ConnectWise, which offers a self-hosted, remote desktop software application that is widely used by Managed Service Providers (MSPs), is warning about an unusually sophisticated phishing attack that can let attackers take remote control over user systems when recipients click the included link. The warning comes just weeks after the company quietly patched a vulnerability that makes it easier for phishers to launch these attacks.

A phishing attack targeting MSP customers using ConnectWise.
ConnectWise Control is extremely popular among MSPs that manage, protect and service large numbers of computers remotely for client organizations. Their product provides a dynamic software client and hosted server that connects two or more computers together, and provides temporary or persistent remote access to those client systems.
When a support technician wants to use it to remotely administer a computer, the ConnectWise website generates an executable file that is digitally signed by ConnectWise and downloadable by the client via a hyperlink.
When the remote user in need of assistance clicks the link, their computer is then directly connected to the computer of the remote administrator, who can then control the client’s computer as if they were seated in front of it.
While modern Microsoft Windows operating systems by default will ask users whether they want to run a downloaded executable file, many systems set up for remote administration by MSPs disable that user account control feature for this particular application.
In October, security researcher Ken Pyle alerted ConnectWise that their client executable file gets generated based on client-controlled parameters. Meaning, an attacker could craft a ConnectWise Control client download link that would bounce or proxy the remote connection from the MSP’s servers to a server that the attacker controls.
This is dangerous because many organizations that rely on MSPs to manage their computers often set up their networks so that only remote assistance connections coming from their MSP’s networks are allowed.
Using a free ConnectWise trial account, Pyle showed the company how easy it was to create a client executable that is cryptographically signed by ConnectWise and can bypass those network restrictions by bouncing the connection through an attacker’s ConnectWise Control server.
“You as the attacker have full control over the link’s parameters, and that link gets injected into an executable file that is downloaded by the client through an unauthenticated Web interface,” said Pyle, a partner and exploit developer at the security firm Cybir. “I can send this link to a victim, they will click this link, and their workstation will connect back to my instance via a link on your site.”
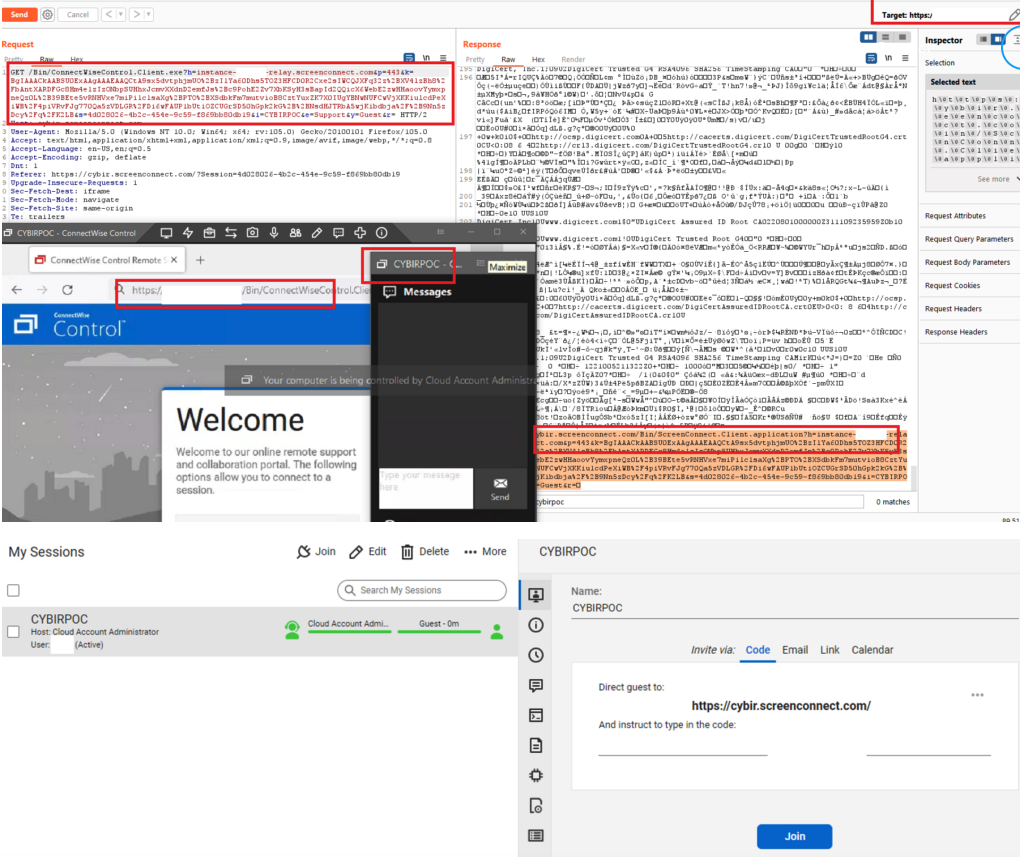
A composite of screenshots researcher Ken Pyle put together to illustrate the ScreenConnect vulnerability.
