Rarely do cybercriminal gangs that deploy ransomware gain the initial access to the target themselves. More commonly, that access is purchased from a cybercriminal broker who specializes in acquiring remote access credentials — such as usernames and passwords needed to remotely connect to the target’s network. In this post we’ll look at the clues left behind by “Babam,” the handle chosen by a cybercriminal who has sold such access to ransomware groups on many occasions over the past few years.

Since the beginning of 2020, Babam has set up numerous auctions on the Russian-language cybercrime forum Exploit, mainly selling virtual private networking (VPN) credentials stolen from various companies. Babam has authored more than 270 posts since joining Exploit in 2015, including dozens of sales threads. However, none of Babam’s posts on Exploit include any personal information or clues about his identity.
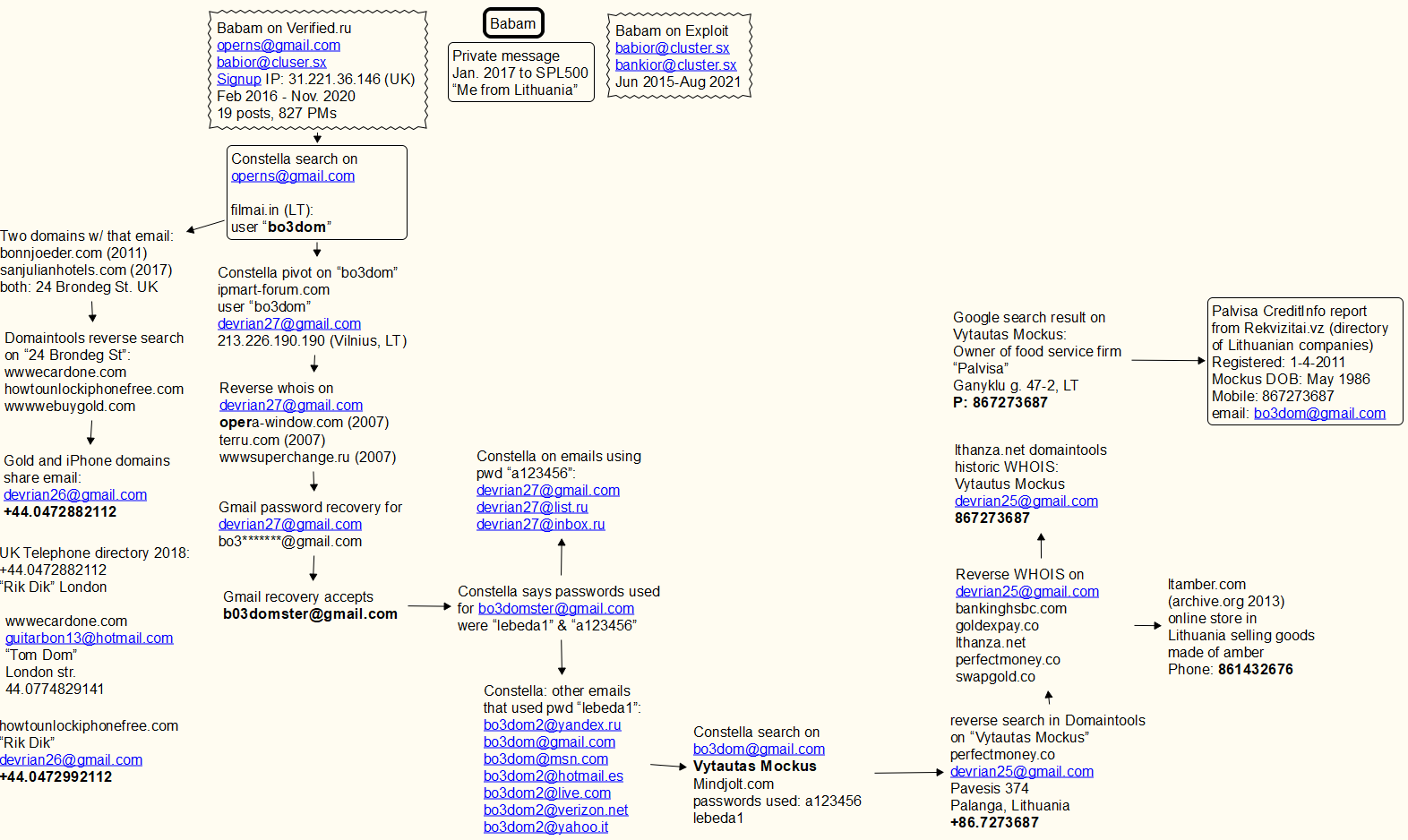
But in February 2016, Babam joined Verified, another Russian-language crime forum. Verified was hacked at least twice in the past five years, and its user database posted online. That information shows that Babam joined Verified using the email address “operns@gmail.com.” The latest Verified leak also exposed private messages exchanged by forum members, including more than 800 private messages that Babam sent or received on the forum over the years.
