The U.S. Department of Justice today announced the arrest of Ukrainian man accused of deploying ransomware on behalf of the REvil ransomware gang, a Russian-speaking cybercriminal collective that has extorted hundreds of millions from victim organizations. The DOJ also said it had seized $6.1 million in cryptocurrency sent to another REvil affiliate, and that the U.S. Department of State is now offering up to $10 million for the name or location any key REvil leaders, and up to $5 million for information on REvil affiliates.
If it sounds unlikely that a normal Internet user could make millions of dollars unmasking the identities of REvil gang members, take heart and consider that the two men indicted as part this law enforcement action do not appear to have done much to separate their cybercriminal identities from their real-life selves.
Exhibit #1: Yaroslav Vasinskyi, the 22-year-old Ukrainian national accused of being REvil Affiliate #22. Vasinskyi was arrested Oct. 8 in Poland, which maintains an extradition treaty with the United States. Prosecutors say Vasinskyi was involved in a number of REvil ransomware attacks, including the July 2021 attack against Kaseya, a Miami-based company whose products help system administrators manage large networks remotely.

Yaroslav Vasinksyi’s Vkontakte profile reads “If they tell you nasty things about me, believe every word.”
According to his indictment (PDF), Vasinskyi used a variety of hacker handles, including “Profcomserv” — the nickname behind an online service that floods phone numbers with junk calls for a fee. Prosecutors say Vasinskyi also used the monikers “Yarik45,” and “Yaroslav2468.”
These last two nicknames correspond to accounts on several top cybercrime forums way back in 2013, where a user named “Yaroslav2468” registered using the email address yarik45@gmail.com.
That email address was used to register an account at Vkontakte (the Russian version of Facebook/Meta) under the profile name of “Yaroslav ‘sell the blood of css’ Vasinskyi.” Vasinskyi’s Vkontakte profile says his current city as of Oct. 3 was Lublin, Poland. Perhaps tauntingly, Vasinskyi’s profile page also lists the FBI’s 1-800 tip line as his contact phone number. He’s now in custody in Poland, awaiting extradition to the United States.
Exhibit #2: Yevgeniy Igorevich Polyanin, the 28-year-old Russian national who is alleged to be REvil Affiliate #23. The DOJ said it seized $6.1 million in funds traceable to alleged ransom payments received by Polyanin, and that the defendant had been involved in REvil ransomware attacks on multiple U.S. victim organizations.
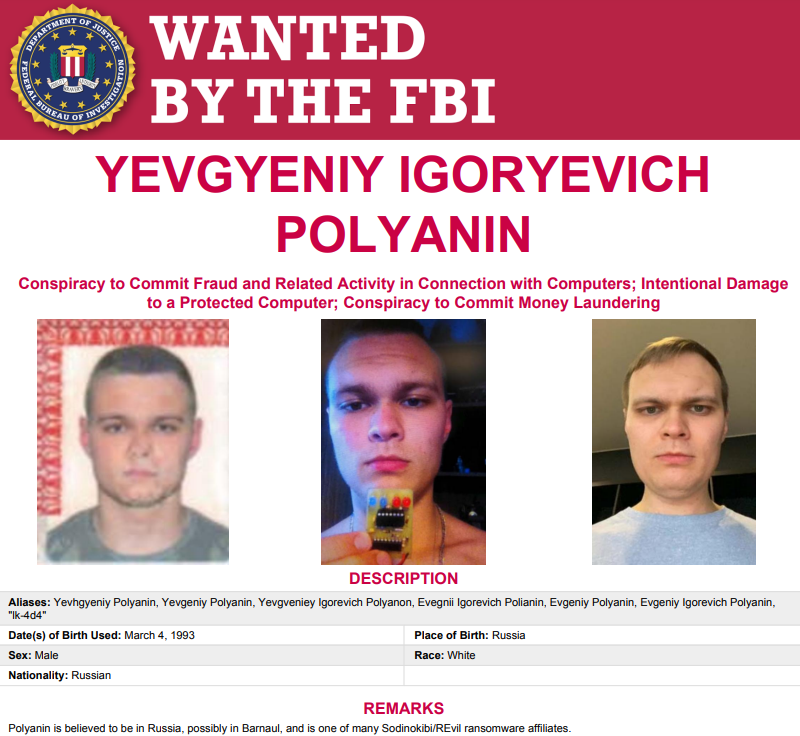
The FBI’s wanted poster for Polyanin.
Polyanin’s indictment (PDF) says he also favored numerous hacker handles, including LK4D4, Damnating, Damn2life, Noolleds, and Antunpitre. Some of these nicknames go back more than a decade on Russian cybercrime forums, many of which have been hacked and relieved of their user databases over the years.
Among those was carder[.]su, and that forum’s database says a user by the name “Damnating” registered with the forum in 2008 using the email address damnating@yandex.ru. Sure enough, there is a Vkontakte profile tied to that email address under the name “Yevgeniy ‘damn’ Polyanin” from Barnaul, a city in the southern Siberian region of Russia.
The apparent lack of any real operational security by either of the accused here is so common that it is hardly remarkable. As exhibited by countless investigations in my Breadcrumbs story series, I have found that if a cybercriminal is active on multiple forums over more than 10 years, it is extremely likely that person has made multiple mistakes that make it relatively easy to connect his forum persona to his real-life identity.
