Someone has recently created a large number of fake LinkedIn profiles for Chief Information Security Officer (CISO) roles at some of the world’s largest corporations. It’s not clear who’s behind this network of fake CISOs or what their intentions may be. But the fabricated LinkedIn identities are confusing search engine results for CISO roles at major companies, and they are being indexed as gospel by various downstream data-scraping sources.
If one searches LinkedIn for the CISO of the energy giant Chevron, one might find the profile for a Victor Sites, who says he’s from Westerville, Ohio and is a graduate of Texas A&M University.
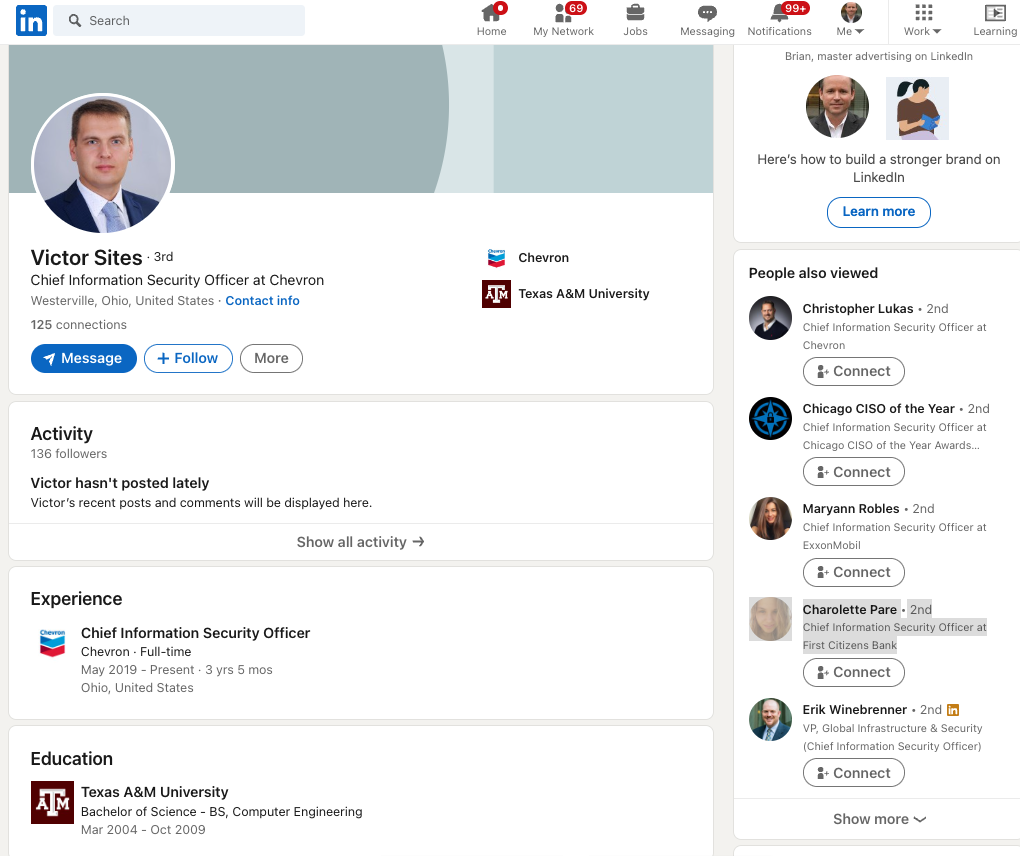
The LinkedIn profile for Victor Sites, who is most certainly NOT the CISO of Chevron.
Of course, Sites is not the real CISO of Chevron. That role is currently occupied by Christopher Lukas of Danville, Calif. If you were confused at this point, you might ask Google who it thinks is the current Chief Information Security Officer of Chevron. When KrebsOnSecurity did that earlier this morning, the fake CISO profile was the very first search result returned (followed by the LinkedIn profile for the real Chevron CISO).