In early 2017, Babam confided to another Verified user via private message that he is from Lithuania. In virtually all of his forum posts and private messages, Babam can be seen communicating in transliterated Russian rather than by using the Cyrillic alphabet. This is common among cybercriminal actors for whom Russian is not their native tongue.
Cyber intelligence platform Constella Intelligence told KrebsOnSecurity that the operns@gmail.com address was used in 2016 to register an account at filmai.in, which is a movie streaming service catering to Lithuanian speakers. The username associated with that account was “bo3dom.”
A reverse WHOIS search via DomainTools.com says operns@gmail.com was used to register two domain names: bonnjoeder[.]com back in 2011, and sanjulianhotels[.]com (2017). It’s unclear whether these domains ever were online, but the street address on both records was “24 Brondeg St.” in the United Kingdom. [Full disclosure: DomainTools is a frequent advertiser on this website.]
A reverse search at DomainTools on “24 Brondeg St.” reveals one other domain: wwwecardone[.]com. The use of domains that begin with “www” is fairly common among phishers, and by passive “typosquatting” sites that seek to siphon credentials from legitimate websites when people mistype a domain, such as accidentally omitting the “.” after typing “www”.

A banner from the homepage of the Russian language cybercrime forum Verified.
Searching DomainTools for the phone number in the WHOIS records for wwwecardone[.]com — +44.0774829141 — leads to a handful of similar typosquatting domains, including wwwebuygold[.]com and wwwpexpay[.]com. A different UK phone number in a more recent record for the wwwebuygold[.]com domain — 44.0472882112 — is tied to two more domains – howtounlockiphonefree[.]com, and portalsagepay[.]com. All of these domains date back to between 2012 and 2013.
The original registration records for the iPhone, Sagepay and Gold domains share an email address: devrian26@gmail.com. A search on the username “bo3dom” using Constella’s service reveals an account at ipmart-forum.com, a now-defunct forum concerned with IT products, such as mobile devices, computers and online gaming. That search shows the user bo3dom registered at ipmart-forum.com with the email address devrian27@gmail.com, and from an Internet address in Vilnius, Lithuania.
Devrian27@gmail.com was used to register multiple domains, including wwwsuperchange.ru back in 2008 (notice again the suspect “www” as part of the domain name). Gmail’s password recovery function says the backup email address for devrian27@gmail.com is bo3*******@gmail.com. Gmail accepts the address bo3domster@gmail.com as the recovery email for that devrian27 account.
According to Constella, the bo3domster@gmail.com address was exposed in multiple data breaches over the years, and in each case it used one of two passwords: “lebeda1” and “a123456“.
Searching in Constella for accounts using those passwords reveals a slew of additional “bo3dom” email addresses, including bo3dom@gmail.com. Pivoting on that address in Constella reveals that someone with the name Vytautas Mockus used it to register an account at mindjolt.com, a site featuring dozens of simple puzzle games that visitors can play online.
At some point, mindjolt.com apparently also was hacked, because a copy of its database at Constella says the bo3dom@gmail.com used two passwords at that site: lebeda1 and a123456.
A reverse WHOIS search on “Vytautas Mockus” at DomainTools shows the email address devrian25@gmail.com was used in 2010 to register the domain name perfectmoney[.]co. This is one character off of perfectmoney[.]com, which is an early virtual currency that was quite popular with cybercriminals at the time. The phone number tied to that domain registration was “86.7273687“.
