A financial cybercrime group calling itself the Disneyland Team has been making liberal use of visually confusing phishing domains that spoof popular bank brands using Punycode, an Internet standard that allows web browsers to render domain names with non-Latin alphabets like Cyrillic.
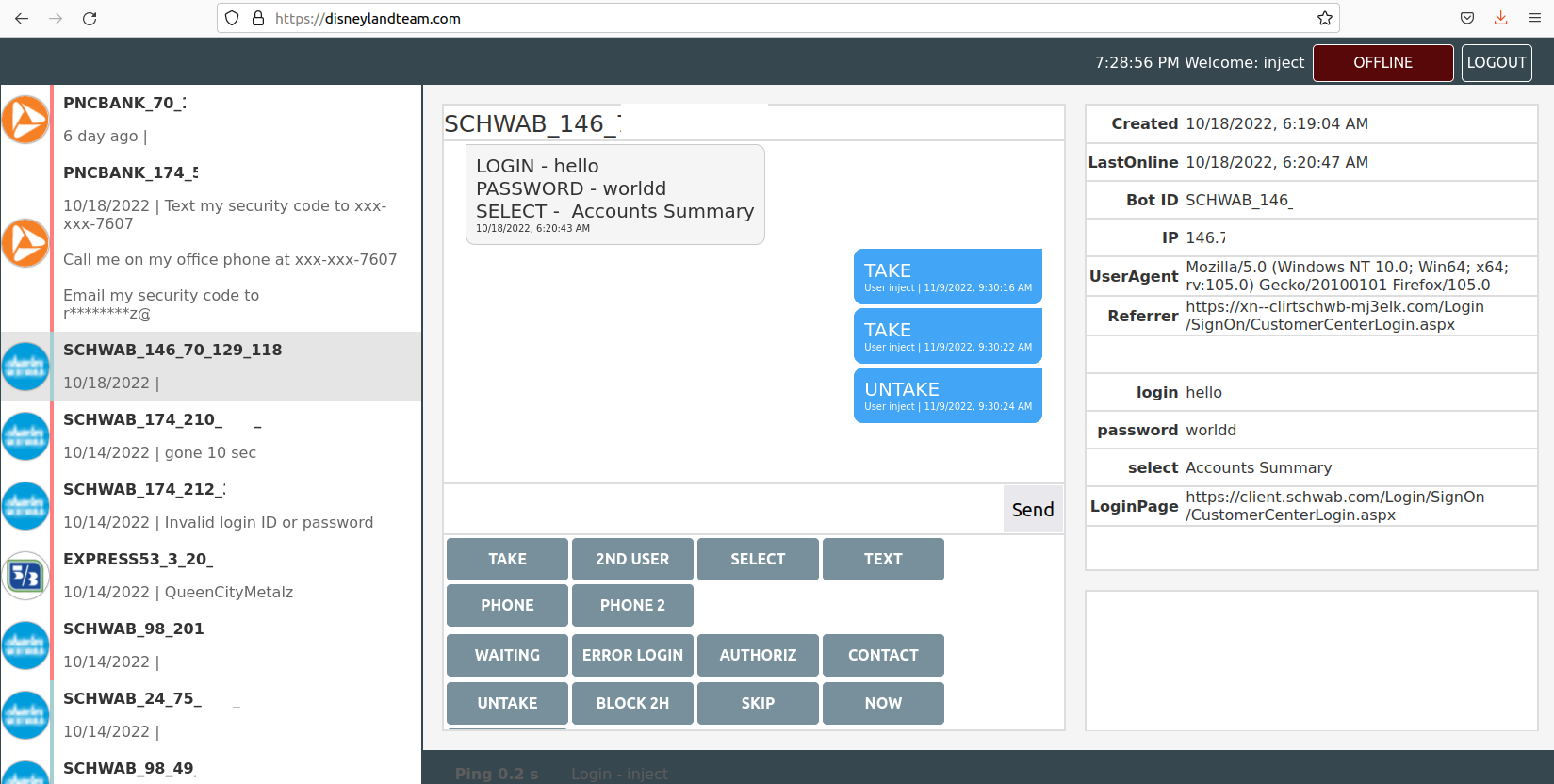
The Disneyland Team’s Web interface, which allows them to interact with malware victims in real time to phish their login credentials using phony bank websites.
