A recent scoop by Reuters revealed that mobile apps for the U.S. Army and the Centers for Disease Control and Prevention (CDC) were integrating software that sends visitor data to a Russian company called Pushwoosh, which claims to be based in the United States. But that story omitted an important historical detail about Pushwoosh: In 2013, one of its developers admitted to authoring the Pincer Trojan, malware designed to surreptitiously intercept and forward text messages from Android mobile devices.
Pushwoosh says it is a U.S. based company that provides code for software developers to profile smartphone app users based on their online activity, allowing them to send tailor-made notifications. But a recent investigation by Reuters raised questions about the company’s real location and truthfulness.
The Army told Reuters it removed an app containing Pushwoosh in March, citing “security concerns.” The Army app was used by soldiers at one of the nation’s main combat training bases.
Reuters said the CDC likewise recently removed Pushwoosh code from its app over security concerns, after reporters informed the agency Pushwoosh was not based in the Washington D.C. area — as the company had represented — but was instead operated from Novosibirsk, Russia.
Pushwoosh’s software also was found in apps for “a wide array of international companies, influential nonprofits and government agencies from global consumer goods company Unilever and the Union of European Football Associations (UEFA) to the politically powerful U.S. gun lobby, the National Rifle Association (NRA), and Britain’s Labour Party.”
The company’s founder Max Konev told Reuters Pushwoosh “has no connection with the Russian government of any kind” and that it stores its data in the United States and Germany.
But Reuters found that while Pushwoosh’s social media and U.S. regulatory filings present it as a U.S. company based variously in California, Maryland and Washington, D.C., the company’s employees are located in Novosibirsk, Russia.
Reuters also learned that the company’s address in California does not exist, and that two LinkedIn accounts for Pushwoosh employees in Washington, D.C. were fake.
“Pushwoosh never mentioned it was Russian-based in eight annual filings in the U.S. state of Delaware, where it is registered, an omission which could violate state law,” Reuters reported.
Pushwoosh admitted the LinkedIn profiles were fake, but said they were created by a marketing firm to drum up business for the company — not misrepresent its location.
Pushwoosh told Reuters it used addresses in the Washington, D.C. area to “receive business correspondence” during the coronavirus pandemic. A review of the Pushwoosh founder’s online presence via Constella Intelligence shows his Pushwoosh email address was tied to a phone number in Washington, D.C. that was also connected to email addresses and account profiles for over a dozen other Pushwoosh employees.
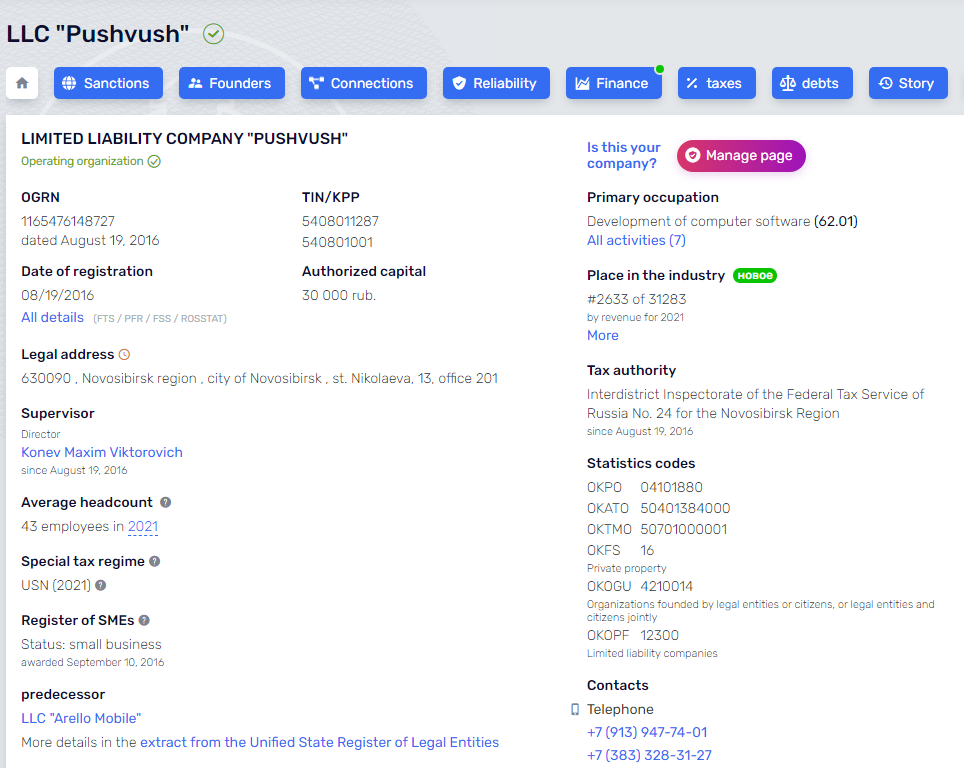
Pushwoosh was incorporated in Novosibirsk, Russia in 2016.