A Google search for “Vytautas Mockus” says there’s a person by that name who runs a mobile food service company in Lithuania called “Palvisa.” A report on Palvisa (PDF) purchased from Rekvizitai.vz — an official online directory of Lithuanian companies — says Palvisa was established in 2011 by a Vytautaus Mockus, using the phone number 86.7273687, and the email address bo3dom@gmail.com. The report states that Palvisa is active, but has had no employees other than its founder.
Reached via the bo3dom@gmail.com address, the 36-year-old Mr. Mockus expressed mystification as to how his personal information wound up in so many records. “I am not involved in any crime,” Mockus wrote in reply.
The domains apparently registered by Babam over nearly 10 years suggest he started off mainly stealing from other cybercrooks. By 2015, Babam was heavily into “carding,” the sale and use of stolen payment card data. By 2020, he’d shifted his focus almost entirely to selling access to companies.
A profile produced by threat intelligence firm Flashpoint says Babam has received at least four positive feedback reviews on the Exploit cybercrime forum from crooks associated with the LockBit ransomware gang.
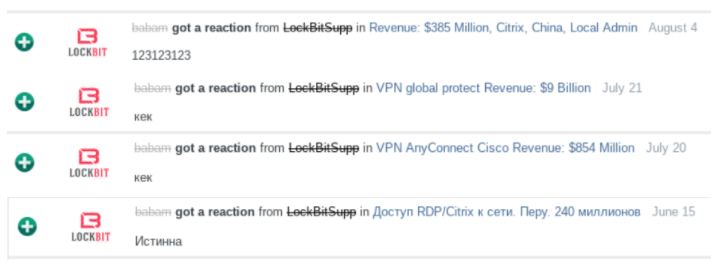
The ransomware collective LockBit giving Babam positive feedback for selling access to different victim organizations. Image: Flashpoint
According to Flashpoint, in April 2021 Babam advertised the sale of Citrix credentials for an international company that is active in the field of laboratory testing, inspection and certification, and that has more than $5 billion in annual revenues and more than 78,000 employees.
Flashpoint says Babam initially announced he’d sold the access, but later reopened the auction because the prospective buyer backed out of the deal. Several days later, Babam reposted the auction, adding more information about the depth of the illicit access and lowering his asking price. The access sold less than 24 hours later.
“Based on the provided statistics and sensitive source reporting, Flashpoint analysts assess with high confidence that the compromised organization was likely Bureau Veritas, an organization headquartered in France that operates in a variety of sectors,” the company concluded.
In November, Bureau Veritas acknowledged that it shut down its network in response to a cyber attack. The company hasn’t said whether the incident involved ransomware and if so what strain of ransomware, but its response to the incident is straight out of the playbook for responding to ransomware attacks. Bureau Veritas has not yet responded to requests for comment; its latest public statement on Dec. 2 provides no additional details about the cause of the incident.
Flashpoint notes that Babam’s use of transliterated Russian persists on both Exploit and Verified until around March 2020, when he switches over to using mostly Cyrillc in his forum comments and sales threads. Flashpoint said this could be an indication that a different person started using the Babam account since then, or more likely that Babam had only a tenuous grasp of Russian to begin with and that his language skills and confidence improved over time.
Lending credence to the latter theory is that Babam still makes linguistic errors in his postings that suggest Russian is not his original language, Flashpoint found.
“The use of double “n” in such words as “проданно” (correct – продано) and “сделанны” (correct – сделаны) by the threat actor proves that this style of writing is not possible when using machine translation since this would not be the correct spelling of the word,” Flashpoint analysts wrote.
“These types of grammatical errors are often found among people who did not receive sufficient education at school or if Russian is their second language,” the analysis continues. “In such cases, when someone tries to spell a word correctly, then by accident or unknowingly, they overdo the spelling and make these types of mistakes. At the same time, colloquial speech can be fluent or even native. This is often typical for a person who comes from the former Soviet Union states.”




I always appreciate the journalistic quality of your work. Thanks for the great read.
Agreed, I’m always amazed by the way you pull so many diverse threads together, weaving them into a complete image. Thanks Brian, another excellent read.
some boring BS – who cares, Brian
Then don’t read it. Video games are on, run along.
Just the grown-ups care
I think this guy really may be asking, (albeit in a snide way), which facts are significant, why, what conclusions we may come to, (or shouldn’t), and anything in the way of advice, based on the article. Usually, I figure out what’s valuable. In this case, I read half, skimmed the rest, and hoped gain my answers from some of your comments and reactions. Even if not, treat your comments like we could use your help with your take away.