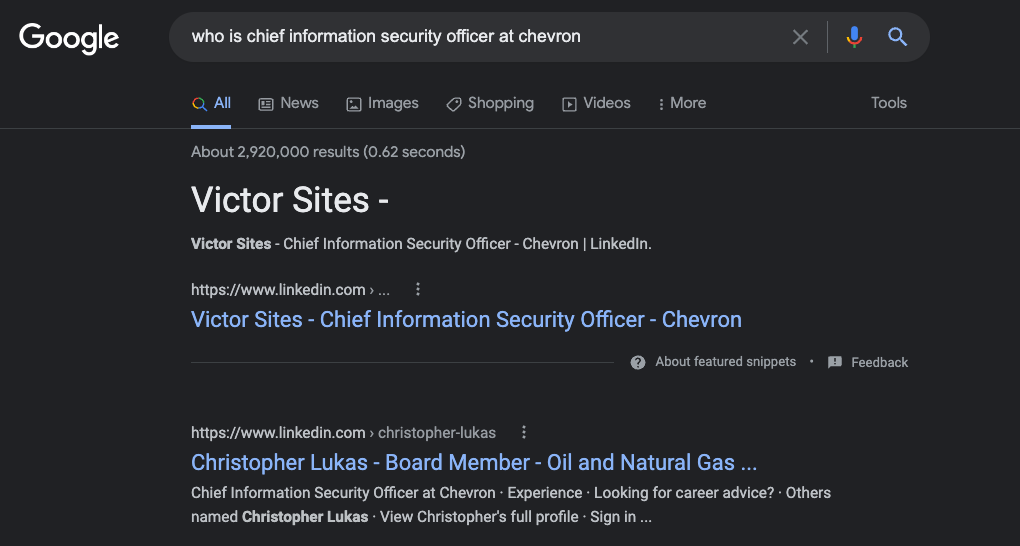
Helpfully, LinkedIn seems to be able to detect something in common about all these fake CISO profiles, because it suggested I view a number of them in the “People Also Viewed” column seen in the image above. There are two fake CISO profiles suggested there, including one for a Maryann Robles, who claims to be the CISO of another energy giant — ExxonMobil.
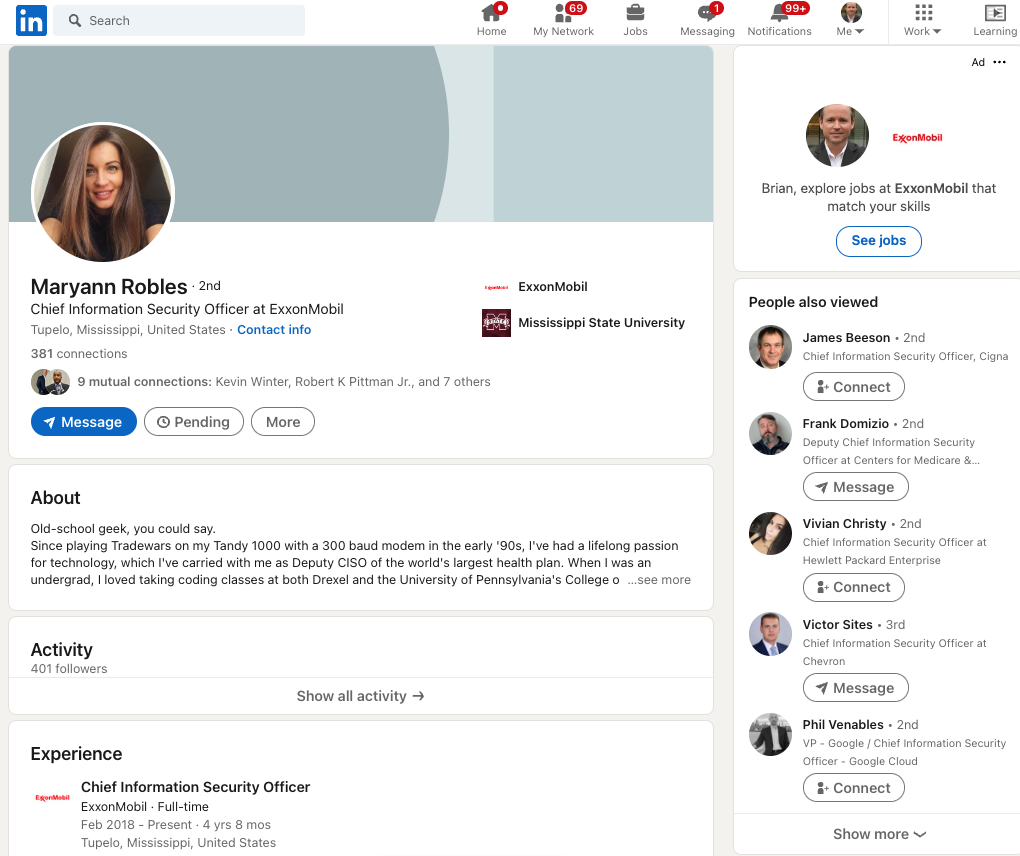
Maryann’s profile says she’s from Tupelo, Miss., and includes this detail about how she became a self-described “old-school geek.”