On Nov. 29, roughly the same time Pyle published a blog post about his findings, ConnectWise issued an advisory warning users to be on guard against a new round email phishing attempts that mimic legitimate email alerts the company sends when it detects unusual activity on a customer account.
“We are aware of a phishing campaign that mimics ConnectWise Control New Login Alert emails and has the potential to lead to unauthorized access to legitimate Control instances,” the company said.
ConnectWise said it released software updates last month that included new protections against the misdirection vulnerability that Pyle reported. But the company said there is no reason to believe the phishers they warned about are exploiting any of the issues reported by Pyle.
“Our team quickly triaged the report and determined the risk to partners to be minimal,” said Patrick Beggs, ConnectWise’s chief information security officer. “Nevertheless, the mitigation was simple and presented no risk to partner experience, so we put it into the then-stable 22.8 build and the then-canary 22.9 build, which were released as part of our normal release processes. Due to the low severity of the issue, we didn’t (and don’t plan to) issue a security advisory or alert, since we reserve those notifications for serious security issues.”
Beggs said the phishing attacks that sparked their advisory stemmed from an instance that was not hosted by ConnectWise.
“So we can confirm they are unrelated,” he said. “Unfortunately, phishing attacks happen far too regularly across a variety of industries and products. The timing of our advisory and Mr. Pyle’s blog were coincidental. That said, we’re all for raising more awareness of the seriousness of phishing attacks and the general importance of staying alert and aware of potentially dangerous content.”
The ConnectWise advisory warned users that before clicking any link that appears to come from their service, users should validate the content includes “domains owned by trusted sources,” and “links to go to places you recognize.”
But Pyle said this advice is not terribly useful for customers targeted in his attack scenario because the phishers can send emails directly from ConnectWise, and the short link that gets presented to the user is a wildcard domain that ends in ConnectWise Control’s own domain name — screenconnect.com. What’s more, examining the exceedingly long link generated by ConnectWise’s systems offers few insights to the average user.
“It’s signed by ConnectWise and comes from them, and if you sign up for a free trial instance, you can email people invites directly from them,” Pyle said.
ConnectWise’s warnings come amid breach reports from another major provider of remote support technologies: GoTo disclosed on Nov. 30 that it is investigating a security incident involving “unusual activity within our development environment and third-party cloud storage services. The third-party cloud storage service is currently shared by both GoTo and its affiliate, the password manager service LastPass.
In its own advisory on the incident, LastPass said they believe the intruders leveraged information stolen during a previous intrusion in August 2022 to gain access to “certain elements of our customers’ information.” However, LastPass maintains that its “customer passwords remain safely encrypted due to LastPass’s Zero Knowledge architecture.”
In short, that architecture means if you lose or forget your all-important master LastPass password — the one needed to unlock access to all of your other passwords stored with them — LastPass can’t help you with that, because they don’t store it. But that same architecture theoretically means that hackers who might break into LastPass’s networks can’t access that information either.
Update, 7:25 p.m. ET: Included statement from ConnectWise CISO.



You have to have an internet only ‘disposable’ computer for these things. It is no big deal if it gets taken over. You do internet work on the disposable and you do your important work on the offline computer. I would use $299 Walmart HP slims for that or a cheap $165 tablet.
I have many computers that are offline. And they are offline not only from ransomware / phishing. They are offline to keep Microsoft from their forced updates. With every reincarnation of Windows things get worse and worse.
Can’t any of you brainiacs create another option other than using Microsoft? And if not, how about a $65 program called ‘Windows Blocker’ that stops Microsoft’s forced updates.
I’ve had so many issues from Microsoft’s forced updates over the years. Hell, they are the biggest phisher of the bunch. I just bought a $2000 custom computer and boom, within a few days of operation, Microsoft ruined it with one of their forced updates. It won’t recognize external optical drives any longer. Tried all the online fixes and still no go.
You want ultimate protection…use a disposable internet computer and keep your other computers offline and far away from Microsoft’s hands if you can.