THE PINCER TROJAN CONNECTION
The dust-up over Pushwoosh came in part from data gathered by Zach Edwards, a security researcher who until recently worked for the Internet Safety Labs, a nonprofit organization that funds research into online threats.
Edwards said Pushwoosh began as Arello-Mobile, and for several years the two co-branded — appearing side by side at various technology expos. Around 2016, he said, the two companies both started using the Pushwoosh name.
A search on Pushwoosh’s code base shows that one of the company’s longtime developers is a 41-year-old from Novosibirsk named Yuri Shmakov. In 2013, KrebsOnSecurity interviewed Shmakov for the story, “Who Wrote the Pincer Android Trojan?” wherein Shmakov acknowledged writing the malware as a freelance project.
Shmakov told me that, based on the client’s specifications, he suspected it might ultimately be put to nefarious uses. Even so, he completed the job and signed his work by including his nickname in the app’s code.
“I was working on this app for some months, and I was hoping that it would be really helpful,” Shmakov wrote. “[The] idea of this app is that you can set it up as a spam filter…block some calls and SMS remotely, from a Web service. I hoped that this will be [some kind of] blacklist, with logging about blocked [messages/calls]. But of course, I understood that client [did] not really want this.”
Shmakov did not respond to requests for comment. His LinkedIn profile says he stopped working for Arello Mobile in 2016, and that he currently is employed full-time as the Android team leader at an online betting company.
In a blog post responding to the Reuters story, Pushwoosh said it is a privately held company incorporated under the state laws of Delaware, USA, and that Pushwoosh Inc. was never owned by any company registered in the Russian Federation.
“Pushwoosh Inc. used to outsource development parts of the product to the Russian company in Novosibirsk, mentioned in the article,” the company said. “However, in February 2022, Pushwoosh Inc. terminated the contract.”
However, Edwards noted that dozens of developer subdomains on Pushwoosh’s main domain still point to JSC Avantel, an Internet provider based in Novosibirsk, Russia.
WAR GAMES
Edwards said the U.S. Army’s app had a custom Pushwoosh configuration that did not appear on any other customer implementation.
“It had an extremely custom setup that existed nowhere else,” Edwards said. “Originally, it was an in-app Web browser, where it integrated a Pushwoosh javascript so that any time a user clicked on links, data went out to Pushwoosh and they could push back whatever they wanted through the in-app browser.”
An Army Times article published the day after the Reuters story ran said at least 1,000 people downloaded the app, which “delivered updates for troops at the National Training Center on Fort Irwin, Calif., a critical waypoint for deploying units to test their battlefield prowess before heading overseas.”
In April 2022, roughly 4,500 Army personnel converged on the National Training Center for a war games exercise on how to use lessons learned from Russia’s war against Ukraine to prepare for future fights against a major adversary such as Russia or China.
Edwards said despite Pushwoosh’s many prevarications, the company’s software doesn’t appear to have done anything untoward to its customers or users.
“Nothing they did has been seen to be malicious,” he said. “Other than completely lying about where they are, where their data is being hosted, and where they have infrastructure.”
GOV 311
Edwards also found Pushwoosh’s technology embedded in nearly two dozen mobile apps that were sold to cities and towns across Illinois as a way to help citizens access general information about their local communities and officials.
