
Photo: BrandonKleinPhoto / Shutterstock.com
Two U.S. men have been charged with hacking into the Ring home security cameras of a dozen random people and then “swatting” them — falsely reporting a violent incident at the target’s address to trick local police into responding with force. Prosecutors say the duo used the compromised Ring devices to stream live video footage on social media of police raiding their targets’ homes, and to taunt authorities when they arrived.
Prosecutors in Los Angeles allege 20-year-old James Thomas Andrew McCarty, a.k.a. “Aspertaine,” of Charlotte, N.C., and Kya Christian Nelson, a.k.a. “ChumLul,” 22, of Racine, Wisc., conspired to hack into Yahoo email accounts belonging to victims in the United States. From there, the two allegedly would check how many of those Yahoo accounts were associated with Ring accounts, and then target people who used the same password for both accounts.
An indictment unsealed this week says that in the span of just one week in November 2020, McCarty and Nelson identified and swatted at least a dozen different victims across the country.
“The defendants then allegedly accessed without authorization the victims’ Ring devices and transmitted the audio and video from those devices on social media during the police response,” reads a statement from Martin Estrada, the U.S. Attorney for the Central District of California. “They also allegedly verbally taunted responding police officers and victims through the Ring devices during several of the incidents.”

James Thomas Andrew McCarty.
The indictment charges that McCarty continued his swatting spree in 2021 from his hometown in Kayenta, Ariz., where he called in bomb threats or phony hostage situations on more than two dozen occasions.
The Telegram and Discord aliases allegedly used by McCarty — “Aspertaine” and “Couch,” among others — correspond to an identity that was active in certain channels dedicated to SIM-swapping, a crime that involves stealing wireless phone numbers and hijacking the online financial and social media accounts tied to those numbers.
Aspertaine bragged on Discord that he’d amassed more than $330,000 in virtual currency. On Telegram, the Aspertaine/Couch alias frequented several popular SIM-swapping channels, where they initially were active as a “holder” — a SIM-swapping group member who agrees to hold SIM cards used in the heist after an account takeover is completed. Aspertaine later claimed more direct involvement in individual SIM-swapping attacks.
In September, KrebsOnSecurity broke the news about a wide-ranging federal investigation into “violence-as-a-service” offerings on Telegram and other social media networks, wherein people can settle scores by hiring total strangers to carry out physical attacks such as brickings, shootings, and firebombings at a target’s address.
The story observed that SIM swappers were especially enamored of these “IRL” or “In Real Life” violence services, which they frequently used to target one another in response to disagreements over how stolen money should be divided amongst themselves. And a number of Aspertaine’s peers on these SIM-swapping channels claimed they’d been ripped off after Aspertaine took more than a fair share from them.
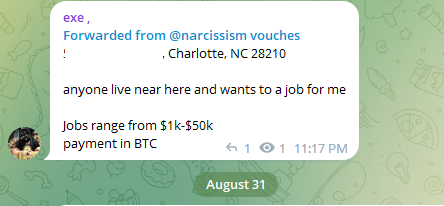
In August, a member of a popular SIM-swapping group on Telegram who was slighted by Aspertaine put out the word that he was looking for some physical violence to be visited on McCarty’s address in North Carolina. “Anyone live near here and wants to [do] a job for me,” the job ad with McCarty’s home address read. “Jobs range from $1k-$50k. Payment in BTC [bitcoin].” It’s unclear if anyone responded to that job offer.
Ring, Inc., which is owned by Amazon, said it learned bad actors used stolen customer email credentials obtained from external (non-Ring) services to access other accounts, and took immediate steps to help those customers secure their Ring accounts.
“We also supported the FBI in identifying the individuals responsible,” the company said in a written statement. “We take the security of our customers extremely seriously — that’s why we made two-step verification mandatory, conduct regular scans for Ring passwords compromised in non-Ring breaches, and continually invest in new security protections to harden our systems. We are committed to continuing to protect our customers and vigorously going after those who seek to harm them.”
KrebsOnSecurity recently published The Wages of Password ReUse: Your Money or Your Life, which noted that when normal computer users fall into the nasty habit of recycling passwords, the result is most often some type of financial loss. Whereas, when cybercriminals reuse passwords, it often costs them their freedom.
But perhaps that story should be updated, because it’s now clear that password reuse can also put you in mortal danger. Swatting attacks are dangerous, expensive hoaxes that sometimes end in tragedy.
In June 2021, an 18-year-old serial swatter from Tennessee was sentenced to five years in prison for his role in a fraudulent swatting attack that led to the death of a 60-year-old man.
In 2019, prosecutors handed down a 20-year sentence to Tyler Barriss, a then 26-year-old serial swatter from California who admitted making a phony emergency call to police in late 2017 that led to the shooting death of an innocent Kansas man.
McCarty was arrested last week, and charged with conspiracy to intentionally access computers without authorization. Prosecutors said Nelson is currently incarcerated in Kentucky in connection with unrelated investigation.
If convicted on the conspiracy charge, both defendants would face a statutory maximum penalty of five years in federal prison. The charge of intentionally accessing without authorization a computer carries a maximum possible sentence of five years. A conviction on the additional charge against Nelson — aggravated identity theft — carries a mandatory two-year consecutive sentence.