“Since playing Tradewars on my Tandy 1000 with a 300 baud modem in the early ’90s, I’ve had a lifelong passion for technology, which I’ve carried with me as Deputy CISO of the world’s largest health plan,” her profile reads.
However, this description appears to have been lifted from the profile for the real CISO at the Centers for Medicare & Medicaid Services in Baltimore, Md.
Interestingly, Maryann’s LinkedIn profile was accepted as truth by Cybercrime Magazine’s CISO 500 listing, which claims to maintain a list of the current CISOs at America’s largest companies:
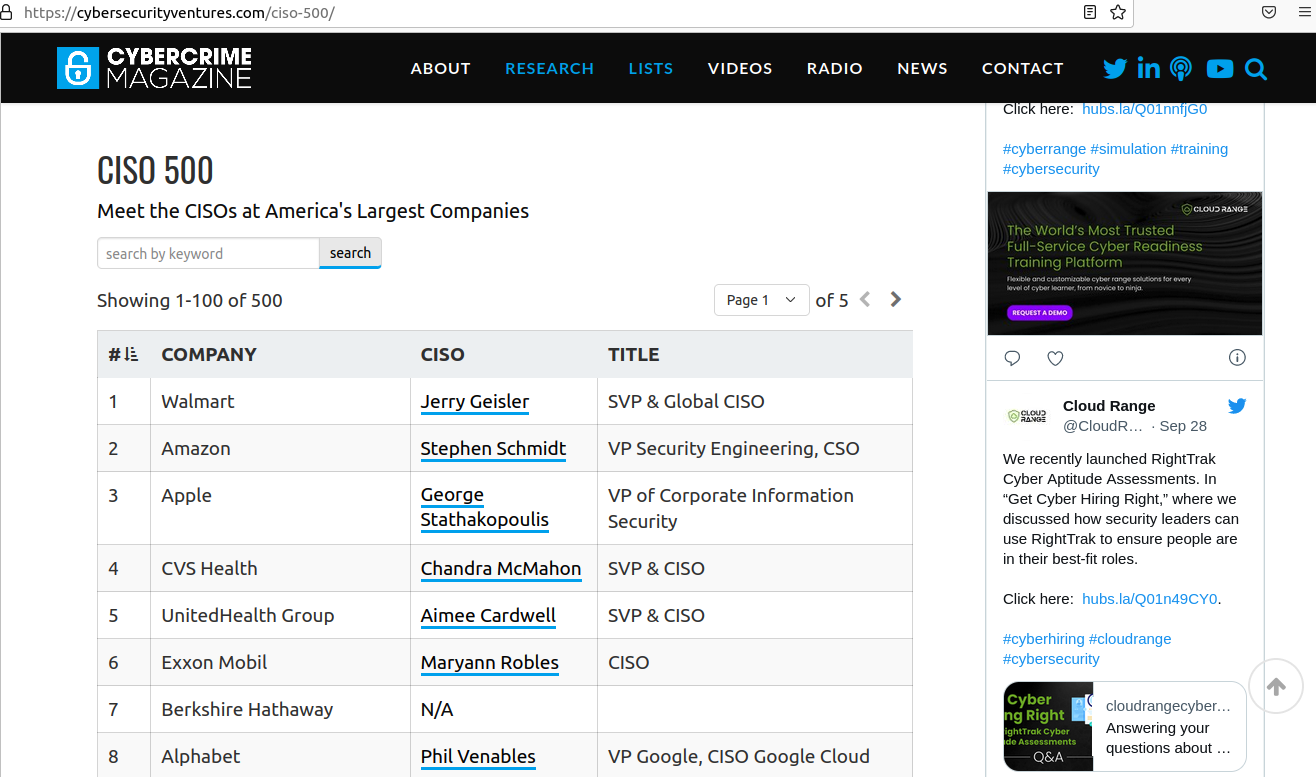
The fake CISO for ExxOnMobil was indexed in Cybercrime Magazine’s CISO 500.
