When the marital infidelity website AshleyMadison.com learned in July 2015 that hackers were threatening to publish data stolen from 37 million users, the company’s then-CEO Noel Biderman was quick to point the finger at an unnamed former contractor. But as a new documentary series on Hulu reveals [SPOILER ALERT!], there was just one problem with that theory: Their top suspect had killed himself more than a year before the hackers began publishing stolen user data.
The new documentary, The Ashley Madison Affair, begins airing today on Hulu in the United States and on Disney+ in the United Kingdom. The series features interviews with security experts and journalists, Ashley Madison executives, victims of the breach and jilted spouses.

The series also touches on shocking new details unearthed by KrebsOnSecurity and Jeremy Bullock, a data scientist who worked with the show’s producers at the Warner Bros. production company Wall to Wall Media. Bullock had spent many hours poring over the hundreds of thousands of emails that the Ashley Madison hackers stole from Biderman and published online in 2015.
Wall to Wall reached out in July 2022 about collaborating with Bullock after KrebsOnSecurity published A Retrospective on the 2015 Ashley Madison Breach. That piece explored how Biderman — who is Jewish — had become the target of concerted harassment campaigns by anti-Semitic and far-right groups online in the months leading up to the hack.
Whoever hacked Ashley Madison had access to all employee emails, but they only released Biderman’s messages — three years worth. Apropos of my retrospective report, Bullock found that a great many messages in Biderman’s inbox were belligerent and anti-Semitic screeds from a former Ashley Madison employee named William Brewster Harrison.

William Harrison’s employment contract with Ashley Madison parent Avid Life Media.
The messages show that Harrison was hired in March 2010 to help promote Ashley Madison online, but the messages also reveal Harrison was heavily involved in helping to create and cultivate phony female accounts on the service.
There is evidence to suggest that in 2010 Harrison was directed to harass the owner of Ashleymadisonsucks.com into closing the site or selling the domain to Ashley Madison.
Ashley Madison’s parent company — Toronto-based Avid Life Media — filed a trademark infringement complaint in 2010 that succeeded in revealing a man named Dennis Bradshaw as the owner. But after being informed that Bradshaw was not subject to Canadian trademark laws, Avid Life offered to buy AshleyMadisonSucks.com for $10,000.
When Bradshaw refused to sell the domain, he and his then-girlfriend were subject to an unrelenting campaign of online harassment and blackmail. It now appears those attacks were perpetrated by Harrison, who sent emails from different accounts at the free email service Vistomail pretending to be Bradshaw, his then-girlfriend and their friends.
[As the documentary points out, the domain AshleyMadisonSucks.com was eventually transferred to Ashley Madison, which then shrewdly used it for advertising and to help debunk theories about why its service was supposedly untrustworthy].
Harrison even went after Bradshaw’s lawyer and wife, listing them both on a website he created called Contact-a-CEO[.]com, which Harrison used to besmirch the name of major companies — including several past employers — all entities he believed had slighted him or his family in some way. The site also claimed to include the names, addresses and phone numbers of top CEOs.
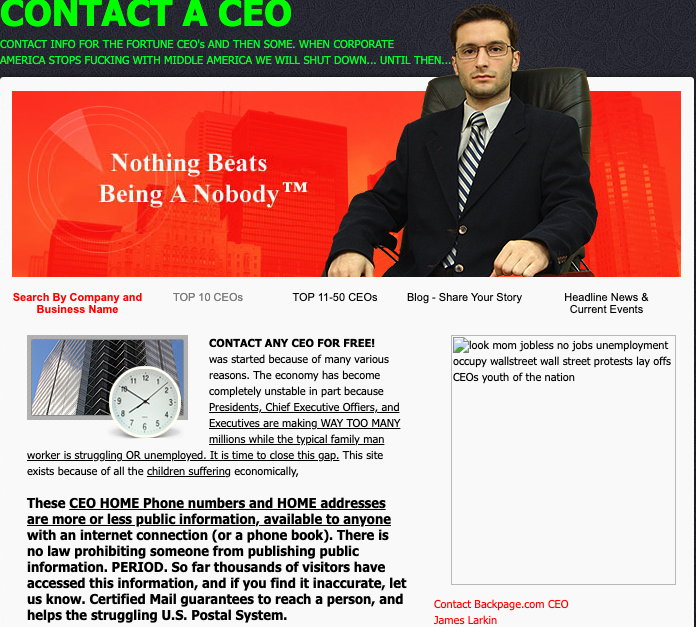
A cached copy of Harrison’s website, contact-the-ceo.com.
An exhaustive analysis of domains registered to the various Vistomail pseudonyms used by Harrison shows he also ran Bash-a-Business[.]com, which Harrison dedicated to “all those sorry ass corporate executives out there profiting from your hard work, organs, lives, ideas, intelligence, and wallets.” Copies of the site at archive.org show it was the work of someone calling themselves “The Chaos Creator.”