The Disneyland Team uses common misspellings for top bank brands in its domains. For example, one domain the gang has used since March 2022 is ushank[.]com — which was created to phish U.S. Bank customers.
But this group also usually makes use of Punycode to make their phony bank domains look more legit. The U.S. financial services firm Ameriprise uses the domain ameriprise.com; the Disneyland Team’s domain for Ameriprise customers is https://www.xn--meripris-mx0doj[.]com [brackets added to defang the domain], which displays in the browser URL bar as ạmeriprisẹ[.]com.
Look carefully, and you’ll notice small dots beneath the “a” and the second “e”. You could be forgiven if you mistook one or both of those dots for a spec of dust on your computer screen or mobile device.
This candid view inside the Disneyland Team comes from Alex Holden, founder of the Milwaukee-based cybersecurity consulting firm Hold Security. Holden’s analysts gained access to a Web-based control panel the crime group has been using to keep track of victim credentials (see screenshot above). The panel reveals the gang has been operating dozens of Punycode-based phishing domains for the better part of 2022.
Have a look at the Punycode in this Disneyland Team phishing domain: https://login2.xn--mirtesnbd-276drj[.]com, which shows up in the browser URL bar as login2.ẹmirạtesnbd[.]com, a domain targeting users of Emirates NBD Bank in Dubai.
Here’s another domain registered this year by the Disneyland Team: https://xn--clientchwb-zxd5678f[.]com, which spoofs the login page of financial advisor Charles Schwab with the landing page of cliẹntșchwab[.]com. Again, notice the dots under the letters “e” and “s”. Another Punycode domain of theirs sends would-be victims to cliẹrtschwạb[.]com, which combines a brand misspelling with Punycode.
We see the same dynamic with the Disneyland Team Punycode domain https://singlepoint.xn--bamk-pxb5435b[.]com, which translates to singlepoint.ụșbamk[.]com — again phishing U.S. Bank customers.
What’s going on here? Holden says the Disneyland Team is Russian-speaking — if not also based in Russia — but it is not a phishing gang per se. Rather, this group uses the phony bank domains in conjunction with malicious software that is already secretly installed on a victim’s computer.
Holden said the Disneyland Team domains were made to help the group steal money from victims infected with a powerful strain of Microsoft Windows-based banking malware known as Gozi 2.0/Ursnif. Gozi specializes in collecting credentials, and is mainly used for attacks on client-side online banking to facilitate fraudulent bank transfers. Gozi also allows the attackers to connect to a bank’s website using the victim’s computer.
In years past, crooks like these would use custom-made “web injects” to manipulate what Gozi victims see in their Web browser when they visit their bank’s site. These web injects allowed malware to rewrite the bank’s HTML code on the fly, and copy and/or intercept any data users would enter into a web-based form, such as a username and password.
Most Web browser makers, however, have spent years adding security protections to block such nefarious activity. As a result, the Disneyland Team simply tries to make their domains look as much like the real thing as possible, and then funnel victims toward interacting with those imposter sites.
“The reason that it is infeasible for them to use in-browser injects include browser and OS protection measures, and difficulties manipulating dynamic pages for banks that require multi-factor authentication,” Holden said.
In reality, the fake bank website overlaid by the Disneyland Team’s malware relays the victim’s browser activity through to the real bank website, while allowing the attackers to forward any secondary login requests from the bank, such as secret questions or multi-factor authentication challenges.