Why are you still using microsoft products? If you are that addicted to point-and-click interfaces, Apple can rob you of your money just as surely as microsoft can, with less heartache and supposedly better customer service. If you can bear touching a command line every now and again, move to one of the 1230948712 Linux implementations, several of which are corporate-supported.
Thanks for the suggestion Another Greaybeard.
Why? A lot of the programs I use are for Windows. Can you run Lightroom 5 or Adobe Photoshop Elements and other programs like that on Linux? I have lots of scanning programs from Epson. Hell, the Epson scanner programs gave me trouble with Windows 11.
I don’t know a thing about switching to Linux. I can look into it, but I figured the programs I use would not work with anything other than Windows.
Depends what you are doing.
You can try GIMP on Windows and it runs natively on Linux. It takes a little while to get used to it but now that I know most of the common functions via short cuts, I can whip out photo edits just as quickly as before.
GIMP and Blender also work really well together if you want to make 3D objects.
One way to stop the auto updates on a Windows machine with Windows 10 Pro or above is as follows:
===
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
“NoAutoUpdate”=dword:00000001
===
Thanks for posting, that’ll be blocked in the next round of mandatory updates.
I got hit with this on Monday and it did use part of the attack described by Ken Pyle. I got the fake alert email, fell for it, clicked through, and logged into a fake ConnectWise site. The site grabbed my credentials (including OTP) and logged into my ConnectWise cloud account and then into my Control instance. Once they were in there they uploaded an installer package called “update.msi” into the toolbox and pushed it out to all the connected Windows agents, which installed it immediately. This package installed a second ScreenConnect client on the computer that pointed to the attacker’s Control instance instead of mine. I worked with their security team a little on the phishing and reported my findings on the installer package once I figured out what was going on, but they weren’t responsive on the point that their own service was being used to take over computers in the attack.
Yeah, this connect Wise bug seems like their systemic problem that they can’t fix easily and thus the company downplays its significance.
Any updates on the latest LastPass breach though, Brian? IMHO that one is much more severe for most people. That product, since it was acquired and gutted of useful features by LogMeIn, had too many breaches lately.
Not much more than what they’ve disclosed yet. The truth will out.
They haven’t patched anything. The latest stable version was released in February 2022. If you’re running this product, you’re vulnerable. The advice ConnectWise support is offering? “Don’t click on stuff in emails.” Thanks, ConnectWise. I think we were already trying to get a handle on that one.
I don’t know where are you looking, but the latest stable version is 22.9.10446.8359 released on 20/11/2022.
This attack is rather limited in scope – doesnt effect on-prem CWControl servers at all… its mitigated by CORS if you follow the setup guide and configure security settings correctly – this attack vector should suprise noone who runs a CWControl server, and should already be addressed in any properly maintained environment.
If anyone is actually suceptible to this vulnerability, ask your network admins why they hadnt addressed this a long time ago.
Sure, if you sign up for a free account, do nothing to configure it, you can fiddle with connection settings like this… Why is this attack shocking or scary to anyone?
Funny,
I studied the variable based installer generator years ago because I needed to figure out some stuff for macOS Installer signing, didn’t really consider the security implications…
But CWC is really a bit of a nightmare, I do wish they’d fix it properly, and either make the on prem version a container or give us back linux compatibility- it’s been years
> Beggs said the phishing attacks that sparked their advisory stemmed from an instance that was not hosted by ConnectWise.
I’m pretty confident this is a lie. The email addresses receiving the phishing attempts are associated with ConnectWise Control Cloud accounts – their hosted service. These aren’t email addresses used within ConnectWise Control (ScreenConnect) instances, and there is no equivalent in self-hosted instances.
I’d like to hear ConnectWise explain where the spammers got a list of ConnectWise Control Cloud (hosted) customers’ emails. I don’t think they’ve publicly acknowledged a breach that would’ve disclosed those email addresses. I work with MSPs that use ConnectWise Control, and those who self-host aren’t getting hit by this phishing campaign, while the hosted customers are. Hosted customers using unique, non-published email addresses for their ConnectWise Control Cloud accounts are getting these phishing emails, so I’m fairly certain that these were leaked from ConnectWise somehow.
I will agree with Beggs that the scenario described by Pyle and the scenario addressed by the ConnectWise advisory are unrelated. While the immediate risk from the scenario addressed by the ConnectWise advisory is much more dangerous (takeover of an MSP’s ConnectWise Control instances), the scenario described by Pyle points to more insidious issues in important parts of ConnectWise Control.