As I explained earlier this year in The Wages of Password Re-use: Your Money or Your Life, it’s possible in many cases to make that connection thanks to two factors. The biggest is password re-use by cybercriminals (yes, crooks are lazy, too). The other is that cybercriminal forums, services, etc. get hacked just about as much as everyone else on the Internet, and when they do their user databases can reveal some very valuable secrets and connections.
In conjunction with today’s REvil action, the U.S. Department of State said it was offering a reward of up to $10 million for information leading to the identification or location of any individual holding a key leadership position in the REvil ransomware group. The department said it was also offering a reward of up to $5 million for information leading to the arrest and/or conviction in any country of any individual conspiring to participate in or attempting to participate in a REvil ransomware incident.
I really like this bounty offer and I hope we see more just like it for other ransomware groups. Because as we can see from the prosecutions of both Polyanin and Vasinskyi, a lot of these guys simply aren’t too hard to find. Let the games begin.




Sounds like you just threw the red meat into a bunch of hungry hounds. Good move.
But if it’s that easy why the 10 million reward? It’s the government lazy too?
Quite often law enforcement is bound by legislation which doesn’t allow them to use the same data sources as private individuals. Especially when nobody has been named as a suspect.
Also, for this amount of money, people might be pushed to rat out their friends, forum owners might be willing to release information, etc.
learn the term parallel construction
I heard that some folks from Russia are so long doing penetration testing – legal ones, with contract signed, clients assuming all civil/adm./criminal/etc.. liabilities – for a variety of firms, that if it ONLY STARTED WITH RANSOMWARE, federal folks are certainly missing a LOT of things.
I am not from Russia.
Parallel construction does not apply in most sane countries. UK/USA excluded from the list, of course.
Learn the term Fruit of the poisonous tree.
Learn the term Fruit of the poisonous tree
The thing is, it avoids that issue entirely “if” it’s entirely parallel,
there is no “absolute documentation” step of how they find out.
Don’t mention the tree, fruit was on the ground by itself, boom.
“observed in plain sight” applies, it is that.
The “real” backstory is way harder to prove unless documented,
even then it’s extremely uphill just to get there, and then prove it.
There is an individual who has been cleared of his crimes for
many months, having spent decades in jail, who is being held
ongoing only because the governor doesn’t want to sign off.
For politics. Hang a hat on any 1 legal precept at own peril.
Single judges to entire Courts run the gamut from good to else.
Four thumbs up for this post. You hit the nail on the head with both of your points
For this amount of money, stupid people (grandmas, adolescents, private detectives, etc..) do unlawful things, mess up with the wrong and dangerous fellas, ending up facing real-world consequences and/or lawsuits.
Its the renewed Wild-West of the internet, with reward posters, real bullets and all.
Slavik is still out there, so we know smart folks continue to produce code, with or without rewards.
Let the dangerous games begin.
So, you’re saying that you’ve traced these international hackers back to the online accounts they created when they were 14 and 15 years old?
Well most hackers don’t start in their 20s. It starts small when they are younger and by the time they are in their 20s they have 5+ years of practical experiences. Truthfully and as bad as that sounds they are more ready for their carrier as a criminal then most kids who finish college.
As old as time, most all crooks have enemies, and what a pleasure for some to rat on their most hated.
With all the infor you turn up…maybe someone can turn that into the bounty 🙂
…yes, but don’t get too excited – over time revil has extorted hundreds of $ millions – DOJ got just $6m…
I really like the reward strategy too Brian. I think it will prove effective, not only to finger more bad actors, but also as deterrence. Arrests and rewards increase the risk equation for cybercriminals, many of whom could desist and get a proper job relatively easily, if they have not yet been indicted, implicated, etc.
Question and observation.
Is anyone aware of any major cybercriminal who’s done a good and careful job of keeping her/her identity secret over a period of more than, say, two years?
Here’s a quote from the 1920s by Dashiell Hammett, author of “The Maltese Falcon,” who was a very successful detective with the Pinkerton organization before he took up writing. The speaker is a police detective talking about a young, up-and-coming stickup artist–not a cybercriminal–there may be differences.
“He ain’t hampered by nothing like imagination.or fear of consequences. I wish he was. It’s those careful, sensible birds that are easiest caught.”
Criminals who are very good at keeping their identity secret, are also very good at keeping their crimes off the radar too.
So, there are many major cybercriminals who aren’t yet identified. And many cyber crimes that are not correctly attributed too. Often a major attack is blamed on a nation-state, and it may be the wrong country entirely, or a different group responsible.
Ego is often the downfall, as cybercrimals who want to take credit for something major, obviously put a target on their backs and don’t last long. Ransomware in particular, since it requires being identified so they can get paid, is hard to keep entirely in the shadows.
But keep in mind, the better cybercriminals, remain hidden, precisely because their better at staying hidden.
slavik made millions for years before anybody knew his identity
Brian, you are as well positioned and capable as anyone for tracking down these criminals for the reward, and then writing about it too. You must be really smiling now. I think the reward offer of such a huge amount of cash will be getting a lot of researchers juices working. Maybe a dent can be made in the ransomware industry and some retribution handed out to some people who really deserve it. I look forward to reading how you “cracked” some of the case(s) in the future.
So how much did the people that turned these two in, receive? They couldn’t have received $5 million each, could they?
Great article! I realized these are my favorite kinds of GI articles. Enough news and reviews, more stuff like this! Let the writers get creative!