Rich Mason, the former CISO at Fortune 500 firm Honeywell, began warning his colleagues on LinkedIn about the phony profiles earlier this week.
“It’s interesting the downstream sources that repeat LinkedIn bogus content as truth,” Mason said. “This is dangerous, Apollo.io, Signalhire, and Cybersecurity Ventures.”
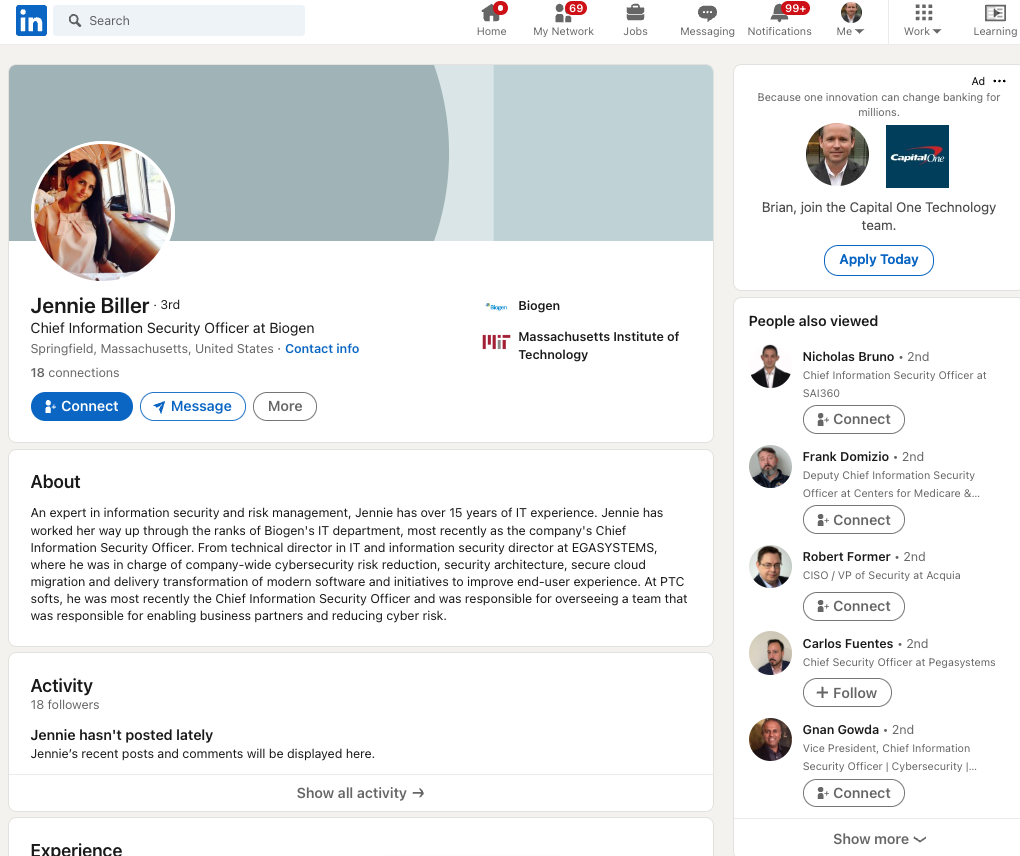
Google wasn’t fooled by the phony LinkedIn profile for Jennie Biller, who claims to be CISO at biotechnology giant Biogen (the real Biogen CISO is Russell Koste). But Biller’s profile is worth mentioning because it shows how some of these phony profiles appear to be quite hastily assembled. Case in point: Biller’s name and profile photo suggest she is female, however the “About” description of her accomplishments uses male pronouns. Also, it might help that Jennie only has 18 connections on LinkedIn.
