The U.S. Drug Enforcement Administration (DEA) says it is investigating reports that hackers gained unauthorized access to an agency portal that taps into 16 different federal law enforcement databases. KrebsOnSecurity has learned the alleged compromise is tied to a cybercrime and online harassment community that routinely impersonates police and government officials to harvest personal information on their targets.
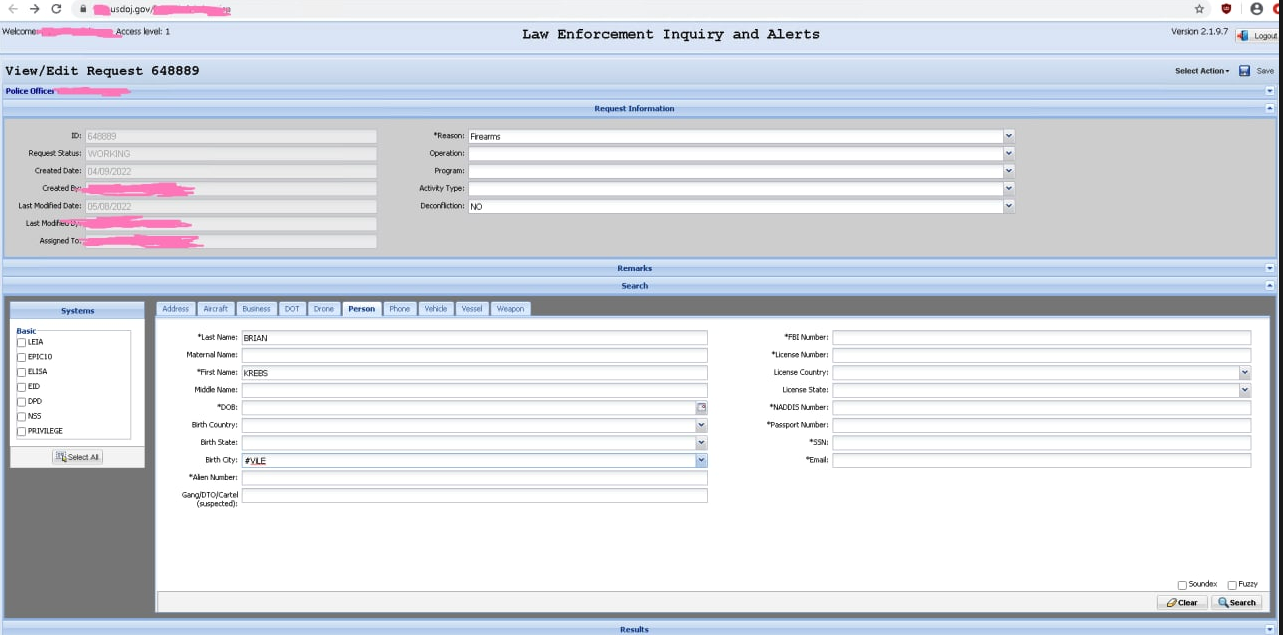
Unidentified hackers shared this screenshot of alleged access to the Drug Enforcement Administration’s intelligence sharing portal.
On May 8, KrebsOnSecurity received a tip that hackers obtained a username and password for an authorized user of esp.usdoj.gov, which is the Law Enforcement Inquiry and Alerts (LEIA) system managed by the DEA.
KrebsOnSecurity shared information about the allegedly hijacked account with the DEA, the Federal Bureau of Investigation (FBI), and the Department of Justice, which houses both agencies. The DEA declined to comment on the validity of the claims, issuing only a brief statement in response.
“DEA takes cyber security and information of intrusions seriously and investigates all such reports to the fullest extent,” the agency said in a statement shared via email.
According to this page at the Justice Department website, LEIA “provides federated search capabilities for both EPIC and external database repositories,” including data classified as “law enforcement sensitive” and “mission sensitive” to the DEA.
A document published by the Obama administration in May 2016 (PDF) says the DEA’s El Paso Intelligence Center (EPIC) systems in Texas are available for use by federal, state, local and tribal law enforcement, as well as the Department of Defense and intelligence community.
EPIC and LEIA also have access to the DEA’s National Seizure System (NSS), which the DEA uses to identify property thought to have been purchased with the proceeds of criminal activity (think fancy cars, boats and homes seized from drug kingpins).