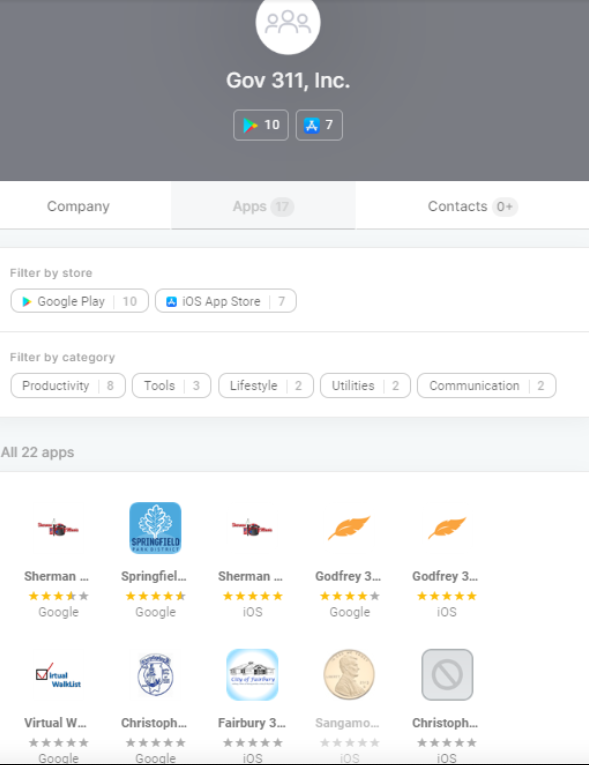 The Illinois apps that bundled Pushwoosh’s technology were produced by a company called Government 311, which is owned by Bill McCarty, the current director of the Springfield Office of Budget and Management. A 2014 story in The State Journal-Register said Gov 311’s pricing was based on population, and that the app would cost around $2,500 per year for a city with approximately 25,000 people.
The Illinois apps that bundled Pushwoosh’s technology were produced by a company called Government 311, which is owned by Bill McCarty, the current director of the Springfield Office of Budget and Management. A 2014 story in The State Journal-Register said Gov 311’s pricing was based on population, and that the app would cost around $2,500 per year for a city with approximately 25,000 people.
McCarty told KrebsOnSecurity that his company stopped using Pushwoosh “years ago,” and that it now relies on its own technology to provide push notifications through its 311 apps.
But Edwards found some of the 311 apps still try to phone home to Pushwoosh, such as the 311 app for Riverton, Ill.
“Riverton ceased being a client several years ago, which [is] probably why their app was never updated to change out Pushwoosh,” McCarty explained. “We are in the process of updating all client apps and a website refresh. As part of that, old unused apps like Riverton 311 will be deleted.”
FOREIGN ADTECH THREAT?
Edwards said it’s far from clear how many other state and local government apps and Web sites rely on technology that sends user data to U.S. adversaries overseas. In July, Congress introduced an amended version of the Intelligence Authorization Act for 2023, which included a new section focusing on data drawn from online ad auctions that could be used to geolocate individuals or gain other information about them.
Business Insider reports that if this section makes it into the final version — which the Senate also has to pass — the Office for the Director of National Intelligence (ODNI) will have 60 days after the Act becomes law to produce a risk assessment. The assessment will look into “the counterintelligence risks of, and the exposure of intelligence community personnel to, tracking by foreign adversaries through advertising technology data,” the Act states.
Edwards says he’s hoping those changes pass, because what he found with Pushwoosh is likely just a drop in a bucket.
“I’m hoping that Congress acts on that,” he said. “If they were to put a requirement that there’s an annual audit of risks from foreign ad tech, that would at least force people to identify and document those connections.”





One of the reasons why you should hesitate to install apps that haven’t been developed in years. Not only for vulns, but also code that would not pass audit anymore.
Novosibirsk, Russia. is in the middle of nowhere , in the center of the country along the southern line of Serbia
the southern line of WHAT ?
Siberia, Russia, not Serbia, which is a country several countries away from Russia.
Siberia . not Serbia LOL
Information is often valuable.