Again, we don’t know much about who or what is behind these profiles, but in August the security firm Mandiant (recently acquired by Google) told Bloomberg that hackers working for the North Korean government have been copying resumes and profiles from leading job listing platforms LinkedIn and Indeed, as part of an elaborate scheme to land jobs at cryptocurrency firms.
None of the profiles listed here responded to requests for comment (or to become a connection).
In a statement provided to KrebsOnSecurity, LinkedIn said its teams were actively working to take these fake accounts down.
“We do have strong human and automated systems in place, and we’re continually improving, as fake account activity becomes more sophisticated,” the statement reads. “In our transparency report we share how our teams plus automated systems are stopping the vast majority of fraudulent activity we detect in our community – around 96% of fake accounts and around 99.1% of spam and scam.”
LinkedIn could take one simple step that would make it far easier for people to make informed decisions about whether to trust a given profile: Add a “created on” date for every profile. Twitter does this, and it’s enormously helpful for filtering out a great deal of noise and unwanted communications.
The former CISO Mason said LinkedIn also could experiment with offering something akin to Twitter’s verified mark to users who chose to validate that they can respond to email at the domain associated with their stated current employer.
“If I saw that a LinkedIn profile had been domain-validated, then my confidence in that profile would go way up,” Mason said, noting that many of the fake profiles had hundreds of followers, including dozens of real CISOs. Maryann’s profile grew by a hundred connections in just the past few days, he said.
“If we have CISOs that are falling for this, what hopes do the masses have?” Mason said.
Mason said LinkedIn also needs a more streamlined process for allowing employers to remove phony employee accounts. He recently tried to get a phony profile removed from LinkedIn for someone who falsely claimed to have worked for his company.
“I shot a note to LinkedIn and said please remove this, and they said, well, we have to contact that person and arbitrate this,” he said. “They gave the guy two weeks and he didn’t respond, so they took it down. But that doesn’t scale, and there needs to be a mechanism where an employer can contact LinkedIn and have these fake profiles taken down in less than two weeks.”




LinkedIn became a cesspool even before Microsoft took it over.
I left a small bit of token information up for one of my last jobs and removed anything about me personally. I doubt that the information has actually been removed since companies like google, microsoft, amazon, apple, etc. are trying to get the goods on everyone they can.
Hi Brian! Great writeup – kind of incredible to be honest.
Am curious – what did your 9 connections that appear to be linked to Maryanne say about their relationship?
most likely fake contact too.
Jennie’s profile uses mixed (confused?) pronouns, not just male:
“…Jennie has worked *her* way up…” but then “…where *he* was in charge of…”
Perhaps the goal is to use the fake LI profiles as a source for credibility when attempting to socially engineer ones who would fall somewhere under the CISO’s chain of command.
Spot on. This happened recently to our company. An employee had a conversation with someone and that carried over to a credential harvesting email message being delivered. Crafty.
ArsTechnica.com has just posted an article about an attack on big companies via supply chain compromise in open-source apps. The article says a North Korean state actor is behind the attack.
I’d say playing Tradewars on a BBS in the 90s was way better than ‘quaint’ but I appreciate the link nonetheless. Thanks Chris!
Maryanne was one of the few people still using a 300 baud modem in the early 1990’s. The rest of us were using inexpensive 2400 baud modems running at 9600 or 14.4bps.
But the Tandy 1000 was a mid 80s machine (and the exact model wasn’t mentioned), and if you’re still running one in the early 90s, it makes some sense that parts of it are outdated too.
Anyway, the article said that was real, but lifted from someone else.
Remember it’s North Korea… So maybe only 300 baud there haha!