“The EPIC System Portal (ESP) enables vetted users to remotely and securely share intelligence, access the National Seizure System, conduct data analytics, and obtain information in support of criminal investigations or law enforcement operations,” the 2016 White House document reads. “Law Enforcement Inquiry and Alerts (LEIA) allows for a federated search of 16 Federal law enforcement databases.”
The screenshots shared with this author indicate the hackers could use EPIC to look up a variety of records, including those for motor vehicles, boats, firearms, aircraft, and even drones.
Claims about the purloined DEA access were shared with this author by “KT,” the current administrator of the Doxbin — a highly toxic online community that provides a forum for digging up personal information on people and posting it publicly.
As KrebsOnSecurity reported earlier this year, the previous owner of the Doxbin has been identified as the leader of LAPSUS$, a data extortion group that hacked into some of the world’s largest tech companies this year — including Microsoft, NVIDIA, Okta, Samsung and T-Mobile.
That reporting also showed how the core members of LAPSUS$ were involved in selling a service offering fraudulent Emergency Data Requests (EDRs), wherein the hackers use compromised police and government email accounts to file warrantless data requests with social media firms, mobile telephony providers and other technology firms, attesting that the information being requested can’t wait for a warrant because it relates to an urgent matter of life and death.
From the standpoint of individuals involved in filing these phony EDRs, access to databases and user accounts within the Department of Justice would be a major coup. But the data in EPIC would probably be far more valuable to organized crime rings or drug cartels, said Nicholas Weaver, a researcher for the International Computer Science Institute at University of California, Berkeley.
Weaver said it’s clear from the screenshots shared by the hackers that they could use their access not only to view sensitive information, but also submit false records to law enforcement and intelligence agency databases.
“I don’t think these [people] realize what they got, how much money the cartels would pay for access to this,” Weaver said. “Especially because as a cartel you don’t search for yourself you search for your enemies, so that even if it’s discovered there is no loss to you of putting things ONTO the DEA’s radar.”
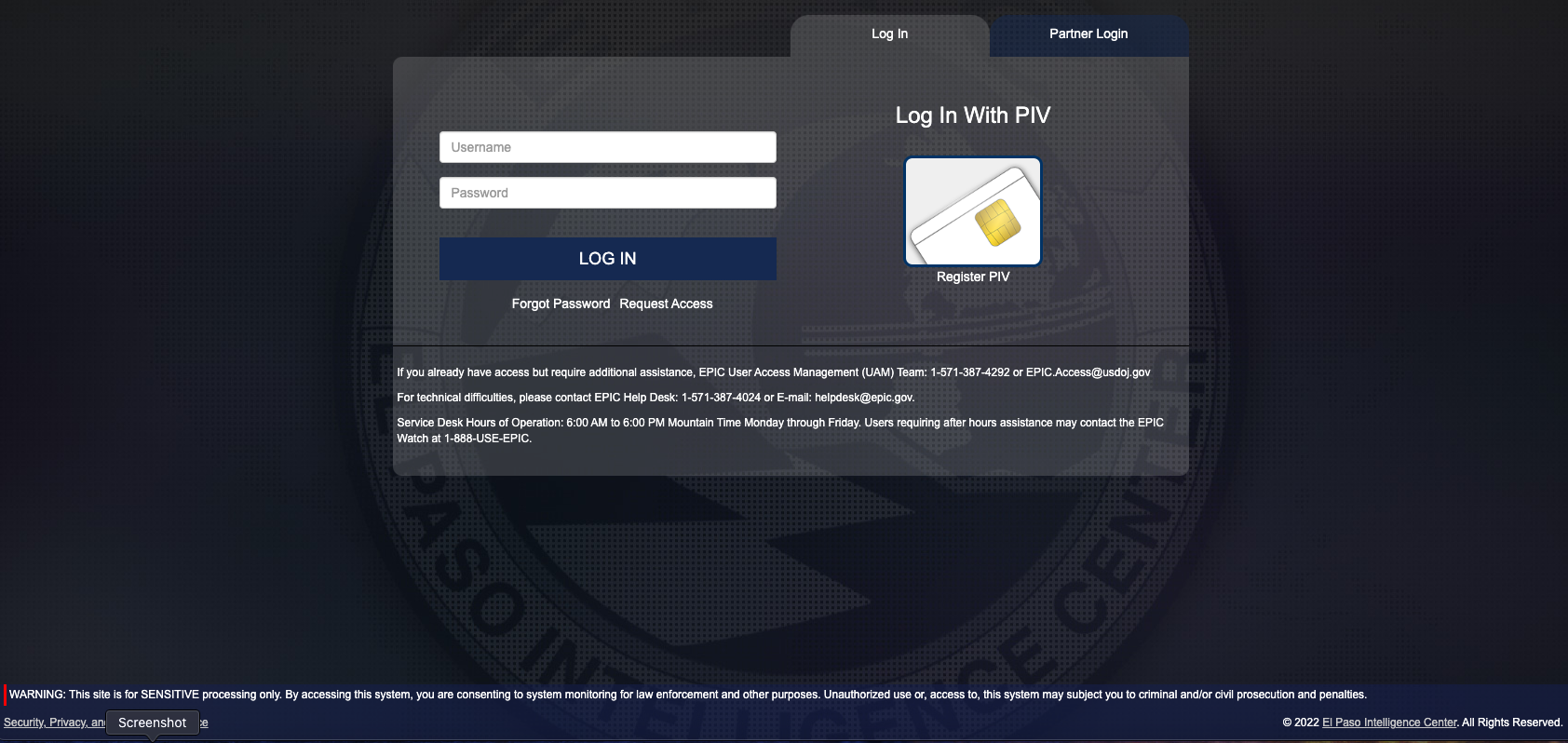
The DEA’s EPIC portal login page.
ANALYSIS
The login page for esp.usdoj.gov (above) suggests that authorized users can access the site using a “Personal Identity Verification” or PIV card, which is a fairly strong form of authentication used government-wide to control access to federal facilities and information systems at each user’s appropriate security level.
However, the EPIC portal also appears to accept just a username and password, which would seem to radically diminish the security value of requiring users to present (or prove possession of) an authorized PIV card. Indeed, KT said the hacker who obtained this illicit access was able to log in using the stolen credentials alone, and that at no time did the portal prompt for a second authentication factor.