The Disneyland Team included instructions for its users, noting that when the victim enters their login credentials, he sees a 10-second spinning wheel, and then the message, “Awaiting back office approval for your request. Please don’t close this window.”
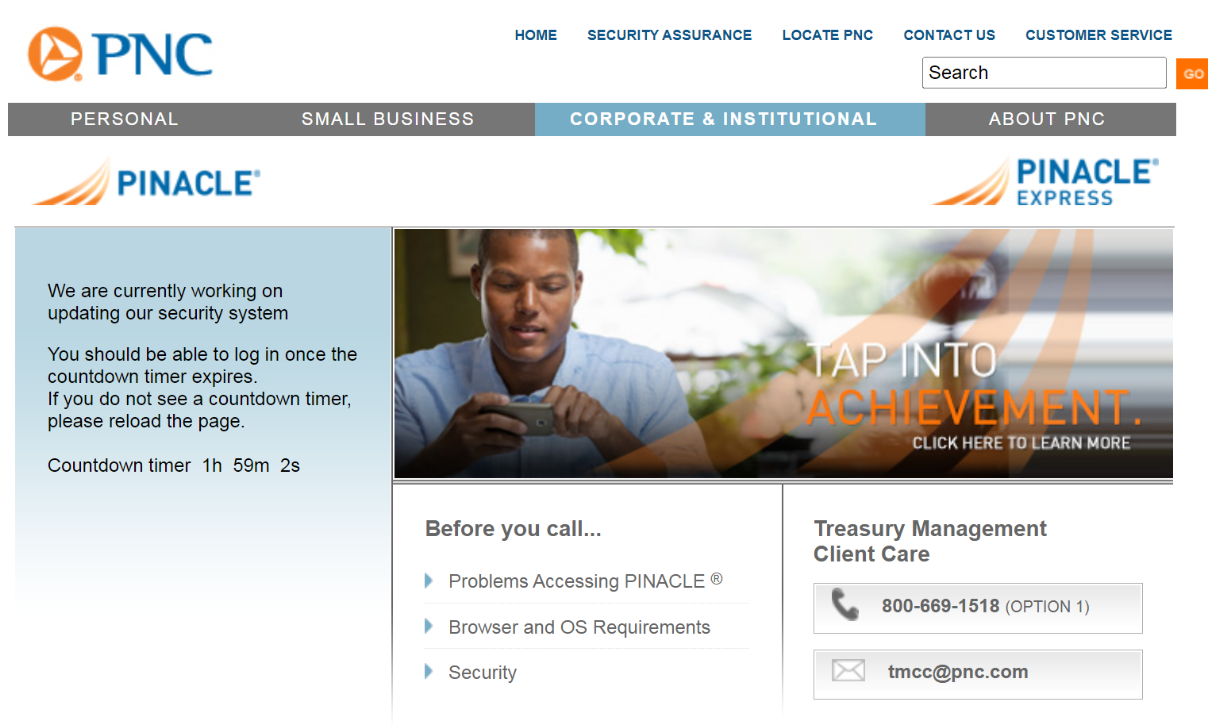
A fake PNC website overlay or “web inject” displaying a message intended to temporarily prevent the user from accessing their account.
The “SKIP” button in the screenshot above sends the user to the real bank login page, “in case the account is not interesting to us,” the manual explains. “Also, this redirect works if none of our operators are working at the time.”
The “TAKE” button in the Disneyland Team control panel allows users or affiliates to claim ownership over a specific infected machine or bot, which then excludes other users from interacting with that victim.
In the event that it somehow takes a long time to get the victim (bot) connected to the Disneyland Team control panel, or if it is necessary to delay a transaction, users can push a button that prompts the following message to appear on the victim’s screen:
“Your case ID number is 875472. An online banking support representative will get in touch shortly. Please provide your case ID number, and DO NOT close this page.”