Basically, Brian showed that the criminal Babam is probably Vytautas Mockus from Lithuania.
that man clearly said he does not do any crime
@neils – thanks for the good laugh… you made my day!
Hey Mr SnarkyXman,
Apparently you do, by reading KOS and then commenting. Kinda comes across as someone who cares.
Perhaps you’ve made some of these same opsec mistakes over time and feel just a little uneasy, especially since you can’t really cover your tracks very easily after the fact?
So you really should care, if you don’t already.
The techniques used seem the most interesting part to me.
A former forum admin I used to know was surprisingly good with understanding and using the Russian language and it always made me curious. The guy was older and a former coal miner in Scotland turn IT pro. Russia supported UK miners when they had a big strike back when Russia was still the USSR and because of that, and the support his family got, he learned the language. An older dude from Fife Scotland would be the last person I’d have suspected of knowing Russian. But he also became a firm believer in communist and that drove him to go on Russian hacker forums and do some pretty shady stuff to, as he saw it, get back at all the corrupt and greedy capitalists.
I lost touch with the guy but I always wondered if he ever got caught. He had decent opsec for a civilian and kept a low enough profile not to be important enough to monitor for espionage, but he was a committed ideolog and eventually that sort of thing will get you noticed…
“I am not involved in any crime, Mockus wrote in reply” Ya right, deny everything !
“Vytautas Mockus (b 10-9-57 in Kupiškis ) is an economist , Lithuanian cooperative and political figure.”
wiki/Vytautas_Mockus
There is more than 1 person with that name, Krebs found this person through the back-channel # etc,
but what if ‘somehow’ actors gained access to email @ for purposes of using the identity as fall guy?
‘Possibly’ they need a capability to intercept phone# too theoretically but that’s not quite impossible.
If they have him wide open they could do setup through him as scammers do with comped accounts.
Of course it’s a convenient hand-wave defense also, but how to determine w/o access to the system?
Or better, sloppy opsec on the front end as a double-front, which they themself “hack” into remotely for
scent-throwing opsec artifacts? Reuse crap passwords as plausible landscape, etc, VPN, TOR, CafeLan.
I’m sure most who get caught like this are just crap opsec careless scammers but … is it possible?
Would there be any way of _ethically_ investigating such without physical help from local authorities?
Wondering, why forum admins does not encrypt all messages/posts and other sensitive information. It is very trivial to do, as decryption can be made with some well protected key. Cracking forums without any secops or just care to take active measures to evade. That’s frightening.
Non-the-less, I live in Lithuania and cyber crime here is uncommonly hitting yellow portal headlines. Pleasure to read it on krebs.
“well protected key” <– therein lies the secret. How to make a well protected key?
Nice job, Brian. Once again you show how very simple techniques of correlating public info can lead to interesting discoveries.
What I was thinking though is: law enforcement _should_ be doing this, and they can do so much more by e.g. subpoenaing records from gmail, etc. Google already has all this info: they probably already grouped together all these email accounts the guy used, they have his IP addresses and geolocation already. They also have all his email messages. The thing is: all this stuff, all these opsec errors people make, it’s not going away, it lives on in the cloud somewhere until sombody begins digging. And then one day, when you’re on vacation in Spain or Italy there comes a knock on your door… Seriously dudes, good advice: limit your vacationing to Nigeria and places like that.
Most of these guys become complacent after a few years of being in the game. You begin to feel invincible.
Amazing investigative work – and thank you for sharing how each step was performed!
Was the email “bo3domster@gmail.com” found by guessing the “ster” suffix? If so, roughly how many guesses did it take to find it out?
Kind of worked backwards into the recovery email. But that is where finding identical passwords helps.
Why investigating about this particular individual ?
Brian Krebs is a journalist and he writes about Internet (cyber) crime. Since Babam is the type of person Brian Krebs writes about because Babam is a criminal who sells access to organization’s networks.
Thanks for this Brian. Your workflows and explanations for these kinds of deep dives have helped a lot of people break into the investigative side of threat intelligence.
Well done, Brian!