It’s not clear why there are still sensitive government databases being protected by nothing more than a username and password, but I’m willing to bet big money that this DEA portal is not only offender here. The DEA portal esp.usdoj.gov is listed on Page 87 of a Justice Department “data inventory,” which catalogs all of the data repositories that correspond to DOJ agencies.
There are 3,330 results. Granted, only some of those results are login portals, but that’s just within the Department of Justice.
If we assume for the moment that state-sponsored foreign hacking groups can gain access to sensitive government intelligence in the same way as teenage hacker groups like LAPSUS$, then it is long past time for the U.S. federal government to perform a top-to-bottom review of authentication requirements tied to any government portals that traffic in sensitive or privileged information.
I’ll say it because it needs to be said: The United States government is in urgent need of leadership on cybersecurity at the executive branch level — preferably someone who has the authority and political will to eventually disconnect any federal government agency data portals that fail to enforce strong, multi-factor authentication.
I realize this may be far more complex than it sounds, particularly when it comes to authenticating law enforcement personnel who access these systems without the benefit of a PIV card or government-issued device (state and local authorities, for example). It’s not going to be as simple as just turning on multi-factor authentication for every user, thanks in part to a broad diversity of technologies being used across the law enforcement landscape.
But when hackers can plunder 16 law enforcement databases, arbitrarily send out law enforcement alerts for specific people or vehicles, or potentially disrupt ongoing law enforcement operations — all because someone stole, found or bought a username and password — it’s time for drastic measures.




Agreed, “it’s time for drastic measures.” Chief among these might be:
– Terminate non-technical managers who misrepresent conditions to avoid doing the real work.
– Eliminate CXO committees that prioritize career gain over security policy, staff, and programs.
Among less drastic measures that would produce similar benefits:
– Trust auditors, examiners, and technical staff more than you trust management.
– Allow implementation of security standards that have been well known for years.
I deliberately use a censored DNS (quad 9) to avoid websites with malware. But would Google (quad 8) be censored? As it turns out you can Google uncensored DNS and find https://blog.uncensoreddns.org/
Bet they also have access proton database (phone call detail records)
There is an executive branch policy to force use of phishing-resistant MFA for all government employees and contractors, but it stops short of enforcing it outside of that one group. No good guidance on partner access or public user access. PIV is only for government employees and contractors. There is a PIV Interoperable which is based on PIV without the background check, but it never caught on. Best hope is to get all government websites that require public or partner access to use something like login.gov and require a minimum MFA.