Will Harrison was terminated as an Ashley Madison employee in November 2011, and by early 2012 he’d turned his considerable harassment skills squarely against the company. Ashley Madison’s long-suspected army of fake female accounts came to the fore in August 2012 after the former sex worker turned activist and blogger Maggie McNeill published screenshots apparently taken from Ashley Madison’s internal systems suggesting that a large percentage of the female accounts on the service were computer-operated bots.
Ashley Madison’s executives understood that only a handful of employees at the time would have had access to the systems needed to produce the screenshots McNeill published online. In one exchange on Aug. 16, 2012, Ashley Madison’s director of IT was asked to produce a list of all company employees with all-powerful administrator access.
“Who or what is asdfdfsda@asdf.com?,” Biderman asked, after being sent a list of nine email addresses.
“It appears to be the email address Will used for his profiles,” the IT director replied.
“And his access was never shut off until today?,” asked the company’s general counsel Mike Dacks.
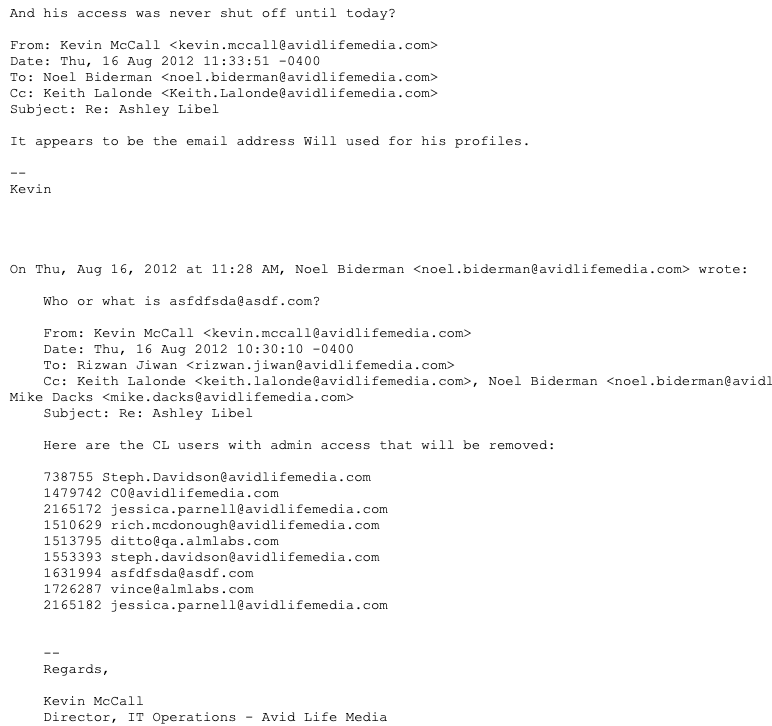
A Biderman email from 2012.
What prompted the data scientist Bullock to reach out were gobs of anti-Semitic diatribes from Harrison, who had taken to labeling Biderman and others “greedy Jew bastards.”
“So good luck, I’m sure we’ll talk again soon, but for now, Ive got better things in the oven,” Harrison wrote to Biderman after his employment contract with Ashley Madison was terminated. “Just remember I outsmarted you last time and I will outsmart and out maneuver you this time too, by keeping myself far far away from the action and just enjoying the sideline view, cheering for the opposition.”
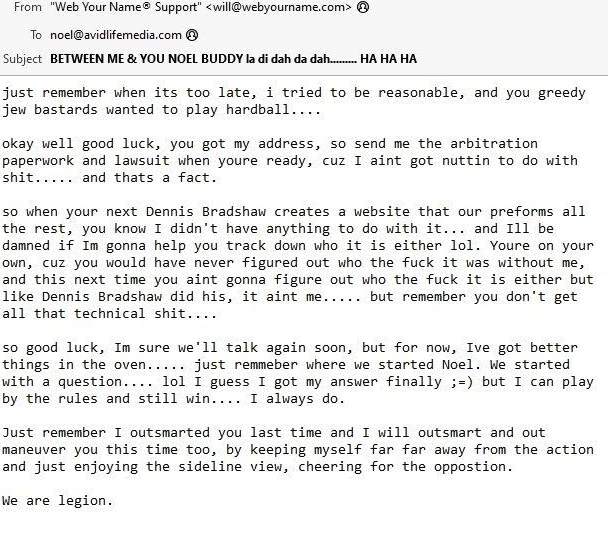
A 2012 email from William Harrison to former Ashley Madison CEO Noel Biderman.
Harrison signed his threatening missive with the salutation, “We are legion,” suggesting that whatever comeuppance he had in store for Ashley Madison would come from a variety of directions and anonymous hackers.
The leaked Biderman emails show that Harrison made good on his threats, and that in the months that followed Harrison began targeting Biderman and other Ashley Madison executives with menacing anonymous emails and spoofed phone calls laced with profanity and anti-Semitic language.
