talking to an auditor of the service industry and in particular the retail sales industry.He said about 80 percent of all retail theft was from the inside persons of large stores and 20 percent theft from outside shoplifters. So, hackers looking for disgruntled employees in the technology field would be a natural thing. It’s that one employee who got a bad performance review or a merger of two companies where duplicate staff are going to be dismissed upon consummation of a merger that can trigger somebody to snag a data base backup and sell it hackers before being she or he is “let go”. You would be surprised at how often that problem happens. Technology is very fast moving and competitive. The “insider threat” or fancy name for a soon to be fired employee should be ranked higher than the Sha1 v. Sha2 style of technology risk.
This article is not correct
https://abnormalsecurity.com/blog/nigerian-ransomware-soliciting-employees-demonware/
This man is crazy, Brian Krebs is Mad
Hi Oluwaseun!
What a dumb skid. Even if he were to find some employee, his open source PYTHON ransomware isn’t going to get far.
“BlackKingdom ransomware … does indeed encrypt files. They exclude c:\windows, however my storage drivers were in a different folder and it encrypted those… meaning the server doesn’t boot any more. If you’re reading BlackKingdom, exclude *.sys files” — Kevin Beaumont (@GossiTheDog)
They even outsource QA
Kreb’s Story is Framed up
https://abnormalsecurity.com/blog/nigerian-ransomware-soliciting-employees-demonware/
Hassold did a good job in exposing such a criminal hacker wanting to take advantage of a disgruntled employee, and sometimes greedy employees who might fall for such scam. This is why organizations are strongly encouraged to invest in the training of their employees particularly in the area of Information security. Such training would help employees to protect company’s data and its clients data. It would also make employees knowledgeable on social engineering techniques normally used by cyber criminals. Employee awareness is very key and goes a long way in preventing social engineering attacks.