Horrifying! Frightening! Appalling! Indefensible! Right on, Brian! Time for law enforcement to enforce… cybersecurity. Thank you for saying it and thank you for your service.
I just started using a security key and am finding that there are ways around it because services often provide alternatives if the key is lost, meaning a feeling of “insecurity” with lost keys (and need to avoid increased support costs) is built into their design.
A scheme like a common access card works because the card is issued by a live human being where you work. No social engineering work arounds.
Any scheme where there is a work around will be social engineered.
Agreed, I use a CAC and they are issued by a live person. They also require a significant amount of identity proofing. I have to bring in documents to prove who I am and where I work. Identity proofing for initial enrollment is absolutely needed to allow the uses of security keys without an “insecure” fallback/recovery method.
The problem is, people don’t want Identity Proofing and they scream about privacy. Often, it’s the users who demand to be insecure.
That does not seem to be a barrier in this case. The federal government can and very much should require strong authentication from any federal employees accessing federal data systems. I believe the Biden administration laid down a deadline last year about this that DEA and others have obviously missed. How the feds deal with state and local is a bigger challenge.
https://www.federalregister.gov/documents/2021/05/17/2021-10460/improving-the-nations-cybersecurity
Yes, I was just addressing the non-gov use case that Reader expressed.
“willing to bet big money that this DEA portal is not only offender here”
I could not take that bet, as I know this to be true.
It is a sad fact that although we’ve made progress and advise the private sector to take security more seriously, the federal government moves much slower than the words travel. Lots of agencies and lots of bureaucracy. And of course, federalism prevents a concerted effort down to the state and local levels too.
Thanks for the link.
“Agencies that are unable to fully adopt multi-factor authentication and data encryption within 180 days of the date of this order shall, at the end of the 180-day period, provide a written rationale to the Secretary of Homeland Security through the Director of CISA, the Director of OMB, and the APNSA.”
As with any Executive Order, there are lots of caveats and loopholes that can neuter the effect. Having single factor “backup” authentication methods is a common one unfortunately.
OMG bureaucracy in the government? Such amazing insider insights.
Mr. krebs doesn’t let my comments post because he knows I’m right. The evidence is all over my AS number. I still have lots of respect for Mr. Krebs but he should let the truth flow so that people don’t fall victim to this horrific government “behavioral modification” program which is really revenge and torture.
If Mr. Krebs doesn’t let your comments through, how am I responding to this? By my count, I’ve let all of your comments through. Some get auto-moderated through no action on my part, and then must be manually approved by me whenever I have time.
But if you keep on about supposed censorship of comments here, you will be censored.
Check this out, Mr Krebs…
https://bgp.he.net/net/23.230.130.0/24#_whois
Why is the route protected and is this “company” in Miami or San Jose or neither? There are several under AS 18779. While you’re at it, look at Uber AS number 63086. Its been cleaned up recently but I have copies of the pre clean up AS number if you would like.
This is all related to the case you’re referring to.
A reminder that this agency (like many) has a virtually unlimited budget, and vast forfeiture powers (that are not just used against “kingpins” as said in the article), yet still takes security shortcuts that border negligence.
The real question is, what are the reprocussions (if any) going to be?
Of course as you know, the answer is none. Is there ever?
None.
As someone who used to be in ‘The Beast,’ this is primarily because the increased security would cause “Complaints,” and “Discomfort,” for those in charge.
HI Brian, Thanks for posting. If this happened this is quite a breach! Maybe time for PIV cards for all users who need access to these systems.
Regards,
Newport
Your writing skills just amazing
The fact that such a system is accessible via the public internet in itself very questionable.
The fact that such a system is accessible via the public internet in itself very concerning.
It’s an interagency portal. They don’t have a single network that can be isolated from the Internet.
This is pretty much the poster child for why government backdoors, justified with “trust us, we know what we’re doing”, is a really, really bad idea.
This is the first nor the last time a database such as EPIC has been compromised. I know for a fact officers have sold access to databases such as these, along with even more sensitive databases. If an actor is smart about it and has officers on the take throughout the system it is almost or impossible to track. You also don’t even have to get an officer on the take, a child or a spouse can be good enough and better in many cases.