Um, how did you get 9600 or 14.4K out of a 2400? Must have been some wild compression there!
It was 2400 bauds (symbols) per second, depending on the system you can get 1,2, 4 or even 8 bits per symbol (sound sample)
Several years ago I did a bunch of LinkedIn hunting looking for fake profiles of people saying they worked for the company but didn’t. LinkedIn was less than helpful or transparent in the process. Doesn’t sound like it’s gotten much better…
I personally had one of these fake CISOs contact me at one point. Not sure if it’s the same attacker, I noticed that they had created multiple CISOs for the same company. Got a very templated looking message, asking to be LinkedIn friends. Nothing sophisticated though.
“well, we have to contact that person …” instead of contacting only *the potential fraudster*, didn’t LinkedIn also contact *the company* ? For Fortune 500 companies (which I picture as established companies, with an easy way to find a reliable channel to contact them), I would expect this to work much better
Congratulations good keep it up !! great job Thanks !!
Using the fake LP isn’t the best idea either. They gave the guy two weeks and he didn’t respond
I guess the idea that you are whoever you say you are on social media applies to LI too. What this means for LI if they can’t fix the issue is that they’ll no longer be seen as some kind of authoritative source, and honestly, I don’t know that that’s a bad thing. We’ve already seen what happens when social media is too powerful. The fact that it’s unreliable shouldn’t come as a surprise, nor should it ever have been an authoritative source.
Wow.
Mary Ann Robles looks way too young to have even been alive when 300 baud modems were standard!
This is what happens when somebody pretends that a “social network” that is policed as poorly as any other social network (i.e. not really policed at all) is somehow a source of legitimate business information and job offers. You can’t create a legitimate source of business information if the information presented by malicious actors is not filtered out from the information presented by legitimate actors.
I received one of these invites less than 2 weeks ago…CISO profile had a pleasing photo and work history went from IT intern in 2020 to CISO in 2022, had 8 followers. Obvious scam, needless to say I ignored the invite and honestly its another wedge pushing me away from the platform. My time is valuable, don’t waste it. There are other trends I see on the platform that constantly force me to rethink using it. Maybe real professional networking is better accomplished IRL
Lot of these real CISOs of US companies are unqualified and incompetent anyway.
Many have unrelated degrees like Music, Arts, Chemistry, Mechanical engineering, … and do some useless Cybersecurity certifications to finally become real CISO just based on some connections I guess. Just look at the kind of silly data breaches and root cause.
The crafting of full and fake digital personas is accelerating because they are proving to be a more and more successful exploit vehicle for the bad guys. Doesn’t matter if it is nation-state, organized crime or just a 17 year old kid who has been popping big companies for massive amounts of data. A fictional, but believable digital persona is exactly the kind of convincing asset needed to take social engineering, business email compromise and a host of other financially related frauds to the next level. I’ve said it in a number of keynotes at a host of conferences where we’ve crossed path Brian – if the bad guys fully understand the power of digital identity, why is the corporate world still debating the subject and treating identity like it is just a basic administrative function?
I used Linkedin when I was looking for work and realized quickly that it was more about narcissism than actual useful information.
My startup saw fake profiles back in 2012. When we contacted LinkedIn to have them pull down the fake profiles it was clear they were more interested in padding their numbers and fake MAU stats than addressing resume fraud on their platform. Looks like not much has changed in 10 years.
Services like LI should be offerinng protection for their most attractive customers. Fortune 500 x 10-20 executives who change likely only once a year equals 5-10,000 interactions by digitally signed emails a year, hardly a burden. Offer the same service to non-Fortune 500 entities for a fee. Also, trigger on duplicates, that’s security from the 50’s. The problem is that LI couldn’t care less about security, or integrity for that matter, it’s supposed to run itself without their involvment.
Great article Brian! Who is behind this do you think? Recruiters often create fake profiles but only the most scurrilous would create profiles for others. Over the past month or so, I’ve received numerous LI connection requests from always attractive Asian women that I decline. They can’t all have such high level positions in the beauty industry!
THIRSTPOST!
