Cybercrime groups that specialize in stealing corporate data and demanding a ransom not to publish it have tried countless approaches to shaming their victims into paying. The latest innovation in ratcheting up the heat comes from the ALPHV/BlackCat ransomware group, which has traditionally published any stolen victim data on the Dark Web. Today, however, the group began publishing individual victim websites on the public Internet, with the leaked data made available in an easily searchable form.
The ALPHV site claims to care about people’s privacy, but they let anyone view the sensitive stolen data.
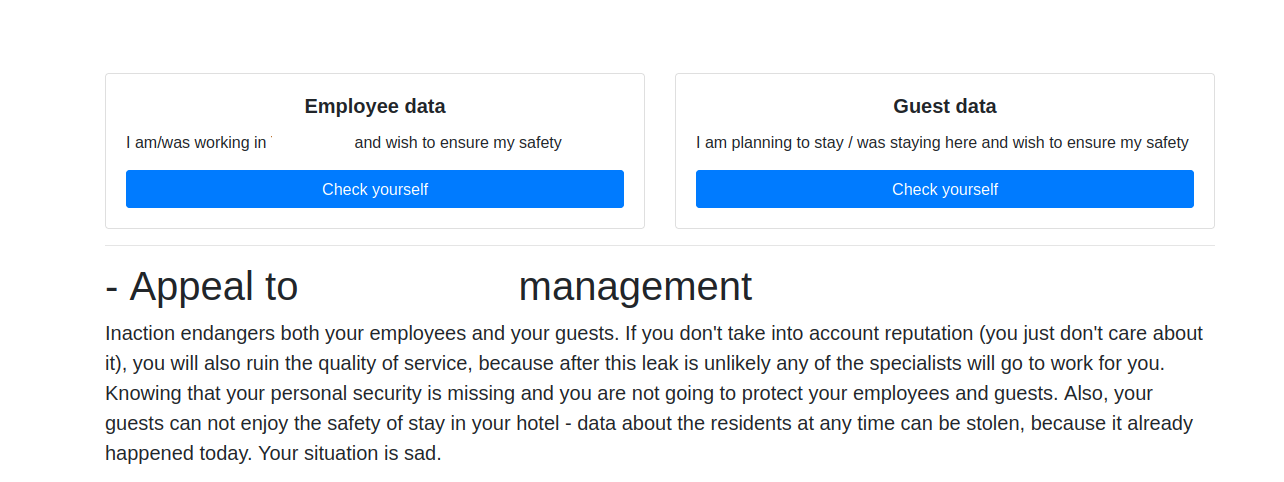
ALPHV recently announced on its victim shaming and extortion website that it had hacked a luxury spa and resort in the western United States. Sometime in the last 24 hours, ALPHV published a website with the same victim’s name in the domain, and their logo on the homepage.
The website claims to list the personal information of 1,500 resort employees, and more than 2,500 residents at the facility. At the top of the page are two “Check Yourself” buttons, one for employees, and another for guests.
Brett Callow, a threat analyst with security firm Emsisoft, called the move by ALPHV “a cunning tactic” that will most certainly worry their other victims.
Callow said most of the victim shaming blogs maintained by the major ransomware and data ransom groups exist on obscure, slow-loading sites on the Darknet, reachable only through the use of third-party software like Tor. But the website erected by ALPHV as part of this new pressure tactic is available on the open Internet.
“Companies will likely be more concerned about the prospect of their data being shared in this way than of simply being posted to an obscure Tor site for which barely anyone knows the URL,” Callow said. “It’ll piss people off and make class actions more likely.”
It’s unclear if ALPHV plans to pursue this approach with every victim, but other recent victims of the crime group include a school district and a U.S. city. Most likely, this is a test run to see if it improves results.
“We are not going to stop, our leak distribution department will do their best to bury your business,” the victim website reads. “At this point, you still have a chance to keep your hotel’s security and reputation. We strongly advise you to be proactive in your negotiations; you do not have much time.”
Emerging in November 2021, ALPHV is perhaps most notable for its programming language (it is written in Rust). ALPHV has been actively recruiting operators from several ransomware organizations — including REvil, BlackMatter and DarkSide — offering affiliates up to 90 percent of any ransom paid by a victim organization.
Many security experts believe ALPHV/BlackCat is simply a rebrand of another ransomware group — “Darkside” a.k.a. “BlackMatter,” the same gang responsible for the 2021 attack on Colonial Pipeline that caused fuel shortages and price spikes for several days last summer.
Callow said there may be an upside to this ALPHV innovation, noting that his wife recently heard directly from a different ransomware group — Cl0p.
“On a positive note, stunts like this mean people may actually find out that their PI has been compromised,” he said. “Cl0p emailed my wife last year. The company that lost her data still hasn’t made any public disclosure or notified the people who were impacted (at least, she hasn’t heard from the company.)”




How are they able to publish this kind of thing on the public internet? Surely it would be easy to trace the host and have it shutdown?
Or is it in Russia or somewhere outside the reach of law enforcement?
It doesn’t have to be online for very long, a lot of web hosts aren’t super responsive or fast as this is a cost center for them.
A man named James McGibney has run extortion websites for many years right out in the open on Amazon Web Service. AWS has done nothing to remove the extortionate sites. That’s how it can be done right out in the open on the internet.
Whackamole.
McGibney owns around a thousand domains which were purchased purely to harass people online. They remain up, but at some point this year we’ll have the final hearing on the frivolous lawsuit he filed against me in 2014, and once collections begin I guess all that stuff will be mine. I’ll see that the domains are transferred to the various victims.
What’s fascinating to me is clearly companies aren’t paying up, because… well who cares, right? Until someone cares and makes a lot of noise… I wonder how long until the ransomware people start contacting members of congress/your local member of parliament or whatever on your behalf “Hi, we have all the data for [name of your constituent] living at [address] because [company name] had crappy security.”
Premise not true plenty of companies paid. Many institutions paid. Who cares?
The footpads are organized and sharing now to go after individual targets to
compromise parent organizations and then lateral. Link by link, email by email.
That’s before the zero days, just known existing vulns. It works without secrets.
It doesn’t take a lot of attack surface if someone knows about it. Now all do.
It’s common practice for companies to provide employee PII to vendors for “free trials” or preferred pricing on goods and services. It’s not illegal, yet California has no law protecting employees from this practice whether a given employee consents by accepting that free trial or that goods/services discount or declines. There is no deterrence for company HR professionals to stop the practice, but with this spin on corporate ransomware there may now be. It’s brand reputation damage and employees are largest consumers of their company’s branding. PII leaks may put-off prospective employees, may impact retention, and may affect new business generation. Asking California to lead the way here.
Disclosure is as broken as DNT = who ever believed this was viable?
Considering the ridiculous numbers of phishing sites hosted via AWS/Cloudflare etc, no surprises there. Add in “forward thinking” Marketing staff who gleefully provide an entire enterprise’s worth of email addresses to “providers of valuable information” and you are already primed for a phishing campaign/BEC/more noise from an untuned IDS. This will hopefully force a little transparency into the mix.