So lovely. Imagine if chekists working for Putin want to override private security capability and hire out some mercs from Wagner group to do a hit on high profile Americans. No need to recon just log into the federal database and plant some juicy stuff, then let the feds gather intel while you wait. 7 dead Russian oligarchs under mysterious circumstances already. This isn’t a far fetched scenario. What is far fetched is the explanations for why federally regulated systems are so insecure, often by design. Look no further than SS7 firewalls and how abysmal cellular privacy is. If any state or non-state actor wants to buy real-time locations for any American citizen all they need is your cell number. That’s real cute. Now imagine we’re at war with an adversary that wants to take out as much leadership as possible from the get.
Thanks for the commentary and the blog post.
Lol, cry more. If murderous American federal scum have access to something, why shouldn’t more peaceful common criminals have the same?
Exactly right. The federal government is the worst terrorist organization in the history of humanity. Everything they have should be publicly accessible and used to prosecute anyone who has acted as a collaborator.
“Peaceful criminals” certainly isn’t the term I would use. If you were a victim of this, you would change your mind about these “peaceful criminals”. Our government should NOT be utilizing these unconstitutional programs on anyone. If our government didn’t have and use the programs freely, neither would the criminals.
Why isn’t two factor authentication mandatory for all such databases?
And we have $40 billion for Ukraine but not for cyber security?
$18 billion just for federal cyber security.
You’ve got to admit the Russian military is a mite bigger threat to deal with than skiddies and mobsters cruising around network links. Please take that false equivalency back to false equivalency HQ (the Cable News channels).
The FSB/mil is literally running some mobster networks so it’s a double-double false =
Almost a bigger story here for me is that Justice department data inventory. Should it be Job #1 security wise to reduce the attack surface. Does the Justice department EVER turn a server/web-content-tree down or are they waiting for hardware failures because they are collectively too cowardly to actually make and end date decision?
Years of wringing hands and ineffective (not non-value add, but don’t solve the problem) on the defense tools suggest another direction, yes? Difficult to read this excellent narrative knowing that while few and far between (in fact can be counted on less than one hand) a solution is actually at hand. Why is it taking so long to adopt? Cyber fatigue, fear of emerging technology, and a cyber market that is its own economic juggernaut. Datacentric, zero-trust, secure data governance – look it up – and adopt it as soon as you can.
It’s so sad the rate at which crypto theft is increasing and newbies are the main targets of this scheme. Few days back I lost some funds to a crypto investors who proved to be real until he got away with my money luckily for me I wrote F U N D R E S T O R E R ▪️C 0 M who rescued me and got back my money completely
I d o n ‘ t b e l i e v e y o u
What about the DEA and the FBI doing illegal surveillance on innocent citizens with an EDR and their Fusion Centers and Infragard groups?
Sim swapping and running apps through Google Instant Apps on people’s phone through debugging programs… their IRON FIST operation.
Its all for human experimental purposes. They basically murder you by false accusations and discredit you so that you can’t get help. People are being trafficked to China and Russian experimentation which to me is an act of treason. Havana Syndrome comes from the equipment they use to do “surveillance” which keeps you connected to different remote medical devices that steals your bio data. The victims are never paid for their “services to mankind”. Victims are paid by harassment, degradation, theft of all data bio and electronic… all of which is unconstitutional. Its a sick game being played by criminals and mentally ill government officials. They use the DoD IP addresses that are supposedly stagnant and a huge list of government contractors participate in destroying and innocent persons’ life. My advice to everyone is that if you see something… don’t say a word. Run like there is no tomorrow. Their main targets seem to be whistleblowers.
You said in the article that the criminals mimmick the US government… cybercrime and online harassment community that routinely impersonates police and government officials. Uhhhh…. they place you into legitimate US government surveillance programs, put you into experimentation programs and basically torture the living hell out of you. These are legitimate government programs that are being abused by people in our government. They don’t impersonate the police and government officials, they ARE the US government. The criminals merely place you into it via revenge websites. The only people I see that should be placed into the programs are the criminals who perpetrate them for the government. Plain and simple… its torture.
Dafuq you smoking out there in bumfuq? You’re not being tortured fool.
Turn off the Q-Afox
You might think this is a necessity for devices like smartphones.