The Disneyland user manual explains that the panel can be used to force the victim to log in again if they transmit invalid credentials. It also has other options for stalling victims whilst their accounts are drained. Another fake prompt the panel can produce shows the victim a message saying, “We are currently working on updating our security system. You should be able to log in once the countdown timer expires.”
The user manual says this option blocks the user from accessing their account for two hours. “It is possible to block for an hour with this button, in this case they get less frustrated, within the hours ddos will kill their network.”
Cybercrime groups will sometimes launch distributed denial-of-service (DDoS) attacks on the servers of the companies they’re trying to rob — which is usually intended to distract victims from their fleecing, although Holden said it’s unclear if the Disneyland Team employs this tactic as well.
For many years, KrebsOnSecurity tracked the day-to-day activities of a similar malware crew that used web injects and bots to steal tens of millions of dollars from small- to mid-sized businesses across the United States.
At the end of each story, I would close with a recommendation that anyone concerned about malware snarfing their banking information should strongly consider doing their online banking from a dedicated, security-hardened system which is only used for that purpose. Of course, the dedicated system approach works only if you always use that dedicated system for managing your account online.
Those stories also observed that since the vast majority of the malicious software used in cyberheists is designed to run only on Microsoft Windows computers, it made sense to pick a non-Windows computer for that dedicated banking system, such as a Mac or even a version of Linux. I still stand by this advice.
In case anyone is interested, here (PDF) is a list of all phishing domains currently and previously used by the Disneyland Team.




“The “SKIP” button in the screenshot above sends the user to the real bank login page,”
I see no SKIP button in that screenshot.
He was referring to the first screenshot, it shows the panel the phishers are using.
First screenshot. Not the one immediately “above.”
look closer 🙂
So you admit that you are blind?
The security importance of a clean screen becomes apparent.
It’s not a matter of having a dirty screen, it’s the fact that immediately above that sentence is a screenshot which does not include the skip button. This was actually bad form on the part of the editor who laid out this page to leave the sentence worded that way after placing the sentence below an unrelated screenshot. Had the second screenshot appeared just after that sentence, there would be no confusion.
I was confused by the same incongruity until I scrolled back up the page to see whether it was referring to a different “image above” than the one immediately “above.”
One thing that can be important is to set up an entirely different and secret e-mail address to be used for banking. Whenever you get e-mail from the bank, if it is not to that e-mail address, then you should be very skeptical of the e-mail.
Wow. Thanks for the heads up. While I use a variety of data points to help “see” a malicious site (misspellings and lack of personalization have been easy to spot), this illustrates how much more difficult it is becoming even for the cautiously aware users. Will using the latest browser updates from Google Chrome, Microsoft Edge (Chromium) or an Outlook safe link (clicked from an updated version of MS Office 365) prevent or flag an oversight?
In Firefox, you can set it to show the full punycode (rather than have it translated to the spoofed non-Latin letters)
about:config > network.IDN_show_punycode = TRUE
However, it seems the use of punycode here is used in conjunction with man-in-the-browser malware already on the victim machine which redirects the victim’s browser. I would think the malware would also just switch the config too.
So in this scenario, the computer is pwned already. The best advice is what Brian said, have dedicated hardware for online banking that you always use for banking, and never use for anything else.
https://krebsonsecurity.com/2018/03/look-alike-domains-and-visual-confusion/
When was this activity initially discovered? IS it possible it was discovered before Gozi operators purportedly moved on from targeting the banking sector? Are the old and new operations “operating” concurrently?
Strip punycode disguises in Firefox by changing this built-in setting:
Erase the URL and type
about:config
The agree/understand the risks etc and continue.
type “puny” in the search settings box
One result should appear:
network.IDN_show_punycode (false)
Double-click so it’s True
Close the tab. That’s it.
The Chrome extension PhishAI used to block punycode but the extension fell out of favor for some reason.
FYI, the website centralops(.) net wll decipher those punycode, phishing domain names
I always, without exception, access my bank by opening a Windows Sandbox instance, and using MS Edge within that. I never type in the banking address because I have established links on that desktop. Is this “secure enough” ?
