
Peter is an IT manager for a technology manufacturer that got hit with a Russian ransomware strain called “Zeppelin” in May 2020. He’d been on the job less than six months, and because of the way his predecessor architected things, the company’s data backups also were encrypted by Zeppelin. After two weeks of stalling their extortionists, Peter’s bosses were ready to capitulate and pay the ransom demand. Then came the unlikely call from an FBI agent. “Don’t pay,” the agent said. “We’ve found someone who can crack the encryption.”
Peter, who spoke candidly about the attack on condition of anonymity, said the FBI told him to contact a cybersecurity consulting firm in New Jersey called Unit 221B, and specifically its founder — Lance James. Zeppelin sprang onto the crimeware scene in December 2019, but it wasn’t long before James discovered multiple vulnerabilities in the malware’s encryption routines that allowed him to brute-force the decryption keys in a matter of hours, using nearly 100 cloud computer servers.
In an interview with KrebsOnSecurity, James said Unit 221B was wary of advertising its ability to crack Zeppelin ransomware keys because it didn’t want to tip its hand to Zeppelin’s creators, who were likely to modify their file encryption approach if they detected it was somehow being bypassed.
This is not an idle concern. There are multiple examples of ransomware groups doing just that after security researchers crowed about finding vulnerabilities in their ransomware code.
“The minute you announce you’ve got a decryptor for some ransomware, they change up the code,” James said.
But he said the Zeppelin group appears to have stopped spreading their ransomware code gradually over the past year, possibly because Unit 221B’s referrals from the FBI let them quietly help nearly two dozen victim organizations recover without paying their extortionists.
In a blog post published today to coincide with a Black Hat talk on their discoveries, James and co-author Joel Lathrop said they were motivated to crack Zeppelin after the ransomware gang started attacking nonprofit and charity organizations.
“What motivated us the most during the leadup to our action was the targeting of homeless shelters, nonprofits and charity organizations,” the two wrote. “These senseless acts of targeting those who are unable to respond are the motivation for this research, analysis, tools, and blog post. A general Unit 221B rule of thumb around our offices is: Don’t [REDACTED] with the homeless or sick! It will simply trigger our ADHD and we will get into that hyper-focus mode that is good if you’re a good guy, but not so great if you are an ***hole.”
The researchers said their break came when they understood that while Zeppelin used three different types of encryption keys to encrypt files, they could undo the whole scheme by factoring or computing just one of them: An ephemeral RSA-512 public key that is randomly generated on each machine it infects.
“If we can recover the RSA-512 Public Key from the registry, we can crack it and get the 256-bit AES Key that encrypts the files!” they wrote. “The challenge was that they delete the [public key] once the files are fully encrypted. Memory analysis gave us about a 5-minute window after files were encrypted to retrieve this public key.”
Unit 221B ultimately built a “Live CD” version of Linux that victims could run on infected systems to extract that RSA-512 key. From there, they would load the keys into a cluster of 800 CPUs donated by hosting giant Digital Ocean that would then start cracking them. The company also used that same donated infrastructure to help victims decrypt their data using the recovered keys.
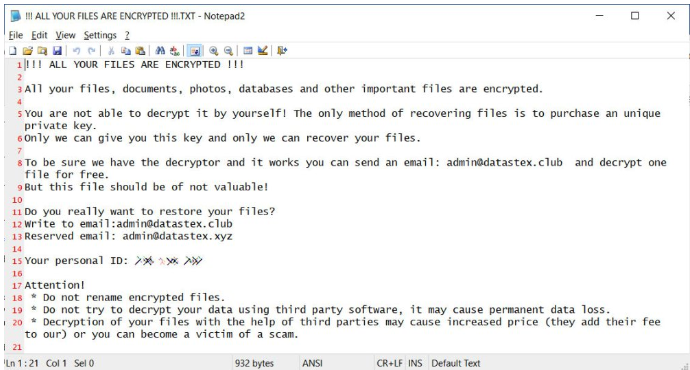
A typical Zeppelin ransomware note.
Jon is another grateful Zeppelin ransomware victim who was aided by Unit 221B’s decryption efforts. Like Peter, Jon asked that his last name and that of his employer be omitted from the story, but he’s in charge of IT for a mid-sized managed service provider that got hit with Zeppelin in July 2020.
The attackers that savaged Jon’s company managed to phish credentials and a multi-factor authentication token for some tools the company used to support customers, and in short order they’d seized control over the servers and backups for a healthcare provider customer.
Jon said his company was reluctant to pay a ransom in part because it wasn’t clear from the hackers’ demands whether the ransom amount they demanded would provide a key to unlock all systems, and that it would do so safely.
“They want you to unlock your data with their software, but you can’t trust that,” Jon said. “You want to use your own software or someone else who’s trusted to do it.”
In August 2022, the FBI and the Cybersecurity & Infrastructure Security Agency (CISA) issued a joint warning on Zeppelin, saying the FBI had “observed instances where Zeppelin actors executed their malware multiple times within a victim’s network, resulting in the creation of different IDs or file extensions, for each instance of an attack; this results in the victim needing several unique decryption keys.”