It always amazes me that so many hackers use lousy passwords for their own accounts. Perhaps their solipsism and selfishness that prevents them from feeling and caring about victims also prevents them from realizing their own exposure.
The apt cliche “a spider caught in its own web” transitioned well to modern times.
I always find these ‘breadcrumb’ stories fascinating, showing ever well people think they are covering their tracks a trail always exists. One of the first books I read when entering IS and computer audit many (many) years ago was ‘The cuckoos egg’ by Cliff Stoll. For anyone who is not familiar with it, it’s well worth a read.
There are ways, the people reported on are for failing more than not.
Hess was one of the first, certainly not the uber example of subterfuge,
his story is illustrative in that he used classic methods, default pw, etc,
but that was plenty enough to have a legit career in full on espionage.
That was the 80’s. Has even this problem been secured? Not really.
It’s amazing how far you can get with OSINT.
Are there tools for this? (from name/email/phone/website plus some typical adjustments like the www hack, lookup on every database known, repeat with new info, and iterate until done? Then automatically map it?)
OSINT = open source intelligence. Getting stuff without using secret databases or human sources.
Good article. Informative. To the doubters, identity theft has been around since there’s been identity. It may be the third oldest profession. And the logic tree is good as far as it goes. Now the “he” is exposed. Now, let’s see what happens next. Grab the popcorn.
I love Brian’s work and like everyone else here i check his site daily to make sure my own organization isn’t the topic of one of his articles – but that being said – the reason why Brian can do this and most of us can’t is not because this requires any particular skill but because he has access to the tools that most security teams might be lucky to have even one of them.
First off, Domain Tools. Awesome. I can only dream my company would purchase that for my team. Incredibly expensive and hard to justify because as awesome as it is it’s only going to be utilized those few times a year you may need it. This actually applies to almost all the tools Brian has access to.
Constella Intelligence has a service that apparently lets customer search through databases that have been hacked – for sure some of them were never really easily accessible by the public but being able to search through the history of essentially what could be considered a search engine for “haveibeenpwned.com” by password or location is kick ass and can only dream of having that kind of functionality at my disposal but who wants to guess how much a service contract with Constella is gonna cost your company (forget about these services if you are an individual – unless you are filthy rich or you happy to be Iron Man)?
I can speak about Flashpoint from personal experience because my current employer is a customer. Can’t say enough good things about them – great intelligence source for augmenting your own internal business intelligence. But even when you have access to some of these tools there are additional paywalls you’ll hit… For example, I was so excited that my company was getting Flashpoint because I wanted to use their Maltego transform. Was gonna be sweet! Wait… what? I can’t use the opensource version of Maltego because you made your transform only available to the Enterprise version of Maltego? And why exactly? So ya… the web interface is nice and yada yada but anywhoodles you get the point.
I can guarantee you that all three of the vendors above offer full functionality and access to Brian – and so they should – what a great way to advertise their products and what a great way for Brian to get the resources he needs to do kick ass (and let’s be honest – fun as hell – because at the end of the day exposing bad guys and putting a face to the 0s and 1s must be tremendously satisfying!) investigations.
How many other tools are provided by other vendors to Brian. In all seriousness – the answer is probably – ALL OF THEM. I mean, I’m sure it just comes down to Brian asking for access.
I will admit – despite working in IT security for almost 10 years now (and thankful I have a job I like) I’ve always had two dream jobs I’d take in a heartbeat… 1. A job in a research lab where I get paid to learn (not just any place – but like somewhere that people like Van Jacobson or Linus Torvalds hang out just because having their names associated with your facility is cool so it’s worth paying them millions to essential play with a big budget to support whatever they can imagine that day) and 2. What Brian does. Well, not just what Brian does – but what Brian does with all the resources at his disposal. Lots of people are doing what Brian does but will never be as effective because those tools are freakin’ expensive and most security teams are lucky if they can get executive management to sign up for even one of them.
Sorry for typos and grammar.
This is precisely the kind of article that helps make this world a better place by shedding some light on all those shady actors that love to operate from the dark. Hopefully one more criminal who will have lots of time on his hands to think about his life-choices.
the journalistic quality of this report is the kind of thing i like to read. Thanks for the details
Brian is the Adrian Monk of cryptosleuthing.
@Marco Thanks for summarizing the tools used. Very interesting.