But on Mar. 5, 2014, Harrison committed suicide by shooting himself in the head with a handgun. This fact was apparently unknown to Biderman and other Ashley Madison executives more than a year later when their July 2015 hack was first revealed.
Does Harrison’s untimely suicide rule him out as a suspect in the 2015 hack? Who is The Chaos Creator, and what else transpired between Harrison and Ashley Madison prior to his death? We’ll explore these questions in Part II of this story, to be published early next week.




Nice cliff hanger, Brian. Got me on the edge of my seat. 🙂
Yeah now I HAVE to come back.
This is retarded
What an interesting read. Harrison was definitely nuts, and I am curious to know more of his (wrong)doings.
As far as “wrongs” go I think in publishing a privileged list of shady sexbots deliberately ignored by management of a shady sex (bot) company that purpots to represent themselves as a “legitimate” shady sex company… it’s all pretty shady.
Waoh, can’t wait for the rest of the article, it’s so interesting, the final point must be insane for you guys to make it into a series !!
Then Jesus asked him, “What is your name?” “My name is Legion,” he replied, “for we are many.”
Waoh, can’t wait for the rest of the article, it’s so interesting, the final point must be insane for you guys to make it into a series !!
Man I’m excited!!! First day here by way of this Ashley Madison doc(& had never heard of anything about it, thought it was a ywf). I can’t wait for part II & all the other interesting reads! Thanks for your years of great work!
“victims” of the breach and jilted spouses.
The only victims were the spouses. Justice was done.
Not entirely true. Ashley Madison never bothered to verify email addresses before signing up an account, which means anyone could have signed up anyone else’s email for the service. Also, some people registered just to see if their significant other was cheating, or to see what all the fuss was about. And it looks like a lot of the men who registered hoping to chat w/ horny housewives were really just chatting w/ bots. But all of those groups of users found themselves the subject of the same extortion attacks after their data was leaked.
But after emails associated with AM were already leaked, what would be the further ransom object if “they” weren’t “actually” using the service in a provable way? Knowing “AM never bothered to verify email addresses before signing up an account” would be nigh enough to casually absolve anything except some futher attributable direct PII or juicy details, right? I suppose most people wouldn’t already know AM didn’t verify emails, but it’s also an easy defense that could itself be verified. What would be the difference vs just harvesting emails generally (or targetedly…) and pseudo-subscribing them to embarassing groups/mailing lists to a similar extortable effect, assuming they weren’t themselves actually chatting with sexbots and giving out PII in the process? Not to defend extortion obviously, just trying to understand the “innocents” angle.
Everyone in my fraternity had accounts on there at one point. We had a pledge class that signed everyone up using their Facebook pictures and the frat info resources as a prank.
You really think that the guys that got married aren’t even slightly susceptible to a ransom 10 years later when they find out that the info used was correct and they’ve been married for 5 years now?
Yep. The lack of validation sucks.
Fwiw, I actually visited their offices to demand they remove my email address as I had never signed up and they didn’t validate it.
That clearly didn’t work as evidenced by the leaks.
Big yawn
Sounds like a cool dude. Pity he was murdered.
The truth is out there !
“who paid Krebs for this article for $100 Alex” said anyone with a braincell…
Spam
i looked at leaked databases when it happened, i saw a lot of names of people I know, and quit looking for 3 reasons:
1. I don’t want to know
2. People’s sex lives should be private
3. Nothing could be verified, you never know who signed up as who or for what
Man, 8 years after the hack and we are STILL getting plot twists in this story. I remember being a teenager browsing 9gag and seeing memes on this, thinking that it would be forgotten in like 2 weeks. Insane stuff.
The situation of the released emails not being verified reminds me of a passage in Isaiah.
9 Therefore justice is far from us,
and righteousness does not overtake us;
we hope for light, and behold, darkness,
and for brightness, but we walk in gloom.
10 We grope for the wall like the blind;
we grope like those who have no eyes;
we stumble at noon as in the twilight,
among those in full vigor we are like dead men.
11 We all growl like bears;
we moan and moan like doves;
we hope for justice, but there is none;
for salvation, but it is far from us.
12 For our transgressions are multiplied before you,
and our sins testify against us;
for our transgressions are with us,
and we know our iniquities:
13 transgressing, and denying the Lord,
and turning back from following our God,
speaking oppression and revolt,
conceiving and uttering from the heart lying words.
-Isaiah 59:9–13.
interesting….
Great reporting Brian.
1. Right off the top, the level of vitriol against KrebsOnSecurity is ridiculous. This just in: an investigative journalist who focuses on cyber security publishes stories on hacking episodes. Some of you player haters seem to have not-grasped this concept.
2. Obvious question you are probably going to answer is: did timestamps on any hack data originate after Harrison’s death? If not, then Harrison could have disseminated or time-delayed a push of hack data.
3. Was there even a criminal investigation done into the death of Harrison and if so, did the investigators realize what a wealthy enemy he had in Biderman? If not, authorities could have easily misclassified Harrison’s cause of death.