Just knowing the number of users on a daily basis in a military point is more than enough to “pick up” mobilisation when it starts, ie and many locations are very specific to precise corps.
This smells very targeted. Hopefully folks were aware. Cofcof
Not in this case. NTC is not an indication of mobilization. They have annual training events, and don’t really get any busier with mobilization. Thats what a MOB station is for.
The Army essentially lucked out with mitigating this, by simply not having popular apps. They built a cheap app, it was in use for a couple of years, then they stopped using in 2019. It was still available, but the info was so outdated that soldiers didn’t use it, let alone learn it existed. Even if soldiers just left it on their phones, it isn’t background malware, it has to be running in the foreground to execute this particular js code.
It’s like finding an old version of an annual conference app. You know how RSA or BlackHat will have an informational app. That’s what the Army made for NTC. But it sucked and not many soldiers installed it.
The world will probably go on. Who will be punished?
What other hostile entities are tapping detailed information like this, and tax returns, and medical records.
Well we have a partial list of our enemies:
The US army
The US CDC
Unilever
The Union of European Football Associations (UEFA)
The National Rifle Association (NRA)
British Labour Party
Who will nail them and fix them permanently?
“Enemies” is a bit much. Malice vs Incompetence, that whole bit.
The wording is individual choice.
It’s worth looking at how associated actors worked in parts of Ukraine. They prepared lists of those to “be sorted out” in advance and distributed them to the commanders of the invasion. When they got there they knew who to go for. Many didn’t make it.
I prefer that people like that don’t get information. Those who give it them bear some responsibility.
You’re right, they bear some responsibilty, but intent or lack of is also related.
If someone removes the brake pedal from the school bus on purpose, yes.
If a mechanic working on the brakes is told to take lunch before done, no.
There are quite a few Russian companies that pretend to be in US. A larger one that comes to mind is Acronis.
Interesting, on their region selection screen they don’t list Russia or Ukraine… must be hiding something
“Other than completely lying about where they are, where their data is being hosted, and where they have infrastructure.”
For which there is a combination of no automatic checking into prior to awarding and deploying contracts, no automatic security investigation or lockout policy to deal with once discovered and no tangible automatic penalties after the fact to deter future plain sight international frauds. This is the klaxon, not that Army deployed one questionable app or Illinois has a handful of outdated 311 phone home calls to Russia. How does it get that far along without anyone doing the checks? It doesn’t have to be Russia either, that just underscores the lack of oversight. It could be any nation including any ally.
The original story from Reuters was fascinating and I’m impressed that Brian dug deeper and found even more info. Kudos to you, Mr. Krebs.
The online ad universe is way too dangerous. It relies on javascript to serve up ads. In security that is what used to be called third-party code which was highly frowned upon. The krebsonsecurity.com site is a rarity these days for it lacks this third party code, yet still has ads. Mobile apps leverage the very same ad infrastructure using the very same techniques within apps rather than within websites.
This status quo allows something like Pushwoosh to hide in plain siight.
“We removed the spyware from our app for fear it might be spyware”.
“Pushwoosh admitted the LinkedIn profiles were fake, but said they were created by a marketing firm to drum up business for the company — not misrepresent its location.” Gee, that’s so much better.
Summary and question, the guy coded an app that ended up being part of malware, before he worked for this company. Never said otherwise, not hiding it. The app has not been seen to do anything malicious, at all. So I am left wondering, what threat is the story about? Usually, you nail the tail on the donkey, but I don’t see a crime here, other than lack of awareness by the users. So this is about sloppy auditing, or is there a part 2 to this story?
The part 2 to the story is the location of the server farm in Russia and data from the US Army, especially relative to Ukarine. Beyond that specific item, there is the larger problem of US government and citizen data possibly stored on that server farm.
Never even mentioned some of the ominous subdomains chosen by pushwoosh…. might be understood in a different context now:
perl-harbor.svc-nue.pushwoosh[.]com
perl-harbor.stage.pushwoosh[.]com
Kinda reminds me of the ‘Golden Age’ of Hollywood… when actors with ‘foreign sounding’ names felt compelled to anglicize, to have a chance at stardom.