The advisory says Zeppelin has attacked “a range of businesses and critical infrastructure organizations, including defense contractors, educational institutions, manufacturers, technology companies, and especially organizations in the healthcare and medical industries. Zeppelin actors have been known to request ransom payments in Bitcoin, with initial amounts ranging from several thousand dollars to over a million dollars.”
The FBI and CISA say the Zeppelin actors gain access to victim networks by exploiting weak Remote Desktop Protocol (RDP) credentials, exploiting SonicWall firewall vulnerabilities, and phishing campaigns. Prior to deploying Zeppelin ransomware, actors spend one to two weeks mapping or enumerating the victim network to identify data enclaves, including cloud storage and network backups, the alert notes.
Jon said he felt so lucky after connecting with James and hearing about their decryption work, that he toyed with the idea of buying a lottery ticket that day.
“This just doesn’t usually happen,” Jon said. “It’s 100 percent like winning the lottery.”
By the time Jon’s company got around to decrypting their data, they were forced by regulators to prove that no patient data had been exfiltrated from their systems. All told, it took his employer two months to fully recover from the attack.
“I definitely feel like I was ill-prepared for this attack,” Jon said. “One of the things I’ve learned from this is the importance of forming your core team and having those people who know what their roles and responsibilities are ahead of time. Also, trying to vet new vendors you’ve never met before and build trust relationships with them is very difficult to do when you have customers down hard now and they’re waiting on you to help them get back up.”
A more technical writeup on Unit 221B’s discoveries (cheekily titled “0XDEAD ZEPPELIN”) is available here.




Love the Unit Name… Throwback to Mr.Holmes!
Very nice. Does anyone have a YouTube link to James’ talk at Black Hat Dubai or elsewhere?
Morris was one of the first villains I recall. That was a wonderful example. It was somewhat malicious, but mostly innocuous. Well, it’s kind of harmless… The feds arrived at MIT all fired up but completely clueless. It wasn’t even the fault of anyone at MIT; it was the fault of some guy at Cornell.
Hello,
Great write-up, I appreciate the details and the link to the write-up about how this issue was handled. It looks to me like Zepplin found its temporary success, or lack thereof by using targeted attack vector campaigns. These breaches in security were caused by; unsecured Remote Desktop Protocol (RDP) credentials and protocols, exploitation of SonicWall firewall vulnerabilities, and targeted phishing.
Best,
Jennifer C.
Hi Brian, there is a small mistake here
“In a blog post published today to coincide with a Black Hat Dubai talk” -> it’s not Black Hat Dubai, its Black Hat Middle East, hosted in Saudi Arabia. https://blackhatmea.com/node/727
Thanks. This was fixed on the site earlier this morning.
Awesome article Brian, always good, and kudos to the white knights who figured this out!
Brian, thanks again for another great article. I’ve been reading KrebsOnSecurity since you first started breaking detailed news on these bad actors work on ATM skimmers. Always a great read and so clearly outlined and detailed!
Server logjam? I can’t see the last 10 days worth of posts. The index page shows this post as the most recent, even though it’s a week and a half old and you post two or three times a week.
Emailed you numerous times using bk@krebsonsecurity.com keeps returning:
“The response was:
The recipient server did not accept our requests to connect. Learn more at https://support.google.com/mail/answer/7720 [krebsonsecurity.com 130.211.45.45: timed out] ”
Is there a different email to use?
Anyway I was trying to share some news , with you:
“Hi Brian,
Saw this on DarkNetLive…
https://darknetlive.com/post/russian-lockbit-ransomware-operator-arrested-in-canada-cf515893
Scanned your site didn’t see it – if you already posted it – my apologies; if not check it out…
Love the blog (although to me calling it a blog does not do it justice) – you’re the preeminent source for all things cyber/hacks/security!!
Cheers, JC”
I had included the actual court docs also, but unable to attach here…
Brian,
Is there a different email than: Brian Krebs ??
Nothing seems to get thru using that one…
“Hi Brian,
Saw this on DarkNetLive…
https://darknetlive.com/post/russian-lockbit-ransomware-operator-arrested-in-canada-cf515893
Scanned your site didn’t see it – if you already posted it – my apologies; if not check it out…
Cheers, JC”
email not working either…
Foodle is a word-guessing game for those who love or have knowledge of food. The game only offers one puzzle per day and challenges players all over the world. Each player will have a total of 6 guesses to find a mysterious 5-letter word. Clues will appear through each guess if matching letters appear. Players can rely on the color of the tiles to make the next guess.
Hello,
Great write-up, I appreciate the details and the link to the write-up about how this issue was handled. It looks to me like Zepplin found its temporary success, or lack thereof by using targeted attack vector campaigns. These breaches in security were caused by; unsecured Remote Desktop Protocol (RDP) credentials and protocols, exploitation of SonicWall firewall vulnerabilities, and targeted phishing.
Best,
Jennifer C.