I always, without exception, access my bank by opening a Windows Sandbox instance, and using MS Edge within that. I never type in the banking address because I have established links on that desktop. Is this “secure enough” ?
@PostToaster, Only you can really judge what is “secure enough” for you, but you’ve already done more than most people. I take it you also have 2 factor authentication for your banking?
No two-factor except when I can use my landline for it. Too much SIM-swapping going on.
“Look carefully, and you’ll notice small dots beneath the “a” and the second “e”.”
There seem to be even exact representatives of the same character: e.g.
а cyrillic small letter a
a latin small letter a
That seems worrying. In my mail client URLS that only differ in these characters LOOK EXACTLY THE SAME, even when hovering over them, but the URLs it then actually navigates to are different.
How to fix this? Mail clients could show the translated ‘xn--*’ url, but that of course only works for tech savvy people and as long as most hostnames are ascii based, because otherwise it will be complete gibberish to humans.
Is there a reason you aren’t recommending people using their banks app in place of a browser?
My advice skews toward businesses, which enjoy exactly zero legal protection against fraud like this. If you’re a consumer and your account gets cleaned out because of a trojan, you’re not on the hook for that loss. Businesses are.
Also, I have a hard time seeing an accountant for a business doing all they need to do with their bank from a mobile phone vs. a computer, but that’s just me.
Agree Brian, on the business preference for using a desktop/laptop for large scale ops, over a small mobile device.
I knew that at the birth of the iPhone. Run a payroll on a 2″ x 3″ screen? Right…
However, the enormous, exponential current Zelle losses, caused by gullible consumers using “weak security” SMS comms, actively sponsored by banks/credit unions, despite the Jy 2016 NIST warning, numerous FBI warnings since, and the stunner, NSA 29Jy21, says the depth of stupidity and greed in the financial world is thicker than I had perceived.
So much good luck to these Zelle banks on their conflict with defrauded, MITM consumers, with their Regulation E claims.
Based on the last 25 years of documented rampant compromise, electronic commerce is not to be trusted.
Always have a non-electronic Plan B…
I guess it is a fraud world after all.. 🙂
Do your banking from “a dedicated, security-hardened system”…meaning a Chromebook. Never use a Windows computer for on-line banking. Best would be to use a Chromebook for reading email and browsing too.
I am not sure if you are joking or not. A friend was cleaning out an abandoned house and came across a Chrome book, wondering if they could use it, they asked me for help.
In less than an hour, without myself even seeing it, we had taken it over, user data and all. (Granted, there was physical contact but it did not seem very secure in the least.)
Generally speaking, if an adversary has physical access to your device, it’s no longer your device.
One entry in your PDF has an ironic error
Trusit
https://treasurymanager.loqln-truist[.]com
Thanks Brian for your reminder of a not-new problem being dusted off by perps and inflicted on us again.
I added a firewall rule to put the kibbosh on all xn-- addresses:
^(.*\.)?.*(xn\-\-).*$
I realize this is draconian and would create an unworkable situation for users who legitimately need to access such domains, but I do not manage any users who have these needs, so for now I’m going with it. In addition to that, I prettied up and added Brian’s list to my pi-hole to specifically block that handful of domains.
I verified that Vivaldi 5.5 (on Android) catches at least some deliberate spoofs, such as the ‘apple’ demo set up by Xudong Zheng.
Wheel spinner is a game that I am sure that anyone who loves spins of fortune will be addicted to sitting in front of the computer playing this game for hours on end. The game has no age limit for players, suitable for those who want healthy entertainment and improved hand reflexes.
Wheel spinner is a game that I am sure that anyone who loves spins of fortune will be addicted to sitting in front of the computer playing this game for hours on end. The game has no age limit for players, suitable for those who want healthy entertainment and improved hand reflexes.