Russians lying to carve out a market in America? Sure. But the American people’s racist and xenophobic instincts can’t be overlooked either.
Where did this US army and CDC outsource their mobile app development?
India?
Or Is it again run by someone who has no idea what cybersecurity is but have bunch of useless certifications like CISSP, CCISO,…. This is what most corporate executives in US are when it comes to cybersecurity. Wasting millions of dollar resources to detect holes in code written by script kiddies with elementary school education!!
These days everyone needs to keep eyes open, think about every move and check everything. You cannot be indifferent to cybersecurity.
Not sure if ‘perl-harbor.xxx’ is ominous. Joint Base Pearl Harbor/Hickam has had at least 2 apps myMC2 (~2013) and Pacific Air Forces App (~2020) that allow tagging, push updates, and have activity tracking.
But it doesn’t say pearl, it says perl. Nice try.
Perl is a programming language. A play on words. US military does that too. Silly stuff especially in acronym making.
Which makes it even more obviously deliberate, but to what end?
By itself a pun-ish domain choice referencing a day of infamy,
yet a choice. It’s the sum of all choices that make a motive.
Have been trying to email you using “bk@krebsonsecurity.com” with both gmail & hotmail same result!?!?!
Here’s what I’ve been trying to send:
https://darknetlive.com/post/russian-lockbit-ransomware-operator-arrested-in-canada-cf515893
Russian LockBit Ransomware Operator Arrested in Canada
Europol has announced today the arrest of a Russian national linked to LockBit ransomware attacks targeting critical infrastructure organizations and high-profile companies worldwide.
Is there a NEW email we should use?
Here’s the error message I get:
“Delivery has failed to these recipients or groups:
Brian Krebs (bk@krebsonsecurity.com)
Your message wasn’t delivered. Despite repeated attempts to deliver your message, the recipient’s email system refused to accept a connection from your email system.
Contact the recipient by some other means (by phone, for example) and ask them to tell their email admin that it appears that their email system is refusing connections from your email server. Give them the error details shown below. It’s likely that the recipient’s email admin is the only one who can fix this problem.
For Email Admins
No connection could be made because the target computer actively refused it. This usually results from trying to connect to a service that is inactive on the remote host – that is, one with no server application running. For more information and tips to fix this issue see this article: https://go.microsoft.com/fwlink/?LinkId=389361“
US “good enough” cyber-security?
“I have always depended on the kindness of strangers.”
A Streetcar Named Desire, Tennessee Williams, 1947
From Reuters: “Google said privacy was a “huge focus” for the company…”
Hilarious!
Brian, can you confirm that this is you on mastodon? You probably have a high risk of impersonation.
@briankrebs@infosec.exchange
Have you considered verifying this site? https://wiki.infosec.exchange/faq/verification/how_do_i_get_verified
Yes, that’s me. You can see the same on my twitter profile, https://www.twitter.com/briankrebs
Actually, interesting. Good job Brian.
My problem, is, with the armed forces. Geolocating a segment of your forces is never a good idea. This one uses phone technology to ” update” positions, it may help you find” lost” people, or update the front, the connected soldier verses the connected enemy. Tag, you are in that ditch. I can see why that is of use on an army base, but in the for a battlefield? Showing, who just got trained? No longer does the company have to hide in an area, to secure it, just activate a few phones, and leave them in a field. And turn on a stingray to connect them. No more sending men into battle, cool. All the army buddies should love that. They can be back in town swilling a beer, training.
Sounds like you’re talking about geolocating fitness trackers. The apps in question were not tracking geolocation.
This has been both an interesting and scary article. Interesting, because after an number of years dealing with classified information transmitted to and from government sources, I had thought that there had emerged a standard for government procurement that checked and prohibited use of second or third party software developed outside the USA. Obviously this has not happened. I hope someone with the Federal agencies sees this article. In fact, we need State agencies to have the same checks.
Scary, because of the comment about the US Army exercise to teach what lessons had been learned from Ukraine fighting. Any of this information, even partially located on a Russian server, would be of benefit to the Russians. This becomes not just a bad information management/connection problem but a larger security issue. Hopefully, Mr. Krebs can continue to follow this story
sada