Update, 11:48 a.m., Dec. 20: Added statement from Ring. Modified description of a “holder” in the SIM-swapping parlance.




That zir is pretty freaky looking.
I’ve been looking for security cams and alarms that are not wifi and smart phone based. Very hard. They are connecting everything to the internet now.
shut it freak
Settle down internet tough guy
Those ears though.
There are several which have local storage (DVR) devices. They include remote access but you don’t have to have that set to use them.
You also can get a system like a ring or blue by adt, arlo, etc. and A) not duplicate passwords, B) enable two-factor verification. Some of these offer local SD card storage and end to end encryption.
An IP camera system could be easily made with a Synology NAS and the free Surveillance Station software. All video stored on the NAS and you could choose to make it accessible or not. There are a number of other options but this is a lot of bang for your buck.
Just in time for christmas….my guy looks like an elf with those massive ears >__<
All the better to hear the music with my dear
“Aspertaine” is that a nickname for being a Aspie ?(Asperger)
“Aspartame” spelled incorrectly? Perhaps an indicator of their IQ.
i ‘ll trade you sunshine for some gold LOL
Nelson inmate lookup
http://kool.corrections.ky.gov/KOOL/Details/529235
I’d say those charges of “TERRORISTIC THREATENING” are def related.
OK now I know this isn’t funny, and I repeat I know none of this is funny, but I do have to say I couldn’t help but giggle a bit at:
“They also allegedly verbally taunted responding police officers[…]through the Ring devices during several of the incidents.”
Stop smiling. Quit it.
Every user on the planet that cares about the current and future state of security and safety on the Internet owes their personal gratitude to Cyberhero Brian “CBK” Krebs for continuing non-stop to put his ass on the line in endless pursuit of the ne’r-do-wells (and threat actors too LOL) who want to take all of the good out of what could be a really, really, really good World Wide Web! Sound flowery? It’s true!
ne’r-do-wells or “miscreants”
free my boy james mccarty we got more licks to hit free him
Your “boy” needs to hit the treadmill
Dude, he can probably hear you. Not that anything will happen just, he probably can.
free my boy, still needing some cb licks done
free my boy, still got some cbs to cash
They did not really “hack” into the Ring doorbells. They hacked some email accounts and then found stupid users that used the same email and password for their Ring account, and simply logged in using those credentials. That’s a rather misleading headline.
They didn’t? After the intruders took over the Ring cams, they could control them remotely and access their feeds, and even taunt the police and victims through the devices. We can differ over what kinds of skills qualify one as a “hacker,” but to the average reader who has this happen to them, their Ring devices were most definitely hacked.
Krebs you are a very small minded. You do not know how the community works.
I would teach you the ins and out if you really want, imagine the amount of posts I can get you.
I have linked my email to this post if you wish to contact more about it.
Please continue being wasted on the internet for our entertainment. We are counting on you.
Wasted? I am offering a helping hand towards krebs.
If he checks his emails and reply I would legitimately help the man out.
He’s not that wasted though. He has limited time in the day for that.
You understand, you’re a busy professional.
I wonder how many users and buyers of Ring and similar systems realize what they are doing to their personal risk profile …and I fear I know the answer already.
Of course also mechanical locks can be exploited, but only by physical presence of a skilled expert or massive force. Exchanging this for an attack that can be performed fully through the internet does not look like a good idea to me.
The key phrase I picked out of this was, “…hack into Yahoo email accounts belonging to victims in the United States. From there, the two allegedly would check how many of those Yahoo accounts were associated with Ring accounts, and then target people who used the same password for both accounts.”
Took me ages to convince my wife the problem with using the same password across multiple accounts. This is just another example of how ‘lazy’ password management contributes to you being a victim.
Some people just won’t learn, until consequences finally hit them in the face. Humans are supposed to grow, mature and acquire the skillset of “thinking ahead” – and acting accordingly – before actual consequences strike! Hate to say it, but this is pretty consistent with the overall infantilism that’s hitting more and more ‘adults’ this day and age. Children (esp. young children) are naturally bad at ‘thinking ahead’, impulse control, temper control. But when it comes to ‘adults’… the failure to think and plan ahead aside, notice the increase in road rage and air rage??
https://arstechnica.com/information-technology/2022/12/swatters-used-ring-cameras-to-livestream-attacks-taunt-police-prosecutors-say/
Free mah boy Aspertaine out tha slammah
3 up M1 first of all second of all aspertaine better not snitch otherwise we going charlotte his girlfriend miranda aint safe either
that guy has a girlfriend?????
This comment will be awaiting moderation.
Aspartame, nutrisweet. Rat poison.
He might be in jail for a long time:
https://www.fourstateshomepage.com/news/northeast-oklahoma/man-accused-of-2021-threat-to-vinita-schools-in-custody/
already out on bail for christmas haha
Wtf are those his real ears? Or maybe some elf costume?
What a creepy looking dude. These guys are seen as heros to a lot of people.. their criminal charges never match the crime and the amount of intrusion they’ve caused ruins lives. DOJ treats these people like gold while the victims suffer and the DOJ treats the victims like rotting garbage. If they would start giving life sentences for crap like this… I’m betting a lot would drop out of the game but this country coddles criminals so that will never happen until we get a president that really sees the problems the DOJ causes.