I tried posting this from my phone, but it didn’t work, guess we’re not Android friendly.
LI, and services like it, need to recognize they need to protect their most important customers. People come to their site in the hopes of interacting with top people, so do something for those people. Fortune 500 x 10-20 top executives x 1 change per year means 5-10,000 digitally signed interactions a year, hardly a burden. Offer the same safety to non-Fortune 500 customers for a fee. It will be wonderful when such services realize they cannot totally automate their existence and not suffer reputational damages from whomever wants to exploit their incredibly weak security. LI doesn’t care about security any more than they care about their integrity, and the integrity and reputation of those who trust in them to hold their data.
Not hard, just requires them to actually spend money on their image.
Someone needs to create a fake Microsoft CSO on there. Suspect that might get their attention to do something more about this issue…
A group of my friends in Asia have been tracking fake profiles that specifically approach security professionals. Overwhelmingly female profiles in that case.
Looks like there’s multiple different groups carrying out these campaigns.
I too have gotten connection requests from fake profiles. These aren’t CISOs mind you but they appear to be fake profiles any way – some sort of bot. No job listing, no details, no postings, very few connections.
Hmmm. LInkedIn needs to do a better job of scrubbing these people.
Together with the group owner, I manage the Sustainability Professionals group (membership 302,000 with an active membership of over 90,000 visitors every 15 days). We receive over 500 fake profile requests to join on a weekly basis. We have used hours (and indeed days) of our efforts to learn the patterns and proactively screen every single request to join to root out these fakes.
So far LinkedIn management has failed to engage properly in investigating the IP addresses and DNS servers responsible for these waves of BOT-generated profiles. We have methodically captured the pattern of fakes and shared this with Microsoft but they have failed to do anything meaningful.
In our situation the abuse is worst when we have several hundred fake profiles who claim to be Crisis Relief Experts – exactly the sort of genuine people who would be excellent members of our Sustainability focused group.
Our list of BLOCKED members is now over 8,000 and we simply deny many more via multiple denial actions as so far LinkedIn has forced us to block one by one which takes around a minute for the multi-click process. It is particularly time consuming as we try to minimise the number of “false positive” fakes.
I have received these type of cold connection requests and I typically do not connect because #1 I don’t know them and #2 their experience and positions compared to their age do not seem believable. I mean how many people graduate college and land a CISO job unless they founded the company themselves…which then they’d likely be the CEO instead. Thank you for reporting on this. It’s troubling to me since the CISO role is a trust and integrity position so maybe that’s part of the purpose of creating these profiles, to reduce the trust factor of legitimate CISOs. I’ve worked hard to get to where I am and beyond the technical, business and soft skills, I also have to be entrusted with sensitive company information beyond strategic plans and business opportunities.
It is not just CISO or North Korea that does this stuff in LinkedIn. It recently happened to my sister-in-law in Vietnam. She is single, and albeit a bit naive. She was catfished via LinkedIn. The person claimed to be a man and Doctor from Harvard. He was practicing in California according to the fake profile.
What turned out to be the smoking gun, and my wife and I were suspicious based upon what my to SIL shared was a bit gotcha. The person claimed to me the Chief Medical Officer of a startup company in medical technology. Well I Googled that company looking for their name as the Chief Medical Officer. I got someone else’s name, and tied them to a legitimate LinkedIn profile. I even sent that person a brief message telling them that their profile was ‘lifted’ and copied into a fake. He responded appropriately. I reported to LinkedIn the issue, and that fake profile was taken down.
As far as my SIL, she was ‘heartbroken’, but alas it was only just that and nothing more.
To a the viewer who is aware, take LinkedIn with a grain of salt. Some profiles are totally fake. Beware.
Probably that bozo that I found preying on my SIL was somewhere in the USA or maybe even in Nigeria…I don’t know as they could be anywhere. All I know is they were a real crook.
LinkedIn never got this completely fixed. They can’t tell the difference between St. Petersburg, FL and St. Petersburg, Russia
https://securityledger.com/2019/01/linkedin-says-glitch-not-fsb-to-blame-for-russian-job-postings/